5 best TrueCrypt alternatives | Encrypt your computer with these apps - proprivacy.com
5 best TrueCrypt alternatives | Encrypt your computer with these apps - proprivacy.com |
| 5 best TrueCrypt alternatives | Encrypt your computer with these apps - proprivacy.com Posted: 19 Sep 2019 12:00 AM PDT If you want to protect your data from prying eyes, then you need to encrypt it. Previously many of us relied on Truecrypt to do this, however, as the popular encryption app was mysteriously discontinued, we have created this article to give you five alternatives to TrueCrypt. If you are serious about security, then you will do this yourself rather than using a third-party to do it for you. This is what is meant by end-to-end encryption (e2ee). But even if you are using e2ee, how do you know that the software is not doing something untoward? Such as secretly sending your encryption keys back to its developers, or creating a backdoor in the encryption. The only guarantee we can have against this is the use of open-source code. Only if a program can be freely examined to ensure it does what it is supposed to (and only what it is supposed to) can we place a reasonable amount of confidence in it. If the code has been audited by a reputable third-party then we can have even more confidence in it, but even this is imperfect, as code can always be changed the second the auditors leave the building. So the fact remains simply being able to audit the code is the surest guarantee possible that any program is secure. TrueCrypt alternativesWe have listed the best alternatives to TrueCrypt below. Most of them use the industry-standard AES cipher, so you may also wish to learn how AES encryption works. Platforms Windows. MacOS, Android, and Linux. Third-party Android and iOS apps allow you to open and access data stored VeraCrypt containers.
VeraCrypt is a fork of TrueCrypt and its direct successor. Other than minor branding changes, it front-end looks the same and its functionality is identical to that of TrueCrypt. It basically is TrueCrypt except that its code has been fully audited, problems discovered with TrueCrypt have been fixed, and the app is under active development. As such, VeraCrypt is widely regarded in the security world as the go-to open-source full-disk encryption program. It allows you to create a virtual encrypted disk (volume) which you can mount and use just like a real disk Or it can encrypt an entire disk partition or storage device (e.g. a hard drive or USB stick), including the entire drive your Operating System boots from. By default, VeraCrypt encrypts all data stored in a volume with an AES-256 cipher, although when creating a volume you can specify an alternative cipher. The NIST averse, for example, can opt to use a Twofish, Serpent, or Camellia cipher. Data is then authenticated using SHA-512 by default, but again, users can opt to use different hashing algorithms if they prefer. A notable feature of VeraCrypt is that any file, for example, an innocent-looking photo file, can be used as the container for a VeraCrypt volume. Even more notable is its hidden volume feature which provides plausible deniability. It does this by hiding an encrypted volume inside another VeraCrypt volume in such a way that, if the correct precautions are taken, it is impossible to prove the second hidden volume exists. Data stored in VeraCrypt containers can be securely synced across devices by storing a volume in (and mounting it from) a cloud storage sync folder. VeraCrypt can be used in this way to store data securely on otherwise insecure platforms such as Dropbox. It is not an ideal tool for this job, however. Volume sizes can be large and are of a fixed size which you must specify when creating them. And when any data inside a volume is changed the entire volume must be re-uploaded Of all the software discussed in this article, VeraCrypt is by far the most thoroughly audited open-source encryption solution available. Please check out our guides on VeraCrypt & how-to basics and A Guide to VeraCrypt hidden volumes for deep dives into this important encryption program. AES CryptPlatforms: Windows, macOS, Linux, Android (third party but open source). A third-party AESCrypt for iOS app is also available, although it is closed source and free users are limited to simply viewing files pre-encrypted on the desktop using AES Crypt.
AES Crypt is a free open source (FOSS) cross-platform per-file encryption app which secures files using the AES-256 cipher. As a per-file encryption app, it allows you to manual encrypt individual files. Batch file encryption is not supported, although this limitation can be overcome somewhat by creating zip files out of folders, and then encrypting the zip file with AES Crypt. This very easy-to-use Java-based file program integrates with the OS, providing simple file encryption using the right-click menu button in Windows, or drag and drop in macOS and Linux (or an extension allows right-clicking in macOS). File decryption is performed by simply double-clicking the encrypted.aes file, and entering the password you supplied when creating it. A command-line interface is also available. It should also be noted that when you create an encrypted version of a file, the original unencrypted version remains untouched. This is great if you just want to store the encrypted version online, but for maximum security, you should delete the original. Just don't forget the password! Platforms (free): Windows. Free MacOS, Android, and iOS apps are available which allow you to open and view files, but not encrypt them. Platforms (Premium): Windows, macOS, Android, and iOS.
Like AES-Crypt, AxCrypt is an open-source cross-platform per-file encryption app which secures files using AES. It is, however, a quite different beast. It comes in a free version aimed mainly at Windows users and a Premium version which costs $35 USD per year (30-day free trial). AxCrypt Free integrates with the Windows OS to provide seamless on-the-fly AES-128 file encryption. Rather than setting a password each time you encrypt a file, you sign into the app and then all selected files are automatically encrypted and decrypted using that password. Folders themselves cannot be encrypted using AxCrypt Free, but all files in a folder can be batch-encrypted. Or you can select as many files as you want from anywhere on your PC and perform batch encryption on them. For Windows users, then, AxCrypt Free offers many advantages over the rather basic AES Crypt. What you lose, however, is cross-platform compatibility. Free apps for macOS, Android, and iOS (but not Linux) allow you to open and view encrypted files, but not encrypt them. The Premium version fixes this problem with full support for all mentioned platforms. It also offers many useful additional features on all supported platforms, including full folder encryption (with sub-folder encryption), key sharing, account key backup, anonymous file names, and more. Platforms: Linux (DEB package or compile from source), macOS (using Homebrew).
gocryptfs is inspired by the brilliant but flawed EncFS. Like Encfs, it creates paired folders or "volumes." One volume contains the unencrypted files (let's call it the "private folder'), while the second matching volume (let's call it the "encrypted folder") holds an encrypted version of the files in the first (private) volume. Unlike VeraCrypt, each file in a volume is encrypted and stored individually, so a change to one file does not mean re-uploading an entire encrypted container. This makes gocryptfs much better than VeraCrypt at storing files on cloud services such as Dropbox, as local files are kept unencrypted in the private volume, but are mirrored on Dropbox (etc.) in encrypted form by simply placing the matching "encrypted volume" in a cloud folder. What gocryptfs does not do is simply encrypt a file. Someone with access to the "personal folder" has access to the unencrypted files. In addition to this, files names in the encrypted folder are obscured, but metadata such as directory structure and file size are not. gocryptfs is command line only, but the setup is very easy. Once set up, you can drag-and-drop files to and from the private folder using your regular GUI file manager. Alternatively, SiriKali is a GUI frontend compatible with gocryptfs. Data is secured and using AES-256-GCM, with GCM also providing authentication. SecureFS and Crysfs are similar EncFS-inspired apps. SecureFS fixes the issues with EncFS and is notable for being available for all major platforms, including Windows (requires MS Visual C++ 2015 redistribution package). Crysfs' support for Windows is still very experimental, but it fully supports Linux and macOS, and improves on gocrypt and SecureFS by encrypting file metadata and directory structure. Platforms: Windows, macOS, Linux, Android, iOS.
Cryptomator provides transparent encryption of files stored in the cloud. The encrypted vault is stored in your cloud folder, but is decrypted and mounted locally as a virtual drive for seamless drag-and-drop functionality. Files are encrypted individually, so when changes are made, only the corresponding encrypted file is changed. In addition to the content of files, the directory structure is hidden, although file modification dates cannot be hidden without breaking your cloud provider's synchronization feature. Vaults are secured using AES-256-CTR and unlocked using a passphrase which is protected against brute force attacks using the scrypt key derivation function. Cryptomator for the desktop works on a pay what you want model. It can be had for free, but users are encouraged to donate towards its development. The mobile apps (which support fingerprint unlock) cost $8.99 at time of writing. Final ThoughtsVeraCrypt is a drop-in replacement for TrueCrypt. If your encryption needs are somewhat different, then the open-source tools discussed in this article reflect the variety of use-cases for encryption apps. You may need to choose between AES Crypt and AxCrypt, and between gocryptfs (or other Encfs-inspired variant) and Cryptomater, but most apps lists here do their own specific thing with very little crossover in functionality between them. The best advice, therefore, is to deploy a variety of encryption apps. This means you will the right tool for the job, rather than trying to knock square pegs into round holes by using a single app to perform jobs it was not designed to do. |
| NordLocker Review | File Encryption Software From NordVPN - Is it good? - proprivacy.com Posted: 18 Nov 2019 12:00 AM PST
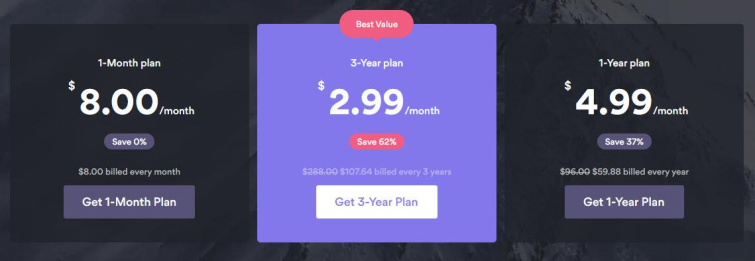
SummaryNordLocker is a new encryption tool from the highly respected VPN company NordVPN. We found it to be a powerful and easy-to-use product, albeit one that will face stiff competition from the wealth of free and open-source alternatives that are available. In this NordLocker review, we take an in-depth look at pricing, features, how secure it is and more. PricingA free version of NordLocker is available which limits users to 5 GB of encrypted data. Free users can, however, decrypt files of any size sent to them. Premium users can encrypt unlimited amounts of data. Pricing is rather high for a month-by-month plan, although it does get more affordable if you buy longer-term packages.
As with the NordVPN service, you can try 30 days of NordLocker Premium out for free with a no-quibble money-back guarantee. It should be noted that a subscription model for the kind of thing which is normally offered as a stand-alone app did raise eyebrows here in the ProPrivacy office, although, there may be good reasons for it. Features
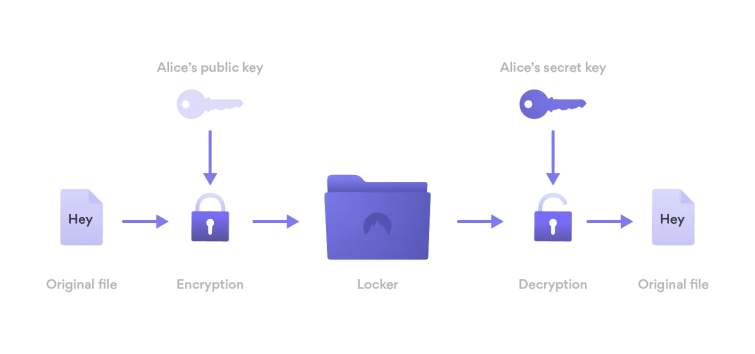
NordLocker is not open-source but is based on the excellent open-source gocryptfs per-file encryption app. This means that each file in a volume is encrypted and stored individually, so a change to one file does not mean re-uploading an entire encrypted container when stored online. The beauty of this system is that if, for example, you open a Word document stored in a NordLocker container, edit and save it, then the changes are seamlessly saved in the encrypted document. This makes NordLocker a great choice for storing files securely on otherwise insecure cloud storage services such as Dropbox or Google Drive. Master password resetWhen you create a new account, you also choose a master password which is used to encrypt your files (see technical security below). NordLocker also generates a recovery key that's only available to you and is best kept offline for added security. This can be used to reset your master password but exercise caution. If you lose both your master password and the recovery key, then you won't be able to open your files. Privacy and securityJurisdictionNordVPN is legally based in the Republic of Panama and the NordLocker Terms of Service make it clear that all legal disputes will be resolved in that jurisdiction. Panama has an uncensored Internet and no domestic surveillance we are aware of. It is also outside any direct sphere of influence of the United States and its Five Eyes spying partners, although a strong economic presence might allow the US to exert indirect pressure on the Panama government should it wish to. NordVPN has admitted to having close links with Lithuanian infrastructure provider Tesonet, but the exact nature of this relationship remains unclear. Privacy policyAt present, the NordLocker website does not host any trackers, although its privacy policy gives it a great deal of leeway to perform extensive tracking of website visitors in the future. NordLocker provides client-side encryption, so its developers have no access to your encrypted data, although some aggregated and pseudo-anonymized diagnostics and usage data are sent from its apps to Tefincom. The Windows client has an option to turn such sharing off, although this is sadly not present in macOS just yet. All data which is collected may be shared with third-party service providers, affiliated companies, and officials in accordance with valid legal demands. European customers' data is, of course, protected by GDPR. Technical securityThe first thing to note is that NordLocker is a closed-source proprietary software. This means we just have to trust its developers that it is what they say it is, and that it's not doing anything it shouldn't. Such is the nature of all closed-source software. All files are encrypted client-side, meaning that NordLocker provides end-to-end encryption. You encrypt your files, and only you or other NordLocker users you have chosen to share them with can decrypt them. So even if you store them somewhere wildly insecure, such as Dropbox or Google Drive, they are secure. Data is secured using AES-256-GCM and the encryption keys hashed using Argon2. Both of which are tried and tested cryptographic primitives. Public key cryptography for the generation and authentication of asymmetric key pairs, however, is via Elliptic-curve cryptography (ECC) instead of the more common RSA.
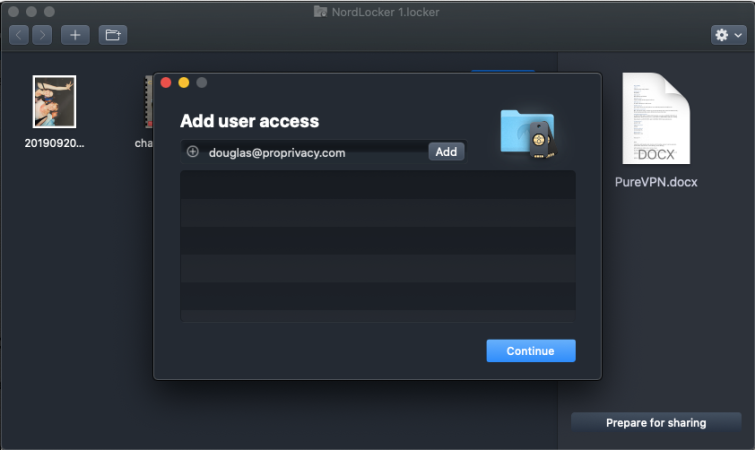
Locker keys never leave your desktop without being encrypted using your secret key and the XChaCha20 cipher with Poly1305 authentication. Your secret key is derived from your master password, which is hashed and salted using the Argon2 key derivation function. Concerns about ECC cryptographyElliptic curve cryptography has the big advantage of requiring much smaller key sizes, but its use is highly controversial. Its existing known vulnerability to side-channel attacks and its theoretical known vulnerability to quantum computing attacks are worrying enough, but even more worrying is how easy it is to insert backdoors into the algorithm. Indeed, ongoing concerns that a backdoor might have been inserted into the Dual_EC_DRBG elliptic curve algorithm appear to be confirmed by internal NSA memos leaked by Edward Snowden. Despite such concerns, "the algorithm, as a whole, remains fairly secure" if properly implemented, which is a known problem. As an IASCA report on Elliptic Curve Cryptography notes. "In a nutshell, a lot of things can go wrong while ECC is being implemented. There are numerous examples of how the failed implementation of ECC algorithms resulted in significant vulnerabilities in the cryptographic software." And being closed-source, there is simply no way to know how well ECC cryptography has been implemented in the NordLocker software. In fairness to NordLocker, though, the kind of attacks that ECC is vulnerable are unlikely to be part of most of its customers' threat models. Sharing filesLockers, folders and individual files (which are converted into Lockers) can be shared with other NordLocker users via almost any means – by email, via a shared Dropbox folder, on a USB stick and various other methods.
Thanks to asymmetric public-key cryptography (ECC), only the intended recipient, identified by their email address, can unlock the Locker using his or her own private key. Due to this, we assume that it requires some form of centralization in order to distribute customers' public keys to senders.
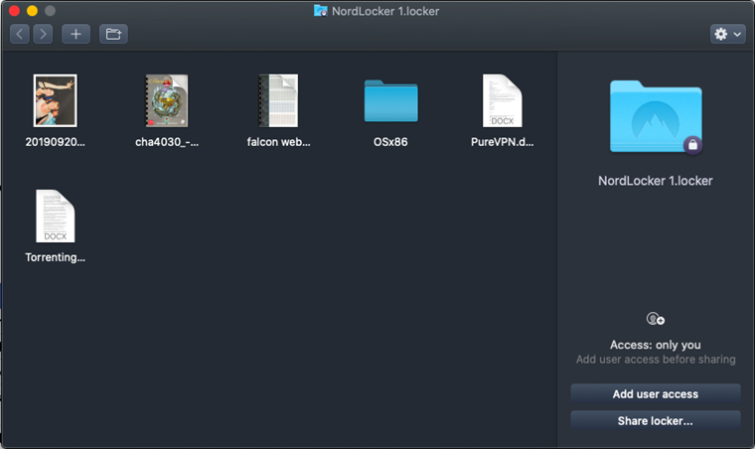
If this is the case, then it explains why NordLocker works on a subscription model rather than being sold as a stand-alone product. But it also raises questions about whether NordLocker can keep a record regarding who sends files to who. Customer CareThe website features a fairly simple FAQ and some troubleshooting guides. 24/7 live chat support is promised but was not available when this review was written. Instead, early adopters will have to rely on email support, which is already in place. Ease of useNordLocker is available for Windows and macOS. The Windows app requires the .Net Framework 4.8, which must be installed during setup if it is not already present on your system. Once opened with your master password, a NordLocker container acts just like a regular folder. Files will be opened by their usual programs and seamlessly re-encrypted when changes are saved.
To encrypt files, just drag and drop them into an open Locker window. You will be asked if you want to keep the original or move it to the Locker-only. You can add user access for other NordLocker customers, which is particularly useful for sharing Lockers that are stored online. To store a Locker online, simply upload it to your cloud service of choice. If you store a Locker in your cloud folder, then any changes made to files to it will be immediately mirrored in your cloud storage. You can also share files and folders by converting them into new Lockers and then sharing them by whichever means you prefer. As already noted, this feature is still in the works at the time of writing.
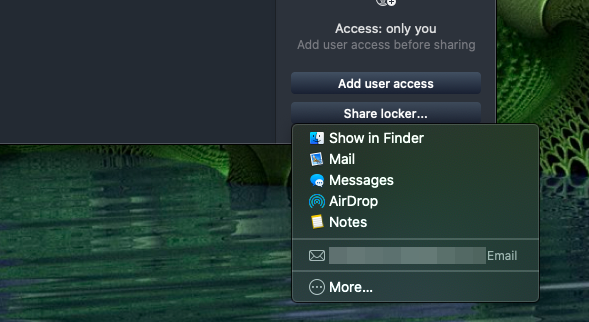
In Windows, shared Lockers are simply saved so that you have to share them yourself manually, such as by adding one as an email attachment. The macOS app has slightly better OS integration, allowing to share Lockers using the built-in macOS sharing function automatically. Final thoughtsNordLocker is a very polished product. It looks great and provides arguably the easiest way we have seen to encrypt files locally or in the cloud and to share them with others securely. We are not convinced that the use of Elliptic curve cryptography is the best choice, but the technical security used to protect your data is otherwise very robust. It's just a shame that the app is closed-source, so we can't really see what is going on or how well the security has been implemented. Our other big concern is pricing. The encryption app space is already crowded, with plenty of excellent and fully open-source options available. We will say that none of these is as polished or versatile as NordLocker, but they are free and open-source. NordLocker is not cheap (especially compared to free), and even as a commercial product its subscription model is a little jarring for what many would think of as a stand-alone product deserving a one-off price tag. But as we have already speculated, there may be reasons for this. It would be nice to be able to access encrypted files from mobile devices, but we would be very surprised if iOS and Android apps are not in the works. Overall, we think NordLocker is a very good product that offers a unique take on encrypting files locally and in the cloud. But it's neither free nor open-source. |
| You are subscribed to email updates from "best file encryption android,android m encryption,how can i encrypt my phone" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |







Comments
Post a Comment