Top 4 mobile security threats and challenges for businesses - TechTarget
Top 4 mobile security threats and challenges for businesses - TechTarget |
- Top 4 mobile security threats and challenges for businesses - TechTarget
- This Android App Promises To Wipe Your Phone If Cops Try To Hack It - Forbes
- Why iMessage On Your iPhone Will Beat WhatsApp’s Radical New Update - Forbes
| Top 4 mobile security threats and challenges for businesses - TechTarget Posted: 11 May 2021 08:45 AM PDT You're probably reading this list on your phone. Mobile is quickly becoming one of the most used endpoints in the enterprise. However, there is a common misconception that mobile devices don't get malware or viruses, or need protection, which is just not true. According to Pew Research Center studies, 85% of Americans own and use smartphones. Businesses are expanding work-from-home practices and BYOD and COPE strategies for mobile devices to enable an on-the-go workforce. While many companies have invested in mobile device management (MDM) tools, the majority of mobile endpoints still lack protections against threats like phishing, malware and mobile-OS exploits. Here are five of the top mobile security threats, and steps IT organizations can take to protect these critical endpoints. 1. PhishingHave you noticed an increase in spam messages or an increase in spam calls? Phishing is one of the most common points of entry to start an attack. Phishing describes types of attacks wherein the bad actor poses as a reputable person or company, usually via email or phone call. Mobile devices hold a lot of data, including in email, text and other messaging apps. Many organizations invest in web gateways, proxies and next-gen firewalls for security. Attackers find holes in those solutions, such as attacking via an employee's personal email and texts instead of corporate email. In 2018, Amazon's then-CEO and Washington Post owner Jeff Bezos had his mobile phone hacked after receiving a malicious video file in a WhatsApp message. A large amount of data was copied from his device. How social engineering weaponizes phishing. Hackers can use social engineering to research users they would like to attack, looking for key attributes like the company where they work, job status, recent posts and updates. This approach is sometimes called spear phishing. That info reveals entry points for hackers to gain users' trust, usually through email or other social posts and messaging. Their aim is to get the user to share sensitive company data and information. While technology plays an important role to help proactively secure devices and users, the danger of social engineering is that it relies on human error, allowing a bad actor to infiltrate through phishing sites and malicious applications. Phishing sites are often URLs opened from a link. These malicious URLs often look similar to an authentic site to trick users into thinking they are on the legitimate site. Phishing attackers use:
Preventive measures for phishing attacks on mobile devices. The best first line of defense is to train mobile users. Inform employees and anyone else with corporate access about how phishing attacks look. Use mobile threat defense (MTD) to help secure devices and end users from phishing attacks. MTD tools secure devices through on-device scanning and detection, using advanced algorithms and filters to prevent attacks in real time. If a device does get hacked, MTD software can quickly quarantine it, preventing potential data loss. 2. Malicious applicationsMalicious apps are designed to collect personal and corporate information and transmit it to third parties. Official app stores like Apple App Store and Google Play have many checks and balances set to prevent malicious code. Apple reviews apps and Google Play has its Protect service. However, apps are known to get through these processes. Additionally, with open mobile OSes like Android, users can install applications from other sources, increasing the exposure to malicious attackers. How to block malicious app downloads. Companies can invest in MDM as a first line of defense against malicious apps. The IT admin can blocklist various applications and allowlist others for the devices enrolled in the MDM system. MDM tools also have other security policies to prevent data loss. Companies can supplement mobile device management with an MTD tool for more advanced protection in real time. MTD software detects and combats malicious behavior from an app or a zero-day attack, wherein hackers exploit a vulnerability in legitimate software before the vendor can patch it. MTD tools quarantine or disconnect the device to minimize the attack's effects. Inform mobile device users about security threats and changes to thwart both phishing and malicious app downloads. Develop a mobile device security policy so these users understand the importance of device security and how to use a device that accesses corporate data. These policies must account for all sorts of factors that users and IT admins could encounter during their workday. Include acceptable use policies, device ownership guidelines, mobile update strategy, extensions of existing security policies and more. IT admins can enforce this policy through a combination of tools and platforms such as MTD, MDM and enterprise mobility management (EMM), and soft management methods such as end-user training and documentation.  3. Insecure Wi-Fi and network spoofing You've heard not to use "Starbucks Wi-Fi" for business. The reason is spoofing and insecure networks. Attackers can easily mimic Wi-Fi networks to intercept device traffic. Open or "free" Wi-Fi hotspots are notorious for man-in-the-middle and similar attacks where the bad actor intercepts and eavesdrops on device network traffic. The user, in many cases, does not need to perform any actions on the device for the attack to happen. For example, a smartphone connects to a known network, like a coffee shop. The smartphone will always try to automatically join a known network if it is in range again. A hacker can easily impersonate -- called spoofing -- the identical Wi-Fi Service Set IDentifier (SSID), which is the network's name. Hackers use this method to collect company information undetected by the mobile device user. How to stop network spoofing. IT organizations can use MDM to enforce Wi-Fi policies on corporate-only and BYO devices, including allowlisting certain SSIDs. Additionally, an MDM can enforce data loss protection and encryption policies to secure mobile devices. Businesses can also supplement an MDM setup with an MTD tool for more advanced detection of malicious behavior, like man-in-the-middle attacks. 4. Poor update habits for devices and appsKeeping endpoints and applications updated is one of the best ways to ensure company data and information is secure. Updates and patches fall under the category of cyber hygiene, along with complex passwords and multifactor authentication. Unpatched devices and applications often contain exploits and vulnerabilities that attackers try to use to collect personal and corporate data. How to stay up to date. Both Apple and Google publish updates to patch security vulnerabilities and exploits to prevent future attacks, limiting the potential for zero-day vulnerabilities. For Android, Google has started publishing monthly security patches that other device manufacturers can implement for their customers. Apple is also proactive with multiple mobile OS updates a year, ensuring devices are secure. Companies can enforce device update policies, as well as manage application updates, via an MDM tool. |
| This Android App Promises To Wipe Your Phone If Cops Try To Hack It - Forbes Posted: 07 May 2021 02:50 AM PDT  Police won't be able to retrieve evidence from an Android phone if it's running LockUp, its coder ... [+] Rafael Henrique/SOPA Images/LightRocket via Getty ImagesIf the police get hold of a smartphone and they have a warrant to search it, they'll often turn to a tool from Israeli company Cellebrite that can hack into it and download the data within. But on Friday a security researcher is releasing an app that he says can detect when a Cellebrite is about to raid the device, turn the phone off and wipe it. It could prove to be a controversial release, given that criminals could use it to erase evidence. But Matt Bergin, the researcher at security company KoreLogic who created the tool, says Cellebrite could easily update its phone-hacking tech to stop his app—dubbed LockUp—from working. And he hopes his work, which also included finding now-patched security weaknesses in the Cellebrite, will bring to light the need for more tests on police forensics tools to ensure they're secure and able to detect evidence tampering. "My goal is not to arm criminals. It's more to educate the general public and make it aware that we need policy changes to address these issues," Bergin added. "I hope we see changes in policy that require the types of testing that I do." Bergin was able to carry out his research on a two-year-old Cellebrite Universal Forensic Extraction Device (UFED) acquired from eBay, a place where the tech, supposedly only to be used by police, has been spotted on sale before. He found a handful of security issues. First, he found a problem with the way in which Cellebrite handled its encryption keys. One of those keys—an authentication key—was supposed to guarantee that the Cellebrite device was the only one to carry out a forensic search on a phone, but they were the same for every unique Cellebrite system. "The problem with that is now, when evidence collected by the UFED is being introduced in the courts, you can't really say that it was the Cellebrite itself that did the collecting of the content," Bergin explained. He also found keys that let him pull all the code used to exploit vulnerabilities in Android, all of which appeared to have been fixed on Google's operating system. As for how LockUp works, it looks for a Cellebrite application called Mr. Meseeks, named after a character in animated TV comedy Rick & Morty, which is downloaded on an Android phone when the forensics tech is about to search a device. LockUp looks at the certificate for each new app installed on a device and if it matches the one for Mr. Meseeks, it'll factory-reset the phone. Though his test Cellebrite system was two years old, Bergin thinks that LockUp will still work as he believes modern versions still use Mr. Meseeks. He's releasing LockUp on Friday during a talk at BlackHat Asia. MORE FOR YOU The code release, on Github, could interest Cellebrite's global customers, which include many of the U.S.' federal government and local police agencies, including Immigration Customs Enforcement (ICE), the FBI, the NYPD and Europol. Cellebrite fixed the encryption issues highlighted by Bergin in 2020. A company spokesperson added: "The demonstrated proof-of-concept application is not considered a vulnerability by KoreLogic or Cellebrite. It is a shared scenario for any forensic software performing app-based extractions. Cellebrite already offers advanced and deeper collection methods that are not susceptible to this type of application. Importantly, our methods can detect and mitigate such attempts, noting the existence of an anti-forensic measure as part of the produced report." Regarding the ability for people to purchase its devices on eBay and other secondhand markets, Cellebrite said, "Under no circumstances may a customer resell, redistribute, transfer or sublicense Cellebrite's technology to any third party without expressed written permission from Cellebrite . . . keep in mind that on the rare occasion when someone is able to obtain a device on a secondary market, the software is outdated and not able to receive updates." The release of LockUp comes just a week after Moxie Marlinspike, founder of the encrypted messaging app Signal, looked into the security of a Cellebrite device and claimed to be able to hack a Cellebrite by including malicious code in an app searched by the forensic tool. The LockUp app may appeal to those who wouldn't consider themselves criminal, but could be under surveillance from their government. Cellebrite devices have allegedly been spotted in use on journalists in countries with poor records on human rights. On Wednesday, the Committee for the Protection of Journalists reported that Oratile Dikologang, digital editor and cofounder of the Botswana People's Daily News website, had his phone searched with a Cellebrite device. Dikologang was accused of writing "offensive" posts on Facebook and during interrogation gave over his password. A Cellebrite and the Forensic Toolkit from U.S.-based AccessData were then used to grab all the data inside. In response to the CPJ's reporting, AccessData didn't respond to multiple requests from the publication, while a Cellebrite spokesperson said: "We have multiple checks and balances to ensure our technology is used as intended. We require that agencies and governments that use our technology uphold the standards of international human rights law. . . . When our technology is used in a manner that does not meet international law or does not comply with Cellebrite's values, we take swift and appropriate action, including terminating agreements." |
| Why iMessage On Your iPhone Will Beat WhatsApp’s Radical New Update - Forbes Posted: 08 May 2021 03:40 AM PDT Has WhatsApp just blown its opportunity to catch-up with iMessage, just as millions consider quitting? And as Facebook versus Apple continues, is iMessage about to become an even more serious threat? Here's what you need to know.  iMessage Vs WhatsApp GettyWhatsApp is playing catch-up with its rivals on security and functionality—especially iMessage. So much so, that if Apple's stock messenger launched an Android app, it would easily become the best cross-platform option on the market. WhatsApp versus iMessage has been one of the highlights in the battle between Facebook and Apple. "We increasingly see Apple as one of our biggest competitors," Mark Zuckerberg has said. "iMessage is a key linchpin of their ecosystem—which is why iMessage is the most used messaging service in the U.S." Now, as details on WhatsApp's biggest ever update continue to leak this week, there is some seriously bad news for its 2 billion users. Far from catapulting WhatsApp ahead of iMessage, the leaked code appears to leave Facebook's messaging giant far behind—even before Apple's major iMessage update later this year. We've known for some time that WhatsApp is addressing its biggest feature gap against iMessage (as well as Signal, Telegram, RCS, even Facebook Messenger). Multiple "linked devices" is now reportedly in test. This would allow you to run the same WhatsApp account from your phone, tablet and computer, and you wouldn't need to keep your phone switched on and connected to make it work. MORE FOR YOU  WhatsApp linked devices WABetaInfoBut iMessage is much more than linked devices, it's a fully synchronized ecosystem that is fully protected by end-to-end encryption. "iCloud keeps your entire message history updated and available on all of your devices," Apple explains. "You will always have the same view everywhere you use iMessage. If you have deleted a message, photo or conversation on one device, it will be removed from all of your devices." As more details on WhatsApp's alternative leak, it is becoming clear that it will fall way short. A new report out this week, based on code leaking from the latest WhatsApp beta, appears to confirm that WhatsApp will not match this functionality, that this update is not as "radical" as hoped. There is no full-scale, live and seamless sync. What this does seem to as regard syncing is a link back to the primary device, aligning pinned chats and starred messages more than content—deletions seem to be excluded. Unlike iMessage, deleting content on one device will not do the same on others, which is a security gap. I have approached WhatsApp for any comments on this update. 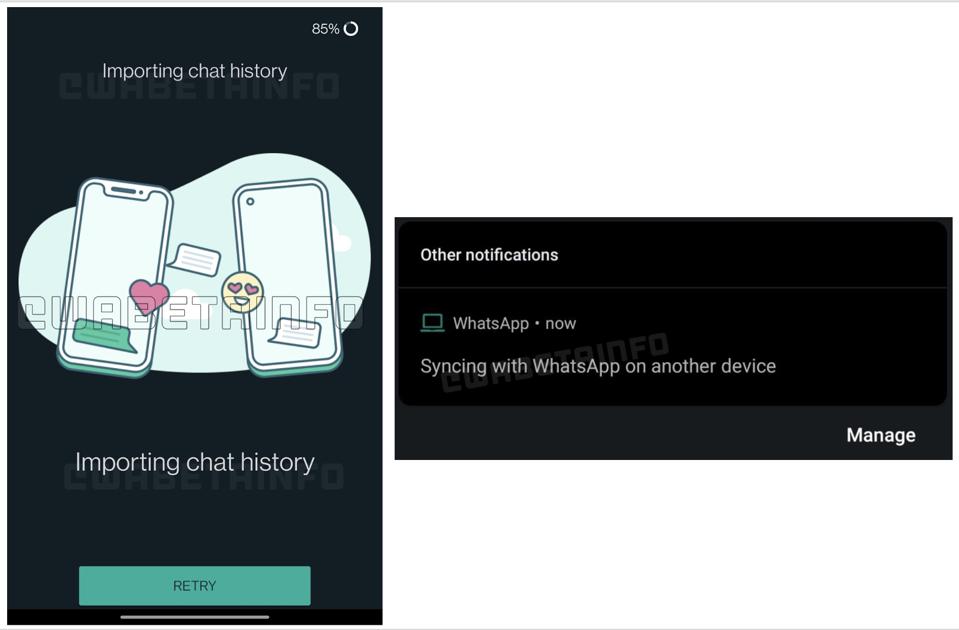 WhatsApp chat migration and sync. WABetaInfoApple's iMessage architecture also does away with the need for a backup as such. Essentially, you run a live, always-on backup using iCloud to keep all your devices fully in-sync. You can add new endpoints or allow your existing devices to catch-up when connecting. You don't have the concept of a daily backup. WhatsApp already has a major issue with backups—they currently fall outside its end-to-end encryption when using Apple's or Google's cloud. And while it does appear that WhatsApp is developing an encryption option for such backups, that's still an archaic concept in the world of messaging as a cloud-based service. Before you email me to argue differently, let's acknowledge the serious caveat in Apple's approach. If a user also enables a generic "iCloud Backup," then Apple will store a copy of iMessage's end-to-end encryption key. This undermines everything I've just said. So, put simply, disable the generic iCloud backup and you're fine.  iMessage Vs WhatsApp WhatsApp/iMessage/iCloudNow let's turn to account security. WhatsApp has a serious issue verifying new devices. Non-mandatory 2FA and a surge in social engineering hacks to steal SMS one-time codes that activate accounts on a phone. Again, shifting to a trusted family of devices design, as with Apple's ecosystem, would end this vulnerability. Mandatory 2FA and the idea that a logged-in WhatsApp app is needed to enable another is highly secure. The best solution to resolve all these major gaps is a fluid sync across multiple end-to-end encrypted endpoints, essentially a live backup to which you can add a new endpoint, using your other trusted logins to avow a new one. This is iMessage and there's no reason why WhatsApp could not invest in a similar architecture. Each endpoint would have a decryption key for your chats and groups. If you lose your phone, no drama—your other endpoints remain live, you can simply replace the device and it will sync your message history. Telegram and Facebook Messenger offer multi-device access but are not fully encrypted by default, with major security and privacy gaps. Google's beta RCS encryption is heavily restricted. Even Signal doesn't sync between endpoints, with each new device simply pulling messages only when up and running. There are security advantages to this, but for 99.999% of users, iMessage's approach is ideal. These days, with most of your apps and services running their own cloud syncs, you don't really need a general cloud backup. Even setting up a new iPhone is much better done with a direct device-to-device transfer. But, all that said, what iMessage doesn't have are any Android users. The iPhone-maker did consider adding an Android client almost a decade ago, but decided it might compromise some of the iPhone's stickiness and so backed away. There is speculation that when Apple's iOS 15 is released in the fall, "iMessage will become more like a social network so that Apple can compete with WhatsApp." What that means we're key to find out. But, fairly obviously, if iMessage doesn't shock the world and launch an Android app after all, then it can't compete with WhatsApp on 70% of the world's smartphone. "I use an Android," WhatsApp CEO Will Cathcart said recently, "because if you look at WhatsApp's user base, we are very Android heavy." But in the U.S., it's different, where Cathcart acknowledged that "most people have an iPhone, and the messaging experience works better on iMessage if everyone else has an iPhone." But iMessage versus WhatsApp isn't just about the 2 billion, it's also about the millions in battleground markets, where Facebook's plans to monetize WhatsApp, to add payments and shopping and hosted business communications, will be shaped. And with this in mind, there's still one area where WhatsApp is much, much worse than iMessage and which won't be addresses with feature updates—privacy. Let's remember, it was the iMessage versus WhatsApp privacy label comparison that kick-started much of the Facebook backlash with WhatsApp users earlier this year. And despite its PR campaign, nothing has really changed. 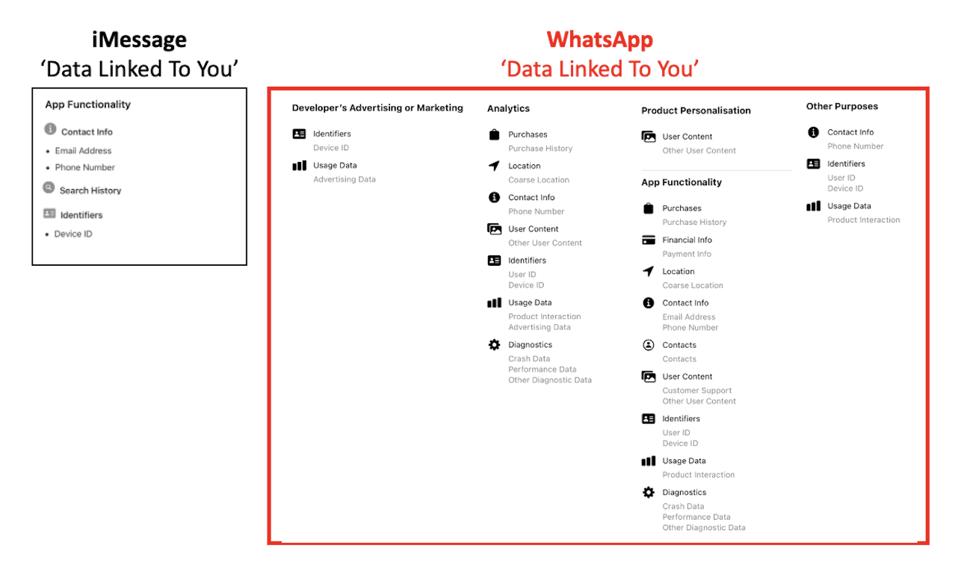 iMessage Vs WhatsApp Apple privacy LabelsOf course, before iOS 15 sees the light of day, there's the small matter of WhatsApp's forced change of terms as mandated by Facebook. This is now less than a week away. And despite reports to the contrary, WhatsApp has not backtracked on the stark reality of this update. Users will need to accept the new terms or will lose functionality, eventually having no use of their accounts. The reminders some users are now seeing will become persistent sometime after May 15, "at that time," WhatsApp says, "you'll encounter limited functionality on WhatsApp until you accept the updates. This will not happen to all users at the same time... After a few weeks of limited functionality, you won't be able to receive incoming calls or notifications and WhatsApp will stop sending messages and calls to your phone." And while WhatsApp still says it will not delete these essentially useless accounts, it also points out that users should "keep in mind that separately, our existing policy related to inactive users will apply." This says that "WhatsApp accounts are generally deleted after 120 days of inactivity [when] the user hasn't connected to WhatsApp." There's a lot at stake for WhatsApp this year—it has certainly been its worst year as regards PR and fending off attacks from rivals over its Facebook parentage. Quite how the combination of new functionality and a better, more secure architecture will play against the impending doom of tighter Facebook integration, remains to be seen. Meanwhile, if Apple really wants to strike a blow against Facebook and its data harvesting practices, then it should revisit those plans to launch an iMessage app for Android. It's hard to overstate just how damaging this would be for WhatsApp and Facebook Messenger and could, in an instant, disrupt the entire messaging landscape. Grab your popcorn, the running battle between Facebook and Apple isn't ending anytime soon. |
| You are subscribed to email updates from "mobile phone security,encryption policy android,how good is android encryption" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment