WhatsApp vs iMessage: Which Messaging Service Is Better? - ValueWalk
WhatsApp vs iMessage: Which Messaging Service Is Better? - ValueWalk |
- WhatsApp vs iMessage: Which Messaging Service Is Better? - ValueWalk
- Private Internet Access review: A great service with a reputation for protecting user privacy - Macworld
- Yubico's tiny YubiKey has the future of security all locked up - Fast Company
| WhatsApp vs iMessage: Which Messaging Service Is Better? - ValueWalk Posted: 18 Jul 2019 12:00 AM PDT  Last year, Facebook CEO Mark Zuckerberg told investors that Apple's iMessage service was by far Facebook's "biggest competitor" in messaging. In countries such as the US where Apple's devices dominate, Facebook Messenger and WhatsApp have seen slow adoption. But WhatsApp has amassed more than 1.5 billion users across the globe. In this WhatsApp vs iMessage comparison, let's check out how the two services stack up. Services like WhatsApp and iMessage have become increasingly important to Facebook and Apple as user communication continues to shift from publicly shared content to private messaging. The two services are pretty similar in most aspects. They both allow users to send messages, photos, videos, voice recordings, and emojis to their friends and family. Users can send to a contact individually or as part of group messages. They both let users make voice and video calls to other users. WhatsApp vs iMessage: Availability across platforms The iMessage app comes pre-installed on iPhones, iPads, iPods, Macs, and Apple Watch. It's one of the most popular apps in Apple's ecosystem. It can sync your messages across all Apple devices logged into your Apple account. It's one of the biggest strengths of iMessage, as well as one of its biggest weaknesses. Apple doesn't offer an iMessage web client, meaning you can't access your messages on a PC. Apple's messaging service is also not available on Android or any other platform outside its ecosystem. It's useful only if your friends and family members are invested in Apple's ecosystem. In contrast, WhatsApp is a cross-platform service. It's available on iOS, Android, Windows 10, macOS, and even BlackBerry and Symbian platforms. You can download WhatsApp on your device and get started within minutes. There is a good chance most of your friends are already using it. If not, you can send them a quick invite to join the service. WhatsApp is linked to your phone number, which means you can use it only on one device. If you want to use it on multiple devices, you have to scan the QR code from your smartphone. WhatsApp uses mirroring, meaning your phone must have a consistent Internet connection if you want to use it from your computer or web browser. To use it from your web browser, go to web.whatsapp.com and scan the QR code using the smartphone app. WhatsApp vs iMessage: User interface Both services have a clean interface. They are easy to navigate and get started. If you use iMessage, your friends don't have to "sign up" for the service (assuming they use Apple devices). You can message them using their Apple ID or phone number and they'll get your message. Apple's service offers iMessage apps to let you collaborate with others without having to leave the app. The iMessage users can place audio calls or FaceTime calls by tapping on the contact name or number at the top of the conversation. Users can see clear indicators in iMessage for message delivery and receipt. They can also use Animoji to create and share animated characters that can use your voice and mirror your facial expressions. There is also the Memoji feature that matches your personality and mood. WhatsApp doesn't yet have something similar to Memoji or Animoji. But it offers many of the same features as iMessage. When you setup your WhatsApp, it gets access to your contacts and automatically shows you all contacts using WhatsApp. You can send messages, photos, videos, voice recordings, and even documents to your friends individually or in a group. It also allows you to make audio or video calls over the Internet. WhatsApp users can also see when someone is online and when the message is sent, delivered or seen. Of course, you can choose to hide your Last Seen status, read receipts, and other things, but then you'll also not be able to see the Last Seen or read receipts of your friends. WhatsApp also shows you detailed storage and network usage. WhatsApp vs iMessage: Security Both services use end-to-end encryption to ensure your data is secure. It ensures that your messages are not seen by the governments, hackers, or providers. It's worth pointing out that Apple encrypts messages sent to and from devices only within its ecosystem. If you use iMessage to message an Android user, that message is not encrypted. If you use iCloud backup, iMessage data is backed up by default. You have to toggle it off from settings to prevent iCloud backup of iMessage data. Backing up iMessage data on iCloud means Apple keeps the encryption keys for the backup, not the user. It effectively negates the end-to-end encryption. WhatsApp does a better job at security. It uses end-to-end encryption for all conversations including voice and video calls. But unlike iMessage, it doesn't keep encryption keys with itself. It means the messages cannot be accessed by anybody other than the sender and the recipient. Even WhatsApp can't access your conversations because it doesn't store your messages. WhatsApp offers a security code that senders and recipients can use to verify that they are getting messages from someone they know, not someone else posing as your friend. But it's not perfect. WhatsApp shares the messaging metadata with Facebook, which doesn't have a great track record in terms of user privacy and security. If you have used the same phone number for both Facebook and WhatsApp, your profiles could be linked. So, which one is better? Apple's iMessage is loaded with tons of features. It's an excellent choice for people whose friends and family members are tied to the Apple ecosystem. If most of your friends use Android or Windows devices, WhatsApp could be a better choice. |
| Posted: 05 Aug 2019 03:00 AM PDT One of the more popular options in the VPN space is Private Internet Access. It made a name for itself by being notoriously cheap at around $40 per year, despite its desktop interface being kind of terrible at the time. These days you won't find PIA as cheap as that, but the desktop app is a lot nicer. Plus, you get a ton of country options, good speeds, and for power users the ability to tweak your connection security.
Private Internet Access: Security, software, servers, and speed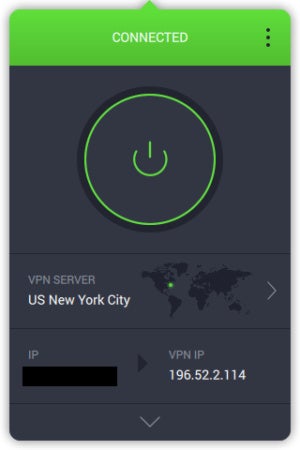 IDG IDG PIA's default view on Mac. Unlike a lot of other desktop apps, PIA allows users to adjust some of their encryption options beyond just the protocol. By default, PIA uses OpenVPN over UDP, AES-128 data encryption, GCM for data authentication, and RSA-2048 for the handshake. If you want to change any of that, you can switch UDP to TCP, and data encryption can be changed to AES-256 (CBC or GCM), as well as AES–128 (CBC). If you choose one of the CBC options, you'll also be able to customize your data authentication and handshake. GCM, however, only lets you adjust the handshake. Most users should just leave this section as is, but PIA has a helpful guide on its site to explain the advantages and disadvantages of various settings tweaks. The macOS app for PIA is very similar to the Windows version. It's a long single column accessible from the top right of the screen in macOS. There's a large power button to turn your VPN connection on and off, and below that is the current country connection. Expand the window, and you can see a section with customizable quick connect options (for up to five different countries), the current performance of your connection, total bandwidth used, and some icons to quickly access parts of PIA's settings. 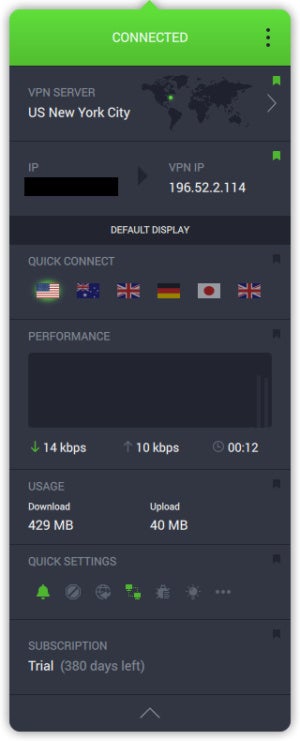 IDG IDG PIA's expanded view on Mac. Overall, it's a great and simple app that offers enough information for power users, but organized in such a way that novices can ignore it entirely to avoid confusion. When you dive into the various country connections, you can see the ping times from each country to your location. We love this feature as it allows you to choose the fastest connection possible. For some countries there is only one region option, while others such as the United Kingdom, Australia, Canada, and the United States, have multiple options with ping times for each. PIA doesn't offer much in the way of extra services. The only thing other than the various connections is PIA Mace, an ad, tracker, and malware blocker. This feature is off by default, but you can turn it on at Settings > Privacy. There's also a VPN kill switch that shuts down your internet connection if you lose contact with the VPN. That way your online activity won't be revealed outside of your secure connection. It's a nice feature, but remember these features are not 100 percent effective at hiding your true location from third parties. PIA offers more than 3,000 servers in 32 countries. It supports up to 10 simultaneous connections at once, which is fantastic. Most services offer up to five or six maximum. Ten is more than enough to cover most people's devices at home. PIA is owned by London Trust Media, which is based in Denver, CO. Its chairman is Andrew Lee and the CEO is Ted Kim. PIA doesn't keep logs and writes all user data to PIA supports apps for Windows, macOS, Linux, Android, and iOS. During speed tests, we saw some pretty good results. They weren't always jaw dropping, but they were decent overall. Speeds were particularly good in the U.S., UK, and Germany. PIA pricing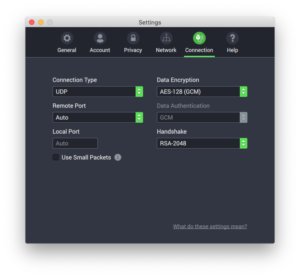 IDG IDG PIA's protocol settings. PIA has three pricing tiers. A one-year subscription will set you back $72 per year, which is a little on the high side, but it does let you connect up to 10 devices at once, which makes the higher price more palatable. If you want to make a two-year commitment it will cost $84 (about $42 per year), and a month-to-month commitment is $10 per month. The month-to-month option is typically high among VPNs to encourage users to choose a one- or two-year commitment. If you're really intent on a month-to-month optio, I recommend looking at Mullvad, which is $6 per month as of this writing. Bottom linePIA is a great service, with a more generous simultaneous device allotment than most services. It also has a good number of country options, a very large server count, and a tested reputation for protecting user privacy. If you need a simple, no-nonsense VPN option PIA is a great choice for both novices and power users. Editor's Note: Because online services are often iterative, gaining new features and performance improvements over time, this review is subject to change in order to accurately reflect the current state of the service. Any changes to text or our final review verdict will be noted at the top of this article. |
| Yubico's tiny YubiKey has the future of security all locked up - Fast Company Posted: 30 Jul 2019 12:00 AM PDT Say "YubiKey" aloud, and you might get a sense of the intention of Yubico, the company behind this USB hardware-based authentication key that's stormed the internet by being very clever and working with open standards. Until recently, I'd only silently read the product name and didn't get the pun until I spoke it—ubiquity. The YubiKey comes in several models, all of which conform to a relatively new approach to validating identity online that relies on unique encryption keys tied to a specific site or app. Yubico has pushed for standardization, enlisting big partners and multiple alliances along the way. Most recently the World Wide Web Consortium (W3C) adopted a standard that Yubico helped develop that directly embeds this encryption approach into web browsers, making it vastly simpler for sites to implement it. As Yubico's technology spreads across the net, ordinary mortals tired of credential theft, phishing, and other fraud may finally latch onto a YubiKey for simplicity and security. Security geeks are already well aware of it. Some I know have recommended one to their less savvy relatives, even when they have to provide setup and hand-holding. Google long ago implemented an early version of what's called Web Authentication (or WebAuthn for short), and Microsoft activated support in November 2018. Firefox incorporated WebAuthn in May 2018. Apple is often a holdout in certain kinds of standards and interoperability in favor of its own, which it considers more secure and more privacy-focused solutions. And yet the company put WebAuthn support into the publicly available technology-preview version of Safari for Mac in December 2018, and it will likely remain in place for the macOS update in the third quarter of 2019. (Apple declined to provide more information about its plans to incorporate the technology into iOS or macOS.) Yubico has paired this standards success with the release of an iPhone- and iPad-compatible USB token that has Apple's Lightning adapter on one end and a USB-C plug on the other. Released as a technology preview, it works with the Brave browser for iOS and the Safari preview and other browsers in macOS. Hundreds of services currently work with WebAuthn and previous standards on which it was built; tens of thousands should follow.  Even Yubico isn't in business purely to sell security hardware. "We never started the company to build the YubiKey," says Jerrod Chong, Yubico's chief solutions officer. Rather, he says, the goal was to provide a broad-based way to keep everyone safe on the internet. It's a lofty, idealistic goal—and it's succeeding. It's all in the timingWith a YubiKey plugged into your computer, tablet, or phone, proving your identity to an app or site is a matter of first enrolling your device using unique, encrypted information buried in the key, and then on future logins, tapping a button. (Some sites may require a regular login plus the button tap each time; others can opt for the token to reauthenticate.) All the cryptographic jiggery-pokery happens invisibly, protecting you from fake sites and your account from password thieves and even sophisticated attacks such as two-factor authentication (2FA) hijacking. While pursuing that mission, YubiKey has grown from 30 to 200 staffers over the last several years and has raised $30 million from investors. Crunchbase estimates that the privately-held company so far earns a modest $10 million in sales in a space that could be worth billions. At the core of the standards Yubico has helped develop and gives away is a simple idea: Users should control and own the encryption keys that let them validate their identity with apps, sites, and services. No middleman has access to keys nor the contents of communications using them, and no central infrastructure is required. Tech giants, of course, might be happy to serve as intermediaries between consumers and the apps and services they use. But Yubico's decentralized approach hasn't scared off big companies. Instead, more have rushed in, with the W3C's approval cementing its future. Yubico's approach to security has enjoyed such success in part because of a quirk in timing. The company developed its login standards and specialized hardware just before makers of smartphones and other devices began to build in features focused on local, device-based authentication, such as fingerprint and face scanning and related technology. As Yubico has grown and spread the approach it helped pioneer, those manufacturers have signed on to broad standards rather than producing proprietary alternatives, perhaps due to the growing public mood in favor of digital privacy and against consolidating power in specific companies' hands. At various times in recent years, Apple, Google, and Microsoft have decided to protect mobile and desktop platforms by adding secure chips that act as one-way conduits and private safes for data like encryption keys and credit cards. Apple embeds these chips in its own gear, as does Google for its Pixel phones; both Google and Microsoft support them in their operating systems and encourage hardware manufacturers to embrace them. These enclaves are the heart of modern biometrics, mobile payment systems, and much more. The secure chips built into devices encode the shape of your face, the whorls on your fingertips, the fry in your voice, and the code on your credit card. Even the makers of that hardware can't extract the data. That became an issue when the FBI asked Apple to build a custom version of iOS that would give the agency greater odds of cracking codes secured by silicon. (Apple demurred and resisted in court; the FBI alleged that it found another way.) However, while these security chips may be involved in authenticating you in native apps, for online purchases, and via device-based logins (such as Apple's Touch ID and Face ID), they don't bridge the gap to the web, where—despite app makers' best efforts—people still spend much of their time. A web-based email service, for example, can't get direct access to a chip such as Apple's Secure Enclave to safely log you in. That's where Yubico fits in—literally. A security chip in a portable packageYubiKeys and similar devices rely on standards that put a security chip in an external package and make it a company-, platform-, and device-agnostic validation method. The keys can work with any device and software that are USB-savvy. This is possible because of the FIDO (Fast ID Online) Alliance. Founded in 2012 to provide a device-locked, cryptographic alternative to passwords, it increased its portfolio in 2013 when Yubico, Google, and their semiconductor partner NXN joined, bringing a hardware-based technology that could provide a second authentication factor. This notion, released as Universal 2nd Factor (U2F), relies on public-key cryptography, where the encryption secret is split into a pair of public and private keys. At sites and services that support U2F, users enroll by logging in and verifying themselves, and then using the U2F device to generate a unique key pair. The remote site retains the public key portion.  This turns conventional two-factor authentication on its head. If a site uses a one-time code or a shared secret to authenticate users—as huge numbers of them do—the information could be intercepted by a third party and is subject to other vulnerabilities. By vesting ownership with the user and using a cryptographic exchange, Yubico's approach dramatically improves the integrity of a second factor in protecting a user's account. Until recent years, U2F had relatively limited adoption, outside of specific apps and websites that required use of the Google Chrome browser. While that list of sites increasingly included big consumer and enterprise players—like Dropbox, Eve Online, and Salesforce—each site or app had to write what was effectively a custom integration. The big tech companies seemed to be more interested in pushing "Sign In With" single-sign-on options that let users rely on their accounts to log in elsewhere. That included the operating-system makers like Microsoft and Google (plus Apple this fall), and a host of others, including Amazon, Facebook, and Twitter. Those unified sign-ins are not only ecosystem-dependent, leading to lock-in; they don't offer a whit more security. In fact, they establish even worse single points of failure. The standard behind the keyBig firms typically want to consolidate and capture users. This time appears to be different, at least for operating-system and browser makers. Yubico's long-held desire to bring secure authentication to websites has come to fruition. In 2016, FIDO brought the web portion of its second-generation standards to the W3C, which released a final version in March 2019. WebAuthn puts the necessary pieces into web browsers for authentication of logins over the web outside of the browser. This allows for plug-in hardware such as the YubiKey. It also permits the use of built-in security chips tied to a specific computer or mobile device. For web developers at sites large and small, this shifts the heavy lifting of using a YubiKey or similar authenticator to the browser and makes implementation the same across all browsers that support the standard. It puts authentication on the same footing as animating objects on a page or storing data locally in a browser.  The company's biggest threat could come from its success. Because WebAuthn allows the use of existing secure enclaves, phone makers may eventually build Yubikey-like functionality into phones and other devices, allowing likely YubiKey buyers to avoid a separate purchase. And yet the same forces that would lead people to want authentication outside of a big company's intermediation might also lead some of them to prefer a portable, personal, third-party device from a neutral company—a security company that's thrived by opening its doors wide. |
| You are subscribed to email updates from "encrypted telephone,encrypted data on iphone,should you encrypt your phone" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment