WhatsApp Beaten As Signal’s New Desktop Calling Goes Live - Forbes
WhatsApp Beaten As Signal’s New Desktop Calling Goes Live - Forbes |
| WhatsApp Beaten As Signal’s New Desktop Calling Goes Live - Forbes Posted: 11 Oct 2020 12:00 AM PDT  getty While on the surface WhatsApp remains king of the messaging hill, beneath the surface there are some worrying signs for Facebook's flagship platform. With its 2 billion users, WhatsApp can seem unstoppable, but it has some weaknesses in its functionality—in the way it works. And, above all, it has one dealbreaker for many—its Facebook ownership. So, what are those functionality weaknesses? Well, there's the continued lack of genuine support for multiple devices—the option to link apps on your phone, tablet and PC to a single account. Then there's the serious flaw in its backup option, which is required to transfer message history to a new phone. Those back-ups fall outside WhatsApp's end-to-end encryption—and that's a critical issue. WhatsApp voice and video calling are excellent—fully encrypted, perfectly integrated with its messaging, single-click calls for the groups we use daily. But those calls—video or voice—are constrained to our smallest screen devices. And that just doesn't work anymore. WhatsApp knows this—multiple linked devices and desktop calling are reportedly in the works. But, in the meantime, we're turning to the competition. Recommended For You All of which makes WhatsApp's much smaller, but much more exciting, upstart rival Signal a potential giant killer in the space. Signal is the modern-day messaging disruptor, seeking to repeat the trick WhatsApp itself carried out all those years ago, before the Facebook acquisition. Signal was designed to put security first, that's its USP—WhatsApp actually uses a tweaked version of the Signal protocol itself. And historically this approach made for a clunky Signal user experience. But all that's now changing. Signal is on a mission to take on the mainstream. And if you haven't tried the app yet, you really should. Back in August I reported that Signal was beta-testing voice and video calls from its brilliant desktop app—a genuine app, not the web-based smartphone scraper offered by WhatsApp. Signal also offers a seamless iPad app. There's no need to keep your smartphone switched on or connected to access Signal from other devices. Signal's new desktop calling feature is now live—go try it for yourself. 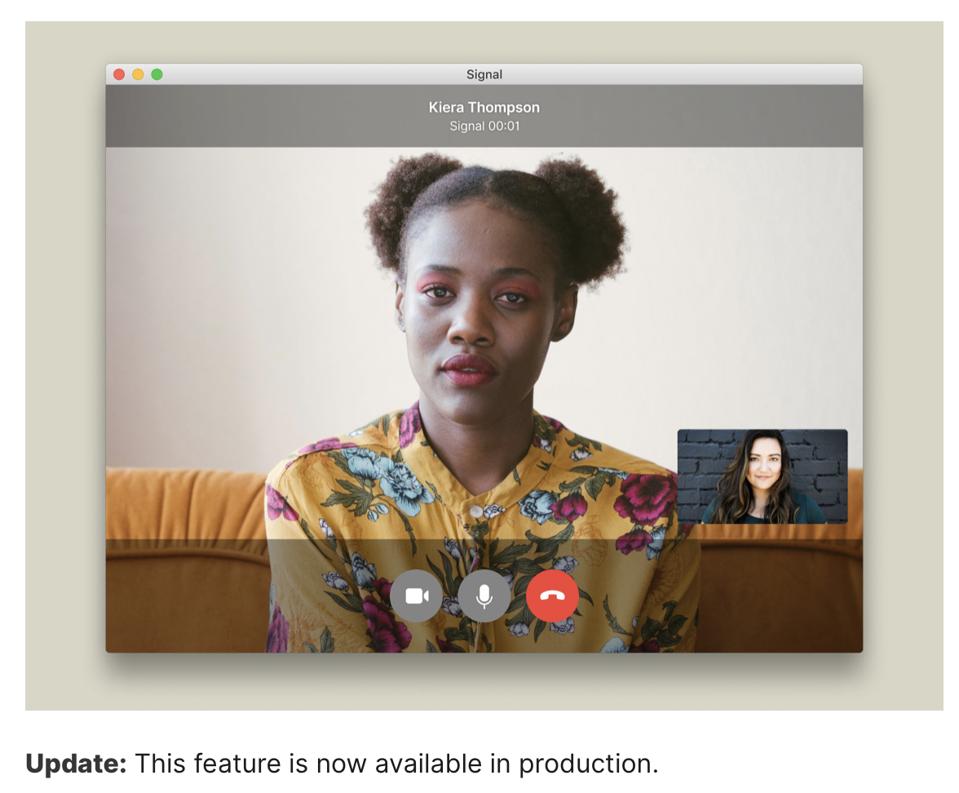 Desktop video calling SignalThis is much more important than it may sound. It emphasizes the multiple encrypted endpoints available in Signal, it showcases convergence—playing a convenience card to the new work from home workforce. There may not be backups with Signal, but these other encrypted instances provide resilience in case you lose your phone. And the platform appears flexible and nimble in contrast to WhatsApp. You'll struggle to find a tech or security reporter recommending WhatsApp over Signal these days. The more material factor, though, is what happens next. Facebook is caught between a rock and a hard place with WhatsApp. Tempted to introduce new monetization and advertising options, it knows that a user backlash will follow any overstep. And the likes of Signal and Telegram are watching and waiting. Signal is fast approaching the critical mass required to be a viable alternative for any WhatsApp exodus. On the desktop calling specifics, Signal has started with person-to-person calls, but group calling is clearly in the works. And while this is all part of its campaign to take on WhatsApp and Telegram for the secure messaging space, it also seems to have bigger video conferencing targets in mind. "We think that calls need to zoom out of the past and into the future," it says in its blog post. Working from home and enforced distancing has exponentially increased our use of video calling. Zoom, Teams and Google Meet, as well as Facebook's new Rooms reflect this. And underpinning this new way of working is a new level of convergence between messaging and calls and an increasing need to operate seamlessly from smartphones to tablets to desktops or laptops. We are inevitably less mobile, we want to access these apps from a laptop or tablet we may be using, and not be switching to our smartphones while at home. While the headline threat to WhatsApp likely comes from Apple's continuing evolution of iMessage, which already offers seamless cross-platform access, and Google's RCS rollout as an update to Android Messages, both have serious issues. That's because both integrate with the pitifully unsecure SMS architecture. Apple's end-to-end encryption only works while messaging users on its own ecosystem, and Google has not yet added any form of end-to-end encryption to its RCS deployment—another feature reportedly in the works. Signal now offers multiple device access, desktop calling, fully encrypted message history transfers to new devices, disappearing messages—another feature WhatsApp still has in the works. Furthermore, it is more secure than WhatsApp—its encryption deployment is openly viewable, it doesn't collect any metadata, it isn't owned by Facebook nor is it about to be integrated into a gargantuan marketing-meets-messaging machine. The integration of Facebook's various platforms—Messenger, Instagram, eventually WhatsApp, is bad news for users. WhatsApp remains the mainstream messenger of choice for most users. You'll find all your contacts most likely already there, it's easy to use and reliable, its security is good enough for 99% of its userbase, it offers a backup option (security caveats apart) for those that might lose their phones and need to restore their history. But this is an equation that's changing. Signal is extremely compelling, and its user experience now beats WhatsApp in many ways, from simple emoji replies to seamless multiple device access. And on the security front, there's no contest. Facebook's collection of WhatsApp metadata—who you message and how often is a grey area. Conversely, Signal's lack of any data collection is black and white. It's all starting to stack up toward a shift away from WhatsApp. Unsurprisingly, while Signal user numbers are measured in tens not hundreds of millions or even billions, it is now soaring. |
| New Wroba Campaign Is Latest Sign of Growing Mobile ... - Dark Reading Posted: 30 Oct 2020 01:23 PM PDT A new malware campaign targeting smartphone users in the US is the latest sign that mobile devices are becoming the next big target for cyberattackers. Kaspersky this week said its threat-monitoring systems had detected malware known as the Wroba Trojan, which targets Android and iOS device owners in the US with a fake package-delivery notification. Android device users who click on a link in the notification are taken to a malicious site with an alert that warns users about their mobile browser being out of date and needing to be updated. Users tricked into clicking "OK" to download the purported browser update end up installing the malware on their device instead. The download does not work on iPhones. So, users of iPhones who fall for the fake package-delivery notification are instead sent to a phishing page designed to look like Apple's login page, which attempts to steal their Apple ID credentials. Once Wroba is installed on a device, it can carry out a variety of malicious activities, according to Kaspersky. This includes sending fake SMS messages, checking installed packages, accessing financial transaction data, stealing the user's contact list, and serving up phishing pages for stealing credentials, including those associated with bank accounts. Kaspersky malware analyst Alexander Eremin says the origins of the phone numbers being targeted in the latest campaign are unclear. He surmises they could either be targeted at random or are, for example, numbers stolen from some e-commerce service that performs package deliveries. In some aspects, Wroba is not unlike other mobile malware — like its distribution via SMS. "But it utilizes some unusual techniques to hide its communication with its command-and-control [C2] server, like using MessagePack format and DES encryption to send the data." Wroba also has the ability to update its list of C2 servers with the help of information in social media accounts. The C2 information, for example, might be stored in encrypted form in the "Bio" or similar field in a social media account, Eremin says. Wroba is not new malware. Malwarebytes first reported on Wroba — then masquerading as a legitimate Google Play store app — back in 2013. But up to now, Wroba, aka FunkyBot, mainly has targeted users in Korea, Japan, and other countries in the Asia-Pacific region. The campaign launched this week marks the first time the operator of the malware has targeted US mobile devices owners, according to Kaspersky. In a report earlier this year, and in at least two more in 2018, Kaspersky has described Wroba as being part of a broader mobile malware campaign called "Roaming Mantis." Earlier versions of the malware were distributed via DNS hijacking. The operators of the malware basically hijacked DNS settings on home routers and redirected users of those routers to malicious sites. Since at least 2018, versions of Wroba have also been distributed via malicious SMS messages (aka smishing) using spoofed package-delivery notices. According to Kaspersky, the operators of Wroba have customized the spoofed notices, so the messages appear to come from trusted domestic package delivery services in each targeted country. Other vendors, such as Fortinet have also been tracking the threat for some time now. Growing Problem Malware is not the only issue. Adware — designed to serve up unwanted ads on mobile devices — is another big problem. In first half of this year, adware accounted for more than 35% of all malicious files that mobile users encountered on their devices, according to Kaspersky. Phishing is a growing problem as well. According to Lookout's 2020 "Mobile Phishing Spotlight Report" enterprise mobile phishing encounters jumped 37% globally between the fourth quarter of 2019 and first quarter of 2020. In North America, the number was much higher, at 66.3%. "Threat actors are building more-advanced phishing campaigns beyond just credential harvesting," says Hank Schless, senior manager of security solutions at Lookout. Through the first nine months of 2020, almost 80% of phishing attempts were designed to get users to install malicious apps on their mobile devices, he says. "Threat actors have learned how to socially engineer at scale by creating fake influencer profiles with massive followings that encourage followers to download malicious apps," Schless says. "Personal apps on devices that can access corporate resources pose serious risk to enterprise security posture." Jai Vijayan is a seasoned technology reporter with over 20 years of experience in IT trade journalism. He was most recently a Senior Editor at Computerworld, where he covered information security and data privacy issues for the publication. Over the course of his 20-year ... View Full BioRecommended Reading: More Insights |
| You are subscribed to email updates from "android data encryption,encrypted sms iphone,require encryption on device" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment