Why Apple’s New iMessage Security Update Beats WhatsApp On Your Phone - Forbes
Why Apple’s New iMessage Security Update Beats WhatsApp On Your Phone - Forbes |
- Why Apple’s New iMessage Security Update Beats WhatsApp On Your Phone - Forbes
- LastPass vs. 1Password: Two top password managers, compared - CNET
- Protecting personal data under working-from-home arrangements - Lexology
| Why Apple’s New iMessage Security Update Beats WhatsApp On Your Phone - Forbes Posted: 06 Feb 2021 12:00 AM PST WhatsApp's 2 billion users can look enviously at Apple's latest iMessage update, which puts the rival messenger well ahead. Worse, seriously misleading comments from Mark Zuckerberg last week suggest he doesn't understand how far WhatsApp has now fallen behind. If you use WhatsApp on an iPhone, here's why you should be concerned.  Getty Somewhat ironically, Apple's iMessage has been notably absent among messengers reporting growth surges as millions reportedly quit WhatsApp. Ironically, because the public fracas between Apple and Facebook over WhatsApp and iMessage privacy labels was one of the initial triggers for the backlash, with iMessage coming out on top. The reason we're all writing about Telegram and Signal and not iMessage is obvious—it's for Apple users only, it doesn't extend cross platform. But iMessage is an exceptional platform, arguably with the best architecture of any, beating Signal, Wickr, Threema, Line, to say nothing of WhatsApp, Telegram and Android Messages. "I want to highlight that we increasingly see Apple as one of our biggest competitors," Mark Zuckerberg told analysts in January. "iMessage is a key linchpin of their ecosystem—which is why iMessage is the most used messaging service in the U.S." Zuckerberg was using iMessage as an example of what he says is Apple "using their dominant platform position to interfere with how our apps and other apps work." Facebook's issue is the imminent privacy update that will offer Apple's iOS users an opt-out from the device tracking that drives a critical part of its advertising business model. "Apple may say that they're doing this to help people," Zuckerberg complained, "but the moves clearly track their competitive interests." MORE FOR YOU But on that same call, Zuckerberg also showed how little he (or the person crafting his comments) understands about the innovations that have put iMessage well ahead of WhatsApp. "iMessage stores non-end-to-end encrypted backups of your messages by default unless you disable iCloud," Zuckerberg said. "So, Apple and governments have the ability to access most people's messages. So, when it comes to what matters most—protecting people's messages, I think that WhatsApp is clearly superior." Those comments were very misleading. It's actually WhatsApp that has an issue with "non-end-to-end encrypted backups" in the cloud, whether from an iPhone or Android. iMessage did have this issue, but it was addressed in 2017 with iOS 11. With the introduction of "Messages in iCloud," Apple fixed a problem no other mainstream messenger has cracked, extending end-to-end encryption to cloud backups. "iMessage is currently the only messaging app that supports syncing messages across multiple devices while still maintaining end-to-end encryption," says Talal Haj Bakry, one of the security researchers behind the infamous iOS clipboard disclosure. "When you send a message through iMessage, it is individually encrypted for each of the recipient's devices, since each device has its own public key. The same technique is used to sync messages across your own devices." Apple users can enable Messages in iCloud on all devices under their iCloud account, as long as two-factor authentication and iCloud Keychain are enabled—both basic security measures. Messages in iCloud takes secure messaging to a level no other platform can match—secure attachments, synchronized content and deletions across all devices, transfer of chat history to a new device, and a safety net if a phone is lost. There is a caveat to this extension of iMessage's end-to-end encryption to iCloud. If you have Messages in iCloud enabled and iCloud backup enabled, then a copy of the iMessage end-to-end encryption key is included in the backup. This would enable Apple to access your content to service a law enforcement warrant, but it doesn't mean you are storing a "non-end-to-end encrypted backup of your messages." Contrary to what Zuckerberg said, you don't need to "disable iCloud" to prevent this potential risk. You just need to disable the duplicate backup, a throwback to the days before continuous cloud usage and multi-device access. It's a single setting and it won't impact your daily use of your iPhone and your other Apple devices. Using iCloud is an intrinsic part of the iPhone experience—this will not be impacted. It just means that you're not storing backups of any non-Apple Apps that don't use the cloud as they work. In Apple's words, the iCloud backup helps you "set up a new device or restore information on one you already have." If you disable it, you can use Apple's new (and excellent) direct transfer instead of restoring from a backup. If you want to use an iCloud backup instead, you can backup your device and then disable automatic backups. You can even do this periodically if you want. When you turn off the iCloud backup setting, "a new [end-to-end encryption] key is generated on your device to protect future messages and isn't stored by Apple." When I asked about the inaccuracy of Zuckerberg's comments, Facebook appeared confused about the way in which iMessage and iCloud interoperate, mixing up Apple's decision to refrain from fully encrypting iCloud backups with the way iMessage extends end-to-end encryption to its own Messages in iCloud storage. If this is enabled, your message history is not included in your general iCloud backup. As Apple explains, "use iCloud Backup so that you have a copy of the information on your iPhone, iPad and iPod touch... Your backups only include information and settings stored on your device. They do not include information already stored in iCloud such as Contacts, Calendars, Bookmarks, Notes, Reminders, Voice Memos, Messages in iCloud, iCloud Photos and shared photos." 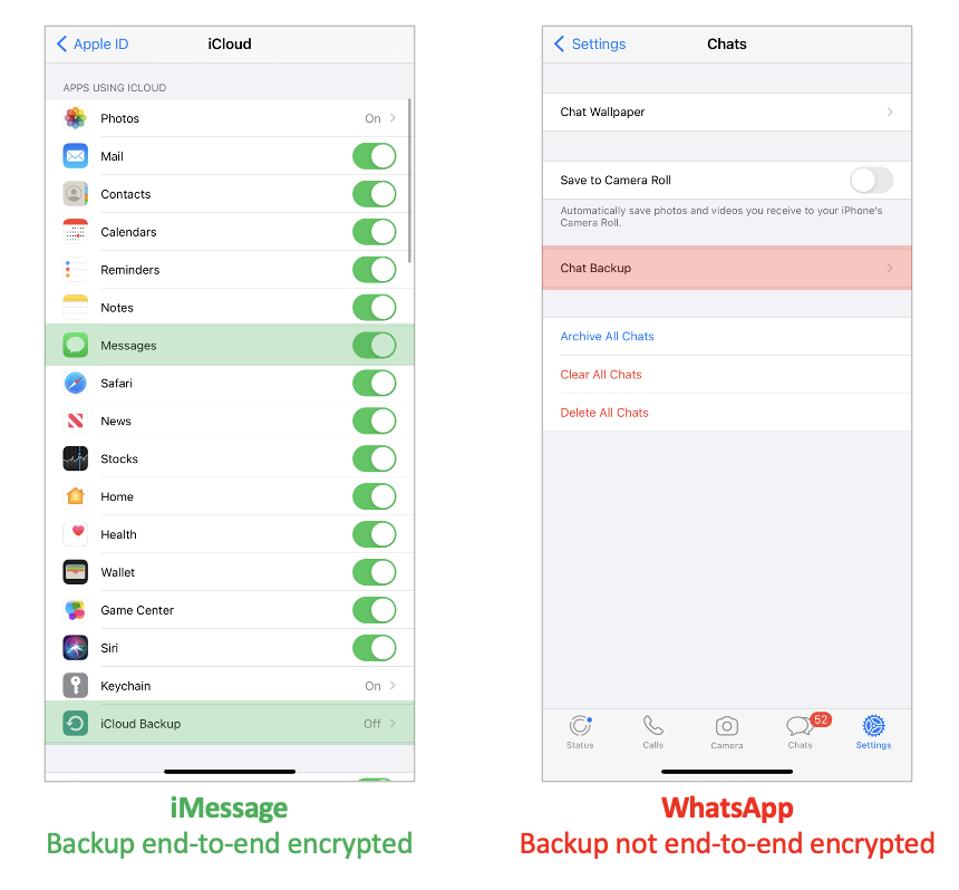 iMessage/WhatsApp iOS WhatsApp, by contrast, does not offer multi-device access or secure cloud backups or any centralized repository to save disk space. Furthermore, WhatsApp continues to recommend using unsecure cloud backups as the default way to switch to a new phone. Apple users should always opt for a direct transfer instead. So, no, WhatsApp is not "clearly superior." Its only advantage over iMessage is that it's cross-platform. 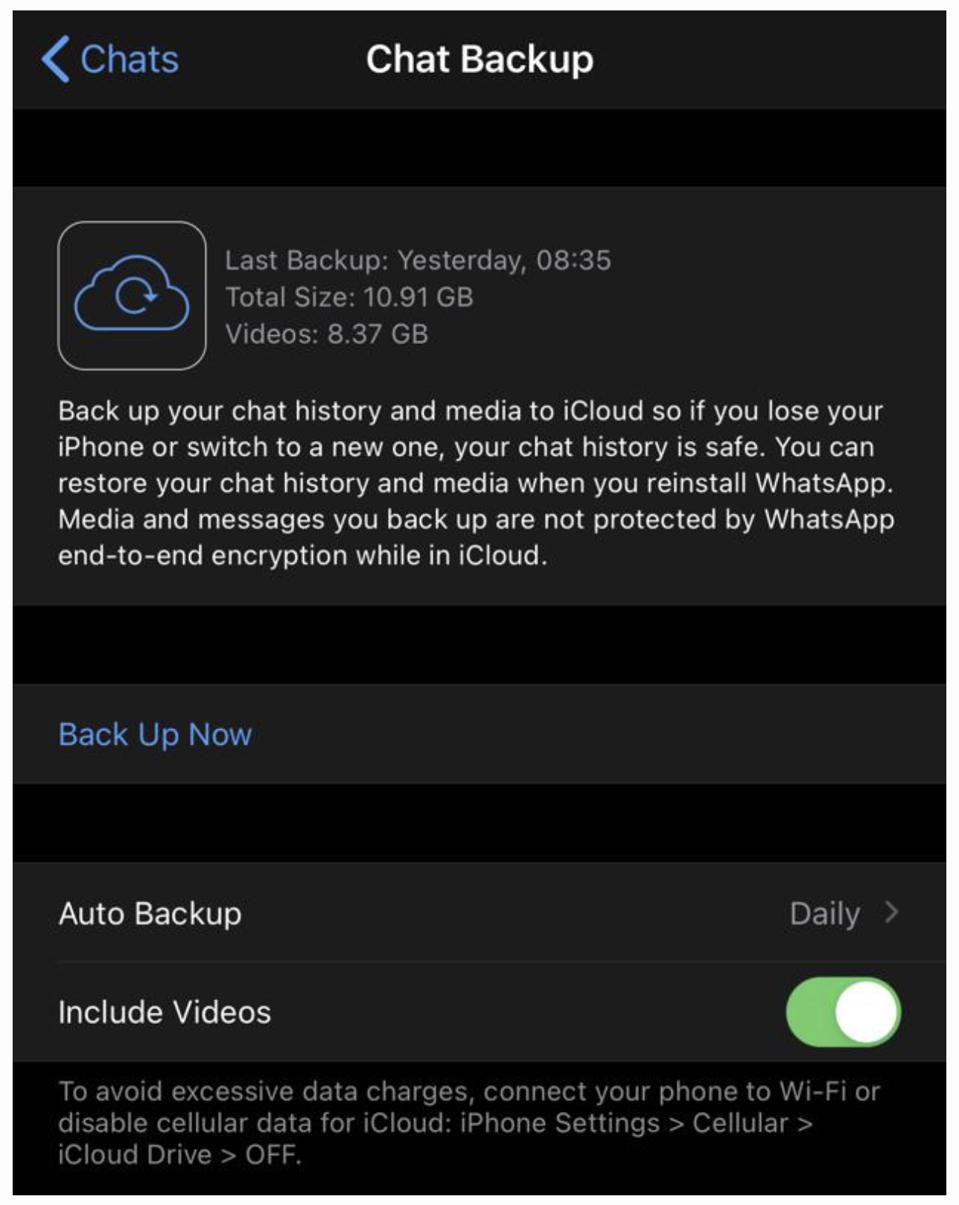 WhatsApp backup encryption warning WhatsApp/iOSResponding to Zuckerberg's confusion, ESET's Jake Moore cautioned that, "making comments like this unfortunately makes it more complicated for the user and may make people less likely to care about their data... fully encrypted and secure backups should be a default necessity, if the general user is to enable this feature and trust it." iMessage was already well ahead of WhatsApp before iOS 14—and that lead has just been significantly extended with the latest OS. The most serious risk to users from hyperscale messaging platforms is their potential to send malware-laced attachments to target devices. This has been an issue for WhatsApp and iMessage, with nation state hackers reportedly exploiting those vulnerabilities. Apple had already assured that iOS 14 introduced security improvements to prevent "zero-click" iPhone attacks, that researchers assumed used iMessage. Now we know the improvement is a new sandbox erected around iMessage that will safely contain any such threats. The disclosure was made by Samuel Groß of Google's Project Zero in a blogpost last week. After "reverse engineering" the update, he reported on "major changes [that] Apple implemented in iOS 14 which affect the security of iMessage." The change is BlastDoor, Groß explained, "a tightly sandboxed service responsible for almost all parsing of untrusted data in iMessages… and should have a significant impact on the security of iMessage and the platform as a whole. It's great to see Apple putting aside the resources... to improve end users' security." This is a serious step forward, a major improvement to iPhone security given the broad attack surface that iMessage and similar platforms provide. "This is a very impressive security enhancement made by Apple," Check Point's head of cyber research, Yaniv Balmas, tells me. "It doesn't completely mitigate the risk, but it very well addresses the robustness of iMessage based on the common attack surface used today." According to Balmas, "this delivers a significant update of the iMessage architecture, in what can only be described as a rewrite that takes into account the known 'attack plan' and tries to address each and every step of it. It shows us that Apple learned how remote zero-click attacks are designed (at least how public exploits are constructed) and targeted pretty much every part of this 'attack plan' to render it useless." But this comes with a warning, Balmas says. "It is going to make iPhone exploitation via iMessage much harder for attackers and will probably shift their attention to other methods and messaging applications like WhatsApp, Telegram, Signal or others which have not yet implemented similar mitigations into their platform/software." Put more simply, iMessage may have been largely shut down as an attack vector, but the same cannot be said for other platforms, including, critically, WhatsApp. When you add this to the marked difference in privacy labels and the Facebook data harvesting factor, there is a stark and growing difference between the two. 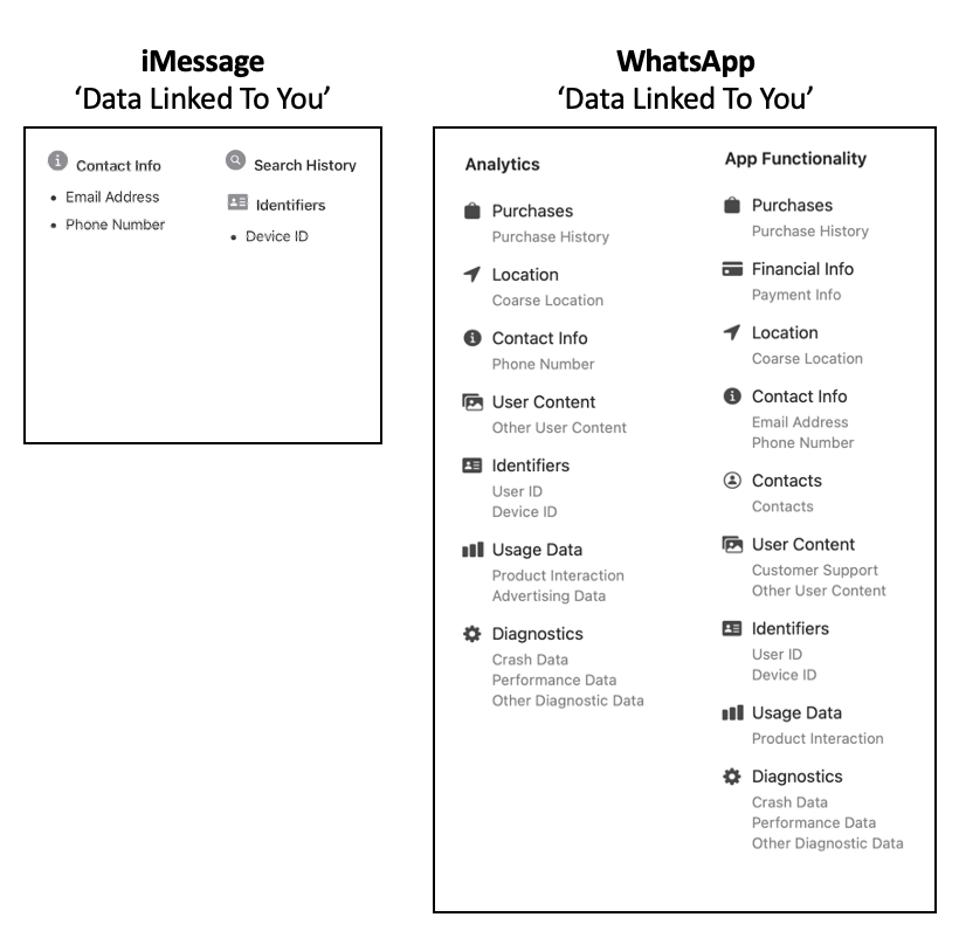 iMessage Vs WhatsApp Apple 'Privacy Labels'"Apple does some very cool things," Wickr CEO Joel Wallenstrom told me as messaging security hit the headlines in December, explaining that he tracks the company's advances in encryption. Wickr is as secure as Signal, sanctioned for use within the DoD. Wallenstrom has warned that the risks in trusting Facebook "with protecting critical IP or a warfighting unit from harm are simply too great." All that said, WhatsApp's convenience and scale cannot be overlooked. My advice is to use (cross-platform) Signal for secure messaging, but WhatsApp is safe to use and you can run that in parallel. Change these settings first, though. But, in the unlikely event iMessage was ever extended cross-platform, then given its significant architectural and security advantages, it would easily be my first choice. |
| LastPass vs. 1Password: Two top password managers, compared - CNET Posted: 03 Mar 2021 06:09 AM PST It wasn't long ago that I raised an editorial toast to the reigning champion of password managers, LastPass, recommending it not only for its broad suite of premium features but -- most crucially -- for its refusal to let down its veteran fanbase of free users, even as it faced sweeping scrutiny over an ownership change. A moment of silence, then, for our beloved fallen freeware: As of March 16, LastPass free-tier users will only be able to use the service on just one device type -- either desktop or mobile, but not both. Goodnight, sweet prince. Read more: Best password manager to use for 2021 The move tragically undermines a key security principle that's made LastPass's free version so effective at core security -- its seamless multiplatform integration. Using a password manager to boost security, perhaps more so than many other privacy products, pivots on a fulcrum of maximum user convenience. If not immediately and consistently visible during all browsing, a password manager can quickly be forgotten, and your ever-increasing number of passwords become more readily stored in a browser itself (a much less secure option). With more types of internet-connected devices in users' hands -- and with a digital divide contributing to a broader shift toward accessing the internet via phone -- internet use is becoming more fluid. So a free password manager that can't adroitly pivot between a user's devices just isn't going to cut it. Along with losing multiplatform access on March 16, people using LastPass's free tier also will lose email customer support beginning May 17. Password managers are arguably the most intimate service in our digital lives. Used well, they hold the keys to our individual kingdoms. While their encryption typically blinds password managers' parent companies from viewing your actual passwords, LastPass still offered a bunker-busting option to reset a free-tier user's master password in an emergency. Now imagine being a free-tier user, caught overseas trying to negotiate a login issue, and the company you trust with more access than any other won't even reply to an email. Ouch. These factors combine to nullify any competitive advantage its free-tier service gained LastPass, and draws it into closer combat with its peers. Meanwhile, 1Password has been closing in on the crown steadily, even as it touts only razor-thin marginal victories in key areas. We're looking forward to getting you fresh CNET reviews of 1Password and several of its peers soon. In the meantime, however, here's where the two password-privacy titans stand in comparison. Read more: Bye, LastPass. Here's how to export your data and switch to a new password manager 1Password 1Password is closing in on LastPass's lead in password management since LastPass announced its new free-tier restrictions. With its hyper-flexible platform compatibility, transparency-boosting company policies, robust security features, and silky-smooth interface -- 1Password leaves us wondering whether LastPass can hold onto its crown. Sarah Tew/CNET LastPass's legacy is swiftly souring after announcing its prized free tier will be limited to use on just one device. LastPass has never been at greater risk of being dethroned, as its security and compatibility advantages over 1Password are reduced to razor-thin marginal wins. Cost-effectiveness: 1Password for singles, LastPass for familiesBoth of these password managers are comparable in base single-subscription price, but 1Password ekes out a lead by just a few pennies. A single one-year subscription to 1Password costs $34.88 and comes with unlimited login storage, 1GB of document storage and optional two-factor authentication through Yubikey for additional security. LastPass offers the same for $35. LastPass beats 1Password on family plans, though. LastPass's family plan costs $4 a month and allows up to six users, while 1Password family plans start at $5 per month and allow only five users. Both managers offer a trial period, but LastPass is better, offering you 30 days compared to 1Password's seven. Platform compatibility: 1Password (by a nose)Both managers work on Windows, MacOS, Linux, Chrome OS, Android, iPhone and iPad. Both offer ways to work with Chrome, Firefox, Safari, Edge and Opera. On mobile, the two come to a draw. But on your laptop? 1Password's got native apps that run with its browser extensions, while LastPass just relies on browser plug-ins. This gives it a slight advantage in flexibility, but only in outlier cases. 1Password also has a Chrome OS app that lets 1Password live in your browser, and offers keyboard shortcuts for fast-searching your logins across all of its desktop options. And if you want to run a leaner version of 1Password, you can also use its mini-apps on Windows and MacOS. Because the managers are both browser-focused, the compatibility factor also gives you an idea of their overall usability -- how they look and feel for an average user. If you have a sluggish machine or are working with extremely limited processing power, LastPass's browser extensions are your better option for a speedy browsing experience. Comparing for visual ease, though, LastPass organizes your password vault in a nested folder system, while 1Password's similar system also lets you add tags to your logins. Can't remember the name of that movie site you were using last week? Just search "entertainment" in 1Password's tags to see the list of streaming sites you logged into. 1Password, like LastPass, works across Windows, MacOS, Linux, Chrome OS, Android, iPhone and iPad. 1PasswordSecurity: Both are secure, but 1Password is more transparentLastPass beats 1Password hands-down on one important security perk -- password generation. While both have random password generators, LastPass' spits out stronger passwords more quickly than 1Password with a one-click process. You can't customize the parameters of password generation like you can in 1Passwords, but that's arguably stronger since it reduces the human error factor by default. Even with less parameter customization, LastPass' generator settings can still be more easily adjusted for sites that are picky about password selection. You can also enable LastPass to automatically update your passwords. Overall, though, 1Password has the edge. Both LastPass and 1Password encrypt your logins locally to normal AES-256 standards -- meaning your passwords are encrypted before they're sent across the internet -- rather than relying on a cloud-based service to scramble them later. And LastPass does offer more convenient two-factor authentication, so you'd think it would have an advantage there, but that's not necessarily the case. 1Password also offers two-factor authentication but its onboarding process gives it a superior security advantage over LastPass. LastPass and 1Password both encrypt your logins locally before they're sent across the internet. LastPassFor LastPass, you only need a master password to create your vault and access it across all platforms. With 1Password, you use a master password to access your vault across platforms but during setup you'll need that master password plus a security key. 1Password also boosts privacy by offering a convenient QR code setup option so you don't risk exposing that key via manual typing. On Macs, you can use Touch ID to unlock 1Password, and on iOS devices you can use Face ID as well. 1Password's Watchtower feature adds another inch to its narrow competitive edge. Watchtower regularly scans the dark web for any appearance of your unique credentials, alerting you if it finds your info out-of-pocket. LastPass offers a similar feature called Dark Web Monitoring. While we're excited to get a closer comparison on the two features in the future, for now the difference appears to be that Watchtower lets you select which sections of your vault you want it to check for. This ability to create intra-account bulkheads could offer you more control over the flow of data between your manager and your credentials. While some might point out that LastPass's history of bugs and breaches makes it a less certain bet, I'd say that's a shortsighted argument: There's always a strong correlation between the popularity of any security tool and the length of its bug rap sheet. There are three more important factors to weigh: the damage incurred by the breach, the company's bug-killing and prevention process and the company's transparency. While LastPass has competently addressed these factors in its own way, LastPass came into the spotlight again in February as researchers discovered seven web trackers attached to LastPass's Android app. 1Password wins for me on this one -- for now -- because it appears to have gone further than LastPass in the depth and substance of its third-party audits, and because it was found to have zero web trackers by the same organization. Neither manager enjoys the distinction of being proudly open-source -- like BitWarden, which is racing forward to grab the baton of best free password manager -- but 1Password seems to be striving for maximum transparency. And that's a move worthy of the crown. We're looking forward to seeing who ends up with that crown in our forthcoming reviews, but for now the competition between 1Password and LastPass is just too close to call -- and that should worry LastPass regardless of the outcome. |
| Protecting personal data under working-from-home arrangements - Lexology Posted: 03 Mar 2021 02:09 AM PST  Introduction The COVID-19 pandemic has undoubtedly changed the way in which businesses are run and to a certain extent normalised remote-working arrangements. The Office of the Privacy Commissioner for Personal Data (PCPD) recently issued three guidance notes relating to working-from-home arrangements:
This article summarises the guidelines' key recommendations for employers and employees, particularly with regard to the use of videoconferencing software. Recommendations for employers Employers should assess their data security risks, including with regard to:
Employers should provide training and support to employees regarding data security techniques (eg, password management, use of encryption, secure use of WiFi and awareness about cybersecurity threats). Employers which provide employees with electronic devices should ensure data security by:
With regard to the use of virtual private networks (VPNs), the PCPD suggests using a so-called 'handshake protocol' to establish secure communication channels and using a full-tunnel VPN where possible. Employers should also implement network segmentation and enable an account lockout function for employees' remote access to their corporate networks. Recommendations for employees Employees should use only corporate electronic devices for work where possible. Some practical measures include:
Employees should avoid working in public places but if this is unavoidable, they should use screen filters. Employees should avoid using public WiFi. Employees should opt for a wired connection (instead of WiFi) where possible. Employees should also adopt up-to-date security protocols such as WiFi Protected Access (WPA) 3 or WPA2 to encrypt the data in transit and safeguard against other attacks. Employees should avoid using personal email accounts or personal instant messaging applications and be aware of phishing and malicious emails. As far as practicable, employees should avoid removing paper documents from office premises. Recommendations for use of videoconferencing software The PCPD suggests that organisations use a videoconferencing software with end-to-end encryption. Users should:
The conference host should set up a unique meeting ID and a strong password and arrange one more 'host' to handle administrative and technical issues. To prevent unauthorised access, the PCPD suggests:
The conference host should also inform all participants and obtain their consent before recording the conference and delete the records when they are no longer necessary. Videoconference participants should be aware of their backgrounds and use virtual backgrounds if necessary. They should turn off microphones when not speaking and avoid discussing personal or sensitive information as far as practicable. They should also be careful not to disclose any sensitive information to other participants when sharing screens. Comment While employers need not comply with the PCPD's guidance notes, they do provide advice on best practices for complying with data privacy laws and employers are advised to observe them. |
| You are subscribed to email updates from "best encrypted phone,full device encryption,how do i encrypt my phone" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |






Comments
Post a Comment