IBM completes successful field trials on Fully Homomorphic Encryption - Ars Technica
IBM completes successful field trials on Fully Homomorphic Encryption - Ars Technica |
| IBM completes successful field trials on Fully Homomorphic Encryption - Ars Technica Posted: 31 Jul 2020 03:45 AM PDT 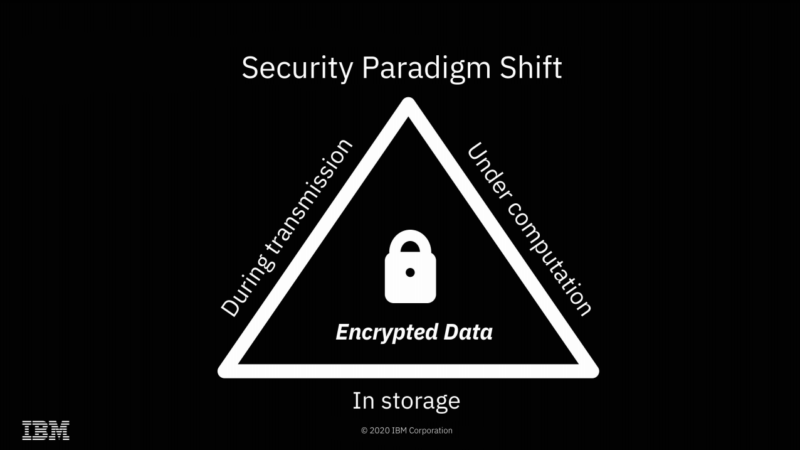 Enlarge / We're already accustomed to data being encrypted while at rest or in flight—FHE offers the possibility of doing computations on it as well, without ever actually decrypting it. Yesterday, Ars spoke with IBM Senior Research Scientist Flavio Bergamaschi about the company's recent successful field trials of Fully Homomorphic Encryption. We suspect many of you will have the same questions that we did—beginning with "what is Fully Homomorphic Encryption?" FHE is a type of encryption that allows direct mathematical operations on the encrypted data. Upon decryption, the results will be correct. For example, you might encrypt You don't ever have to share a key with the third party doing the computation; the data remains encrypted with a key the third party never received. So, while the third party performed the operations you asked it to, it never knew the values of either the inputs or the output. You can also ask the third party to perform mathematical or logical operations of the encrypted data with non-encrypted data—for example, in pseudocode, Homomorphic Encryption possibilities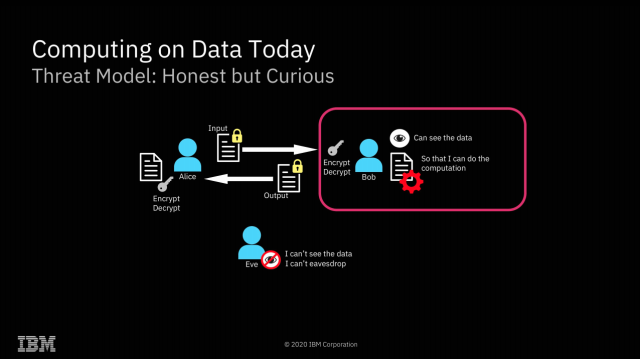 Enlarge / The most obvious application of FHE is solving what I like to call "the sysadmin problem"—preventing secret discovery by root-privileged operators. The most obvious implication of FHE is a solution to what I like to call "the sysadmin problem"—if you do your computation on a system managed by a third party, the root-privileged operators at the third party generally have access to the data. Encryption at rest prevents access to the data outside the scope of whatever computation is going on at that specific moment—but with root privileges, a system operator can scan or alter the contents of RAM to gain access to whatever data is currently being operated on. With FHE, you can perform those calculations without the actual data ever being exposed to the remote system at all. Obviously, this solves the sysadmin problem pretty thoroughly—when the machine itself never has access to the decrypted data, neither do its operators. Of course, FHE isn't the first solution to the sysadmin problem—AMD's Secure Encrypted Virtualization is another, and it's considerably more efficient. With SEV enabled, an operator who has root privilege on a host system can't inspect or meaningfully alter the contents of RAM in use by a virtual machine running on that system. SEV is, effectively, free—SEV-protected VMs don't operate any more slowly than non-protected VMs do.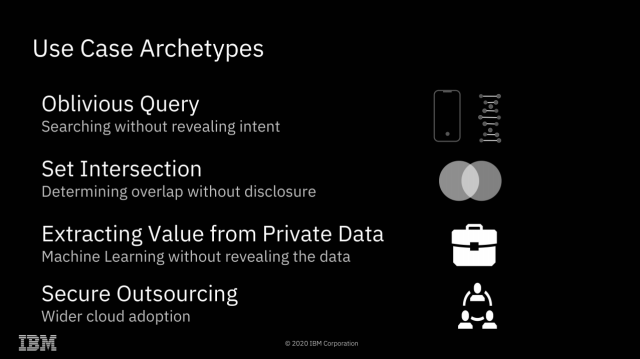 Enlarge / It's hard to come up with all the possibilities of fully homomorphic encryption off the top of your head—so here are a few to get us started. Fully Homomorphic Encryption offers many possibilities that Secure Encrypted Virtualization does not, however. Since all mathematical and logical operations can be built from additive and multiplicative operations, this effectively means that any computation can be performed upon FHE encrypted data. This opens a dizzying array of possibilities: one might search a database without ever letting the database owner know what you searched for or what the result was. Two parties might discover the intersection set of their separately held datasets without either party revealing the actual contents of their data to the other. "Secure outsourcing" is the only one of these archetypes that is possible without Fully Homomorphic Encryption. It's worth spending most of our time focusing on the other three, which do require it—because FHE comes at a significant cost. Homomorphic Encryption limitations
Although Fully Homomorphic Encryption makes things possible that otherwise would not be, it comes at a steep cost. Above, we can see charts indicating the additional compute power and memory resources required to operate on FHE-encrypted machine-learning models—roughly 40 to 50 times the compute and 10 to 20 times the RAM that would be required to do the same work on unencrypted models. In the next image, we can see that the result curves of a machine-learning prediction task are very nearly identical whether the operations were done on data in the clear or on FHE-encrypted data. We wondered about the remaining difference—was FHE a little bit lossy? Not exactly, Bergamaschi explained. The model in use is based on floating-point data, not integer—and it's the floats themselves that are a little lossy, not the encryption. Each operation performed on a floating-point value decreases its accuracy a little bit—a very small amount for additive operations, and a larger one for multiplicative. Since the FHE encryption and decryption themselves are mathematical operations, this adds a small amount of additional degradation to the accuracy of the floating-point values. We should stress that these charts are only directly applicable to machine learning, and not every task lending itself to FHE is a machine-learning task. However, other tasks present their own limitations—for example, we spent some time going back and forth over how a blind search (one in which the search operator knows neither what you searched for nor the result it gave you) could work. Normally, if you query a database, the database doesn't need to do a full text search on every row in the table(s) being queried—the table(s) will be indexed, and your search can be tremendously accelerated by use of those indices. If you're running a blind search using an FHE-encrypted value, however, your encrypted query must be masked against every full-text row in the queried table(s). In this way, you can both submit your query and get your result without the database operator possessing knowledge of either—but that full-text read and masking operation against every single row in the queried tables won't scale very well, to say the least. How much of a problem this is depends greatly on the type of data being queried and how much of it there is—but we're probably looking at machine learning's 50:1 compute penalty and 20:1 memory penalty all over again, if not worse. Successful field trials
As daunting as the performance penalties for FHE may be, they're well under the threshold for usefulness—Bergamaschi told us that IBM initially estimated that the minimum efficiency to make FHE useful in the real world would be on the order of 1,000:1. With penalties well under 100:1, IBM contracted with one large American bank and one large European bank to perform real-world field trials of FHE techniques, using live data. The American trial involved was based upon using machine-learning models to predict the likelihood of a loan being issued and given access to retail banking, loan, and investment information for a large group of customers. The dataset consisted of 364,000 entries, with several hundred features—and the model needed to identify relatively rare events (about 1 percent) in the dataset. Success for the trial was based on the encrypted predictions having similar accuracy to baseline, variable selection with similar accuracy, and acceptable compute overhead. We don't have as much detail about the European study, as it's still under NDA—but the results of the American study were published in 2019 and can be viewed in detail at the Cryptology ePrint archive. IBM's Homomorphic Encryption algorithms use lattice-based encryption, are significantly quantum-computing resistant, and are available as open source libraries for Linux, MacOS, and iOS. Support for Android is on its way. |
| Android Phones Might Be More Secure Than iPhones Now - OneZero Posted: 14 Jul 2020 12:00 AM PDT What the market for zero-day exploits tells us about our phonesIn all the heated debates between iOS and Android fanboys, privacy is not a war that Android often wins. Apple's walled garden approach to apps has its problems, but Google Play has historically been flooded with unsafe apps. The open source nature of Android has given hackers leeway to find security loopholes, and there's still has no default encrypted messaging app on the platform. Plus, less than 10% of Android users have updated to the latest version of the OS. In other words, nearly all its users run outdated software which almost certainly has bugs and security loopholes. Apple, meanwhile, puts the spotlight on its privacy centric features at every opportunity it gets. Its well-enforced App Store guidelines have weeded out millions of unsafe apps and the company's regular OS updates are quickly installed by most of its users. Apple's encrypted messaging app, iMessage, and its famous blue bubbles are now a status symbol, and the company's opposition to creating back-door access for law-enforcement agencies is headline-grabbing news that reinforces its image as the protector of your privacy. But things could be changing. By studying the market for iOS and Android zero-day exploits, we can get a decent idea of the security of each platform. A zero-day (0-day) is a vulnerability in a software or hardware that has been discovered but not yet patched. These pose a severe threat because they can be exploited to spread malware, steal sensitive data, take control of the targeted device, or worse. It gets its name from the fact that the vendor had zero days to issue an update to fix the vulnerability. Antivirus, firewall, and other security features are ineffective against them, making them powerful weapons and lucrative commodities. "The zero-day market is based on supply and demand, a spike in supply of zero-day exploits for a specific product means that the security level of that product is decreasing and the price goes down as there are too many exploits available," Chaouki Bekrar, founder of the well-known exploit acquisition platform Zerodium told the website SecurityWeek. "Obviously, we cannot draw a final conclusion about the overall security level of a system just based on its bug bounty price or the number of existing exploits, but these are very strong indicators that cannot be ignored." Zerodium lists the maximum payouts for different types of exploits on its website. Historically, iOS exploits have been valued much higher because they are harder to find. In January 2019, for example, Zerodium offered up to $2 million for an exploit that can lead to iOS jailbreak with zero clicks (no interaction from the target user) and $1.5 million for an exploit that requires one click. Meanwhile, the maximum payout for an Android exploit was capped at $500,000. But in September, Zerodium made a surprise announcement in which they increased the maximum payout for Android exploits to $2.5 million. For the first time, they were paying more for Android hacks than iOS hacks. They also decreased the payout for some iOS exploits. This could either mean that Android is getting more secure and vulnerabilities are harder to find, or that a disproportionate attention to iOS exploits over the years has increased its supply and depressed its prices. In a message to Wired, Bekrar confirmed that it is a bit of both. "Android security is improving with every new release of the OS thanks to the security teams of Google and Samsung, so it became very hard and time-consuming to develop full chains of exploits for Android and it's even harder to develop zero-click exploits not requiring any user interaction." But on the other hand, he writes, "During the last few months, we have observed an increase in the number of iOS exploits, mostly Safari and iMessage chains, being developed and sold by researchers from all around the world. The zero-day market is so flooded by iOS exploits that we've recently started refusing some of them." Maor Shwartz, an independent vulnerability researcher who also spoke to Wired, agreed. He says that the majority of the targets are Android users, but the number of vulnerabilities is lower because a lot of those vulnerabilities have been patched. "Every researcher I've talked to, I've told them, if you want to make money, go focus on Android," said Shwartz. Shwartz also says that the reason Android vulnerabilities are more valued is because it's harder to find a browser vulnerability in Chrome than Safari. That, combined with the difficulty of finding something called a "local privilege escalation exploit, makes Android a difficult target. Previously, this exploit was only hard to find in iOS, but recent security improvements have made it rare in Android as well. Over the years, Google has also been silently strengthening Android by adding new file-based encryptions, modifying what resources an app can access and how, and adding mitigations to make hacking harder even with zero-day exploits. If you're interested in learning more about this, watch Android's principal software engineer, Narayan Kamath, go over the privacy features of the upcoming Android 11 in this video. Ironically, Shwartz credits these improvements to Android's open source approach. For many years, the better security in Apple devices was attributed to its closed nature. The glut of iOS exploits was once again exposed this year when Zerodium announced in May that it was temporarily stopping purchases of certain iOS exploits and reducing the prices it would pay on many other iOS exploits due to a high number of submissions. After the announcement, Zerodium CEO Bekrar followed up with a blunt tweet: "iOS security is fucked . . . Let's hope iOS 14 will be better." However, Ryan Naraine, directory of security strategy at Intel, dismissed the announcement as "pure PR/marketing shenanigans," reminding us that Zerodium's claims need to be taken with a grain of salt. A lot about the company is still unknown, including the list of buyers it sells to and the exact prices it paid to acquire zero-days in the past. Nevertheless, there are other sources that corroborate Zerodium's observations. In an interview with SecurityWeek, Zuk Avraham, founder of mobile security firm Zimperium, also confirms the decrease in prices of iOS exploits. He adds: "Large portions of iOS code were not touched for years, it is a known secret that many of the vulnerabilities aren't patched properly, and in general, there are many vulnerabilities in iOS — much more than what most people think or are aware of." Many of these vulnerabilities were exposed by researchers working for Google's Project Zero in August 2019. They found five severe exploit chains that affected iPhones running nearly every version of iOS from iOS 10 to iOS 12, the latest at the time. Another researcher who goes by the name axi0mX discovered an unfixable zero-day vulnerability in the iPhone bootrom. This zero-day resulted in an exploit dubbed "checkm8" that allows jailbreaking of iPhones from the 4S to the X. The developers of the popular jailbreaking tool UnC0ver took this even further and released a new jailbreaking tool that works on iPhones running iOS 13.5, the latest version until the first week of June when Apple released an update with a patch. This jailbreak exploits a zero-day bug in the kernel. Adding to this list is an often overlooked aspect of iOS privacy: the lack of end-to-end encryption on iCloud. That means that while Apple can refuse to help law-enforcement agencies in unlocking a phone because it does not have the means to decrypt it without creating a back door, it cannot say the same when the FBI asks for a person's iCloud backup. Apple is required to turn over data from iCloud if law enforcement requests it because Apple has the ability to decrypt the data. Meanwhile, the latest Android devices support fully encrypted backups, making it all the more harder for anyone to access your data. Atlanta-based Grayshift and Israel-based Cellebrite sell tools to law-enforcement agencies around the world that the agencies can use to unlock and extract data from password-protected phones. These companies exploit zero-days to bypass the limitations on the number of password attempts, allowing them to try different passcode combinations without getting locked out of the device. They also have exploits that allow the extraction of data from these phones. The FBI recently used a Grayshift product to unlock an iPhone 11 Pro Max, Apple's most advanced iPhone. The agency frequently works with Cellebrite too, and is speculated to have used its services in 2016 to unlock the iPhone of the San Bernardino shooter, the incident that led to the famous court battle between Apple and the FBI over encryption. However, the Washington Post reports that the FBI unlocked the device by paying a professional hacker for another iOS zero-day instead. In a series of tests, the National Institute of Standards and Technology (NIST) compares the services offered by these companies. According to Vice, the tests found that Cellebrite's UFED tool is capable of fully extracting a vast trove of information from an iPhone X, including GPS data, call logs, contacts, and messages. It was also successful at extracting data from apps like Instagram, Snapchat, and Twitter, among many others. But NIST found that the same capabilities did not extend to the latest Android devices. On devices like the Google Pixel 2 and Samsung Galaxy S9, the tools could not extract GPS, browsing history, and social media data. It also wasn't able to extract any data from the Huawei P20 Pro. "Right now, we're getting into iPhones. A year ago we couldn't get into iPhones, but we could get into all the Androids. Now we can't get into a lot of the Androids," Detective Rex Kiser told Vice. Kiser is in-charge of digital forensic examinations at the Fort Worth Police Department. But since these tests were conducted, Cellebrite has updated the capabilities of its tools and it appears to be better at extracting data from the latest Android devices. There are companies and federal agencies that can find a way to crack iOS and Android devices; it's only a matter of how hard it is. Cellebrite is getting better at getting into Android, but it's still a harder target, meaning that it's now easier to find zero-days to exploit on iOS devices than Androids. Grayshift, on the other hand, currently only works on iOS devices, but the company is planning to make a tool for Android as well. Another sign of an increased demand for Android exploits. While it might look like Android is becoming safer than iOS, most of the new security features are only present in the latest Android versions and smartphones, and most Android users don't have the latest versions of the software or the hardware. While nearly 70% of all iPhone users run the latest version of iOS, less than 10% of Android users can claim the same. Moreover, when a zero-day is discovered and a patch is issued, users must update their phone to apply the patch. Apple can easily send updates to iOS devices because Apple doesn't have to deal with multiple hardware manufacturers (Samsung, OnePlus, Huawei, etc) like Google does. The updating process is relatively automated as well. Although Google is also working to deliver security updates in a similar fashion, it still has some way to go before many of its users catch up to the latest version of Android. Until then, Android's superior security, if it exists at all, will only be available to a meager percentage of its users. |
| You are subscribed to email updates from "encryption of android phone,how to decrypt android phone,your phone is encrypted" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment