Android security: Multiple bootloader bugs found in major chipset vendors' code - ZDNet
Android security: Multiple bootloader bugs found in major chipset vendors' code - ZDNet |
| Android security: Multiple bootloader bugs found in major chipset vendors' code - ZDNet Posted: 04 Sep 2017 12:00 AM PDT  The researchers have found flaws in bootloaders from a number of makers but note that the design of Huawei's bootloader makes its bugs "quite severe". Image: James Martin/CNETSmartphone bootloader firmware should be secure even if the operating system is compromised. But researchers have found five flaws in major chipset vendors' code that leave the process vulnerable. The vulnerabilities have been found by a group of researchers from the University of California, Santa Barbara, who've built a tool called BootStomp to automatically detect security flaws in bootloaders, which load the OS kernel when devices are turned on. The tool identified six zero-day flaws in two bootloaders after analyzing code from four large chipset makers, including Qualcomm, MediaTek, Nvidia, and Huawei. They also rediscovered a known flaw in a Qualcomm bootloader using the tool. Five of the six new-found flaws have been confirmed by the vendors. As they note, bootloaders are difficult to analyze with software partly because they're closed source, hardware specific, and hard to reverse-engineer. BootStomp has been built to overcome those difficulties. "The goal of BootStomp is to automatically identify security vulnerabilities that are related to the (mis)use of attacker-controlled non-volatile memory, trusted by the bootloader's code," the researchers explain. "In particular, we envision using our system as an automatic system that, given a bootloader as input, outputs a number of alerts that could signal the presence of security vulnerabilities. Then, human analysts can analyze these alerts and quickly determine whether the highlighted functionality indeed constitutes a security threat." Ensuring the integrity of bootloaders is critical to Google's Verified Boot and ARM's Trusted Boot, where bootloaders verify the integrity of each other to create a so-called 'chain of trust'. If someone tampers with bootloader components, a kernel or the file system image, the device should be unusable. As the researchers note, this sequence should be a rigid process that prevents a compromise even if the Android OS itself has been hacked. However, hardware vendors are given the flexibility to implement bootloaders differently to suit their products. Using BootStomp, the researchers have found 36 potentially dangerous paths during bootloading sequences, of which over a third were vulnerabilities. "Some of these vulnerabilities would allow an adversary with root privileges on the Android OS to execute arbitrary code as part of the bootloader. This compromises the entire chain of trust, enabling malicious capabilities such as access to the code and storage normally restricted to TrustZone, and to perform permanent denial-of-service attacks -- ie, device bricking. "Our tool also identified two bootloaders that can be unlocked by an attacker with root privileges on the OS." For the paper, the researchers assumed the attacker can control any content of non-volatile storage on a device, which could happen if an attacker has gained root on it. The five bootloaders were from devices using three different chipset families, including Huawei P8 ALE-L23 with the Huawei/HiSilicon chipset, a Sony Xperia XA with a MediaTek chipset, and Nexus 9 with Nvidia's Tegra chipset. They also looked at a new and old version of Qualcomm's bootloader. The known bug, CVE-2014-9798, is a denial of service affecting an old version of Qualcomm's bootloader. The new bugs included one in Nvidia's bootloader, and five affecting the Huawei Android bootloader. The researchers note that the design of Huawei's bootloader makes the bugs "quite severe" because they would allow an attacker to break the chain of trust, and gain persistence in the device that would be difficult to detect by a user. The paper was first reported by Bleeping Computer based on a recent presentation at the USENIX conference in Vancouver, Canada.  The researchers have set out the alerts raised and bugs found by BootStomp's taint analysis, with time in minutes and seconds and memory in MB. Image: University of California, Santa Barbara/USENIXPrevious and related coverageGoogle issues anniversary Android patch - and Qualcomm bugs dominate Google's 13th monthly Android patch puts a spotlight on all the bugs outside the core operating system. Android lockscreen bypass: Google patches flaw on Nexus 5X phones Google has fixed a bug affecting the Nexus 5X that allowed an attacker to extract information from a device, even if it was locked. More on security |
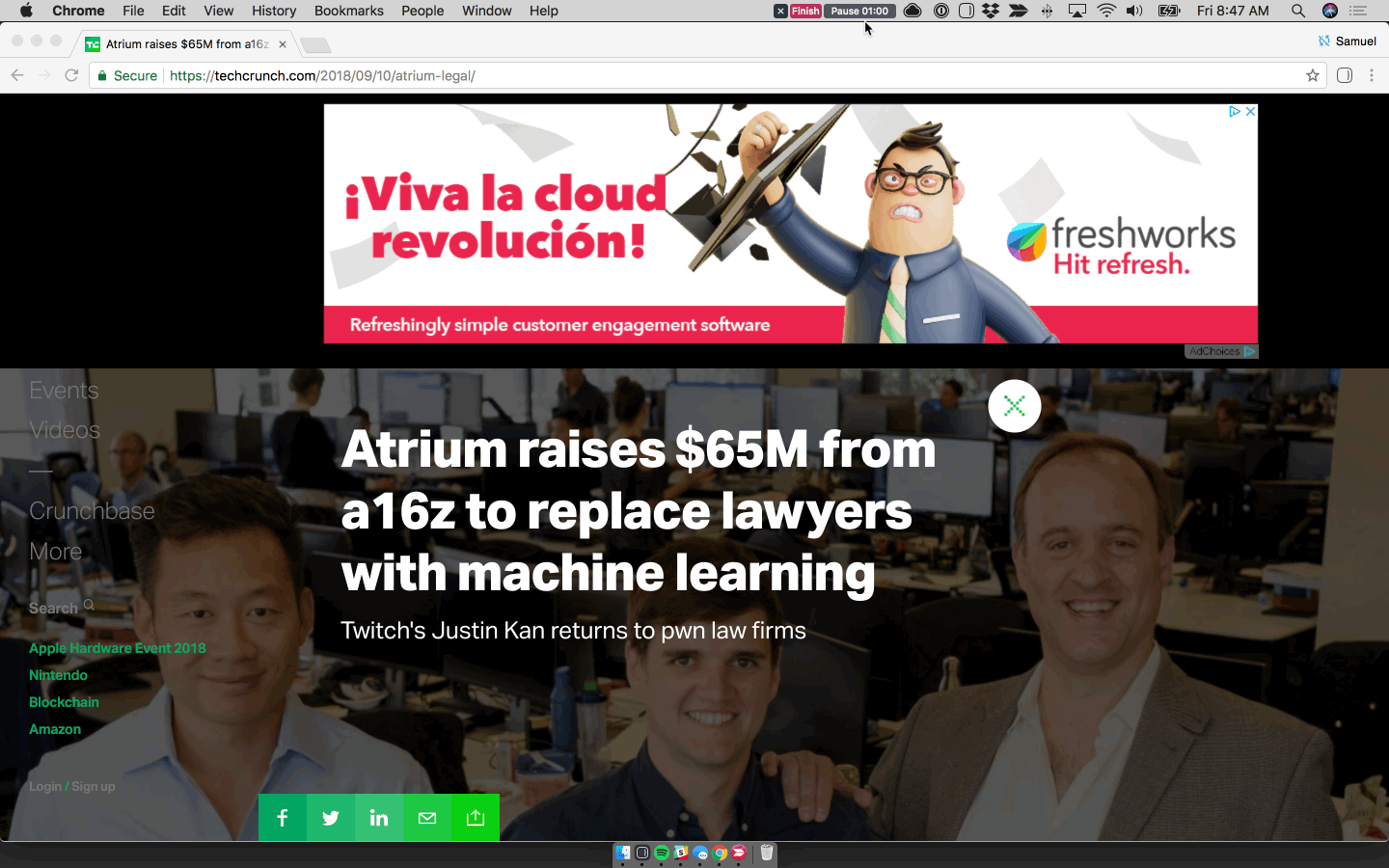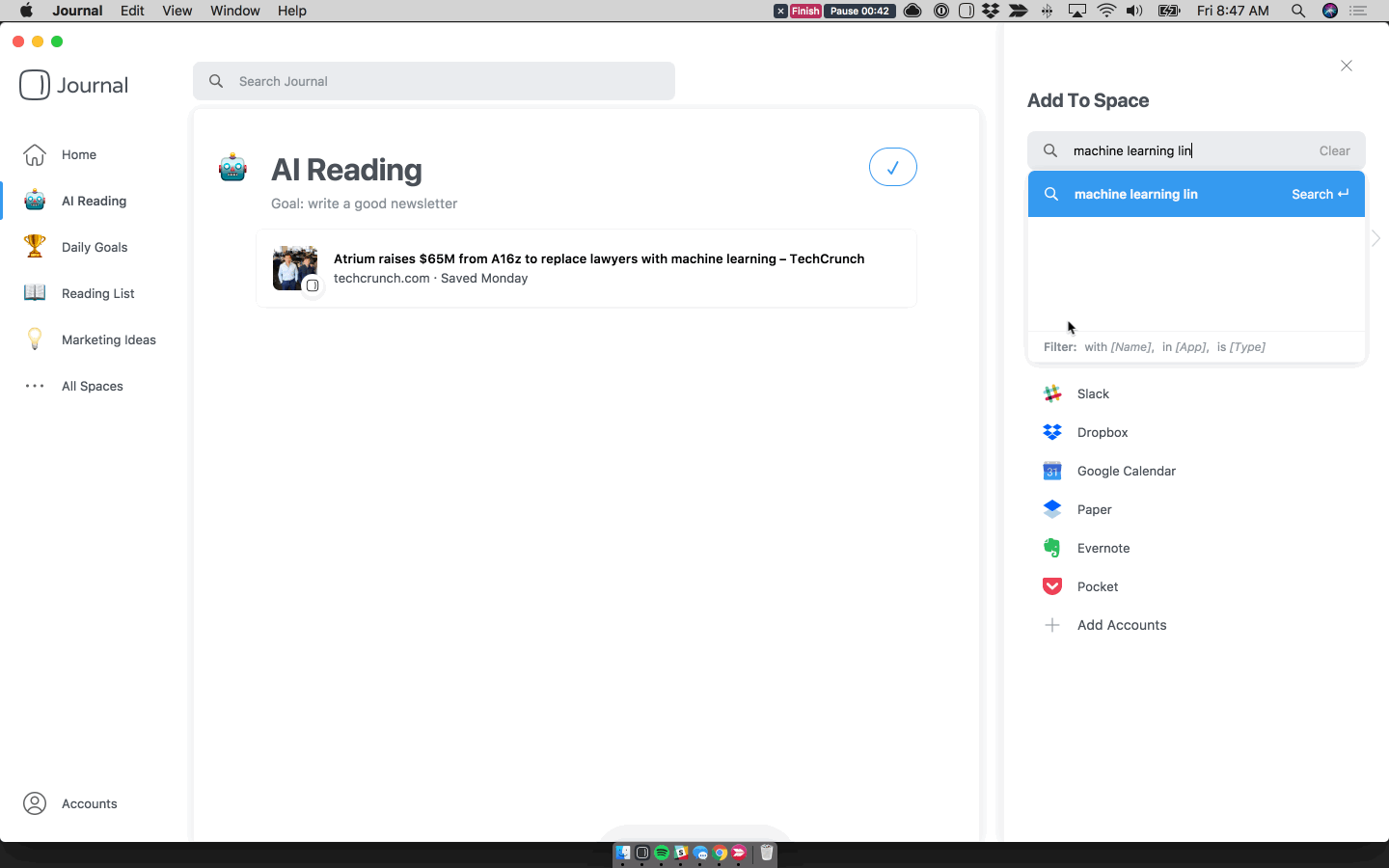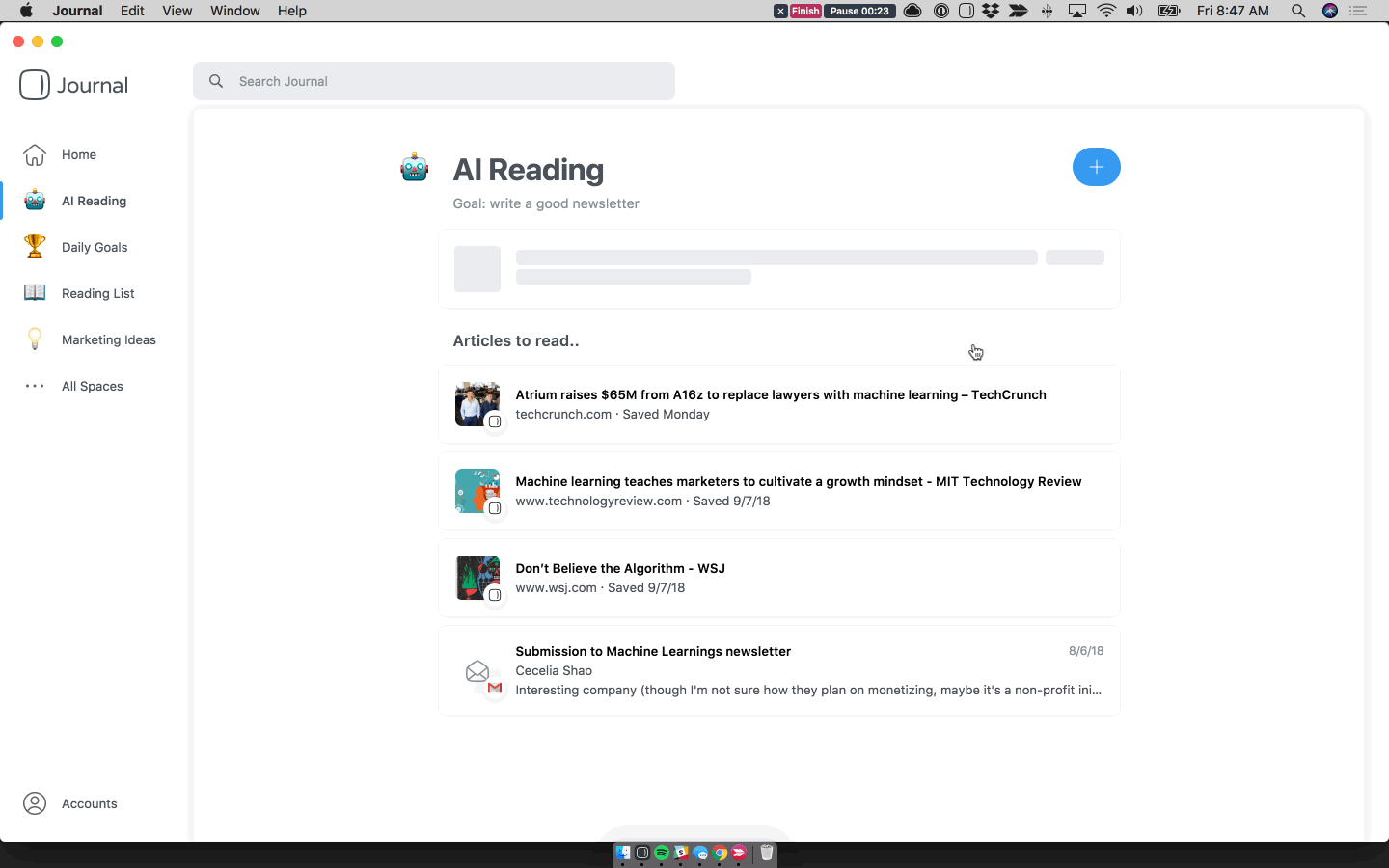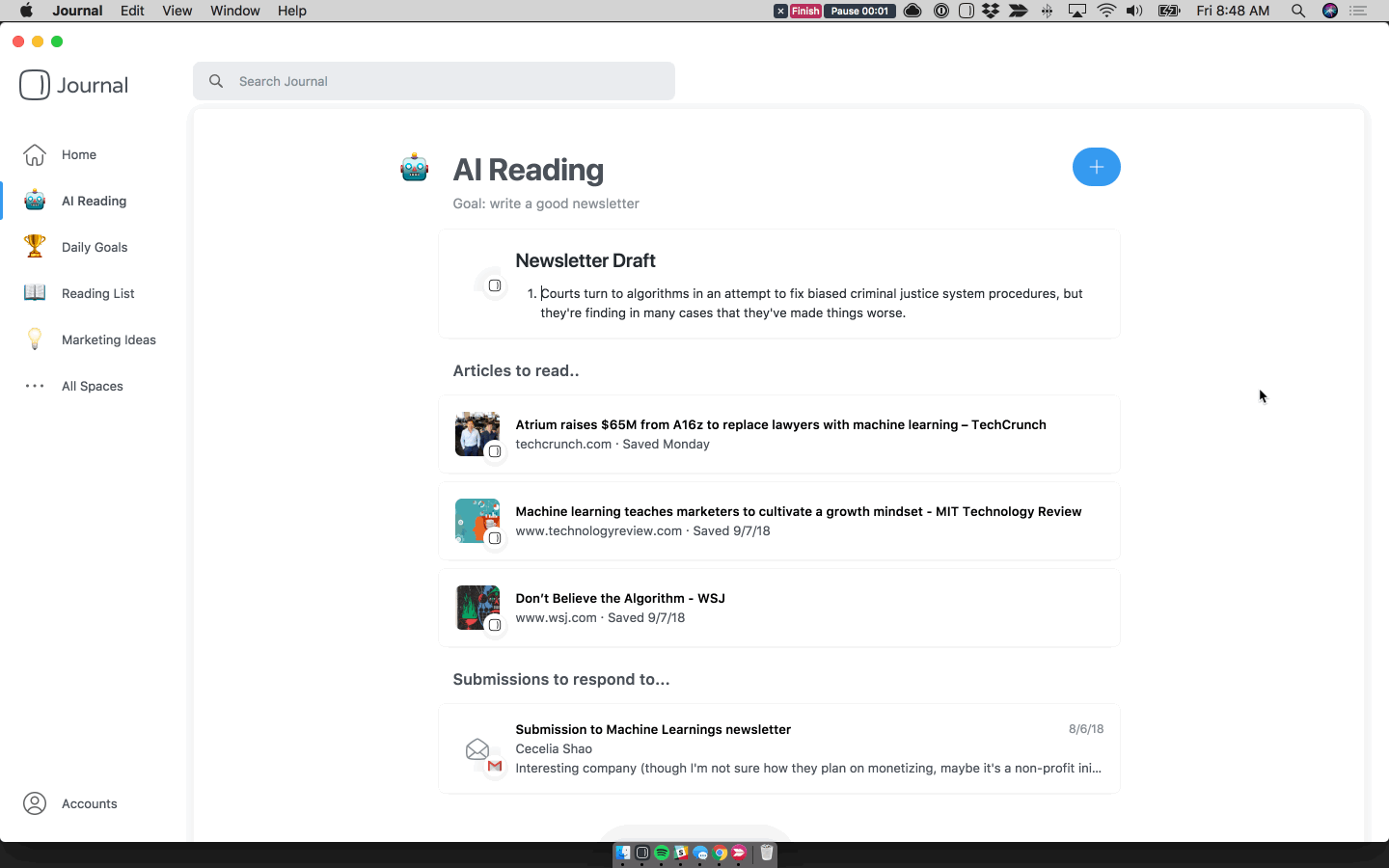
| Journal raises $1.5 million to bring Google-like search to your personal life - TechCrunch Posted: 16 Oct 2018 06:11 AM PDT In today's world of Slack, email and a gazillion other web apps and services, it's become increasingly hard to search for information. Did your boss Slack you or email you that information about your bonus? Or did they share it via a Google Doc? Who knows? Clearly not you, but Journal knows. Journal, a machine learning and natural language processing-powered platform designed to search across all your web services and tools, today announced a $1.5 million seed round led by Social Capital. Since receiving the funding about a year ago, Journal has been able to launch a beta community of users. Today, Journal is publicly launching its Mac app, web app and Chrome extension. "We're passionate about helping people use information effectively," Journal co-founder and CEO Samiur Rahman told TechCrunch. "In this case, we want to help people manage their knowledge. So we want to help individuals to leverage all of the places that they have information right now." It was that thesis that led Rahman and his team to land on wanting to build a suite of tools that "acts as a second brain for people. That's obviously a long way away but that's what our long-term vision is."
Based on the demo Rahman showed me, Journal looks pretty darn useful. I had an opportunity to install it, but I was hesitant to do so. That's because Journal requires viewing permissions to your email, apps and other services with which you sync Journal. That's scary for a couple of reasons — the main one being privacy. For example, what happens if Journal gets hacked? Or if the government requests data from Journal? Well, Journal uses zero-knowledge encryption that ensures Journal employees can't read or decrypt the information of the user. Here's a bit more information on how Journal handles security:
I'm not a security expert, so I asked my colleague, TC Security Editor Zack Whittaker, for some insight. He told me Rahman's explanation makes sense, further explaining that what Journal does is essentially split the private keys needed to access your data. Whittaker said that's smart, but that he's more concerned about general trust. Journal has access to a treasure trove of data — much of which would be very valuable to advertisers. Right now, advertising is not part of Journal's revenue plans, but that could change. "I can't say for certainty that we won't, but I think ad-based revenue ends up creating some really bad incentives, especially when you've got all this really private data about people and their usage patterns. The very likely route is that we end up going through companies that pay for teams to use." As with most tech products these days, it comes down to how much do you trust the company and how much do you care about your data? And depending on who you are, you may have a stronger threat model — that is, what threats you face based on who you are. Black communities, for example, are at a greater risk of surveillance by the government than white communities. So you adjust your behavior based on your personal threats. Privacy concerns aside, Journal looks like a really useful product. But we'll see if I get around to setting it up. |
| You are subscribed to email updates from "best encryption software,google phone encryption,huawei p8 encryption" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment