Which Encryption Mechanism Should You Use? - Built In
Which Encryption Mechanism Should You Use? - Built In |
- Which Encryption Mechanism Should You Use? - Built In
- Symmetric vs Asymmetric Encryption: A Guide for Non-Techies - hackernoon.com
- Chrome browser has a New Year’s resolution: HTTPS by default - Naked Security
| Which Encryption Mechanism Should You Use? - Built In Posted: 05 Jan 2021 07:35 AM PST  In the last few years encryption, and cryptography in general, has firmly become a part of the mainstream, largely due to privacy conversations centered around technology giants, the meteoric rise in popularity of Bitcoin, and even the success of movies like The Imitation Game. Even most laymen today understand the word encryption to refer to the technique of transforming data so it can be hidden in plain sight — and they understand its importance. Encryption has, however, been a firmly rooted component of all enterprise software design for many years. Historically, these capabilities were provided by underlying infrastructure and libraries used by IT and developer teams, who merely had to centrally turn on flags in their builds, enable configurations in their servers, and ensure the use of transport layer security (TLS) in their networking infrastructure. But with the move to microservices-based architecture and infrastructure-as-code paradigms, individual teams are now responsible for the security of their application and infrastructure stack, and it has become important for them to understand how to properly leverage encryption for all the services they develop. To properly secure data, it needs to be protected at rest, in transit, and in use. Below are various common encryption terms and frameworks, and what developers can do to leverage them properly.
Encryption of Data at RestData at rest refers to how data is stored in persistent storage. An attacker with access to the physical storage infrastructure or your device can gain unauthorized access to the data stored on it unless it is encrypted. Encryption of data at rest can be achieved in multiple ways. Disk- or File System-Level EncryptionWith disk- or file system-level encryption, the encryption is performed by the implementation of the virtual storage layer. This is completely transparent to all application software and can be deployed with any underlying storage layer, regardless of its encryption capabilities. Responsibility: Today, all cloud vendors provide this capability, and this is not something developers have to worry about — they just need to enable it. Threats It Protects Against: Stolen disks or other storage media.
Server-Side EncryptionServer-side encryption is responsible for encrypting and decrypting data, transparently from its clients. The cryptographic keys used for encryption are known only to the server. In the cloud native world, the server can either be a cloud service with keys typically controlled by the cloud provider or a service built by the developers with keys managed by developers. From the perspective of the clients, encryption is transparent. Responsibility: Many individual cloud services provide this capability, developers will need to enable the feature if it does exist. For an added layer, developers can build and manage their own server-side encryption mechanisms that can even be combined with a cloud service-based server-side encryption. Threats It Protects Against: Stolen disks or other storage media, file system-level attacks, and cloud provider internal threats if built by the developers.
Client-Side EncryptionHere the client is responsible for encrypting data before sending it to the server for storage. Similarly, during retrieval, the client needs to decrypt the data. This makes the design of application software more difficult. An advantage of client-side encryption is that not every bit of stored data needs to be encrypted, only the sensitive parts can be protected. This is often beneficial when the cost of computation is a concern. Responsibility: This is solely on the developers to design and make the process as seamless as possible for the client and end user. Threats It Protects Against: Man-in-the-middle and storage provider internal threats.
What Are the Limits of Encryption of Data at Rest?Encryption of data at rest is now considered best practice, but is not without its limitations and challenges. The most critical aspect is how and where the encryption keys are stored, who can gain access to them, and so on. While good solutions are available to secure key storage, it is essential to set them up correctly. Weaknesses in key management are, unfortunately, far too common, and are much likelier to lead to confidentiality breaches, than someone breaking a modern encryption algorithm. Everyone likely knows at least one person who lost access to their data on their smart device because they couldn't remember their back-up key. Advice to Developers: If at all possible, utilize the resources of your cloud provider for key management. Many of the services have simple configuration toggles to enable encryption at rest and will handle key management transparently. For the most security, you should choose a customer-managed key where possible. Suggested Tools: Key management services from major cloud providers including Amazon Web Services (AWS) Key Management Service (KMS), Microsoft Azure Key Vault, and Google Cloud Platform (GCP) Cloud Key Management. Another challenge with encryption of data at rest is that key rotation (the recommended practice of periodically changing secret keys) can be extremely disruptive and costly since large volumes of data may need to be decrypted and then re-encrypted. This poses a challenge when an employee with access to the key leaves the organization or the key is otherwise considered as compromised. Advice to Developers: Again, if at all possible, utilize the resources of your cloud provider for automatic key rotation as well. Today, all three major providers support automatic master key rotation, and it is a simple config flag when enabling encryption. In these scenarios, a master key will be a reference to the version of the actual encryption key. That is, when a key is rotated, all new data will be encrypted with the rotated key. Manual rotation is possible, but difficult. Suggested Tools: AWS KMS, Azure Key Vault, and GCP Cloud Key Management.
Encryption of Data in TransitAs developers run their services in the cloud, integrating with other third-party services, encryption of data in transit becomes a must. For years, there was a great deal of pushback due to concerns about latency in applications and as such many applications never implemented transit-level encryption. However, HTTPS has made huge performance gains over the past decade, and all services today have come to use it — with HTTPS even being used interchangeably with the terms SSL and TLS. Advice to Developers: Enabling HTTPS for any public endpoints is a necessity today and is extremely simple to do. There will be some minor configuration needed to be done, but if you are using any of the major cloud providers, you can quickly and seamlessly generate and integrate certificates with your services. Suggested Tools: Each of the cloud providers offer a way to generate public and even private certificates. So there's AWS Certificate Manager, Azure App Service, and GCP Certificate Manager. If you want to use another service, LetsEncrypt is free and has tools for automatic generation and rotation.
Encryption of Data in UseThis is an area of increasing interest, which addresses the risk that data ultimately needs to be available in plain-text form while it is being processed by an application. Even with the strongest encryption techniques applied to data at rest and in transit, it is the application itself that often runs at the very boundary of trust of an organization and becomes the biggest threat to the data being stolen. Below are two relatively recent techniques to address threats to data privacy while it is in use:
A somewhat related technique, popular among companies trying to avoid these problems altogether, is that of tokenization. It involves substituting sensitive data with a non-sensitive equivalent, with no intrinsic business value. The original sensitive data is kept in a highly secure, often offsite or third-party location. A common example is an online retailer storing credit card tokens instead of credit card numbers themselves. The original credit card number is kept with a third-party service, which only makes it available to an authorized payment processor when needed. While this protects the data and often offloads compliance burden on the business tasked with securing the data, it could be susceptible to token replay attacks and therefore requires that the tokens be protected, effectively just transferring the problem instead of solving it. Like with all other security techniques, there is no silver bullet or one approach IT and development teams can use to secure their data from prying eyes. The above framework, however, is a good starting point for organizations embracing digital transformation and taking a collaborative approach to security. |
| Symmetric vs Asymmetric Encryption: A Guide for Non-Techies - hackernoon.com Posted: 05 Jan 2021 03:18 AM PST  @casey-craneCasey CraneCasey Crane is a tech lover and cybersecurity journalist for Hashed Out and Infosec Insights. If you find understanding or explaining the differences between asymmetric and symmetric encryption daunting, then take a relaxing breath — we'll break it all down into layman's terms. Symmetric and asymmetric encryption — what are they and what do they mean in terms of data security? To put it simply, both are ways that individuals, businesses, and other organizations can protect their data. Asymmetric and symmetric encryption involve cryptographic techniques and tools, and both are useful in different types of digital environments. But these processes aren't all that easy to explain to others. This is why we've put together a non-techies guide. No matter whether you're new or advanced, this article can help you break down symmetric and asymmetric encryption. This way, you can easily explain it to others who may not be as tech-savvy as you. This will definitely come in handy for your upcoming holiday dinner conversations with family and friends. So, what is symmetric encryption and how does it differ from asymmetric encryption? Let's break each type of encryption down and compare them to see what is best in which applications. What Is Symmetric Encryption?Symmetric encryption means that your information is encrypted and decrypted using a single key. The data sender (or originator of the data) has one copy of the key, which they use to encrypt the data. (By "encrypt," I mean convert it from plaintext, readable data into unreadable gibberish known as ciphertext.) The data recipient, who has another copy of the same key, can use it to decrypt the data — meaning that they can revert it from ciphertext to plaintext.
The key itself is a string of randomly generated bits. When generated well and with enough entropy (randomness), the strings of bits should be completely unpredictable and, therefore, impractical to guess using modern computers. Symmetric encryption is what large businesses typically use in internal environments to encrypt their at-rest data. Why? Because symmetric encryption is fast, convenient, and isn't super resource-intensive in terms of bandwidth and processing power.
But symmetric encryption isn't perfect. In fact, it has a couple of important shortcomings that we have to talk about that mean that it can't stand on its own in public channels. But before we do that, let's first go over what asymmetric encryption is and why it's essential to the security of your data in public online environments. What Is Asymmetric Encryption?Now, let's take the concept of symmetric encryption and kick it up a level and you get asymmetric encryption. You see, asymmetric encryption is a cryptographic process that uses two separate keys — a public key and a private key — to encrypt and decrypt data. The keys are related but mathematically unique, unlike symmetric keys.
Now, while this may sound perfect, asymmetric encryption isn't a one-size-fits-all tool for security. Because it uses two separate and larger keys, it makes it too unwieldly and impractical for large-scale business encryption applications. As such, it's better suited as an authentication mechanism in many cases. This is why many businesses defer to using asymmetric key exchanges for authentication purposes and symmetric encryption to actually secure the data itself during the session. Don't worry — I'll also help you break down asymmetric key exchanges into layman's terms as well. The Role of a Public Key Exchange in Website SecurityThere's a related aspect of asymmetric encryption that comes Similarly, the key exchange process isn't truly a "key exchange," either. It's a bit of a misnomer. Rather, what it is, is a process that involves exchanging certain public variables and incorporating private variables to generate a shared key (i.e., a symmetric key) that only you and your intended recipient can create together. No, don't worry, I'm not going to get into all of the mathematical specifics of how that process works here. And your friends or family certainly won't need you to dive into all of that business, either. But you can check out this great video to get into more of the specifics on how that all works: Secret Key Exchange (Diffie-Hellman) - Computerphile
It's also important to note that this process is integral to the SSL/TLS
But asymmetric cryptographic process aren't the sole mechanisms used in website security. Symmetric encryption also plays a star role in website data encryption. Asymmetric and Symmetric Encryption Are Complementary in Website SecurityWhen it comes to website security, symmetric encryption and asymmetric cryptographic techniques go together like rock stars and bad life choices. You use techniques from one (asymmetric key exchange) to help make the other (symmetric encryption) more secure in public channels. In fact, you're actually using both of them right now to read this article. You see, when you connect to a website, any data that you send to that site is sent via an insecure protocol by default. This insecure connection is known as the hypertext transport protocol, or HTTP. This is the same insecure "http" that you'll sometimes see when you click on website URLs that display this type of warning message:  Tisk, tisk, Apache.org. You know better than to leave your site insecure like this! When you transmit data using HTTP, it means that it's sent via plaintext. And considering that when you connect to a website, because of how HTTPS works, you're actually punted between multiple touchpoints along the way. And this means that your data also passes through all of those touchpoints as well. So, all of the types of data that you don't want falling into cybercriminals' hands — such as your name, address, credit card information, or other sensitive details — are vulnerable to being intercepted by bad guys. When bad guys intercept your data in this way, it's known as a man-in-the-middle attack (MitM attack) because they're essentially inserting themselves into the middle of your communication. As a result, messages from you to another party will pass through them first, which gives them an opportunity to read or even modify your message before passing it along. Needless to say, it's not only insecure, but it's also bad news for you and the person (or website) you're communicating with. So, to make this process more secure, website admins will instead opt to use the secure HTTPS protocol (which stands for "hypertext transport protocol secure") to transmit data between users and their web servers. They do this by installing an SSL/TLS (secure sockets layer/transport layer security) certificate — or what's otherwise known as a website security certificate. This type of digital certificate ensures that you connect via HTTPS instead of the insecure HTTP protocol. It makes your web address bar in Google Chrome display a friendly secure padlock icon like this (instead of the "not secure" warning like earlier):  Image caption: As my grandfather loved to say, "this is more better." Every website should be using an SSL/TLS certificate to allow its users to securely As a result, instead of sending plaintext data across the internet, you're sending gibberish ciphertext that no one can decipher without the requisite private key. That's a win for you and a loss for the cybercriminals who want to mess you over. Asymmetric Key Exchange + Symmetric Encryption = Secure ConnectionsRemember how earlier I said that symmetric encryption had a few shortcomings? Well, the biggest one relates to key distribution. That's because there's only one key that could be known by a bunch of individuals. So, if you keep handing out that key to a bunch of different people, it gets harder to keep track of and can result in the key becoming compromised. You see, with symmetric encryption, you have to distribute the key in a secure way and make sure that only those authorized have a copy. Otherwise, if some authorized individual intercepts it, then they can simply decrypt your messages all they want. This means that either the keys must be exchanged in person or via a secure key exchange method. But if you're communicating with someone over the internet who's located across the world, that isn't really possible. This is where symmetric encryption comes into play. According to the National Institute of Standards and Technology (NIST), one of the leading authorities for cybersecurity standards, both types of encryption have their uses and work well together:
Basically, this massive run-on statement is a fancy way of saying that you should use both asymmetric key exchange/agreement and symmetric encryption processes together to securely distribute the shared key and create an encrypted connection. This is perfect for those otherwise open (and insecure) public, multi-user environments. Symmetric vs Asymmetric Encryption: Breaking Down the DifferencesAs you likely know, there are many ways that symmetric and asymmetric encryption differ in terms of how they work, the algorithms and keys they use, as well as when and where you should implement them. Let's go over a few of them. Symmetric vs Asymmetric Encryption Use Different Algorithms and Key Sizes Two of the biggest differences between symmetric and asymmetric encryption are:
Symmetric encryption algorithms are significantly faster and use smaller keys than their asymmetric counterparts. They can be used to encrypt and decrypt either blocks or streams of data. The keys tend to be smaller in terms of the number of random bits that they contain. Asymmetric encryption algorithms, on the other hand, use more complex encryption algorithms and significantly larger keys. This makes them great for encrypting and decrypting data in public channels in small batches, but not so great for use at scale. Okay, let's take a moment to compare their key lengths. I'll also break down some of the different encryption algorithms and key exchange agreements that fall under the umbrellas of symmetric and asymmetric encryption. Asymmetric Vs. Symmetric Key Lengths: If this is as clear as mud to you, let's have a quick comparison of what the difference looks like in terms of key lengths (using the random key generator at cryptotools.net): 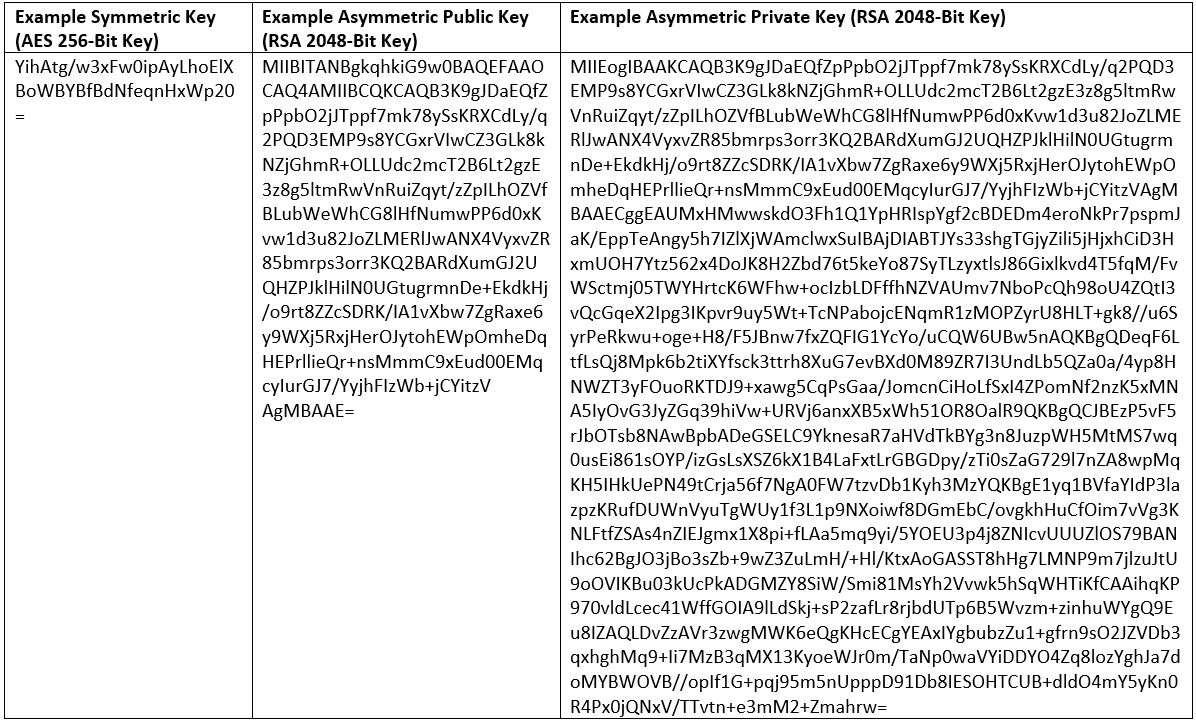 Yeah, just a wee bit of a difference in terms of key lengths, am I right? Now you can see why we say that using symmetric encryption is significantly faster than asymmetric encryption when you're encrypting and decrypting data at scale. So, what types of encryption algorithms are considered symmetric and which ones are asymmetric? Asymmetric Vs. Symmetric Encryption (and Key Exchange) Algorithms: The go-to standard for symmetric encryption is AES, or what stands for the advanced encryption standard. AES was announced as the replacement for the data encryption standard (DES) in October 2000. For asymmetric encryption, RSA (which stands for its creators' surnames — Rivest, Shamir, and Adleman — is the encryption algorithm that's most commonly used. As far as key exchanges go, though, RSA is still in use in TLS version 1.2 but is being deprecated in lieu of Diffie-Hellman in TLS 1.3. Each Type of Encryption Has Different UsesOkay, let's quickly go over some of the different uses for both types of encryption. For example, symmetric encryption is best used for:
Asymmetric encryption processes, on the other hand, are best
Final Thoughts on Symmetric and Asymmetric EncryptionWhen it comes to website and general internet security, it's easy to see how both of these types of encryption have important roles that help make it possible.
I hope this article has provided you with a little clarity about the differences between symmetric and asymmetric encryption, what each process is on its own, and how each applies to different situations and use cases. TagsJoin Hacker Noon Create your free account to unlock your custom reading experience. |
| Chrome browser has a New Year’s resolution: HTTPS by default - Naked Security Posted: 05 Jan 2021 06:56 AM PST HTTPS, as you probably know, stands for secure HTTP, and it's a cryptographic process – a cybersecurity dance, if you like – that your browser performs with a web server when it connects, improving privacy and security by agreeing to encrypt the data that goes back and forth. Encrypting HTTP traffic end-to-end between your browser and the server means that:
Without HTTPS, there are many places along the way between your browser and the other end where not-so-innocent third parties could easily eavesdrop on (and falsify) your web browsing. Those eavesdroppers could be nosy neighbours who have figured out your Wi-Fi password, other users in the coffee shop you're visiting, curious colleagues on your work LAN, your ISP, cybercriminals, or even your government. This raises the question: if snooping and falsifying web traffic is so easy when plain old HTTP is used, why do we still have HTTP at all? LISTEN NOW: UNDERSTANDING HTTPS/SSL/TLS |
| You are subscribed to email updates from "data encryption,file encryption apps,data in transit encryption" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |


Comments
Post a Comment