Trump administration reportedly considering ban on end-to-end encryption - Android Police
Trump administration reportedly considering ban on end-to-end encryption - Android Police |
- Trump administration reportedly considering ban on end-to-end encryption - Android Police
- Sikur launches new encrypted phones, this time using Sony hardware - Android Police
- How to Completely Hide Root Using Magisk - Gadget Hacks
| Trump administration reportedly considering ban on end-to-end encryption - Android Police Posted: 30 Jun 2019 12:00 AM PDT  Encryption in everyday devices should be an industry-wide standard, but many world governments are still fiercely opposed to the idea. End-to-end encryption makes it possible to send messages that can only be read by the recipient, meaning both hackers and law enforcement are out of luck. According to a new report, senior U.S. officials are debating a possible encryption ban. According to Politico, senior officials in the Trump administration met recently to discuss if the government should seek a ban on types of encryption that law enforcement can't break — effectively outlawing end-to-end encryption. One source told Politico, "the two paths were to either put out a statement or a general position on encryption, and [say] that they would continue to work on a solution, or to ask Congress for legislation." Australia passed similar legislation last year, though the country doesn't outright ban end-to-end encryption. It only requires companies to hand over user data if it can be done without weakening encryption. The U.S. federal government has fought tech companies for years of their use of encryption, and the Trump administration has stated on several occasions that it believes law enforcement should be given access to encrypted data. Before he was elected as President, Trump railed against Apple in early 2016 after it refused to unlock an iPhone used by one of the San Bernardino shooters. The FBI later paid a security firm more than $1 million to break into the iPhone, using a flaw that Apple has since patched. Rod Rosenstein, a Trump-nominated official at the Department of Justice (until he resigned in May), said in a speech in 2017, "Warrant-proof encryption defeats the constitutional balance by elevating privacy above public safety." This isn't even the first time that Trump administration officials met behind closed doors to discuss laws against encryption. A meeting with security researchers occurred over a year ago, but no legislation came out of it. |
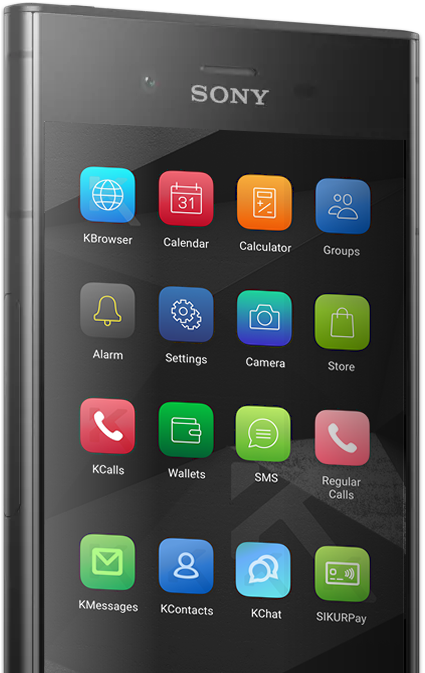
| Sikur launches new encrypted phones, this time using Sony hardware - Android Police Posted: 26 Sep 2018 12:00 AM PDT  It's been quite a while since we've heard the Sikur name, with the security-focused company last seen in February promoting its "hack proof" SIKURPhone. The company had 20,000 units available for pre-order, but they weren't scheduled to ship until August. Like all its phones, the device essentially amounted to a very secure messenger and cryptocurrency wallet with few third-party apps. Now Sikur is back, this time with Sony-branded hardware. The SIKURPhone XZ1 and the XA2 run SikurOS, which is a beefed up version of Android. Additional security is obviously the main selling point here, with Sikur advertising it as "the safest digital wallet on the market," but the company can now can boast about the hardware design too. Although the devices are basically older Sony models with a custom OS, the SIKURPhone XZ1 retails for $850 and has a 19-megapixel rear camera and a Snapdragon 835. Stepping down to the $650 SIKURPhone XA2, you'll find a Snapdragon 630, half the RAM at 3GB, but a larger rear camera with 23 megapixels. Both feature the same security measures as the company's older phones. While previous models were extremely limited in terms of app selection, the company plans to launch a curated app store by the end of 2018. This won't be Sikur's first time partnering with another hardware manufacturer. Back in 2015, it teamed up with Archos for the GranitePhone, which of course ran GraniteOS. The GranitePhone was quite underpowered even for its time, especially considering its $850 price tag. The new Sony models should give customers a more premium experience while keeping the price point steady. Both models come with access to the SIKURPlatform, a cloud-based suite of apps built with the same encryption found in the phones. With the desktop app, users can send and receive voice messages, create and edit documents, and make video calls. For enterprise users, the built-in management console provides remote management for devices and users. |
| How to Completely Hide Root Using Magisk - Gadget Hacks Posted: 17 Jul 2019 12:00 AM PDT Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good. In the case of Pokémon GO, the game's developers would even go as far as silently scanning your internal storage for the Magisk folder or any files related to the platform itself. It was quite a bold move and very intrusive since it was done in the background without user consent. At that time, you had to delete all Magisk files and folders to be able to play while being rooted. Pretty messy stuff if you ask me, but those days are long gone thanks to the new advancements in Magisk being able to avoid detection altogether. It's almost bulletproof now that the platform has adopted the randomized package name and Magisk Hide features. When you combine these two features, even stubborn games like Pokémon GO and Harry Potter: Wizards Unite are playable while being rooted. Step 1: Randomize Your Package NameThe first thing you need to do on your quest for a worry-free experience is to randomize the package name of the Magisk Manager app itself. The package name is a unique identifier for each installed app, much like the MAC address or IMEI on your phone right now. By ditching the original package name for something entirely random, the offending apps and games won't know what to look for. Open the Magisk Manager app, tap the menu icon on the left, then head to "Settings." Locate the "Hide Magisk Manager" option, then tap it once to begin the process of randomizing your package name. It will make the necessary changes in the background real fast, close the app, then reopen it once more with a newly randomized package name. Awesome! Not only does the package name get changed to something undetectable, but the app name is also altered from "Magisk Manager" to just "Manager." The keyword "Magisk" is taken out to disassociate the app with the name itself, which further enhances the ability to hide your root access. It's essential to make sure you're using this feature all the time going forward, so keep that in mind.   Step 2: Use Magisk HideNow that you have the first half of the changes required to make everything work, it's time to use of the Magisk Hide feature to further complement your new randomized package name. This is the other part required when trying to get all apps and games to play nicely with your root access. Many financial or banking apps like to block root users, so that's another thing to be aware of. To get started, open the newly named "Manager" app to the main screen like before, tap the menu on the left, then head to the "Magisk Hide" entry on the list. Locate the offending app(s) that are detecting your root access and tap the dot on each one to put a checkmark on them. That's it! Some apps will have just a single entry on the Magisk Hide list while others could have multiple, such as Pokémon GO. Tapping the down arrow icon will expand the rest of the entries for that specific app. It should enable them all by default when you tap the first dot, but it's always good to make sure everything is checked off when going through the list of offending apps anyway. Step 3: Enjoy Your Apps & GamesFrom here, you can dive right into the apps and games that you thought you'd never be able to use as a root user. You don't have to worry about doing a reboot when using Magisk Hide, but occasionally you might try that if an app is still not playing nice with root access. The apps and games listed below are just a few good examples you might find yourself using now that you can completely avoid root detection. There are plenty more examples out there that try to block root users, but with the power of Magisk at your disposal, you should have little to no issues whatsoever. There's always a chance for new root detection methods, but everything is good right now. Pokémon GOHarry Potter: Wizards UnitePS4 Remote PlaySpectrum TVCredit One BankFinal NoteSome really cool new development for hiding your root status even further than this is coming with the new test versions of Magisk on Android 10 "Q," so stay tuned for future news on this very topic. I'll be updating the guide when we start seeing some stable public builds for everyone to use as a daily driver. |
| You are subscribed to email updates from "android marshmallow encryption,secure voice app,encrypting lg g3" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment