The Case Against Full-Disk Encryption - LinuxInsider.com
The Case Against Full-Disk Encryption - LinuxInsider.com |
- The Case Against Full-Disk Encryption - LinuxInsider.com
- How to create and mount virtual disks on Windows 10/7 PC with most lightweight tool - H2S Media
- IBM completes successful field trials on Fully Homomorphic Encryption - Best gaming pro
- The best VPN service for 2020 - CNET
- Data Privacy Concerns for Distance Learning - Study Breaks
| The Case Against Full-Disk Encryption - LinuxInsider.com Posted: 27 Jul 2020 04:00 AM PDT [unable to retrieve full-text content]The Case Against Full-Disk Encryption LinuxInsider.com |
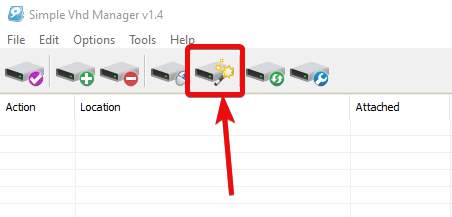
| How to create and mount virtual disks on Windows 10/7 PC with most lightweight tool - H2S Media Posted: 30 Jul 2020 11:28 PM PDT If you deal with virtual machines, you might already know about virtual storage devices that can be created manually by you for certain requirements. If you need to encrypt certain files and folders on your system but not the entire to volume or partition, you can create a virtual storage device, but the files and folders in that, and then eventually encrypt the virtual storage device so that you can easily share the encrypted volumes with others safely. There can be a number of other circumstances when it can really be useful to create a virtual drive, and talking about Windows, you can easily mount a virtual drive if you have one supported virtual storage device on your system. However, if you want to create a virtual storage device, you need to use some third-party program, and that said, today I will talk about one of the best and most lightweight programs that can not only help you to create virtual drives of any size and any format, but you can also use the program as a handy shortcut to mount those virtual drives on your system running Windows. This is going to be easier than you can think of and today and talk about how to use this simple yet powerful program on your computer. If you can use encryption software like VeraCrypt along with the software that I will talk about, you can easily encrypt all your virtual storage devices easily. So, without any further delay, let's get started with how you can create and manage virtual storage devices on your Windows computer in the easiest way with the most lightweight software available on the internet. Downloading VHD Manager Windows 10Step 1: The first step is to download Simple VHD Manager v1.4 by a developer called Sordum. This is a small portable program, and thus, you will not even need to install it on your computer. Step 2: After you have downloaded the program, it will come as a file named 'VhdManager.zip' within your default 'Downloads' folder. Step 3: Just open it, and extract the folder with the name 'VHD_manager_v1.4' to a folder to use the application on your system. Also see: Create Virtual Hard Disk on Windows without any third-party software. Creating a virtual disk using a VHD Manager applicationStep 1: Open the file with the name 'VhdManager.exe' or 'VhdManager_x64.exe' depending upon whether you are using a 32-bit or 64-bit version of Windows, and you can find both these files within the folder 'VHD_manager_v1.4'. Step 2: Now that the application is open, you can get started with creating a new virtual hard drive, or mount an existing virtual drive on your system. So, let's start with, how you can create a virtual hard drive using VHD Manager. Just click on 'File', and then click on 'Create and Attach VHD' or directly click on the 'Create and Attach VHD' in the toolbar, as shown in the screenshot below.
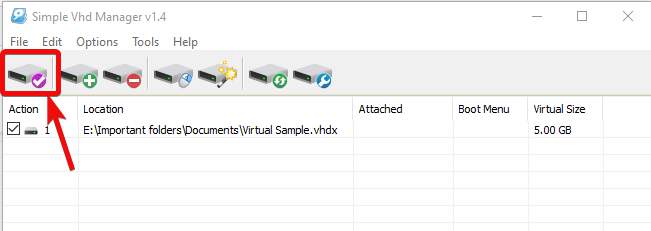
Step 3: Now, you will have to enter the size of the virtual drive, in either GB or MB, which you can select from the drop-down menu, and you can type in the space in the textbox corresponding to the drop-down menu. Step 4: Choose one between VHD and VHDX as the format for the virtual disk. Both VHD and VHDX will be supported by Windows, however, VHDX comes with some extra features like, the ability to create bigger volume, expand volumes, and much more. So, just choose the preferred format among the two. Step 5: You can also choose between 'Dynamically expanding' and 'Fixed'. With 'Dynamically expanding', the chosen size of the virtual drive will not be reserved at once, and the size will increase with adding more files to the virtual disk. But with 'Fixed', the storage space will be reserved in advance. 'Dynamically expanding' seems to be a more economical option. Step 6: Finally, click on 'Create and Attach VHD' after you are done with changing all the settings.
Step 7: Now, as usual, you will have to choose the location where you want to create the virtual disk and assign a name to it. After that, click on 'Save'. Step 8: The virtual disk will be attached to your system. You will instantly get the option to format the virtual disk in any format you want, and click on 'Start'. Just click 'OK' in the warning that appears.
Step 9: You can start using the virtual disk, and you can see the file in Windows Explorer, or within 'This PC'.
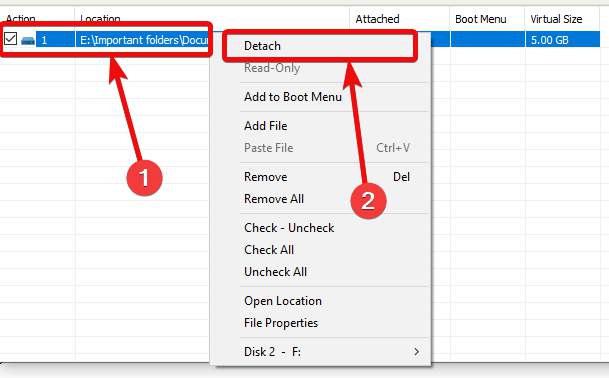
Step 10: After you are done with the virtual disk, you can now detach it from your computer, by clicking on the virtual disk in the list, and then by clicking on 'Detach'.
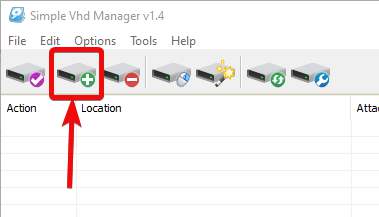
Attaching a virtual disk already createdStep 1: Now, if you have a virtual disk ready, you will first have to add the disk to the list before you can mount it on your system. Click on 'File' in the menu bar, and then click on 'Add File'. Alternatively, click on 'Add file to list' in the toolbar.
Step 2: Just select the file containing the virtual disk from the explorer window that comes up, and click on 'Open'.
Step 3: After it has been added to the list, click on 'Attach Marked Files' from 'File' in the menu bar or click on 'Attach marked and detach unmarked files' from the toolbar.
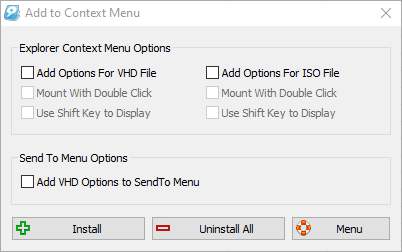
Now, the file will be mounted on your Windows computer as a disk. Other options Besides the options to create and mount virtual disks, VHD Manager also comes with some extra features, like the ability to open 'Disk Management' right from within the interface, by clicking on the button as shown in the screenshot below. You can also click on 'Add to Context Menu' to be able to deal with virtual disks through the right-click context menu.
You can find several useful options that can make it even easier dealing with virtual disks with the context menu shortcuts.
So, there are a number of options available within VHD Manager that can make it easier to deal with virtual disks on Windows computers. You can also trigger additional commands from within the interface, as well. You can explore the other additional options that can come in handy to you in a number of situations. So, that was all about, how you can deal with virtual disks in the easiest possible way on Windows computers. Do you have any questions? Feel free to comment on the same below. Read more: |
| IBM completes successful field trials on Fully Homomorphic Encryption - Best gaming pro Posted: 31 Jul 2020 05:54 AM PDT  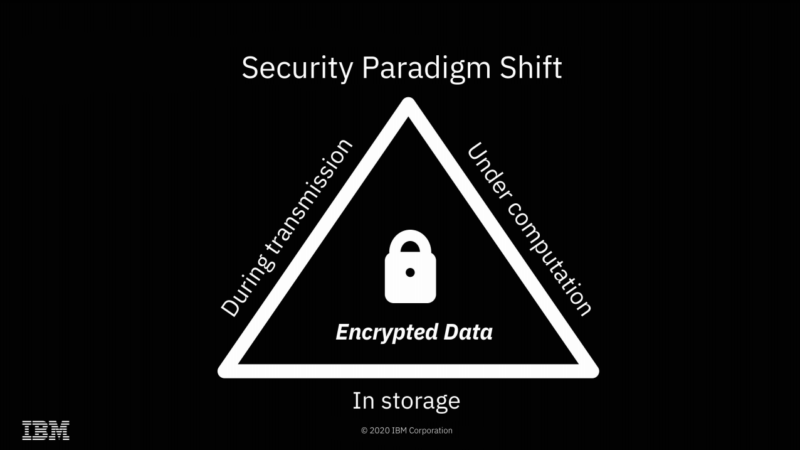 Enlarge / We're already accustomed to knowledge being encrypted whereas at relaxation or in flight—FHE gives the opportunity of doing computations on it as nicely, with out ever really decrypting it. Yesterday, Ars spoke with IBM Senior Analysis Scientist Flavio Bergamaschi in regards to the firm's current profitable discipline trials of Absolutely Homomorphic Encryption. We suspect a lot of you'll have the identical questions that we did—starting with "what is Absolutely Homomorphic Encryption?" FHE is a kind of encryption that enables direct mathematical operations on the encrypted knowledge. Upon decryption, the outcomes can be right. For instance, you may encrypt You do not ever must share a key with the third celebration doing the computation; the info stays encrypted with a key the third celebration by no means obtained. So, whereas the third celebration carried out the operations you requested it to, it by no means knew the values of both the inputs or the output. You can too ask the third celebration to carry out mathematical or logical operations of the encrypted knowledge with non-encrypted knowledge—for instance, in pseudocode, Homomorphic Encryption potentialities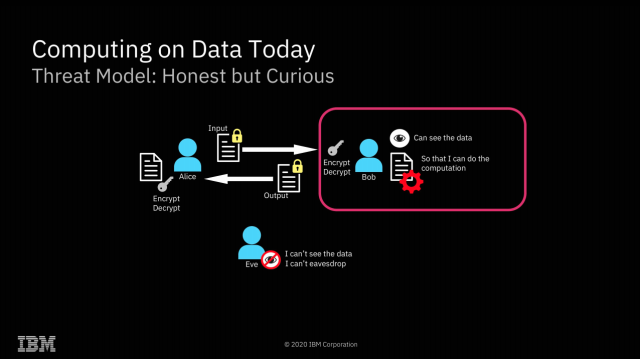 Enlarge / The obvious utility of FHE is fixing what I wish to name "the sysadmin drawback"—stopping secret discovery by root-privileged operators. IBM The obvious implication of FHE is an answer to what I wish to name "the sysadmin drawback"—in the event you do your computation on a system managed by a 3rd celebration, the root-privileged operators on the third celebration typically have entry to the info. Encryption at relaxation prevents entry to the info outdoors the scope of no matter computation is occurring at that particular second—however with root privileges, a system operator can scan or alter the contents of RAM to realize entry to no matter knowledge is at present being operated on. With FHE, you'll be able to carry out these calculations with out the precise knowledge ever being uncovered to the distant system in any respect. Clearly, this solves the sysadmin drawback fairly completely—when the machine itself by no means has entry to the decrypted knowledge, neither do its operators. After all, FHE is not the primary answer to the sysadmin drawback—AMD's Safe Encrypted Virtualization is one other, and it is significantly extra environment friendly. With SEV enabled, an operator who has root privilege on a number system cannot examine or meaningfully alter the contents of RAM in use by a digital machine working on that system. SEV is, successfully, free—SEV-protected VMs do not function any extra slowly than non-protected VMs do. 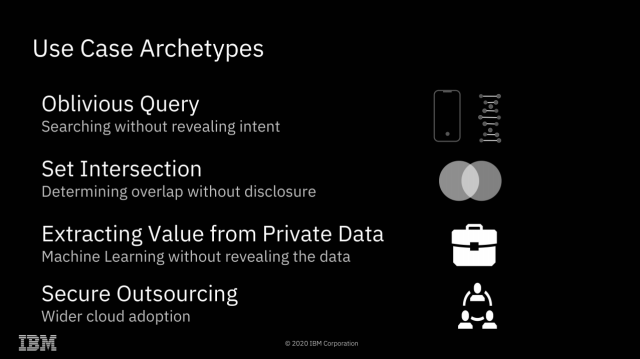 Enlarge / It is exhausting to give you all the probabilities of totally homomorphic encryption off the highest of your head—so listed below are just a few to get us began. IBM Absolutely Homomorphic Encryption gives many potentialities that Safe Encrypted Virtualization doesn't, nonetheless. Since all mathematical and logical operations could be constructed from additive and multiplicative operations, this successfully implies that any computation could be carried out upon FHE encrypted knowledge. This opens a dizzying array of potentialities: one may search a database with out ever letting the database proprietor know what you looked for or what the outcome was. Two events may uncover the intersection set of their individually held datasets with out both celebration revealing the precise contents of their knowledge to the opposite. "Safe outsourcing" is the one one in all these archetypes that's potential with out Absolutely Homomorphic Encryption. It is value spending most of our time specializing in the opposite three, which do require it—as a result of FHE comes at a major value. Homomorphic Encryption limitations
Though Absolutely Homomorphic Encryption makes issues potential that in any other case wouldn't be, it comes at a steep value. Above, we will see charts indicating the extra compute energy and reminiscence assets required to function on FHE-encrypted machine-learning fashions—roughly 40 to 50 occasions the compute and 10 to 20 occasions the RAM that will be required to do the identical work on unencrypted fashions. Within the subsequent picture, we will see that the outcome curves of a machine-learning prediction activity are very almost similar whether or not the operations have been finished on knowledge within the clear or on FHE-encrypted knowledge. We puzzled in regards to the remaining distinction—was FHE slightly bit lossy? Not precisely, Bergamaschi defined. The mannequin in use relies on floating-point knowledge, not integer—and it is the floats themselves which are slightly lossy, not the encryption. Every operation carried out on a floating-point worth decreases its accuracy slightly bit—a really small quantity for additive operations, and a bigger one for multiplicative. For the reason that FHE encryption and decryption themselves are mathematical operations, this provides a small quantity of further degradation to the accuracy of the floating-point values. We should always stress that these charts are solely instantly relevant to machine studying, and never each activity lending itself to FHE is a machine-learning activity. Nevertheless, different duties current their very own limitations—for instance, we spent a while going forwards and backwards over how a blind search (one through which the search operator is aware of neither what you looked for nor the outcome it gave you) may work. Usually, in the event you question a database, the database would not have to do a full textual content search on each row within the desk(s) being queried—the desk(s) can be listed, and your search could be tremendously accelerated by use of these indices. In the event you're working a blind search utilizing an FHE-encrypted worth, nonetheless, your encrypted question have to be masked in opposition to each full-text row within the queried desk(s). On this manner, you'll be able to each submit your question and get your outcome with out the database operator possessing data of both—however that full-text learn and masking operation in opposition to each single row within the queried tables will not scale very nicely, to say the least. How a lot of an issue that is relies upon tremendously on the kind of knowledge being queried and the way a lot of it there may be—however we're most likely taking a look at machine studying's 50:1 compute penalty and 20:1 reminiscence penalty yet again, if not worse. Profitable discipline trials
As daunting because the efficiency penalties for FHE could also be, they're nicely beneath the edge for usefulness—Bergamaschi instructed us that IBM initially estimated that the minimal effectivity to make FHE helpful in the actual world can be on the order of 1,000:1. With penalties nicely beneath 100:1, IBM contracted with one giant American financial institution and one giant European financial institution to carry out real-world discipline trials of FHE methods, utilizing stay knowledge. The American trial concerned was primarily based upon utilizing machine-learning fashions to foretell the probability of a mortgage being issued and given entry to retail banking, mortgage, and funding info for a big group of consumers. The dataset consisted of 364,000 entries, with a number of hundred options—and the mannequin wanted to establish comparatively uncommon occasions (about 1 %) within the dataset. Success for the trial was primarily based on the encrypted predictions having comparable accuracy to baseline, variable choice with comparable accuracy, and acceptable compute overhead. We do not have as a lot element in regards to the European research, because it's nonetheless beneath NDA—however the outcomes of the American research have been revealed in 2019 and could be viewed intimately on the Cryptology ePrint archive. IBM's Homomorphic Encryption algorithms use lattice-based encryption, are considerably quantum-computing resistant, and can be found as open supply libraries for Linux, MacOS, and iOS. Assist for Android is on its manner. In February, Microsoft revealed that it will be slowly phasing out Cortana performance in cell and different units, implying that the third-party Harman Kardon Invoke could be amongst them. On Friday, Microsoft clarified that these adjustments will happen in early 2021, together with the Invoke—however the firm will provide present playing cards of as much as $50 to sweeten the deal. Microsoft mentioned Friday that it's eliminating the third-party Cortana skills—Cortana plug-ins that could possibly be used to ask for a Fitbit exercise abstract, for instance—by September 7. In January, 2021, the cell Cortana app for iOS and Android will cease working. And in "early 2021," Microsoft says, the Cortana performance for the Invoke may also stop to exist. There's additionally yet one more, surprising change to Microsoft's system integration. Microsoft said it plans to take away many of the Cortana capabilities from the first-generation Floor headphones as properly. Microsoft has publicly shifted Cortana from the general-purpose assistant she was when Home windows 10 launched to a business-minded AI, or a "transformational AI-powered assistant expertise," as Microsoft now places it. Maybe extra importantly, Cortana is being repositioned not as an AI that powers Microsoft's Floor and different , however as a part of Microsoft's different companies. "Microsoft is on a journey to carry Cortana to Microsoft 365 experiences that will help you keep linked and productive—effectively and securely," the corporate defined it in one in every of its support documents describing the brand new adjustments. What Cortana going away means for the InvokeAndrew Shuman, the company vp in control of Cortana, informed PCWorld in Might that Invoke customers largely performed music, relatively than use it because the good speaker Microsoft initially envisioned. "With the Invoke, all we noticed with any reliability was taking part in music," Shuman mentioned. "And actually, it was 'play artist' or 'play style' as a result of folks can't keep in mind the precise option to say a track title or an album identify or any of this stuff." The adjustments to the Invoke will probably be made through a firmware replace that may roll out across the finish of January, 2021, Microsoft mentioned. That replace will take away the Cortana performance, however will probably be designed to transition the Invoke from a "good" to a "dumb" speaker—leaving all of its capabilities intact, however connecting through Bluetooth as a substitute.  Mark Hachman / IDG Mark Hachman / IDG The cool blue ring that signified that Cortana was on and listening will probably be one of many issues Microsoft removes from the Invoke. "The firmware replace will probably be delivered robotically to units linked to WiFi inside six months of its launch," Microsoft mentioned, not specifying what would occur if the Invoke wasn't linked to Wi-Fi for six months. "As soon as the Invoke is up to date, Cortana will now not be accessible on the system." The Invoke may be up to date additional through the Cortana System Setup app on Home windows 10. In any case, Microsoft mentioned it will provide a $50 present card to Invoke house owners, with one catch: You have to have triggered the Cortana performance after July 31, 2019, and earlier than Microsoft's announcement on Friday. If that's the case, you possibly can go to the Invoke/Cortana support page after which apply for a gift card at the redemption site. You'll want to produce the Invoke's MAC handle, which is printed on the underside of the unit. Floor Headphones lose Cortana, tooMicrosoft can be providing a $25 present card to those that purchased the first-generation Floor Headphones, with the identical proviso: You have to have used the headphones to launch a voice request after July 31, 2019, and earlier than as we speak's announcement. With the Headphones, the Cortana integration will probably be diminished, however not completely gone. In a support document, Microsoft describes the adjustments: When utilizing your Floor Headphones with Android and iOS units, you gained't be capable to activate Cortana by saying, "Hey Cortana," or by touching and holding the touchpad on both ear. That very same performance applies to Home windows 10 PCs operating the Might 2020 Replace. Nevertheless, you'll nonetheless be capable to contact and maintain the touchpad in your Floor Headphones or say, "Hey Cortana," to activate Cortana to do issues like examine your calendar, set a reminder, and add to your to-do lists.  Mark Hachman / IDG Mark Hachman / IDG Whereas the Floor Headphones' noise-cancelling expertise will stay, your capacity to speak to Cortana will probably be severely diminished. Likewise, as a result of the cell Cortana app is being retired, you gained't be capable to use it to replace the Headphones. The Floor Audio app (iOS, Android, Windows) will substitute it. Word: If you buy one thing after clicking hyperlinks in our articles, we could earn a small fee. Learn our affiliate hyperlink coverage for extra particulars. |
| The best VPN service for 2020 - CNET Posted: 31 Jul 2020 09:22 AM PDT If, like a lot of people, you're still working from home due to the COVID-19 crisis, remote VPN access is more important than ever. But in the increasingly expanding market for commercial virtual private networks, choosing the best VPN to suit your specific needs can be downright difficult. To help you make the right choice, we've sifted through the multitude of overhyped VPN providers touting their own private network to find the best VPN service for you. We'll be regularly updating this directory and keeping a close eye on how each VPN provider stands compared with its competitors, as well as any new VPN services that may hit the market. Because don't recommend free VPN services, this directory is packed only with paid commercial VPNs. In our current testing and ranking system, we looked at more than 20 factors, including price, security, bandwidth caps, ease of remote access, number of server locations, logging, client software, dedicated and dynamic IP, and customer support. To see exactly how we test and rate each virtual private network, check out our full evaluation walk-through. Let's look at each of our VPN vendors below in more depth. Keep in mind that this is an evolving list: It was originally published earlier and is constantly updated. We're actively working on more VPN testing and research, so expect this guide to change throughout the year as our virtual private network use continues and we put each VPN option through rigorous paces. ExpressVPN
ExpressVPN consistently proves itself one of the fastest VPNs on the market, and actively promotes its commitment to privacy. The company tells us its network is powered by TrustedServer technology, which ExpressVPN built to ensure that there are never any logs of users' online activities. In the privacy world, ExpressVPN has a strong track record, having experienced a server seizure by authorities which proved their zero-log policy true at the time. We also like the quality of the VPN's setup guides, and the detailed information in its FAQ. Like the rest of the top five VPN services we've reviewed for 2020, ExpressVPN offers a useful kill switch feature, which prevents network data from leaking outside of its secure VPN tunnel in the event the VPN connection fails. Unlike the others, though, ExpressVPN gained points from us for its support of bitcoin as a payment method -- something not all of our favorites offer, but which adds an additional layer of privacy during checkout. The company has been in business since 2009, and ExpressVPN has a substantial network of fast VPN servers spread across 94 countries. Its best plan is priced at less than $7 a month for an annual package, which includes three months free. Read more: ExpressVPN review: A VPN speed leader with a secure reputation Surfshark
While Surfshark's network is smaller than some, the VPN services makes it up on features. Let's start off with the biggest win it offers: unlimited device support. If you want to run your entire home or office on Surfshark's VPN, you don't have to worry about how many devices you have on or connected. It also offers antimalware, ad-blocking and tracker-blocking as part of its software. Surfshark received generally high marks when its Chrome and Firefox extensions were audited for privacy by German security firm Cure 53 (PDF link of full report) -- though that audit was commissioned by Surfshark. The company has a solid range of app support, running on Mac, Windows, iOS, Android, FireTV and routers. Additional devices such as game consoles can be configured for Surfshark via DNS settings. We particularly like the feature that allows you to whitelist certain apps and websites to automatically bypass the VPN. For some business uses, this can be critically important. Surfshark also offers three special modes designed for those who want to get around restrictions and more carefully hide their online footsteps. Camouflage Mode masks your VPN activity so your ISP doesn't know you're using a VPN. Multihop jumps your connection through multiple countries to hide your trail. Finally, NoBorders Mode "allows [you] to successfully use Surfshark in restrictive regions." Just be careful. Doing any of these three things could be illegal in your country and could result in severe penalties. During our testing, we saw no DNS or IP address leaks, and had no trouble accessing Netflix. For a year plan, Surfshark comes in close to many of the other full-featured VPN providers, at $72 for the first year. Be careful, because it looks like that will jump to $143 after your first year is up. Month-by-month plans are $12. Its best offer is $2 a month, for its 24-month plan (you pay $48 up front). Definitely take advantage of its generous 30-day trial to decide if you like this service (and maybe set a reminder in 23 months to see if you can talk it into a continued discount rate). Read more: Surfshark VPN review: A feature-rich service with blazing speeds and a security focus NordVPN NordVPN is one of the most recognized brands in the VPN field. It offers a generous simultaneous connection count, with six simultaneous connections through its network, where nearly all other providers offer five or fewer. NordVPN also offers a dedicated IP option, for those looking for a different level of VPN connection. NordVPN offers a kill switch feature, and the ability to VPN into Tor. We detected no privacy leaks during our tests, and found its speeds to be reliably fast. The company's one-year subscription plan costs is for $7 a month ($84 billed at once). While that yearly price is lower than most other contenders, the month-to-month price of $12 is at the high end of the spectrum. As of September 2019, the company's other pricing tiers have crept up a bit: It's now $3.49 a month for a three-year plan (or $125.64 total), up from $2.99/$107.55. And the two-year plan is now $4.99 a month ($119.76), up from $3.99/$95.75. And yes, it also has a full 30-day refund policy. While NordVPN has lived on this list for a long time, we moved it to the penalty box in October 2019 to re-evaluate our recommendation after a report emerged that one of its rented servers was accessed without authorization in 2018. Nord's actions following the discovery included -- eventually -- multiple security audits, a bug bounty program and heavier investments in server security. While we'd have preferred that Nord self-disclosed the issue much earlier, the fact that the breach was limited in nature and involved no user-identifying information served to further verify that NordVPN keeps no logs of user activity. As a result, Nord remains on this list as a recommended vendor. Read more: NordVPN review: Still the best value for security and speed IPVanish
A big win for IPVanish is its fun, configurable interface, which makes it an ideal client for those who are interested in learning how to understand what a VPN does under the hood. Its multiplatform flexibility is also ideal for people focused on finding a Netflix-friendly VPN. A unique feature of IPVanish, and one we're intrigued by, is the VPN's support of Kodi, the open-source media streaming app that was once known as XBMC. Any serious media fan has used or built Kodi or XBMC into a media player, and the integrated IPVanish Kodi plugin provides access to media worldwide. At $5 a month or $39 a year, IPVanish is obviously trying to move you towards its yearly program. We're a little disappointed that it only allows a seven-day trial, rather than a full 30 days, but it does offer a full money-back guarantee. That said, the company gets kudos for its recent increase from five to now 10 simultaneous connections. We also liked its connection kill switch feature, a must for anyone serious about remaining anonymous while surfing. Read more: IPVanish review: Get under the hood with this zippy VPN Norton Secure VPN
LifeLock, long known for excellence in security products, has a relatively limited offering in its VPN product. Norton Secure VPN does not support P2P or BitTorrent, it does not have a kill switch feature, and it does not support Linux, routers or set top boxes. Its Netflix and streaming compatibility is somewhat limited. Even worse, during testing, we experienced privacy-compromising data leaks. During CNET's testing, Norton Secure VPN speeds were comparable to other mid-tier VPNs but not particularly competitive. Although its VPN is only available on four platforms -- Mac, iOS, Windows and Android -- Norton gets big points for its 24/7 live customer phone support and 60-day money back guarantee. Read more: Norton Secure VPN review: More work is needed for this privacy product to shine Below you'll find additional VPNs. We're in the process of reevaluating them for 2020. PureVPN PureVPN does not log connection information. The company joined the "no log" movement in 2018, which was recently verified via a third-party audit by Althius IT (albeit one commissioned and paid for by PureVPN). We like that PureVPN offers a 31-day refund policy and supports Bitcoin payments, to further extend anonymous browsing. We also like that PureVPN has both Kodi and a Chromebook solutions available. In addition, PureVPN was the first VPN service we noted to fully implement the GDPR. StrongVPN StrongVPN blasts onto our favorites list with excellent infrastructure and decent price performance. As with our other favorites, StrongVPN has a strong no-logging policy. Since VPN is all about protecting your privacy, that's a place the savvy VPN providers can pick up points. Strong also picks up kudos for its large base of IP addresses, which also helps protect your anonymity. It has a solid collection of servers and worldwide locations. For those of you who need a dedicated IP, you can get one from the company, but you'll need to contact support to get help setting it up. One of StrongVPN's strongest strengths is the company's network. It owns and operate its entire network infrastructure, which means it has no externally dictated limits on bandwidth or the type of internet traffic allowed on the network. This gives you the confidence that you'll be able to power through your work. StrongVPN's regular monthly price of $10 is in the middle of the pack, but its yearly price of $70 is among the lowest of our contenders. CyberGhost VPN CyberGhost has been around since 2011 and has come out strongly as a supporter of "civil rights, a free society and an uncensored internet culture." We really liked how the company specifically showcases, on its website, how folks normally prevented from accessing such important services as Facebook and YouTube can bring those services into their lives via a VPN. The company has solid Linux support, supports VPN via routers, and has a solution for the popular Kodi media player. It checks off all the boxes on protocol support and gets kudos for offering a connection kill switch feature, along with supporting P2P and BitTorrent in most countries. Plus, it allows you to use seven devices at once with its service. The few extra dollars it costs are worth it. We liked how the company offers custom app protection, IPV5 support and DNS, IP and WebRTC leak prevention. CyberGhost also picked up points for preserving anonymity by not logging connection data. Private Internet Access
Speaking of price, if you want a solid VPN provider, Private Internet Access is the place to go. The key to getting the most savings with this vendor is buying its two-year plan for $83.87. That works out to $3.49 a month. It also offers a one-year plan for $71.88, but as you can see, you can get an entire additional year for less than 10 bucks if you sign up for its two-year plan. The company does not release information on the number of IP addresses available, but at 3,252, its server count is more than any of our other picks. These folks have been around since 2010, and don't log anything. It provides a generous five connections, a connection kill switch feature, and some good online documentation and security guidance. Our one disappointment is that its refund policy is seven days instead of 30, but you can certainly get a feel for its excellent performance in the space of a week. Hotspot Shield Hotspot Shield is a product that has had some ups and downs in terms of our editorial coverage. Back in 2016, it picked up some positive coverage based on founder David Gorodyansky's comments about protecting user privacy. Then, in 2017, a privacy group accused the company of spying on user traffic, an accusation the company flatly denies. Finally, in 2018, ZDNet uncovered a flaw in the company's software that exposed users. Fortunately, that was fixed immediately. So what are we to make of Hotspot Shield? Frankly, the controversy caused us to drop it from our directory for a while. But it approached us, made a strong case for its ongoing dedication to privacy, and we decided to give it another chance. Here's the good news. It offers one of the best money-back guarantee we've seen for VPN services, a full 45 days. It supports Linux, Windows, Mac, iOS and Android, along with plugins for Chrome and Firefox. It also supports routers and media players. And, as a bonus, it has a connection kill switch feature. The company does not support P2P or BitTorrent -- and it also doesn't support the OpenVPN. Every other vendor does, but Hotspot Shield limits its protocol support to L2TP/IPSec and something it calls Hydra, an enhancement of the transport protocol. Overall, the company did impress us with its attention to privacy. It has a published privacy canary. It also told us, "We have built in malware, phishing and spam protection. Our commitment to our users is that Hotspot Shield will never store, log or share your true IP address." Goose VPNI had to know why Goose VPN was so named. My first order of business was to reach out to the company's co-founder and ask. Geese, I was told, make excellent guard animals: There are records of guard geese giving the alarm in ancient Rome when the Gauls attacked; geese have been used to guard a US Air Defense Command base in Germany and a brewery in Scotland. It's clear that the goose is an ideal mascot for a service that's meant to guard your digital communications. And so, we have Goose VPN. Goose VPN has a couple of standout features. First, you can have an unlimited number of simultaneous connections (or devices) using the VPN at once. Second, if your bandwidth needs are 50GB or less per month, you can sign up for $2.99 a month, the cheapest monthly rate we've seen. If you want unlimited bandwidth, the company definitely is pushing you towards buying a year at a time. Its monthly fee for unlimited bandwidth is a middle-of-the-road $12.99 a month, but if you spend $59.88 for a year's service, you'll find it's the second lowest by-the-year price of the services we've reviewed. Goose provides all the usual clients, including iOS, Android, Mac and Windows, and adds support for routers, Android TV and Linux. It is working on a kill switch feature, which may even be up and running by the time you read this review. The company also offers 24/7 ticket-based support. Ducks quack, geese honk and swans whoop (we know, because we looked it up). Overall, especially given the unlimited connections and low yearly price, we think Goose VPN is something to honk about. VyprVPN Services
VyprVPN has the largest bank of IP addresses of any of the services we've examined. The company offers a wide range of VPN protocols, including its own high-performance Chameleon connection protocol. We like that the company offers a connection kill switch feature and, for those who need it, there's an option to get a dedicated IP address. VyprVPN is a standout in its effort to provide privacy and thwart censorship. When China began its program of deep packet VPN inspection, Golden Frog's VyperVPN service added scrambled OpenVPN packets to keep the traffic flowing. The company offers three plans: two years for $60, one year for $45, or monthly at $12.95. The company's two-year offering is the sweet spot.
|
| Data Privacy Concerns for Distance Learning - Study Breaks Posted: 31 Jul 2020 05:45 AM PDT Post Views: 228 Remote classroom learning has been around since the internet connected teachers with learners back in the 1990s. In the case of adult learners, online classes, less reliant on the lectures and teacher domination, are well suited to the self-motivated learning style of older students. With the coronavirus pandemic, more younger students have been forced away from the campus and toward their home laptops. Social closeness and collegial atmospheres have made way for social distancing and remote learning. For the fall 2020 college term, for example, more than 1000 universities cancelled their in-person classes in favor of moving everything online. So, with more students logging on to the internet, they provide a new and expanded set of targets for scammers, hackers, and thieves. Students at home are particularly vulnerable. Social distancing and home quarantine promote more social media activity. That increased activity leaves more profile footprints for those who want to steal identities, personal information and financial data. So, there are data privacy concerns home learners need to be aware of. The first is that anyone spending lots of time online should know how a VPN works. Essentially a VPN masks the user's online activity and presence to provide an extra layer of security and privacy. Next, online students need to practice common sense security to protect their devices and maintain academic integrity. The following are 7 suggestions online learners should follow in their quest to stay safe online: 1. Activate and maintain the device's built-in security systemBoth the Windows and Mac OS operating systems have solid security systems. The Mac OS has a firewall setting along with extra security measures that include hard drive encryption. The Windows Defender can protect the student against malware and common virus vectors.Even so, protecting against online predators requires extra attention. Immediately allow Windows and Mac OS updates and system patches. Those patches are fixes in response to recently discovered breaches. Install them the same day they arrive. Regardless of the operating system's built-in anti-virus tools, install commercial grade anti-malware like Norton and McAfee to keep up with the latest virus definitions and malware threats. 2. Employ a reliable and secure password strategyYou should block unauthorized access to your devices and their operating systems with reliable passwords. Those passwords must be hard to guess, but easy to remember. For example, you can protect your device with a password like @HIAuTMc2478. That password is an example of password phrasing with the symbols and first initials of this phrase: "Symbol At Home I Always use This Mac computer (last 4 digits of your telephone number)." It is 12-digits long, and has a combination of lower and upper case with symbols and numbers. It is hard to crack, but easy to remember. When you have settled on difficult to crack passwords, follow these additional security access steps: — Allow your computer to go into the sleep mode when unattended after 5-10 minutes. Require your device password to reactivate the display. — Allow your operating system to encrypt your hard drive. Both Mac and Windows have utilities to do that, and encrypting the hard drive will block unauthorized copying and disk imaging. — Use a password to protect your sensitive files. That extra protection is yet another way to secure your school work from hackers, thieves and plagiarizers. — Do not use the same password to access everything on line. In the case of those inevitable massive data breaches, your access credentials can be compromised and sold in the dark web. The compromise of a single password that accesses multiple sites can cascade exponentially. You can avoid the temptation to use just one password by using the Windows or Mac browser password utilities. You can also use a password manager to generate uncrackable passwords to automatically sign you into individual websites and accounts. — Employ multi-factor authentication. This is where you sign into a site with your regular password, but you must take an additional step to gain access. That step is commonly entering a numeric password you receive either by email or text message.— Don't give out your passwords. If you must share your computer, set up another user account for guests. 3. Always, always back up your workMac OS and Windows 10 have built-in backup utilities. Those utilities work best with an external storage device, and the user needs a basic knowledge of backup and restoring techniques. There are several alternative subscription cloud-based backup utilities that run in the background and require no special attention or settings. The best choice, regardless of the backup hardware tool, is a complete backup strategy that runs in the background, saves the student's work at least once per hour, and allows retrieval of a previous version of a saved file along a timeline. Anyone who has ever lost or overwritten a term paper file only needs to learn the backup lesson once. 4. Do not download copyrighted or otherwise illegal contentStreaming sites which provide pirated content and music are not only illegal, but they are also vectors of an unlimited range of malware and viruses. Avoid the temptation of downloading that recent blockbuster. Go the legal route and stay safe. 5. Protect your school emailIt is a bad idea to link every online account to a single school email address. For example, linking a Twitter or Facebook account to the school's financial portal is a bad idea for obvious reasons. Social media are magnets to scammers and hijackers, who exploit weaknesses in school accounts. They can access your transcripts, financial aid information and your class schedule. All that personal information is a treasure trove for anyone wanting to use fake identities on line. 6. Beware of phishing and social engineeringYou receive an email from someone with the subject line "You can get free school texts here." Sounds good, right? You open the mail and it has a link "Learn how here" or maybe what appears to be an image file that says "Open me now." If you click on either, you have fallen for a phishing scam. Click on that link or open that file and you could be infecting your computer with a virus, or you could be connected to a fraudulent web site that sends all kinds of grief to you and possibly your school network. Note: Check your email settings. You can set it to never download or allow HTML links to open when you view an email. It is actually possible to launch a virus simply by opening an email, especially if your email client allows scripting. 7. Don't post anything on line you wouldn't want your mother to readChat sessions or political discussions in classes can become a bit heated. It is tempting to send back an expletive-loaded angry response when someone pushes your buttons. That F-bomb you launched immediately becomes part of the class records. Or maybe you like to post partying photos on your Facebook account. What seemed like a hilarious picture of you drinking beer from a pitcher could come back to haunt you when applying for a job or internship later. 8. Avoid unprotected free Wi-Fi hot spotsSocial distancing notwithstanding, never log into an unprotected public network while in the open. While you're updating your student financial account and paying tuition with your credit card, someone at the other end of the coffee shop may be watching you and launching an MITM attack. MITM stands for "man-in-the-middle." Tech-savvy cyber criminals employ cunning tactics to get between you and your destination server/web site. Their tactics include: — Employing a "web pineapple" device to access unsecured networks. Like a scanner, the device shows the MITM the users who are vulnerable to attack. — Hijacking by deploying rogue Wi-Fi networks. You log into an unsecured public Wi-Fi network, and the MITM routes you to a fake network that begins scooping up the user's credentials and files. — Spoofing a realistic looking web app. The user logs in and the MITM takes over. — Sidejacking or stealing session cookies, which consist of unencrypted login information. You might be logging into your webmail account when the intruder intercepts the login cooker. Your webmail account is now compromised. — Installing software to "sniff out" online activity and intercept the data going to and from the unsuspecting users. The best protection from becoming a victim of an MITM attack is installing a VPN on your computer. As previously mentioned, the VPN hides the user's location and encrypts the data the user sends and receives. ConclusionMore students than ever before are taking advantage of remote learning. Home user's need to become cybersecurity conscious. That would include strengthening their computer's built-in security tools and employing a solid password strategy. Students should get into the habit of backing up all their work, all the time. Other measures include never downloading dangerous, illegal content, which can inject viruses and malware. Then there are phishing scams where innocent looking email can be loaded with dangerous links and files. Students should also protect their reputations and avoid posting profanity or compromising photos on line. Finally, never log into a public Wi-Fi hot spot without the protection of a virtual private network. Public Wi-Fi spots are hangouts for hackers and MITM perpetrators who employ cunning methods to steal data through a variety of clever ruses. Students should install a premium VPN service like Surfshark on their computers as a first line of defense against online threats. |
| You are subscribed to email updates from "encryption software,encrypted device memory,what happens when you encrypt your phone" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
















Comments
Post a Comment