Asymmetric vs Symmetric Encryption: Definitions & Differences - Hashed Out by The SSL Store™ - Hashed Out by The SSL Store™
Asymmetric vs Symmetric Encryption: Definitions & Differences - Hashed Out by The SSL Store™ - Hashed Out by The SSL Store™ |
- Asymmetric vs Symmetric Encryption: Definitions & Differences - Hashed Out by The SSL Store™ - Hashed Out by The SSL Store™
- Cloudflare and Apple design a new privacy-friendly internet protocol - TechCrunch
- New Communication Platform Launched as “Impenetrable. Period.” - EIN News
- Compare SpecsThe Best Email Encryption Services for 2020 - PCMag.com
| Posted: 07 Dec 2020 11:18 AM PST Encryption is what makes secure data exchanges possible on the internet — let's explore the differences between symmetric vs asymmetric encryptionAsymmetric vs symmetric encryption. Not sure what these terms are or what they mean in relation to your life? Let's put this into terms that'll help you understand their importance immediately. Encryption is everywhere. From sending emails and making online purchases to securing sensitive government or healthcare-related information, symmetric and asymmetric encryption play critical roles in making secure data possible in our digital world. They're what keep your communications secure and your sensitive data out of the hands of criminals (and the hands of anyone else who shouldn't have it). But what are symmetric and asymmetric encryption? When comparing asymmetric vs symmetric encryption, in what ways are they alike, and how are they different? Lastly, which is more secure in different applications? Let's hash it out. What Is Encryption and How Does It Work? A Quick RefresherOkay, this is going to be a bit of a heavy topic, but we're going to simplify this as much as possible to appeal to all of our readers, regardless of your level of tech-savviness. So, before we can jump right into talking about asymmetric vs symmetric encryption, I think it would be important to quickly review what encryption is in general and how encryption works in general. You can define encryption as a means by which to convert readable content (plaintext) into unreadable gibberish (ciphertext). Encryption is a mathematical operation that exists within the realm of cryptography. This is why you'll often hear people talking about encryption and cryptography within the same discussion or sometimes use the terms interchangeably. However, there's an important difference:
Basically, encryption is the process of transforming plaintext into ciphertext through the use of two important elements:
Let's take a look at a simplified illustration of the process to better understand how encryption works in general: 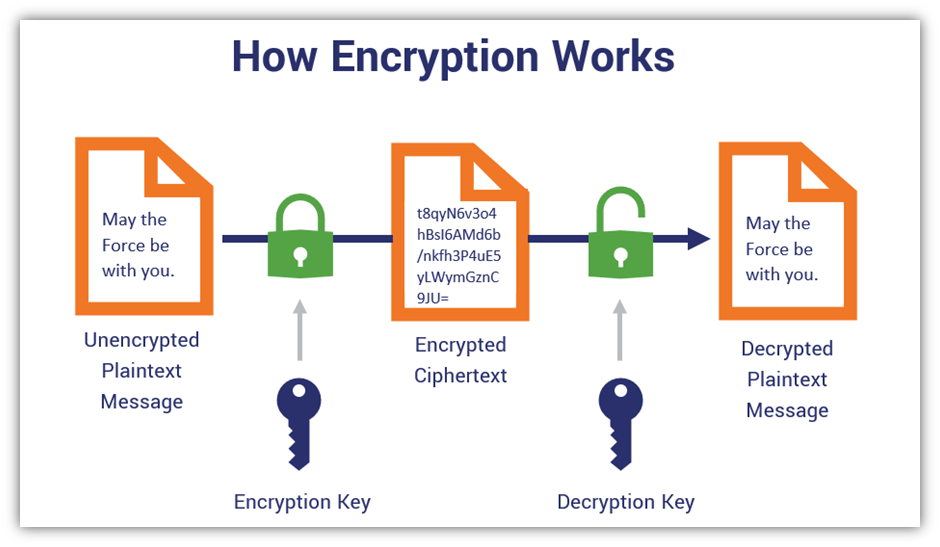
That's encryption in a nutshell. In the example graphic above, you may have noticed that the encryption and decryption keys are the same. No, this isn't a mistake — it's an example of symmetric encryption (which we'll talk more about shortly). That's because in symmetric encryption, one key encrypts and decrypts data. Asymmetric encryption looks similar, but it will involve using two separate keys that are related yet still unique. We've talked about different types of encryption before in some of our blog posts. But when it comes to a topic like asymmetric encryption vs symmetric encryption, there's a lot to unpack. So, let's explore each of these types of encryption individually to ensure a full understanding. Asymmetric vs Symmetric Encryption: What They Are & How They WorkWhat Is Asymmetric Encryption? Public Key Encryption Defined & Explained Asymmetric encryption is also a process of encrypting data between two parties — but instead of using a single key (as with conventional cryptographic systems), it uses two unique yet mathematically related keys to do so. The first key, known as the public key, encrypts your data before sending it over the internet; the other (aka the private key) decrypts the data on the recipient's end of the exchange. This is why asymmetric encryption is also known as public key encryption and public encryption. The public and private keys are mathematically related yet uniquely paired so that they match only one another. However, one key is publicly available while the other remains hidden and is never shared. However, encrypting data isn't all that asymmetric encryption does. As TV infomercials love to say — but, wait, there's more! Asymmetric encryption also offers:
Asymmetric encryption plays a crucial role in public key infrastructure (PKI), which we'll talk more about shortly. But first, let's hash out what symmetric encryption is and why it's also so important. What Is Symmetric Encryption? Secret Key Encryption Defined & Explained Symmetric encryption is another way to encrypt and decrypt data, but it uses one secret key instead of two to do so. Basically, the sender and the recipient have identical copies of the key, which they keep to themselves. This is why symmetric encryption is also known as private key encryption, private key cryptography, secret key encryption, secret key encryption, secret key cryptography, and symmetric cryptography. Symmetric encryption is the workhorse of cryptography. It's what enables you to encrypt massive quantities of data without bogging down processors, internet speed, and other IT resources. It's significantly more efficient than asymmetric encryption at scale and is an invaluable tool for large organizations and businesses in particular that value data security, privacy, and confidentiality. You'll find symmetric encryption in use for everything from banking and financial transactions to protecting data at rest. We recently wrote an article that offers a deep dive into the topic of symmetric encryption. Be sure to check that out for a more in-depth look at what symmetric encryption is and how it works. What Is the Difference? Symmetric vs Asymmetric EncryptionOkay, so now that we know what asymmetric and symmetric encryption are overall, let's compare and contrast them. There are several key traits that make symmetric and asymmetric encryption different in terms of how they work and where they're most valuable: 1. The Number, Nature, and Size of the Cryptographic KeysSymmetric keys are identical, whereas asymmetric public and private keys are mathematically related yet still unique. Symmetric keys are also typically shorter in length than their asymmetric counterparts. Symmetric keys are frequently 128 bits, 192 bits, and 256 bits, whereas asymmetric keys are recommended to be 2048 bits or greater. For example, here's an example of what a base64-encoded AES-256 symmetric encryption key looks like: Now, let's take a quick peek at what RSA 2048-bit asymmetric encryption keys look like. Public key: Private key: See the difference? But that's not the only thing that differs when comparing asymmetric vs symmetric encryption. 2. How the Keys Are DistributedWith asymmetric encryption, exchanging keys via digital public channels isn't an issue. That's because asymmetric key exchange protocols were literally designed with that very purpose in mind. To securely exchange symmetric keys, on the other hand, you'd need to meet up in person (offline). Not only is this inconvenient, but it also defeats the purpose of communicating digitally in the first place! Exchanging symmetric keys in public channels (like on the internet) otherwise is an issue because the key is vulnerable. Using asymmetric techniques in the key exchange process is more secure. This is why PKI incorporates the use of asymmetric key exchange protocols for the symmetric key exchange process as part of the TLS handshake. According to the original X.509 standards that were published by the CCIT (now ITU-T) and ISO in 1988:
 Manage Digital Certificates like a Boss 14 Certificate Management Best Practices to keep your organization running, secure and fully-compliant. 3. The Types and Complexities of the Encryption AlgorithmsOne of the big differences between symmetric vs asymmetric encryption is the types of encryption algorithms used in each process. Symmetric encryption algorithms are either block ciphers or stream ciphers, and include algorithms like DES, TDEA/3DES, AES, etc. Asymmetric encryption algorithms, on the other hand, include algorithms like RSA, DSA, ECC, etc. 4. How Time-Consuming and Resource-Intensive Each Process Is at ScaleSymmetric encryption, because it's faster and only uses one key, is great for large organizations and businesses that need to encrypt vast quantities of data. Asymmetric encryption uses two separate keys and more complex algorithms in the encryption and decryption process, which makes it slower for encrypting and decrypting large amounts of data. However, when comparing asymmetric vs symmetric encryption, you also must keep in mind the channels that you're using it in. Is it a public-facing channel or something private? 5. One's Better Suited Than the Other For Use in Public/Private ChannelsWe've already talked about this, but to quickly summarize — symmetric encryption on its own is best suited for non-public channels and asymmetric encryption is best for public channels. That's a quick way to think of the differences with asymmetric vs symmetric encryption. But why does it have to be either/or? Why can't we use both together in a way that's complementary? Well, we do — and this concept is at the very heart of public key infrastructure. The Roles of Asymmetric and Symmetric Encryption in Public Key InfrastructureAsymmetric encryption and symmetric encryption both play crucial roles in public key infrastructure, or PKI for short. PKI is a framework of technologies, processes, and policies that serves as the foundation of internet security. Basically, it's what makes secure data exchanges possible over the internet. You see, the internet itself is insecure. So, PKI outlines everything that makes it possible to:
Public key encryption, key exchanges, and digital signatures all play pivotal roles in securing digital communications. Once parties are authenticated and keys are securely exchanged to create a secure connection, then symmetric encryption can often take over to speed up the data encryption process. Encryption Is What Makes Your Online Shopping, Banking & Other Data Exchanges SecureWithout encryption, the data you transmit across the internet travels in plaintext format. This means that anyone who can intercept it can read it. So, whenever you buy something from amazon.com, for example, your credit card and other personal information travel through multiple touchpoints — networks, routers, servers, etc. — located throughout the world. This means that when you transmit data through those channels, someone could intercept that data and read it. Of course, this is why we constantly preach about using websites that are secured by SSL/TLS certificates here at Hashed Out. Why? Because it means that your data is secure while traveling through all of those different channels to get from point A to point B. So, if you like being able to buy 'snazzy' custom socks that have your dog's face printed on them in private, without someone intercepting your order and stealing your credit card information, then you're a fan of PKI.  Symmetric vs Asymmetric Encryption: Which Is Better?Forgive me for a moment as I channel my inner Peter Griffin, but "you know what really grinds my gears?" When I ask a question and I get the wishy-washy answer "it depends." But, in the case of determining which is "better" — asymmetric or symmetric encryption — that same loathed answer really rings true. That's because "better" can be defined in different ways depending on the specific circumstances at hand. For example, in non-public facing environments, symmetric encryption is great because it's a less complex process that allows for faster, more efficient data encryption. This means that you can encrypt large quantities of data without bogging down your IT resources. But when you use that same speedy encryption process in public channels on its own, without an asymmetric key exchange first, then it's not so great. In fact, it can be downright dangerous. This is why asymmetric encryption is so important in public channels (such as on the internet). Asymmetric encryption, although slower, is better for those circumstances where your data is at risk of being intercepted by unintended third parties. It offers you greater security in terms of authentication and non-repudiation — so you know you're talking to the right person — as well as data integrity. Symmetric vs Asymmetric Encryption: Which Is More Secure?So, to answer the question about whether symmetric or asymmetric encryption is more secure, I'd again have to give the dreaded answer, "it depends." And it really does — the answer depends on how you define "more secure" and in what context the encryption takes place. For example:
So, if you're comparing an asymmetric key pair and a symmetric key of equal size (in terms of bits) side by side, you'd be able to calculate the asymmetric pair's private key more easily. This explains why we use asymmetric key sizes (2048 bits or higher) that are significantly larger than symmetric key sizes (typically just 256 bits) in asymmetric encryption. However, the larger the asymmetric keys are, the more processing power they require. This is why, when establishing an encrypted website connection, we start out using an asymmetric key exchange before switching to symmetric encryption to secure the session. So, in that way, asymmetric encryption helps to make symmetric encryption more secure. Of course, this answer is also dependent on the technologies that are in use at the time. For example, asymmetric encryption methods like RSA are incredibly secure (but are also resource draining). It would take thousands of lifetimes to break this algorithm using modern computers. But what happens when computers get smarter, faster, and more capable? The Rise of Quantum Computing and Its Future Impact on EncryptionOf course, when it comes to encryption, concerns relating to quantum computing are always lurking. Quantum computers, unlike classical computers, operate using different directions that's based on quantum physics. As such, they can run advanced algorithms (quantum algorithms) and achieve things that traditional computers simply can't. As such, the overarching concern is that these computers, which are capable of completing steps and processing calculations at exponentially faster rates than our modern supercomputers, will break modern asymmetric cryptography as we know it. So, you'll often hear people calling out warnings about the dangers of quantum computing with regard to quantum cryptography. Shor's AlgorithmThis is what people are typically referring to when they talk about the threat of quantum computing to encryption. Mathematician Peter Shor came up with this algorithm, which provides exponential speedup, in 1994. (He later revised and expanded upon the paper a couple of years later.) The concern surrounding his algorithm is that it would make the factoring of larger numbers and calculation of discrete logarithms that asymmetric cryptography is based on vulnerable. Here's a quick video from Shor himself on the factoring algorithm: If that explanation was clear as mud, let's try a different approach. Essentially, it nullifies modern public key encryption schemes (like RSA). So, what this means is that quantum computers will break our modern asymmetric cryptosystems — leaving them useless against cybercriminals and other schmucks who wish to do bad things. However, Shor's algorithm applies to asymmetric cryptographic systems, not symmetric ones. You need the public key to be able to calculate the private key using Shor's Algorithm — and remember, symmetric encryption doesn't use public keys. But is there a type of algorithm that poses a threat to symmetric encryption? Yes and no. Grover's AlgorithmIf your first thought is of a blue Muppet when you read that header, then I'd suggest you grab another cup of coffee before reading this part. This algorithm, which was developed by Lov Grover in 1996, is one that applies to symmetric cryptographic systems. It's an algorithm that provides a quadratic speedup to address unordered search (whereas Shor's offers exponential speedup), which means that it can make brute-force searches substantially faster for encryption schemes that use smaller key sizes. The idea behind Grover's algorithm is that it essentially cuts symmetric key lengths in half, making them faster to compute. However, it's a concern is something that many experts believe can be addressed by increasing key spaces to double key lengths. Researchers in the Department of Informatics at the University of Oslo in Norway shared the following in an article in the International Journal of Advanced Computer Science and Applications (IJACSA):
The researchers go on to state some good news as far as symmetric encryption is concerned:
Researchers at Princeton University's Center for Information Technology Policy created a paper for Carnegie's Encryption Working Group that shares the following about the implications of quantum computing on encryption:
Preparing for the Future With Post-Quantum CryptographyLet me start off by saying that the situation isn't as bleak as some would make it out to be. Yes, absolutely, quantum computing poses a future threat to modern asymmetric cryptography. But the sky isn't falling — yet. There are some bits of good news to consider. For one, quantum computing is a concern we've known about for decades. Quantum cryptography was proposed back in the 1980s, and both Shor's and Grover's algorithms were developed in the mid-1990s. So, it isn't something new. Experts are working to come up with solutions and standards that will prepare us to deal with these issues once quantum cryptography officially arrives. For example, the National Institute of Standards and Technology (NIST) has been working on narrowing down the list to several post-quantum cryptography (PQC) algorithms as part of its standardization plan. For example, as of July 2020, they've managed to narrow the list down to just 15 algorithms for:
Why so many algorithms and why worry about it now? According to NIST's Post-Quantum Cryptography Call for Proposals page:
But there is good news here. Certificate authorities like Sectigo and DigiCert are trying to head such problems off at the pass. They're preparing for the inevitable by creating what they're calling "hybrid" certificates. The thought here is that these certificates will help prepare organizations for the impending PQC world while also still making it so that their systems and infrastructure are still compatible with non-PQC setups. So, instead of using certificates that support only current asymmetric encryption algorithms or PQC encryption algorithms, they'll enable your systems to still be interoperable with systems that support either or both types of algorithms. The truth is that we're still years away from having quantum computers commercially available. It's on the horizon, but we're just not there yet. So, all of this is to say that while quantum computers are a concern that the industry as a whole is preparing for, it's just a waiting game at this point. Final Thoughts on Asymmetric vs Symmetric EncryptionThere are so many benefits and applications for symmetric and asymmetric encryption. The more that you learn about these two methods of encryption and how they work to secure our data in digital spaces, the more fascinating it becomes. Hopefully, this article has helped you better understand the strengths and weaknesses of each process, as well as how they complement each other. Asymmetric and symmetric encryption alike both hold important places within the realm of public key infrastructure and digital communications. One without the other would be either incredibly insecure or so bulky and unmanageable that it wouldn't be practical. This is why both types of encryption are crucial to internet security as we know it. Have thoughts about symmetric and asymmetric encryption that haven't been covered here? Be sure to share them in the comments section below! |
| Cloudflare and Apple design a new privacy-friendly internet protocol - TechCrunch Posted: 08 Dec 2020 04:00 AM PST  Engineers at Cloudflare and Apple say they've developed a new internet protocol that will shore up one of the biggest holes in internet privacy that many don't know even exists. Dubbed Oblivious DNS-over-HTTPS, or ODoH for short, the new protocol makes it far more difficult for internet providers to know which websites you visit. But first, a little bit about how the internet works. Every time you go to visit a website, your browser uses a DNS resolver to convert web addresses to machine-readable IP addresses to locate where a web page is located on the internet. But this process is not encrypted, meaning that every time you load a website the DNS query is sent in the clear. That means the DNS resolver — which might be your internet provider unless you've changed it — knows which websites you visit. That's not great for your privacy, especially since your internet provider can also sell your browsing history to advertisers. Recent developments like DNS-over-HTTPS (or DoH) have added encryption to DNS queries, making it harder for attackers to hijack DNS queries and point victims to malicious websites instead of the real website you wanted to visit. But that still doesn't stop the DNS resolvers from seeing which website you're trying to visit. Enter ODoH, which builds on previous work by Princeton academics. In simple terms, ODoH decouples DNS queries from the internet user, preventing the DNS resolver from knowing which sites you visit. Here's how it works: ODoH wraps a layer of encryption around the DNS query and passes it through a proxy server, which acts as a go-between the internet user and the website they want to visit. Because the DNS query is encrypted, the proxy can't see what's inside, but acts as a shield to prevent the DNS resolver from seeing who sent the query to begin with. "What ODoH is meant to do is separate the information about who is making the query and what the query is," said Nick Sullivan, Cloudflare's head of research. In other words, ODoH ensures that only the proxy knows the identity of the internet user and that the DNS resolver only knows the website being requested. Sullivan said that page loading times on ODoH are "practically indistinguishable" from DoH and shouldn't cause any significant changes to browsing speed. A key component of ODoH working properly is ensuring that the proxy and the DNS resolver never "collude," in that the two are never controlled by the same entity, otherwise the "separation of knowledge is broken," Sullivan said. That means having to rely on companies offering to run proxies. Sullivan said a few partner organizations are already running proxies, allowing for early adopters to begin using the technology through Cloudflare's existing 1.1.1.1 DNS resolver. But most will have to wait until ODoH is baked into browsers and operating systems before it can be used. That could take months or years, depending on how long it takes for ODoH to be certified as a standard by the Internet Engineering Task Force. |
| New Communication Platform Launched as “Impenetrable. Period.” - EIN News Posted: 08 Dec 2020 05:45 AM PST Secured Communications' Mercury 2.0 for enterprise customers worldwide is an ultra-secure platform designed for healthcare, education, and financial industries Because we feel very strongly about protecting the privacy and security of all of your communications, as well as mitigating company risk, we created the Mercury platform to be Impenetrable. Period." SAN FRANCISCO, CA, UNITED STATES, December 8, 2020 /EINPresswire.com/ -- Secured Communications, the global leader in safeguarding corporate communications, announces Mercury 2.0 with the addition of a great number of intuitive and productivity-enhancing improvements to its already robust, trusted, and efficient platform, Mercury.— Robert Wilson, Secured Communications CEO This update incorporates feedback from the company's enterprise customers including the healthcare, education, and financial industries, which now includes significant upgrades to the ultra-secured unified platform that offers encrypted messaging, high-definition videoconferencing, clear audio calls, file sharing and other capabilities all in one protected ecosystem. Because Mercury was built on security first, the company can easily add productivity and performance enhancements without compromising its unparalleled security, reliability & performance. Robert Wilson, the company's CEO, commented, "Because we feel very strongly about protecting the privacy and security of all of your communications, as well as mitigating company risk, we created the Mercury platform to be Impenetrable. Period." He continued, "Security is the top priority in every decision we make as a company." Mercury provides a suite of completely protected corporate networking capabilities that allow users to communicate privately and securely without disruptions or leaks of sensitive information, helping businesses to minimize the risk of losses through information hacking, reputational damage and data breaches. Though the company boasts its end to end AES 256 encryption, dedicated redundant servers in the US/UK, 99.9999% uptime, and HIPAA, FIPS, GDPR and Privacy Shield certifications, Secured Communications continually innovates to make Mercury as functional and as simple to use as possible. Adding to its already ultra-secure, highly productive platform, Mercury 2.0 boasts many new enhancements for both desktop and mobile: • High Definition & Fidelity Meetings and Calling: High-definition and high-fidelity video and audio that surpass other platforms in quality, making users feel as if they are in the same room with those whom they are meeting. • Secured Calls (Desktop & Mobile): Call functionality has been rebuilt from the ground up to provide calls that are clearer, faster, and even more secure; now available on desktop in addition to mobile app. • Call Transition to Meeting (Desktop & Mobile): Calls can now seamlessly transition into high-definition meetings with the simple press of a button. • Secured Contact Improvements: Mercury 2.0 builds on the platform's Secured Contacts system which ensures that users are messaging, sharing files, calling & meeting with only the intended, identity-verified recipients. • Stealth Mode™: This new function enables users to contain all communications within the Mercury interface for ultimate security. The company's continuing cooperation with law enforcement and counterterrorism agencies around globe drove the development of the new Stealth Mode™ technology which allows users at risk of heightened surveillance to restrict all communications to within the Mercury ecosystem. • Mercury Gatekeeper™: This feature automatically detects and alerts users to use approved browsers and secure hardware, ensuring the highest quality security and HD video and audio performance. • Global Secured Media Relay Technology: Industry leading technology that allows for improved performance of Mercury's high-definition videoconferencing platform & secure call platform throughout the globe - 11 Countries added. About Secured Communications Secured Communications is the global leader in safeguarding communications. Developed in partnership with former senior FBI and global law enforcement leaders, the company's suite of products protects information with the most advanced and intuitive encrypted solutions. Its platform is trusted by counterterrorism professionals, public safety agencies and vetted corporations worldwide. Mercury, powered by Secured Communications, allows users to host secured video conferences, make secure calls, send messages, and share files seamlessly, all within a single application interface. Secured Communications views its clients as partners and offers first class concierge support in addition to providing customization services and integrations to help them manage their most sensitive communications and stay in control of vital information. Secured Communications is HIPAA, FIPS and GDPR compliant, among others. For more information, please visit https://securedcommunications.com/mercury-enterprise.html. Media |
| Compare SpecsThe Best Email Encryption Services for 2020 - PCMag.com Posted: 25 Nov 2020 06:07 AM PST The academics who invented email aimed to improve and expedite communication between people. They clearly didn't think a lot about restricting that communication to the right people. Read someone else's email? How rude! In the modern world, most of us are aware that email isn't a secure means of communication. Hackers, snoops, and even your email provider could be reading anything you write. Unless, that is, you encrypt that email to protect your privacy. Fortunately, there are utilities to help with email encryption, some are free, some are simple to use, and some are both. Wait, Isn't My Email Already Encrypted?You may remember a while ago when Google tweaked Gmail so that it always uses a secure HTTPS connection. That means it uses the standard Transport Layer Security (TLS) for encryption. This is good, but it's the bare minimum. Every website should use HTTPS. As of a couple years ago, Google says it no longer reads your mail. However, it's easy to accidentally give mail-reading permission to third-party apps. And Google does read your messages sufficiently to do things like automatically put airline flight notifications in your calendar. Google also has a policy explaining when it will release your email to government entities, one that clearly indicates that it can do so if compelled. Apple Mail supports full-on encryption and digital signatures. To enable these features, you must obtain a security certificate. There used to be quite a few sources for free certificates, but the list is shrinking. We used Actalis to obtain a cert for testing. With the certificate installed in your keychain, your emails are digitally signed by default. And if all the recipients of a message also have certs, you can click the lock icon to send the message encrypted. A quick survey of my PCMag colleagues turned up exactly nobody who had installed an email security certificate, and this is a technically minded group. You'd expect even fewer ordinary consumers to have encryption enabled for their Apple Mail…except that you can't go lower than zero. In any case, Apple has had some glitches with encryption. Researchers in 2019 discovered unencrypted copies of secure emails in the database that Siri uses to better serve you. I think we can agree that Siri does not need to read our encrypted emails. The point here is that your email provider's goals aren't centered on security and privacy. If you really want to protect your emails from prying eyes, look to a third-party company that puts security first. Do I Have to Pay for Email Encryption?Maybe you're convinced that encrypting your email is a good thing, but are you convinced enough to pay for it with your hard-earned cash? Don't worry: You don't have to pay. Preveil and Virtru are totally free. Both are simplified consumer-focused editions of enterprise-level products. Their "big brother" products bring in the cash. You can also use ProtonMail and Private-Mail for free, but you must accept certain limitations. Smart consumers will set up a free account and see if the limitations chafe. If they do, converting to a paid account is simple. StartMail is the only product covered here that doesn't have a free tier, though it does offer a 7-day free trial. Do I Have to Change My Email Address?On the one hand, starting fresh with a never-before-seen email address can be freeing. You know that the new address hasn't been bandied about on the Dark Web or hoovered up by data aggregators. On the other hand, you must let all your contacts know that your address changed and reconfigure all your online accounts to use the new address. ProtonMail, Private-Mail, and StartMail all require that you switch to a brand-new email address. As with any other webmail system, it must be unique within the system. But since these services don't have the millions or even billions of users that a Gmail or Yahoo does, you may well be able to get your own name without tagging on a bunch of numbers or other characters. Wouldn't you rather have a [email protected] address than a [email protected] one? With Preveil and Virtru, you keep your existing email. In fact, Virtru requires that you use a Gmail address, and access it in Chrome. Preveil doesn't limit you to any specific email provider. It integrates with Gmail and Outlook on Windows and Apple Mail on macOS, and with the native mail app on your mobile devices. Who Can I Email?Encrypting your messages does no good unless the recipient can decrypt them. Different products handle that end of the equation in a variety of ways. The recipient of a Preveil message must install Preveil to read it, period. But since the product is free and easy to install, that's not much of a limitation. Your communication is secured with military-level encryption, but you don't have to remember passwords or do anything beyond choosing to encrypt the message. Virtru also manages encryption keys outside your view. The recipient of a Virtru message clicks a link to view and reply to the message in a browser window, with no need to install Virtru. StartMail, Private-Mail, and ProtonMail all use an encryption system called Pretty Good Privacy (PGP) to secure messages between users of their respective services. That means they can also exchange encrypted mail with users of other email systems that support PGP. Setting up the necessary key exchange to enable third-party PGP messaging can be difficult, though. Those same three products also include a provision for securely communicating with those who both don't use the service and don't have a PGP key. While the implementations differ, the overall method is the same. You encrypt your message with a password and transmit the password to the recipient using a text, a phone call, or some other non-email communication. How Is My Email Protected?Using PGP encryption requires that you enter the PGP passphrase for your encryption key. When you send non-PGP encrypted messages, each can have its own password. Preveil and Virtru don't require a password—your possession of a trusted device is enough for basic authentication. And yes, you can revoke trust for a lost device. Whether basic authentication relies on a password or trusted device, you can crank up security by enabling two-factor authentication, when available. ProtonMail, Private-Mail, and StartMail all support two-factor authentication using Google Authenticator or any work-alike that can provide a standard Time-based One-Time Password (TOTP). With Preveil, you need access to a trusted device (something you have), the password for your email account (something you know), and whatever authentication method you use to open the trusted device, typically a passcode or biometric system. It's a form of multi-factor authentication, though not the traditional password-plus-TOTP type. What Else Do I Get?As noted, with some services you start fresh with a brand-new email address. But once you start using that address, once many different merchants and websites have it, it won't stay pristine. That is, unless you never tell anybody your email address. How can you email without giving away your address? By using a Disposable Email Address (DEA) service, that's how. Such a service generates a one-off DEA every time you need to give out your address. Messages to that DEA show up in your regular inbox, and replies seem to come from the DEA. And if one of your DEAs starts to get spam or other problems, you can just delete it. Private-Mail and StartMail can both create and manage DEAs. However, they're rather limited compared to dedicated DEA utilities such as Burner Mail and ManyMe. Abine Blur goes beyond those two, letting you shop while hiding not only your actual email address but your credit card number and phone number. With most of these services, you can share a file securely by attaching it to an encrypted message; Private-Mail is the exception, as it supports only plain text. It makes up for that lack by giving you encrypted cloud storage, along with the ability to securely share files from your encrypted storage. Preveil also offers cloud storage with secure sharing. You can set ProtonMail and Virtru messages to expire after a given time. Private-Mail and ProtonMail let you set an away message when you won't have email access. These two also include the ability to define filtering rules. What's the Best Service for Encrypting Your Email?As you can see, all these products have their virtues, and each offers a different set of features. For its weapons-grade encryption, ease of use, and low price (free!), Preveil is our top pick and our Editors' Choice winner. However, if you want a new email address for your encrypted messages, support for third-party PGP communication, or another unusual feature, you've got plenty of choices. While you're thinking about security, you should read our roundup of the best encryption software for protecting the data on your drives.
Where To Buy |
| You are subscribed to email updates from "encrypted cell phone calls,what is the meaning of encryption,how to make encrypted phone calls" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |



Comments
Post a Comment