Get Extra Security with This VPN & Email Encryption Bundle - Gadget Hacks
Get Extra Security with This VPN & Email Encryption Bundle - Gadget Hacks |
- Get Extra Security with This VPN & Email Encryption Bundle - Gadget Hacks
- As WhatsApp deepens integration with Facebook, here are two alternatives for iOS - 9to5Mac
- Perfect Forward Secrecy Explained - Hashed Out by The SSL Store™ - Hashed Out by The SSL Store™
| Get Extra Security with This VPN & Email Encryption Bundle - Gadget Hacks Posted: 06 Jan 2021 12:08 PM PST  The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113). How does it work? Zenmate keeps your passwords and information safe as you're browsing on your at-home private WiFi connection or any public domain. It hides your IP address from lurkers and encrypts all of your traffic histories, so no one (not even the government!) can see what you're up to. It makes sense that it won the Europas Award for Best Security/Privacy Startup and boasts 4.3 out of five stars on VPNMentor. It can even unblock any restricted YouTube videos, and you can choose servers from over 77 different countries. Plus, with the second half of this bundle, you can encrypt all of your emails (inbox and sent) to make sure what you're doing online is truly private from employers or anyone else. SmartMail features extra-secure storage, unlimited alias email addresses, and one-click encryption — all with a clear, easy-to-read privacy policy. You know it's good since it's based in The Netherlands, which basically has some of the world's strictest privacy laws. If you ever run into any issues, there's a 24/7 support team available to answer any question that comes up. Both of these programs are included with the bundled price of $44.99 (60% off from $113). Snag this deal for a limited time and put cybersecurity at the top of your to-do list for the new year. Prices subject to change. Keep Your Connection Secure Without a Monthly Bill. Get a lifetime subscription to VPN Unlimited for all your devices with a one-time purchase from the new Gadget Hacks Shop, and watch Hulu or Netflix without regional restrictions, increase security when browsing on public networks, and more. |
| As WhatsApp deepens integration with Facebook, here are two alternatives for iOS - 9to5Mac Posted: 07 Jan 2021 09:58 AM PST As first reported yesterday, WhatsApp will soon start sharing your data with Facebook whether you like it or not. In light of that, many people are searching for WhatsApp alternatives with deeper focuses on privacy and security. Here are two recommendations.
BackgroundFirst, when WhatsApp was acquired by Facebook for $19 billion, the messaging app assured users that the acquisition would not bring any changes to its focus on user privacy and "knowing as little about you as possible." In 2016, WhatsApp began sharing data with Facebook by default, but users still had the ability to opt-out. It was revealed yesterday, however, that WhatsApp is making changes to its privacy to remove the opt-out option completely, at least outside of Europe. This has left many people looking for alternatives to WhatsApp for cross-platform messaging. But the switch from WhatsApp to alternatives is not as easy as you might think. For many people, WhatsApp is a primary tool for communicating with friends and family, and while those of us intertwined in the technology community might be willing to make the switch, not everyone will feel the same way. WhatsApp is referred to by many as the true cross-platform messaging solution that the world needs. What's important to remember is that messaging remains end-to-end encrypted, so Facebook (as it stands right now) can't see the content of messages. Of course, the ideal solution is for Apple to bring iMessage to Android and Windows, but it's highly unlikely that such a development is even something Apple is considering. Just like one solution for easy, cross-platform, encrypted video communication would be to bring FaceTime to non-Apple devices. Nonetheless, here are some alternatives to WhatsApp for cross-platform encrypted messaging. Signal Signal has seen a dramatic rise in popularity over the last year as people have turned to new platforms for encrypted communication. The app supports group text and audio messages, as well as audio and video calls. It's compatible with IPhone, iPad, Mac, Windows, Linux, and Android. In comparison to WhatsApp, Signal makes its focus on privacy abundantly clear. There are a variety of touches throughout the Signal application to underscore this focus, including things such as view-once media, Signal PIN, and more. Signal is also an independent nonprofit, which means that development is supported purely by donations from users. Signal uses end-to-end encryption for messaging, based on the Signal Protocol, and also doesn't log metadata about messages or users. The App Privacy label on the App Store indicates that Signal does not collect any data that is linked to users. A report from The Wall Street Journal shed more detail on this:
By all indications, if you're looking for a new messaging application that's biggest focus is on privacy and encryption, Signal is an excellent option. Signal is available on the App Store as a free download. Telegram Telegram is one of the most popular alternatives to WhatsApp, providing a cross-platform solution for messaging with end-to-end encryption that is also completely free to use. In fact, Telegram actually claims to be more secure than WhatsApp because of its use of the MTProto protocol:
As for protecting data other than the encrypted messages themselves, Telegram says that uses a distributed infrastructure. "The relevant decryption keys are split into parts and are never kept in the same place as the data they protect," the company explains. The new App Privacy labels on the App Store show three pieces of data that "may be collected and linked to your identity," including contact information, contacts, and identifiers. Telegram is available on the App Store as a free download. Wrap-upAgain, like I wrote at the beginning of this piece, switching from WhatsApp to something like Telegram or Signal isn't quite as seamless as it might appear. Neither app has garnered the mainstream adoption of WhatsApp, but if you want to be the anti-Facebook force among your friends and family, Signal and Telegram are both great alternatives. Do you have any additional recommendations? Do you plan on sticking with WhatsApp despite the increasing ties to Facebook? Let us know down in the comments! FTC: We use income earning auto affiliate links. More. Check out 9to5Mac on YouTube for more Apple news: |
| Perfect Forward Secrecy Explained - Hashed Out by The SSL Store™ - Hashed Out by The SSL Store™ Posted: 09 Dec 2020 12:00 AM PST Perfect Forward Secrecy Ensures HTTPS Traffic Stays Encrypted – Even if the Private Key is Later CompromisedImagine for a second that someone breaks into your house. They can theoretically take whatever is in your place at that moment. That's a scary enough thought right there. But what if it went a step further? What if they could also pick from everything that's ever been in your house in the past? And then be able to steal any future item you purchase, as well? Sounds like a nightmare scenario, doesn't it? Unfortunately, the same thing can happen with your data. Encryption keeps it safe, but only as long as your private key is safe. We all dread the thought of one of our private keys being compromised, ending up in the hands of a hacker. Your future communications would immediately be at risk. Not only that, but what's stopping them from examining your past data for juicy, sensitive information that they can exploit for their own gain? But don't worry, it's not all doom and gloom. Cryptographers have once again come to the rescue! A solution was created to deal with exactly this sort of problem, and it's called "perfect forward secrecy." Long story short, it prevents future security incidents from compromising past encrypted data. More and More Site Owners Are Taking Advantage of Perfect Forward SecrecyEven better, it's a security feature that is continuing to become more and more common. All major browsers support it, as do post-Windows XP operating systems. SSL Labs found in their October 2020 scan that 21.8% of surveyed sites supported perfect forward secrecy with all modern browsers and 64.5% supported perfect forward secrecy with most browsers. Only 1.2% of sites didn't support perfect forward secrecy at all. The numbers keep going up, and the support of industry giants certainly hasn't hurt, either. Google has been using it with Gmail and other products for years now, and Apple made perfect forward secrecy a requirement on the App Store in 2017. When TLS 1.3 was introduced, the Internet Engineering Task Force (IETF) mandated perfect forward secrecy, only allowing cipher suits that offered it. It's an important part of the future of cryptography, and for good reason. 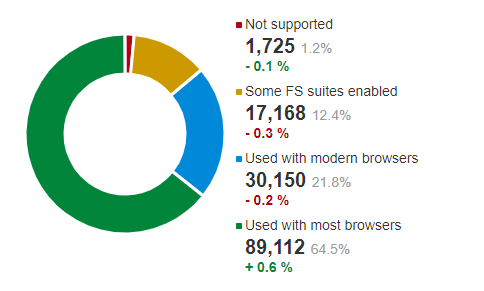 So how exactly does perfect forward secrecy work? Why is it such a powerful security feature? And how can you go about enabling it on your own server? Let's hash it out. The Need for Perfect Forward SecrecyWithout the use of perfect forward secrecy, the repercussions are far more severe if a private key is compromised. Suddenly, an attacker instantly has access to all the past data that was transmitted between a client and server using a particular key. Hypothetically, they could record encrypted traffic for as long as they like, waiting until they're able to get their hands on the private key. Then, once they have it, they can go back and decrypt everything they've been logging. Let's say you login to your online bank using HTTPS to protect your password as it's sent over the internet. Next year, a hacker manages to get their hands on your bank's TLS private key after the sysadmin accidentally uploads the private key to GitHub. Could a hacker use that private key to decrypt your session data from last year and get your password? Without forward secrecy, the answer is yes. Hackers can do this when perfect forward secrecy isn't present due to the nature of the key exchange between the client and the server. First, the client creates a pre-master secret, which is encrypted with the public key of the server. Then, it's sent to the server, where it's decrypted with its private key. Now, both the client and server have the pre-master secret. From this point forward, session keys are generated based on the pre-master secret, and are used for the back-and-forth communication. These session keys are called the master secret. But what if the server uses the same private key repeatedly for the pre-master encryption process? Then, if an attacker were able to steal that key, they'd be able to eavesdrop on and decrypt all the server's encrypted communications, past data included. To make this scenario happen, the attacker would monitor traffic to obtain the two random numbers used in the encryption process (one by the client and one by the server). They are transmitted in plain text, so it wouldn't be difficult. They could also obtain the encrypted pre-master secret. Since they now have the server's private key, they can decrypt the pre-master secret with it. At this point, they have all the pieces of the puzzle necessary to generate the master secret, and thus decrypt all the session data. One particular session may not contain any sensitive data, but if hackers are watching long enough then there's a good chance that they'll eventually be able to find something worth their while. Threat Prevention With Perfect Forward SecrecyHeartbleed Proves Why Perfect Forward Secrecy is NecessaryYou may remember hearing about the Heartbleed vulnerability. It was an OpenSSL bug that was discovered in 2012 and eventually patched in 2014. Hackers took advantage of a server operation called a "heartbeat request", which was usually used to determine if the server was still online. With Heartbleed, attackers told the server that they were going to send the server a 64KB heartbeat request message, but instead they sent a much smaller one. The server would reply with the short message that was originally sent to it, but since the server thought it was supposed to be replying with a longer one, it would pad the rest of the message with whatever data happened to be in its memory. The attack could be run over and over to gather large amounts of data, which could contain literally anything – passwords, personal data, session data, even the server's private key. Since the heartbeat request is a routine event it never gets logged, so you can't go back and see what data was actually sent. See the problem here? If the server's private key was in fact compromised, the hacker can intercept and decrypt traffic and no one would have any idea. With perfect forward secrecy however, this entire scenario can't happen. Protection in a Post-Quantum WorldThe proliferation of quantum computers is inevitable, and it's really just a matter of time before they are available for general use by the public at large. When that day arrives it will render many cryptographic algorithms useless, exposing data that was originally thought to be secured. So, what's to stop a hacker from collecting encrypted data now with the intention of saving it until they can get their hands on a quantum computer and crack it? The answer is nothing. In fact, many cybercriminals are currently carrying out this type of attack, commonly referred to as "harvest and decrypt." Specifically, they're carrying out the "harvest" portion of the attack in the present day, while the "decrypt" part has to wait for quantum computing. Waiting a few years is a small price to pay, however, if the end result is the decryption of high-value information like state secrets, financial records, or confidential intellectual property. Where does perfect forward secrecy come into play then? It protects your data because of the symmetric encryption methods used. A quantum computer can't break it because it won't have all the pieces of the puzzle that it needs. The session key doesn't get exchanged over the network, rather it is generated independently by both parties based on complex equations. You can read more about asymmetric & symmetric encryption, and how they work together here. Without perfect forward secrecy and symmetric encryption however, your data is vulnerable to a harvest and decrypt attack. Let's look at a standard SSL/TLS handshake, for example. If you can break the private, asymmetric private key, then you can use that to decrypt the handshake. Then you have what you need to determine the session key. How Perfect Forward Secrecy HelpsPerfect forward secrecy is a feature of SSL/TLS that prevents an attacker from being able to decrypt the data from historical or future sessions if they're able to steal the private keys used in a particular session. This is achieved by using unique session keys that are freshly generated frequently and automatically. The session keys are also not directly sent back and forth, since they are created using a method that doesn't depend on any known prior knowledge (the Diffie-Hellman key exchange protocol). Therefore, an attacker can't get the session key by decrypting the data sent during the handshake. By using unique session keys, attackers are only be able to view the data specific to a particular exchange. The risk exposure is thus greatly reduced. Hackers will be less likely to target a server utilizing perfect forward secrecy since their efforts will result in access to a relatively tiny amount of data. There's no future gain to be had for the attacker either since new parameters are being constantly generated. In practice, the website you're visiting may switch session keys every time an encrypted page is reloaded. Your phone calling app may switch keys after each call. And your messaging app may switch keys after every message sent in a conversation. As a result, the theft of one key doesn't compromise anything else – neither sensitive information nor other keys. Perfect Forward Secrecy in SSL/TLSAs you may know, part of the SSL/TLS handshake involves the server and client agreeing on the cipher suite to be used for encrypted communication. For perfect forward secrecy to be implemented, a compliant type of encryption must be used. Currently, two key exchange algorithms will work:
One of the keys (no pun intended) is that exchanges must be ephemeral, which means that the session keys are one-time use only. And since they are based on random values supplied by each party in the exchange, each new key is unique. After each use, all the encrypted information relating to the transaction is deleted and new Diffie-Hellman parameters are generated. This is what limits the use of a compromised session key to one particular session only. The other key is the Diffie Hellman key exchange protocol itself. Thanks to the complex mathematical operations behind Diffie-Hellman, the session key cannot be obtained via brute force. This is because, as we mentioned earlier, it's not actually sent sent at any point and is generated via an independent mathematical method. It makes the server's private key useless to the attacker because the corresponding public key is never used to encrypt anything. Things to Know Before Implementing Perfect Forward SecrecyBefore you deploy perfect forward secrecy on your website, there's a few things you should know:
Implementing Perfect Forward Secrecy on Your ServerThis process for enabling perfect forward secrecy support on your server is a pretty simple process, and most modern servers are already configured for it. If not, you can generally do so in four straightforward steps:
We'll get to the specific configuration process for both Nginx and Apache servers shortly. While perfect forward secrecy is easy to enable, it's also easy to incorrectly configure it. Below are a few important things to remember as you're going through the process:
After completing all of the above steps, the top of your list of cipher suites should look something like this:
Configuring Perfect Forward Secrecy on Nginx1. Locate the SSL protocol configuration with the following command: grep -r ssl_protocol /etc/nginx 2. Add the SSL protocols to your configuration: ssl_protocols TLSv1.2 TLSv1.1 TLSv1; ssl_prefer_server_ciphers on; 3. Set the correct SSL ciphers, and reference our tips in the previous section in order to pick the right ones. The example below works well on modern servers and provides a high level of security: ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH'; 4. Restart your server: sudo service nginx restart Configuring Perfect Forward Secrecy on Apache1. Locate the SSL protocol configuration with the following command: grep -i -r "SSLEngine" /etc/apache 2. Add the SSL protocols to your configuration: SSLProtocol all -SSLv2 -SSLv3 SSLHonorCipherOrder on 3. Set the correct SSL ciphers. Here we'll use the same example in our Nginx instructions above to provide high security on a modern server: ssl_ciphers 'EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH'; 4. Restart your server: apachectl -k restart Set Up Perfect Forward Secrecy to Protect Your Data Moving ForwardAs the TLS protocol has advanced, the concept of perfect forward secrecy has continued to grow in importance. With this evolution has come increased adoption for its implementation by web browsers, operating systems, communication software, and industry giants all over the world. As a result, more and more site owners can now use it to further boost security and protect their data. If you're using legacy systems without perfect forward secrecy, you should strongly consider upgrading. It will take some time and effort, but in the end it's a small price to pay for the benefits provided. You'll be a much less attractive target to attackers, since even a successful attack won't gain them much, if anything. Either way, the industry is moving in the direction of perfect forward secrecy, and it's inevitable that it will be a requirement in the future. It's up to you whether to make the switch now or wait until it's absolutely necessary. However, if you deal with sensitive information or are subject to data regulation laws, then it's nothing but a good idea to embrace perfect forward secrecy as soon as possible. |
| You are subscribed to email updates from "encrypted cell phone calls,what is the meaning of encryption,how to make encrypted phone calls" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment