iMessage vs. RCS: Which is better? - iMore
iMessage vs. RCS: Which is better? - iMore |
| iMessage vs. RCS: Which is better? - iMore Posted: 18 Dec 2019 12:00 AM PST You know and love iMessage, and for a good reason. Launched back in 2011, iMessage has become one of the most popular messaging platforms in the world. It's baked right into iOS and macOS devices, giving you an easy and streamlined platform for fast and fun text messaging. iMessage's feature-set and popularity are unmatched, but its lack of support for Android devices has been a long-running pain point for some users. Pros
Cons
RCS, or Rich Communication Services, is the upgraded version of old-fashioned SMS texting. The most popular way to access RCS right now is by using the Google Messages app, giving you many of the same features found in iMessage — including texting over Wi-Fi, typing indicators, high-res file sharing, and more. RCS is now widely available for all Android devices to use, but it's only up and running in select countries. Pros
Cons
iMessage and RCS have a lot more in common than you might expect. Both messaging platforms allow you to text over data and Wi-Fi, support read receipts, typing indicators, and can send high-resolution photos and videos. iMessage has the benefit of being around for nearly a decade, allowing it to feel more well-rounded, but RCS is showing a lot of promise in these early days. Neither one does anything for truly universal messaging, however, as iMessage is exclusive to iOS, and RCS currently only works with Android phones. Features
First thing's first, let's talk features. Both iMessage and RCS bring a lot to the table, allowing you to elevate your conversations with useful tools and other goodies. All of the core features you'd expect from any messaging app are available on both iMessage and RCS. They both include the ability to text over data and Wi-Fi, typing indicators, and read receipts that let you see when someone has read your sent message. Both iMessage and RCS also allow for high-resolution photo and video sharing, support group conversations, and have tools for blocking spam/unknown numbers. In regards to all of these core features, iMessage and RCS are pretty evenly matched.
As you start to dive into some of the more minute features, you can start to see the benefits of iMessage being around since 2011 and having time to update/improve — some of the highlights being:
Something else both platforms do well is desktop access. iMessage conversations can be seen on the built-in Messages app for macOS, where Google Messages has a web app you can visit from virtually any web browser (including from your iPhone). Last, but certainly not least, iMessage has the big benefit of supporting end-to-end encryption — allowing for highly secure messaging between you and your contacts. By contrast, RCS messaging through Google Messages is not end-to-end encrypted. Google says that RCS messages are protected as the company doesn't keep a copy of your texts as they go through Google's servers, but you still aren't getting true end-to-end security. Ease-of-use
Moving away from features, here's where iMessage starts to really show its dominance over the current implementation of RCS. Using iMessage is about as simple as can be. Open the Messages app on your iPhone, send a message to someone, and if they also have an iPhone, it'll be sent as an iMessage with the iconic blue bubble. If you send a message to someone that doesn't have an iPhone, it sends as a green bubble to indicate that it's being sent as a regular SMS text message. That's all there is to it. This simplicity has been a big part of why iMessage is as popular as it is today. There's nothing you have to think about for it to work, allowing you just to message away without having to worry about a thing. RCS has gotten a lot better, but it's not quite as seamless as the iMessage experience. If you want to use RCS on an Android phone, you need to be using Google Messages. It's pre-installed on a lot of phones, but not all of them — requiring you to download it from the Play Store if it's not. Once that's done, you then have to go into the settings and turn on "chat features." Other Android users that use Google Messages and have chat features turned on will be able to communicate with you via RCS. However, if they're using a different texting app or don't have chat features enabled, you'll still be using SMS texting. Availability
On a similar note, iMessage also has the upper-hand when it comes to availability. Not only does iMessage just work out of the box without any additional setup required, but it also works in every country. Comparatively, Google has only enabled RCS chat features in the Google Messages app for people in the United States, the United Kingdom, and France. Other countries will likely follow suit as time goes on, but there's no getting around the limited support RCS faces right now. Two great messengers for their respective operating systems
Considering how much longer iMessage has been around for, it shouldn't come as any surprise that it's the superior platform. It has more features, is easier to use, and is much more widely available. Then again, those advantages should be expected when pitting an eight-year-old messaging service against one that began its full rollout in 2019. Google is making a lot of headway with RCS, and while there is certainly room for improvement, the implementation is already pretty great. Both iMessage and RCS are top-notch messaging services for iOS and Android, respectively, with that being the ultimate conclusion. Neither one works across both operating systems, and while Apple could start supporting RCS down the road, that doesn't seem likely to happen in the immediate future. So, if you like iMessage, keep on using iMessage. If you have an Android phone and want to give RCS features in Google Messages a shot, go for it. Neither one will steer your wrong, and with both being free to use, you have nothing to lose. Ultimate messengeriMessageYou know and love it iMessage is the go-to messaging app for iOS, and there's a good reason for that. iMessage is chock-full of features, is incredibly easy to use, and has proven to be incredibly fast and reliable. Something newRCS (Google Messages)The Android messenger to watch While it's still in its early days, RCS features with Google Messages are already off to a great start. Once Google can expand it to more countries and make the onboarding more seamless, it'll be hard to ignore. We may earn a commission for purchases using our links. Learn more. | |||||||||||||||||||||||||||||||||||||||
| Posted: 17 Dec 2019 12:00 AM PST  Anadolu Agency via Getty Images WhatsApp has endured a difficult 2019 on the security front, with stories of nation-state hacking campaigns and multiple vulnerabilities, even as it battles with governments and their agencies over its insistence on end-to-end encryption. And now, just as the year draws to a close, there's news of yet another security threat that has compromised the integrity of the platform. The risk this time is from specially crafted "app killing" messages that crash WhatsApp severely enough that users are taken offline and may find it difficult to recover. Are you at risk?WhatsApp has patched the issue—it did so in September when it was first privately disclosed by cybersecurity researchers at Check Point. But if you have not installed a new release since before that time you remain at risk. Check Point "urges all WhatsApp users to update to the latest version of the app immediately." WhatsApp also maintains that the threat is obscure, never likely to impact users in the real world. In this they are wrong and have missed the reason the issue is so important and carries such potential critical risk. To understand why that's the case, let's look at the threat itself and how it works. The exploit is unnervingly simple. It relies on two separate security vulnerabilities in WhatsApp, both now patched. The first is that any user could be added to a group without needing to consent, that user then receives messages sent to the group; the second is that the metadata built into a message can be manipulated to break the WhatsApp phone app when that message is received. Combine the two vulnerabilities together and you have a frightening new attack vector. Let's look at how a nation state bad actor might exploit such a vulnerability. If I have the phone numbers of a group of reporters or activists or dissidents, I can add those numbers to an unwanted group and then send that group an "app killing" message. I would do that all at the same time. The first a target would know of the threat is when an innocuous, likely socially engineered "WhatsApp Killing" message is received. As soon as that message is opened, WhatsApp will crash, failing to restart until it is deleted and reinstalled. If users don't have current backups then their data will be lost. I could mount this attack ahead of a protest or political event, or I could use it to take one or more individuals offline. Check Point researcher Oded Vanunu explained to me that these "app killing messages" present a critical risk, "denial of service scenarios have been seen before on WhatsApp," he said, "but not where you need to uninstall the app. This is very aggressive. Users who do not back up will lose everything. Users that are not technical won't be able to activate WhatsApp any more." A WhatsApp spokesperson told me that the platform "greatly values the work of the technology community to help us maintain strong security for our users globally—we quickly resolved this issue for all WhatsApp apps in mid September. We have also recently added new controls to prevent people from being added to unwanted groups to avoid communication with untrusted parties all together." WhatsApp either doesn't know or won't share the percentage of its vast user base that has shifted onto patched versions of its apps. This issue seems to hit Android rather than iOS. But that advice, to ensure your messaging platforms are always up-to-date, should be followed by all users on all platforms. This issue also highlights the vulnerability of groups. Most of us now belong to countless groups—large and small. And many of those groups have growing or changing memberships. It's worth being mindful of how many groups you belong to—especially groups you don't recognise or no longer use, how those groups are administered, and even checking periodically on those memberships lists. How does it work?The latest vulnerability can be seen in Check Point's proof of concept video and messaging screenshot below, with the group chat message manipulated with erroneous metadata. When WhatsApp fails to process that data, it is forced into a crash loop impacting all group members. There is no way out. "The group chat cannot be restored and needs to be deleted." The app itself must be reinstalled. The team at Check Point has made deconstructing WhatsApp security something of a speciality. Vanunu told me they research WhatsApp protocols "because its infrastructure allows malicious users to manipulate messages and distribute fake news—we wanted to understand how this is possible on an encrypted platform." The team says WhatsApp provides "threat actors with an additional weapon in their arsenal to leverage the messaging platform for their malicious intentions." 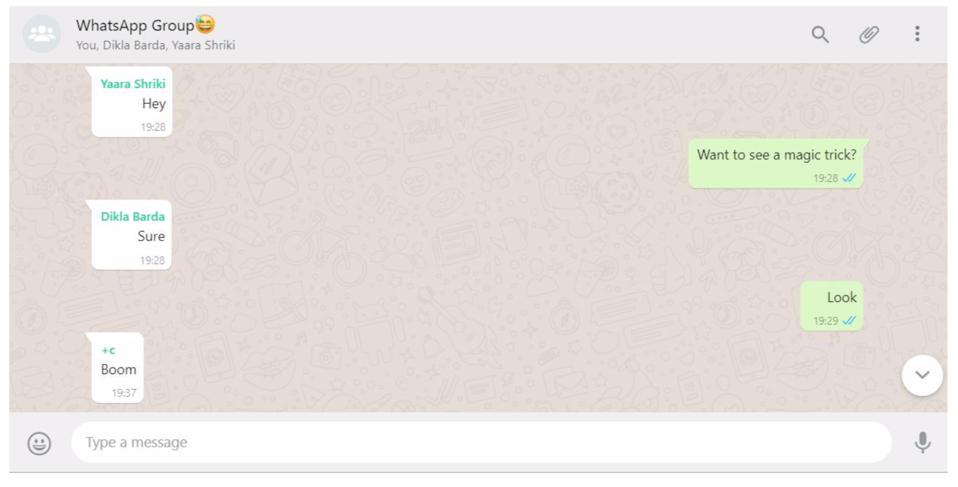 Check Point "By sending this message," Check Point explains, "the WhatsApp application will crash in every phone that is a member of this group." Worse, the crash will repeat every time the app is reopened, forcing all users to delete the app and then reinstall it. Beyond the communications denial of service, once you know a user has been pushed from one platform you can mount an attack on another. "Say I want to infect you," Vanunu tells me. "I know my infection exploit only works on SMS, so I DoS your WhatsApp, and then phish you with an SMS to infect you." This isn't the first timeThis latest issue comes hot on the heels of others for WhatsApp—and it's a worrying pattern. The year's lowlight was undoubtedly the alleged hacking of dissidents and activists by Israeli spyware firm NSO, as I reported in May. WhatsApp confirmed that the attack would "take over the functions of mobile phone operating systems." There were material implications for the safety and security of lawyers, journalists and activists, and Facebook instigated legal action against NSO as a result of the attack to protect the integrity of its technology. But that was not an isolated security breach. In October, I reported on a WhatsApp flaw that allows an attacker to use a "malicious GIF image" to potentially access user content. WhatsApp quickly patched the issue. Then in November, I reported that Facebook had quietly confirmed another security vulnerability that would expose users to the risk of malware being planted on their devices through "specially crafted MP4 files" sent via WhatsApp. The company discovered and patched the issue before, it said, any exploitation could take place. What next for WhatsApp?The WhatsApp team and owner Facebook takes security seriously—difficult to argue it's "in their DNA" without doing that. And the platform's security issues are not unique. We have seen others exposed—particularly rival Telegram, and the standard SMS alternative is wide open to attack. But WhatsApp has become the mass-market security standard bearer, and that's why this hits so hard. On the encryption front, Facebook is making a stand alongside other U.S. tech giants, with company spokespeople describing government requests to open encryption to lawful intercept as "a gift to criminals, hackers and repressive regimes," exposing users to "real-life harm." And for that the security community applauds the platform. But, at the same time, this is Facebook, and that means inevitable skepticism as future plans to monetise WhatsApp unfold. WhatsApp has become and remains a target for threat actors because of its ubiquity. You can pretty much guarantee it will be installed on a target device, and that makes finding its security vulnerabilities a worthwhile venture. It is going on right now—as ever in security, we only report on the exploits we know about. |
| You are subscribed to email updates from "android file encryption,cell phone encryption security,encrypted chat android" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |





Comments
Post a Comment