Best encryption software for business in 2020: BitLocker, FileVault, Guardium, and more - ZDNet
Best encryption software for business in 2020: BitLocker, FileVault, Guardium, and more - ZDNet |
- Best encryption software for business in 2020: BitLocker, FileVault, Guardium, and more - ZDNet
- How Android 10 is making your phone more private and secure - The Next Web
- What if the FBI tried to crack an Android phone? We attacked one to find out - The Conversation US
| Best encryption software for business in 2020: BitLocker, FileVault, Guardium, and more - ZDNet Posted: 08 May 2020 12:00 AM PDT When mass data collection and big data analysis exploded on the technology scene, security and encryption, unfortunately, took a back seat. In a world where data breaches are commonplace -- involving everything from device theft to vulnerability exploitation and open AWS buckets exposed to the world -- businesses both large and small must now educate themselves and employ encryption software to enhance the data they have become controllers of. Encryption can help protect information stored, received, and sent. Readable information is scrambled through the use of encryption keys, algorithms that can sort through this text and return it to a readable format. Today, the Advanced Encryption Standard (AES) using 128- and 256-bit key lengths, the successor to DES, is in common use worldwide. If strong encryption and security practices are not in place, businesses are not only opening themselves up to potential cyberattacks, but also the loss of corporate and customer information, fines for non-compliance with laws including HIPAA and GDPR, financial damage, and the loss of reputation. Below, we list our favorite encryption solutions, suitable for users, SMBs, and enterprise players. Disclosure: ZDNet may earn an affiliate commission from some of the products featured on this page. ZDNet and the author were not compensated for this independent review. Free Best suited for: Windows users who need onboard device encryption Subscription Best suited for: Enterprise users who need flexible encryption across multiple environments IBM Guardium is a data protection platform that pulls together a suite of security tools in an effort to streamline data management and reduce vendor product disparity. Free Best suited for: Mac users who want on-device encryption. Subscription Best suited for: Protecting information on machines used by multiple individuals, collaboration Subscription Best suited for: Users who need strong encryption across multiple operating systems and the cloud Subscription Best suited for: Users that need enterprise-wide encryption Subscription Best suited for: Those who need end-to-end encryption for cloud storage services Subscription Best suited for: Users who require real-time management of encryption and applications Subscription TokenEx is an encryption offering that specializes in the management and security of financial data. What we look for in encryption softwareZDNet's recommendations are based on major themes: Strength, flexibility of use, and multi-device and OS support. |
| How Android 10 is making your phone more private and secure - The Next Web Posted: 04 Sep 2019 12:00 AM PDT Google released Android 10 last night to all Pixel phones. The update brings some nifty features like system-wide dark mode, a new gesture navigation system, and smart replies in notifications. But the release is actually focused on privacy and security upgrades; let's take a closer look at what's under the hood. Location restrictionsPrior to Android 10, you could only choose to allow individual apps to track your location all the time or never at all. Starting from this version, you can allow an app to track your location only when the app is in use. The apps will also have to ask explicitly if it needs background location access. 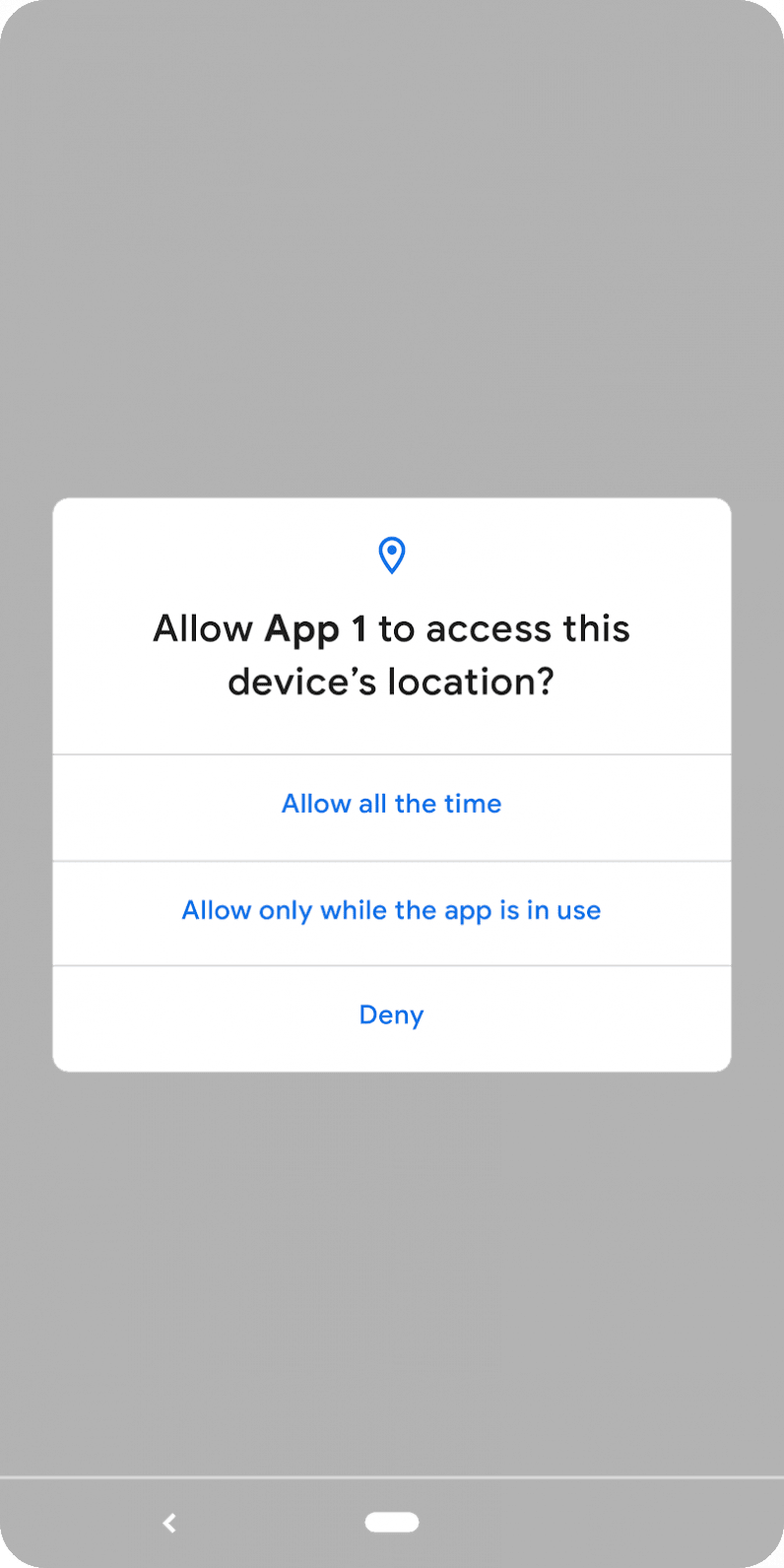 Google has followed Apple's implementation and for good reason. The iPhone maker upped the ante by introducing the "Allow once" option this year with iOS 13 for apps that need location access for a one-time authentication. I really hope Android implements this as an update or includes it in the next version. New changes indicate apps that scan for networks using location data will have better protection from snooping. Protection from device trackingWith Android 10, apps can't access sensitive device information such as device IMEI and serial number. Plus, the new Android version randomizes your MAC address by default when a device is connected to Wi-Fi. This effectively prevents apps from relaying sensitive identifying information about your device to remote servers, and reduces the chances of bad actors spying on you. Limiting app access to external storageGoogle is also limiting apps' access to their own folders in your device storage. That means an app can't access other folders stored in your SD card. It can still access media resources such as photos and videos thorugh a secured shared implementation. Android 10 also prevents apps from starting foreground activities and jumping in front of the queue. Instead, it'll force the app to run in the background or display only relevant notifications. There are a bunch of new privacy changes that restrict access to camera metadata and turning Wi-Fi on or off. You can check out all the changes here. Android 10 also offers a dedicated privacy screen in settings where you can manage your permissions, activity controls, and ad settings. Enterprise securityOn the enterprise side, Android 10 will allow IT managers to freeze updates for 90 days and manually push them to push them in the form of a consolidated file if there's some customization needed. Plus, admins can they can prevent the installation of apps from unknown sources when an employee is using a work profile. To increase security, apps can prompt users to create a stronger screen lock password if the requirements are not met. 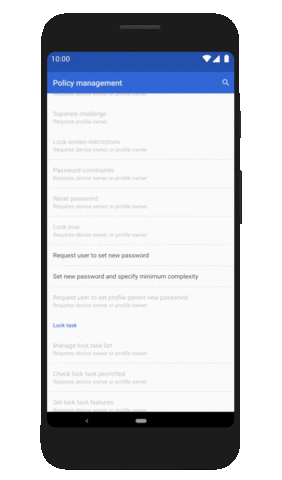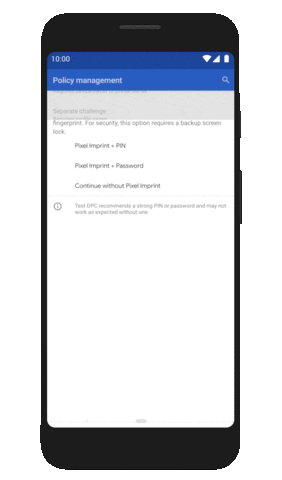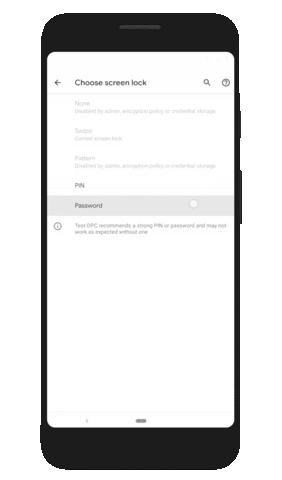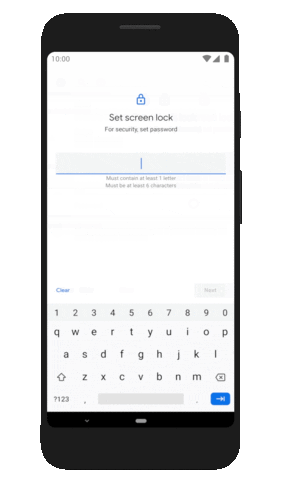 Device-specific security measuresStarting with Android 10, phone makers have to encrypt data on the device using Google's new Adiantum encryption method. That'll ensure that hackers can't read into your devices. The update also implements stronger security protocols such as TLS 1.3 for increased security while accessing the internet. The search giant has also made changes to the Biometric API that allows apps and services to use face and fingerprint authentication to make it more robust and secure. Google's security team says it's working on a system to integrate electronic ID in a device, so you can use your phone as an ID, just as you would your driver's license. However, we might see that in a later version of Android. You can check out Android 10's security features here. In the past year, we've seen various security incidents involving Android devices. While these changes might not make them the most secure devices around, it'll make things harder for hackers looking to break into your devices. Read next: Ethereum market faces bearish 'death cross' pattern, while Bitcoin retains momentum |
| What if the FBI tried to crack an Android phone? We attacked one to find out - The Conversation US Posted: 29 Mar 2016 12:00 AM PDT The Justice Department has managed to unlock an iPhone 5c used by the gunman Syed Rizwan Farook, who with his wife killed 14 people in San Bernardino, California, last December. The high-profile case has pitted federal law enforcement agencies against Apple, which fought a legal order to work around its passcode security feature to give law enforcement access to the phone's data. The FBI said it relied on a third party to crack the phone's encrypted data, raising questions about iPhone security and whether federal agencies should disclose their method. But what if the device had been running Android? Would the same technical and legal drama have played out? We are Android users and researchers, and the first thing we did when the FBI-Apple dispute hit popular media was read Android's Full Disk Encryption documentation. We attempted to replicate what the FBI had wanted to do on an Android phone and found some useful results. Beyond the fact the Android ecosystem involves more companies, we discovered some technical differences, including a way to remotely update and therefore unlock encryption keys, something the FBI was not able to do for the iPhone 5c on its own. The easy ways inData encryption on smartphones involves a key that the phone creates by combining 1) a user's unlock code, if any (often a four- to six-digit passcode), and 2) a long, complicated number specific to the individual device being used. Attackers can try to crack either the key directly – which is very hard – or combinations of the passcode and device-specific number, which is hidden and roughly equally difficult to guess. Decoding this strong encryption can be very difficult. But sometimes getting access to encrypted data from a phone doesn't involve any code-breaking at all. Here's how:
But if these options are not available, code-breaking is the remaining way in. In what is called a "brute force" attack, a phone can be unlocked by trying every possible encryption key (i.e., all character combinations possible) until the right one is reached and the device (or data) unlocks. Starting the attack There are two types of brute-force attacks: offline and online. In some ways an offline attack is easier – by copying the data off the device and onto a more powerful computer, specialized software and other techniques can be used to try all different passcode combinations. But offline attacks can also be much harder, because they require either trying every single possible encryption key, or figuring out the user's passcode and the device-specific key (the unique ID on Apple, and the hardware-bound key on newer versions of Android). To try every potential solution to a fairly standard 128-bit AES key means trying all 100 undecillion (1038) potential solutions – enough to take a supercomputer more than a billion billion years. Guessing the passcode could be relatively quick: for a six-digit PIN with only numbers, that's just a million options. If letters and special symbols like "$" and "#" are allowed, there would be more options, but still only in the hundreds of billions. However, guessing the device-specific key would likely be just as hard as guessing the encryption key. Considering an online attackThat leaves the online attack, which happens directly on the phone. With the device-specific key readily available to the operating system, this reduces the task to the much smaller burden of trying only all potential passcodes. However, the phone itself can be configured to resist online attacks. For example, the phone can insert a time delay between a failed passcode guess and allowing another attempt, or even delete the data after a certain number of failed attempts. Apple's iOS has both of these capabilities, automatically introducing increasingly long delays after each failure, and, at a user's option, wiping the device after 10 passcode failures. Attacking an Android phoneWhat happens when one tries to crack into a locked Android phone? Different manufacturers set up their Android devices differently; Nexus phones run Google's standard Android configuration. We used a Nexus 4 device running stock Android 5.1.1 and full disk encryption enabled. 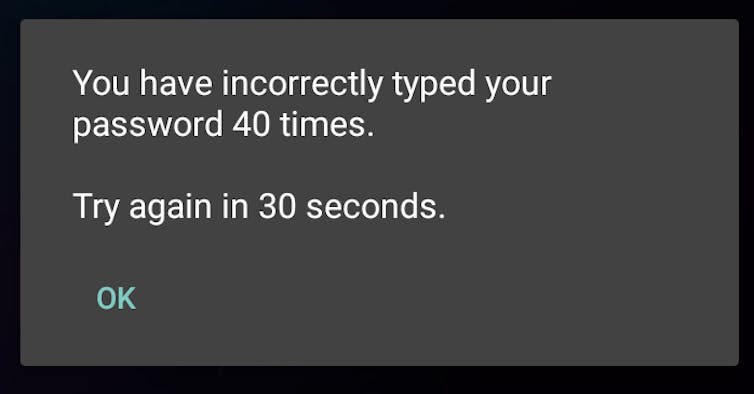 We started with a phone that was already running but had a locked screen. Android allows PINs, passwords and pattern-based locking, in which a user must connect a series of dots in the correct sequence to unlock the phone; we conducted this test with each type. We had manually assigned the actual passcode on the phone, but our unlocking attempts were randomly generated. After five failed passcode attempts, Android imposed a 30-second delay before allowing another try. Unlike the iPhone, the delays did not get longer with subsequent failures; over 40 attempts, we encountered only a 30-second delay after every five failures. The phone kept count of how many successive attempts had failed, but did not wipe the data. (Android phones from other manufacturers may insert increasing delays similar to iOS.) These delays impose a significant time penalty on an attacker. Brute-forcing a six-digit PIN (one million combinations) could incur a worst-case delay of just more than 69 days. If the passcode were six characters, even using only lowercase letters, the worst-case delay would be more than 58 years. When we repeated the attack on a phone that had been turned off and was just starting up, we were asked to reboot the device after 10 failed attempts. After 20 failed attempts and two reboots, Android started a countdown of the failed attempts that would trigger a device wipe. We continued our attack, and at the 30th attempt – as warned on the screen and in the Android documentation – the device performed a "factory reset," wiping all user data. 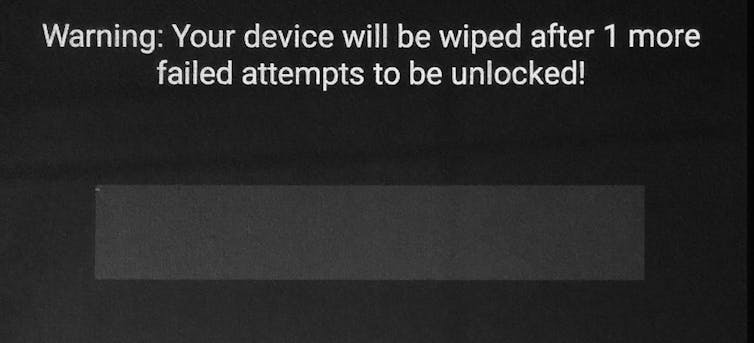 In contrast to offline attacks, there is a difference between Android and iOS for online brute force attacks. In iOS, both the lock screen and boot process can wipe the user data after a fixed number of failed attempts, but only if the user explicitly enables this. In Android, the boot process always wipes the user data after a fixed number of failed attempts. However, our Nexus 4 device did not allow us to set a limit for lock screen failures. That said, both Android and iOS have options for remote management, which, if enabled, can wipe data after a certain number of failed attempts. Using special toolsThe iPhone 5c in the San Bernardino case is owned by the employer of one of the shooters, and has mobile device management (MDM) software installed that lets the company track it and perform other functions on the phone by remote control. Such an MDM app is usually installed as a "Device Administrator" application on an Android phone, and set up using the "Apple Configurator" tool for iOS. 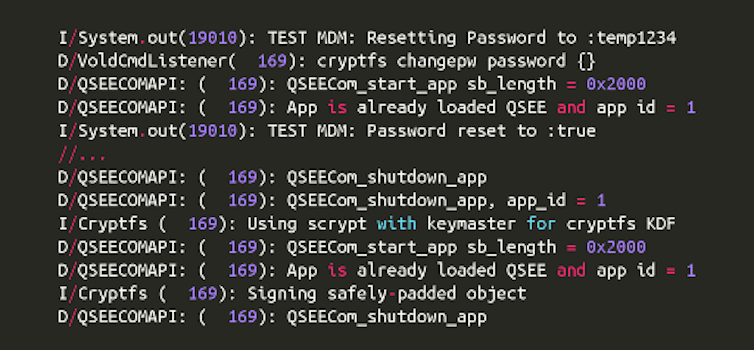 We built our own MDM application for our Android phone, and verified that the passcode can be reset without the user's explicit consent; this also updated the phone's encryption keys. We could then use the new passcode to unlock the phone from the lock screen and at boot time. (For this attack to work remotely, the phone must be on and have Internet connectivity, and the MDM application must already be programmed to reset the passcode on command from a remote MDM server.) Figuring out where to get additional helpIf an attacker needed help from a phone manufacturer or software company, Android presents a more diverse landscape. Generally, operating system software is signed with a digital code that proves it is genuine, and which the phone requires before actually installing it. Only the company with the correct digital code can create an update to the operating system software – which might include a "back door" or other entry point for an attacker who had secured the company's assistance. For any iPhone, that's Apple. But many companies build and sell Android phones. Google, the primary developer of the Android operating system, signs the updates for its flagship Nexus devices. Samsung signs for its devices. Cellular carriers (such as AT&T or Verizon) may also sign. And many users install a custom version of Android (such as Cyanogenmod). The company or companies that sign the software would be the ones the FBI needed to persuade – or compel – to write software allowing a way in. Comparing iOS and AndroidOverall, devices running the most recent versions of iOS and Android are comparably protected against offline attacks, when configured correctly by both the phone manufacturer and the end user. Older versions may be more vulnerable; one system could be cracked in less than 10 seconds. Additionally, configuration and software flaws by phone manufacturers may also compromise security of both Android and iOS devices. But we found differences for online attacks, based on user and remote management configuration: Android has a more secure default for online attacks at start-up, but our Nexus 4 did not allow the user to set a maximum number of failed attempts from the lock screen (other devices may vary). Devices running iOS have both of these capabilities, but a user must enable them manually in advance. Android security may also be weakened by remote control software, depending on the software used. Though the FBI was unable to gain access to the iPhone 5c by resetting the password this way, we were successful with a similar attack on our Android device. This article was updated April 8, 2016, to add a missing word "not" in the sentence beginning "The phone kept count…" |
| You are subscribed to email updates from "android encryption strength,samsung note 4 encryption,what is android phone mean" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment