December 20, 2019. - The CyberWire
December 20, 2019. - The CyberWire |
- December 20, 2019. - The CyberWire
- 10 Nastiest Malware Of 2019 That Shook Cybersecurity World - Fossbytes
- Surfshark's holiday VPN deal gifts you one free month with 2-year plan - iMore
- NordLocker Review – A Reliable, Comprehensive & Easy-To-Use File Encryption Solution! - TechNadu
| December 20, 2019. - The CyberWire Posted: 20 Dec 2019 10:39 AM PST Cyber Attacks, Threats, and VulnerabilitiesIsraeli spyware allegedly used to target Pakistani officials' phones (the Guardian) WhatsApp hackers may have used NSO Group technology for 'state-on-state' espionage Stalking Stalkerware: A Deep Dive Into FlexiSPY (Juniper Networks) In October, the FTC announced it had reached a settlement effectively shutting down Retina-X Studios, maker of MobileSpy, PhoneSheriff and TeenShield. According to the FTC: "Retina-X did not make sure purchasers were using the apps for legitimate purposes. In fact, to install the apps, purchaser... Multiple-malware dropper 'Legion Loader' dissected (SC Media) The insidious nature of difficult-to-detect, multiple strains of malware working in tandem to unleash complete obliteration is on full display with the dropper Legion Loader. This 'grab-bag' hacking attack drops six different types of malware in one go (ZDNet) 'Hornet's Nest' campaign delivers a variety of malware that could create a nightmare for organisations that fall victim to attacks, warn researchers. FCA Probes Claims BoE News Conferences Were Hacked (Law360) The Financial Conduct Authority said Thursday it is investigating claims that high-speed traders eavesdropped on market-sensitive press conferences by Bank of England officials slightly ahead of their official video broadcast. Frankfurt shuts down IT network following Emotet infection (ZDNet) Frankfurt city officials take down IT network to prevent Emotet to be used as a staging point to launch a ransomware attack. Emotet Wishes You a Merry Christmas from Greta Thunberg (Proofpoint US) Recently, the Proofpoint Threat Insight team, among other researchers, observed a global malicious email campaign that leveraged a number of topical lures in a single message that attempts to deliver the well-known malware Emotet. Malicious New Windows Malware Attack: Fake Greta Thunberg Emails Used To Lure Victims (Forbes) Windows users are warned of a new email campaign that may put you at serious risk. Don't open that Christmas party email - it could be swarming with malware (TechRadar) Emotet botnet malware hidden within fake Christmas party invites Scammers are using Play Store apps to serve ads that nobody can escape (CyberScoop) A sneaky network of more than 100 Android applications is allowing fraudsters to make money by pushing pervasive advertisements to users' devices, according to new cybersecurity findings. China-Based Cyber Espionage Group Targeting Orgs in 10 Countries (Dark Reading) Dozens of organizations across multiple sectors have become victims of APT20 in the past two years. 170m passwords stolen in Zynga hack, monitor says (the Guardian) Words With Friends company admitted hack in September but size only now revealed Ambitious scam wants far more than just PayPal logins (WeLiveSecurity) ESET researchers spot fraudulent websites that impersonate PayPal and trick users into handing over far more than 'only' their logins to the payment service. Dark-web peddlers sell popular RAT for US$20 (SC Magazine) Researchers at Proofpoint have found a widely-used remote access trojan being sold for below US$20 on underground forums Cryptocurrency-mining botnet uses a Taylor Swift image to hide malware payloads (ZDNet) MyKingz (Smominru) botnet hides the malware it deploys on infected hosts inside a JPEG of Taylor Swift. MyKings botnet conceals code in Taylor Swift image (SC Magazine) A cryptomining botnet is using code hidden in a Taylor Swift photo to infect computers around the world. Phishers prey on fans of 'Star Wars: The Rise of Skywalker' film (TechRepublic) Some users have already been affected by 65 malicious files disguised as copies of the latest Star Wars film, according to Kaspersky. Here's how to avoid being a victim of such phishing attempts. Here Come the 'Star Wars' Scams: Don't Fall for Them (PCMAG) Cybercriminals are using 'Star Wars: The Rise of Skywalker' as bait by creating fake websites that claim to offer free access to the film. But in reality, the websites try to trick you into handing over your credit card information. Fake 'Star Wars: The Rise Of Skywalker' streams are stealing fans' credit card info (CNBC) If you Google "Star Wars: The Rise of Skywalker watch free," you may have compromised your credit card information, according to a press release from global cybersecurity firm Kaspersky. Wawa announces massive data breach, 'potentially all' locations affected, CEO says (6abc Philadelphia) The CEO of Wawa says they are investigating a data breach that has potentially affected all of their locations. More Ring account passwords found on the dark web (TechCrunch) More than 1,500 Ring account passwords exposed, but Ring denies a breach. Online database exposes info on 267 million Facebook IDs (SC Magazine) A database holding more than 267 million user IDs, phone numbers and names of Facebook users was left exposed on the internet without requiring any form of authentication to access Unsecure database exposes details of 26,000 Honda Motors customers (SC Magazine) Unsecure Elasticsearch cluster owned by the Honda Motor Company left 976 million records of about 26,000 customers open online Exploit Kit Starts Pushing Malware Via Fake Adult Sites (BleepingComputer) Spelevo exploit kit's operators have recently added a new infection vector as part of their attacks, attempting to social engineer potential targets into downloading and executing addition malware payloads from decoy adult sites. Get in line! 38,000 students and staff forced to queue for new passwords (Naked Security) It's not a bread line, and it's not a line to see Santa – it's an analog response to a nasty cyber attack. AVEVA Vijeo Citect and Citect SCADA (Update A) (CISA) 1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit --------- Begin Update A Part 1 of 5 --------- Vendor: AVEVA and Schneider Electric Equipment: AVEVA's Vijeo Citect and Citect SCADA; Schneider Electric's Power SCADA Operation --------- End Update A Part 1 of 5 --------- WECON PLC Editor (CISA) 1. EXECUTIVE SUMMARY CVSS v3 7.8 ATTENTION: Low skill level to exploit Vendor: WECON Equipment: PLC Editor Vulnerability: Stack-based Buffer Overflow 2. RISK EVALUATION Successful exploitation could allow an attacker to execute code under the privileges of the application. Moxa EDS Ethernet Switches (CISA) 1. EXECUTIVE SUMMARY CVSS v3 7.5 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Moxa Equipment: EDS-G508E, EDS-G512E, and EDS-G516E Series Ethernet Switches Vulnerability: Uncontrolled Resource Consumption 2. RISK EVALUATION Successful exploitation of this vulnerability could cause the target device to go out of service. Philips Veradius Unity, Pulsera, and Endura Dual WAN Routers (CISA) 1. EXECUTIVE SUMMARY CVSS v3 5.3 Vendor: Philips Equipment: Veradius Unity, Pulsera, and Endura Dual WAN Router Vulnerability: Inadequate Encryption Strength 2. RISK EVALUATION Successful exploitation of this vulnerability could compromise the management interface of the front end router impacting the availability of data transfer via wireless communication. Reliable Controls MACH-ProWebCom/Sys (CISA) 1. EXECUTIVE SUMMARY CVSS v3 8.2 ATTENTION: Exploitable remotely Vendor: Reliable Controls Equipment: MACH-ProWebCom/Sys Vulnerability: Cross-site Scripting 2. RISK EVALUATION Successful exploitation of this vulnerability could allow an attacker to execute commands on behalf of the affected user. Omron CX-Supervisor (Update A) (CISA) 1. EXECUTIVE SUMMARY CVSS v3 8.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Omron Equipment: CX-Supervisor Vulnerability: Use of Obsolete Function 2. UPDATE INFORMATION This updated advisory is a follow-up to the original advisory titled ICSA-19-318-04 Omron CX-Supervisor that was published November 14, 2019, on the ICS webpage on us-cert.gov. Equinox Control Expert (CISA) 1. EXECUTIVE SUMMARY CVSS v3 9.8 ATTENTION: Exploitable remotely/low skill level to exploit Vendor: Equinox Equipment: Control Expert Vulnerability: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') 2. RISK EVALUATION Successful exploitation of this vulnerability may allow remote code execution. LifeLabs cyberattack one of 'several wake-up calls' for e-health security and privacy (CBC) The data breach of the Canadian laboratory testing company LifeLabs is one of "several wake-up calls" for security and privacy challenges that come with the push for a medical system in which eHealth plays a significant role. Macy's breach is a game-changing Magecart attack (CSO Online) The attackers customized the Magecart code to the Macy's website to steal credit card information in the wallet and new registrations. New Orleans' Mission: Clean 4,000 Computers in 48 Hours (BankInfo Security) New Orleans is setting an aggressive pace to restore services after a ransomware attack crippled the city's IT systems: fixing more than 450 servers and 3,500 New Orleans Struggles To Fix Computer Systems After Cyber Attack (NPR) The city of New Orleans is struggling to fix computer systems after a widespread cyber attack. Police officers have needed to use personal computers and residents can't conduct routine city business. City Council to make adjustments to final meeting of 2019 following cyber attack (Fox 8 Live) Thursday is set to be the last New Orleans City Council meeting of the year but it may come with complications after a recent cyber attack. Henry County Pays US$650,000 to Get Back on Feet (CISO MAG) To restore parity from a malware attack and a corresponding data breach, Henry County ended-up paying more than US$650,000. Two attacks on Maze ransomware list confirmed (SearchSecurity) The Maze ransomware group claimed responsibility for an attack on Busch's Fresh Food Markets, making this the second disclosed ransomware attack on the group's list after the company refused to pay up. Ransomware: The number of victims paying up is on the rise, and that's bad news (ZDNet) Ransomware attacks have continued to rise - and more and more organisations are opting to pay cyber criminals in order to restore their networks. Report: Ransomware Goons Had A Great 2019, With At Least 948 Reported Attacks (Gizmodo Australia) Ransomware operators are closing out a year of extorting local governments, hospitals, and schools across the country with a bang, with at least four more U.S. cities falling victim to sophisticated scams this month alone and a recent report tallying the total number of incidents at nearly a thousand.... Is Security of Crypto Exchanges Far From Being Infallible? (Cointelegraph) Cryptocurrency exchanges have improved their security, though they're still prone to hacking attacks. How can exchange operators handle such threats? What's behind Putin's old-school operating system? (Naked Security) Reports surfaced this week that the president of Russia is still using Windows XP as his primary operating system. Security Patches, Mitigations, and Software UpdatesChrome 79 patched after Android WebView app chaos (Naked Security) Google has rushed out a fix for a bug in the Android version of Chrome that left some app users unable to access accounts or retrieve stored data. Drupal Warns Web Admins to Update CMS Sites to Patch a Critical Flaw (The Hacker News) Drupal releases security patches critical vulnerabilities that could let remote hackers compromise web servers. Facebook to stop using 2FA phone numbers for friend suggestions (Computing) The change is being introduced in five countries this week,Privacy ,Facebook,two-factor authentication,2FA,FTC,Michel Protti Cyber TrendsCyber Risk Index | Trend Micro (Trend Micro) We teamed up with the Ponemon Institute to investigate the level of cyber risk across organizations and create a Cyber Risk Index (CRI). Refreshed regularly, the CRI is a comprehensive measure of the gap between an organization's current security posture and its likelihood of being attacked. Our second survey shows an increase in the risk, particularly in terms of the attacks targeting organizations. Cybersecurity Predictions for 2020 (Netskope) Just like every year, we've seen the cybersecurity industry shift and change quite a bit in 2019. Finding new threats, building new infrastructure, and uncovering new risks both in and out of the cloud. WIth 2020 looming on the horizon, there's plenty to unpack and predict what's next for the security industry as we kickoff … Venafi Study: Critical Machine Identities Protected Less than Human Identities (Venafi) Venafi research reveals organizations aren't protecting machine identities as effectively as human identities – and they may be more important to cybercriminals. Read more. Spam over phone and email is changing consumer communication preferences (Help Net Security) Of today's main communications mediums - text, phone calls and email - consumers continue to get the most spam over phone and email. MarketplaceF5 Networks to acquire Shape Security for $1 billion (MarketWatch) F5 Networks Inc. said late Thursday it will acquire privately held cybersecurity company Shape Security in a deal with an enterprise value of $1 billion. In... Kenes Rakishev and Moshe Hogeg decided to merge Sirin Labs with cyber security company from Israel (Talk Finance) Sirin Labs will overwinter the lack of interest to blockchain technology by joining forces with the yet unnamed Israeli cybersecurity startup. The plan, which is already confirmed by Kenes Rakishev and Mosche Hogeg, is on the final stages of implementing. We think, that we know what kind of security startup is about to merge with Sirin Labs, but we prefer … Google Offers Financial Support to Open Source Projects for Cybersecurity (The Hacker News) As Part of its Patch Rewards Program, Google Offers Financial Support to Open Source Projects for Cybersecurity. eSentire announces partnership with CrowdStrike (IT World Canada) Managed detection and response firm eSentire has announced a partnership with Crowdstrike to complement one another's security solutions. The partnership, announced on OnePlus announces new bug bounty program to strengthen its cybersecurity (Android Central) Aiming to strengthen the security of its systems, OnePlus has announced a new bug bounty program for security researchers around the world. It is also teaming up with HackerOne to defend its systems against threats. Alexander Botting Joins Venable's Cybersecurity Team as Senior Director of International Cybersecurity Services (Citybizlist) Venable LLP is pleased to announce that Alexander Botting has joined the firm as senior director of international Products, Services, and SolutionsMedigate and Cerner to Advance Medical Device Security (BusinessWire) Medigate, a dedicated medical device security and asset management solution, today announced it's joining forces with Cerner Corporation (Nasdaq: CERN ImageWare Systems Partners with Laxton to Provide Law Enforcement Agencies with Modern in-the-field Biometric Devices (Financial Buzz) ImageWare® Systems, Inc. (OTCQB: IWSY), a leader in mobile and cloud-based identity proofing and biometric authentication solutions, announced today a partnership with Laxton Group, a global provider of election, identity, and self-service solutions, to supply Law Enforcement agencies worldwide with a complete in-the-field biometric identity solution. Image Protect Expands Fotofy Platform Compatibility to Include Rapidly Growing Global Push Notification Marketplace (West) Image Protect Inc. (OTC: IMTL) (imageprotect.com) ("Image Protect", "IMTL", or the "Company"), a global leader in the end-to-end copyright infringement sector, is excited to announce imminent steps and a pending partnership discussion that will expand the Fotofy Platform into the massive and rapidly growing Push Notification space. TrueFort Expands Fortified Ecosystem with Infoblox and Others (BusinessWire) As vendors we need to ensure smooth integration and information sharing between toolsets, through initiatives like the TrueFort Fortified Ecosystem. Praxis Elevates Focus on Data Privacy and Protection with Asia Pacific Economic Cooperation Cross Border Privacy Rules system (APEC CBPRs) Certification | BioSpace (BioSpace) Praxis Elevates Focus on Data Privacy and Protection with Asia Pacific Economic Cooperation Cross Border Privacy Rules system (APEC CBPRs) Certification - read this article along with other careers information, tips and advice on BioSpace New Asigra Program Defends Public/Non-Profit Organizations Against Cyber Attacks Targeting Backup Data (Asigra) Asigra Inc., a leading cloud backup, recovery and restore software provider since 1986, today announced a new program focused on defending the backup repositories and data of Canadian public and non-profit organizations against cyber-attacks. Elcomsoft Extracts Skype Histories From Microsoft Account (PR Newswire) ElcomSoft updates Elcomsoft Phone Breaker, the company's forensic extraction tool. Version 9.40 can remotely extract Skype conversation... Sophos Launches Managed Threat Response Service (CIOL) Sophos announced the availability of Sophos Managed Threat Response (MTR), a fully managed threat hunting, detection and response service. The re-sellable service provides organizations with a dedicated 24/7 security team Arctic Wolf Enhances Managed Detection and Response Service With Managed Containment (BusinessWire) Arctic Wolf Networks, a leading security operations center (SOC)-as-a-service company, today announced the addition of Managed Containment to the Arct What's that? Encryption's OK now? UK politicos Brexit from Whatsapp to Signal (Register) Take a break from calling for the end of e2e, so they can switch encrypted chat apps Technologies, Techniques, and StandardsShip engine and auxiliary networks will be cyber secure (Riviera Maritime Media) Lloyds Register has awarded one of the first system-level cyber certification in the world to a major OEM FIRST released ethics guidelines to deepen trust among incident response teams (FIRST — Forum of Incident Response and Security Teams) Calling for public consultation until end of January, 2020 Proposed standard would make warrant canaries machine-readable (Naked Security) For years, organisations have been using a common tactic called the warrant canary to warn people that the government has secretly demanded access to their private information. Now, a proposed stan… 7 signs your cybersecurity is doomed to fail in 2020 (Help Net Security) Cybercrime represents big money. Unfortunately, that will equate to operational and financial losses for unprepared businesses in 2020 and beyond. Are you talking business risk intelligence to the C-Suite? - (Enterprise Times) Ian Schenkel talks about Business Risk Intelligence and why business management teams need to adopt personal brand protection How to manage a departing employee's access to IT (Cloud Pro) We talk to experts in access rights, data removal and human resources to navigate this most tricky of passages How to Handle Brand Impersonation on Social Media (PhishLabs Blog) In a world where it only takes moments to create a profile on social media, there is a difference between parody and malicious attacks. Challenges of using firewall tech to do segmentation (Help Net Security) Security segmentation limits the ability for attacks to move laterally by breaking data center and campus networks or clouds into smaller segments. How to get rid of My Login Hub Browser Hijacker - virus removal guide (updated) (PC Risk) My Login Hub is an application that supposed to provide a quick access to various email accounts, users supposed to be able to access them directly from a newly opened tab. However, My Login Hub turns out to be a browser hijacker, a potentially unwanted application (PUA). Design and InnovationAn aerospace company is using blockchain tech to combat counterfeit products in aviation industry (TheNews.Asia) An aerospace company is using blockchain tech to combat counterfeit products in aviation industry Honeywell, an aircraft part producer, is partnering with iTRACE and SecureMarking to reduce the pro… Facebook is building an operating system so it can ditch Android (TechCrunch) Facebook doesn't want its hardware like Oculus or its augmented reality glasses to be at the mercy of Google because they rely on its Android operating system. That's why Facebook has tasked Mark Lucovsky, a co-author of Microsoft's Windows NT, with building the social network an … Facebook will bar posts, ads that spread disinformation about the U.S. census (Washington Post) Facebook will remove posts, photos and other content that mislead people about the U.S. census starting next year, seeking to prevent malicious actors from interfering in a critical, once-in-a-decade process that determines political representation. Instagram hides 'false' content, unless it's from a politician (Naked Security) Instagram's expanding its fact-checking program but, like Facebook, says it won't keep political speech away from "public debate and scrutiny." On Census, Facebook And Instagram To Ban Disinformation And False Ads (NPR) Under pressure to prepare for 2020 census interference, Facebook says content misrepresenting who can participate and the data the government collects will be banned from its social media platforms. Why video games and board games aren't a good measure of AI intelligence (The Verge) Reimagining what intelligence means for AI. Legislation, Policy, and RegulationU.S. Concerned Russia-Backed UN Resolution Will Hurt Online Freedom (RadioFreeEurope/RadioLiberty) The United States said a cybercrime resolution sponsored by Russia is an attempt to push state cyber controls and fears it will pass the United Nations General Assembly later this month. Chinese government cuts US Democratic debate live feed (CNN) The live feed of the sixth Democratic presidential debate was cut without warning in China Thursday night during a discussion on allegations of human rights abuses in the country's western region of Xinjiang. Greenland chooses Ericsson over Huawei for 5G rollout (Reuters) Greenland has picked Sweden's Ericsson over China's Huawei to supply e... Italy security committee urges tougher government stance on Huawei, ZTE (Reuters) Italy should consider preventing Chinese telecoms firms Huawei and ZTE from taki... Federal Council considers introduction of cyber incident reporting duty | Lexology (Lexology) While many countries have introduced far-reaching obligations to report cyber incidents, Switzerland has not yet followed this lead. However, the… Homeland Security cyber 'hunt' teams are coming to help (Fifth Domain) A massive spending package included a provision that directs the Department of Homeland Security to maintain its cyber hunt and incident response teams. Facebook's location tracking policy still worries US Senators (Naked Security) Does Facebook continue to track the locations of its users even when they've told it not to? Yes! The Pentagon has declared war on...*checks notes*... Tik Tok (Task & Purpose) The Dec. 16 cyber awareness message advises DoD employees that uninstalling Tik Tok, "Will not prevent already potentially compromised information from propagating, but it could keep additional information from being collected." Trump Announces Picks to Replace Outgoing Leaders at NSF, CISA (Nextgov.com) The administration plans to nominate a replacement for the National Science Foundation director and appoint a new assistant director for the Cybersecurity and Infrastructure Security Agency. Federal deputy CIO Graves to move on to private sector (Federal News Network) Margie Graves, who has been the federal deputy CIO since 2016, plans to return to the private sector in 2020 after spending 18 years in federal services. Litigation, Investigation, and Law EnforcementJustice Department investigates Sci-Hub founder on suspicion of working for Russian intelligence (Washington Post) The investigation into Alexandra Elbakyan has criminal and intelligence-gathering elements, according to people familiar with the matter. Email blackmail brouhaha tears UKIP apart as High Court refuses computer seizure attempt (Register) And you thought politics was winding down for Christmas Jet2 hacker, a former contractor with axe to grind, jailed for 10 months (ZDNet) He lurked in the CEO's inbox to check if the airline knew of his involvement. Disgruntled IT Worker Jailed For Airline Cyberattack (Law360) An aggrieved former information technology worker at Jet2 has been jailed for 10 months for a cyberattack on the low-cost British airline that cost it £165,000 ($215,000), the National Crime Agency said Thursday. US court jails scammer who fleeced Facebook and Google out of $120m in email fraud (Computing) Rimasauskas shook down Google and Facebook with fake emails purporting to be from a major Taiwan-based supplier Google fined €150m by French authorities over anti-competitive abuse of search ads (Computing) Google hit with third-highest antitrust fine by French authorities The Hacker Who Took Down a Country (Bloomberg) Daniel Kaye, also known as Spdrman, found regular jobs tough but corporate espionage easy. He's about to get out of prison. | ||||||||||||||||||||||||||||||||||||||||||
| 10 Nastiest Malware Of 2019 That Shook Cybersecurity World - Fossbytes Posted: 20 Dec 2019 05:06 AM PST 2019 was a big year for cybersecurity as several threat groups unleashed malware that led to a loss of a large sum of money to organizations, governments, and compromised data of millions of users all over the world. These malware strains are more than enough to state that we need to take cybersecurity more seriously in the coming years. In 2019, small and medium businesses were more prone to risk as they lack proper cybersecurity measures to evade attacks. Here is a list of the nastiest malware that are the highlights of the cybersecurity world in 2019: Top 10 Malware Of 20191. Emotet – Malware disguising itself as Snowden's book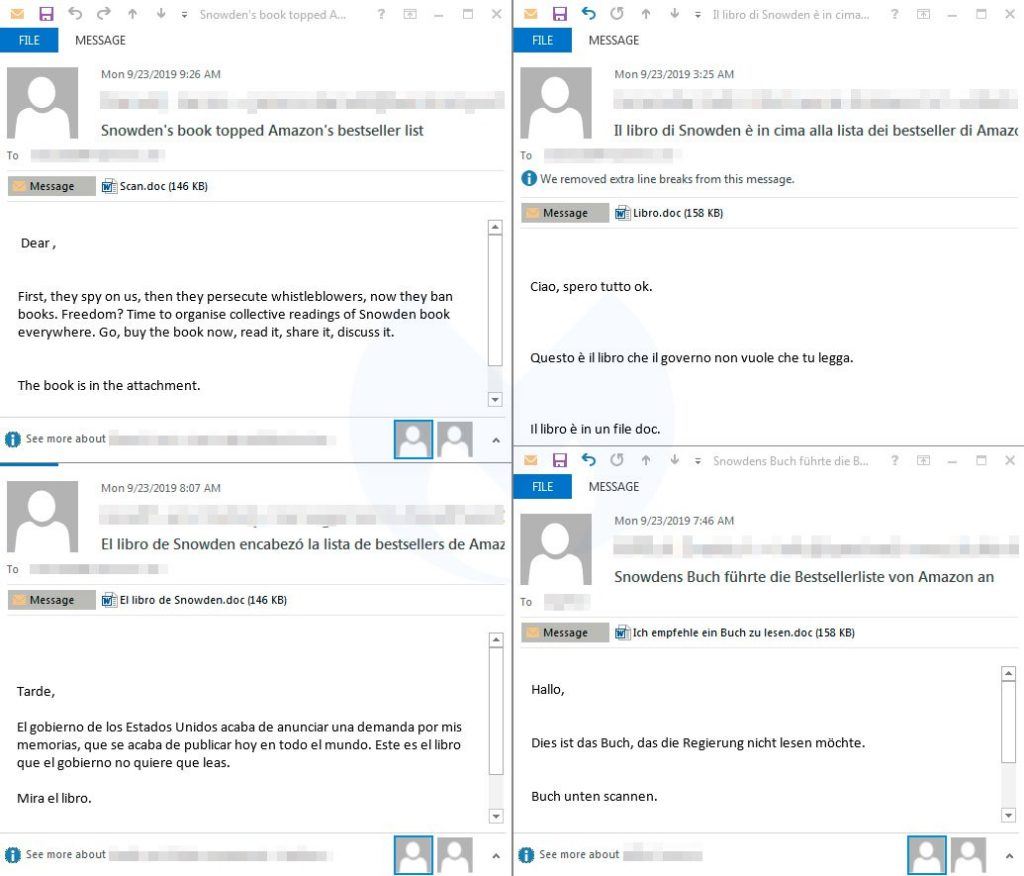 Emotet is a deadly botnet malware that made a come back in 2019 and interestingly, it disguised itself as Edward Snowden's recently released book "Permanent Record." Once installed, the malware hijacks email credentials and could even send malicious emails to people in your contact list. Emotet is a deadly botnet malware that made a come back in 2019 and interestingly, it disguised itself as Edward Snowden's recently released book "Permanent Record." Once installed, the malware hijacks email credentials and could even send malicious emails to people in your contact list. 2. Trickbot – Trojan that can disable Windows Defender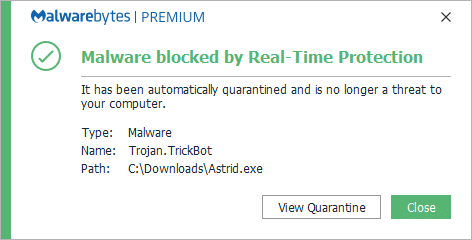 Trickbot isn't exactly a malware that surfaced in 2019 but gained a feature this year that made it a notorious threat amongst Windows users. The trojan deploys 17 steps to disable Windows Defender's real-time protection. Trickbot trojan affected nearly 250 million Gmail accounts last time it gained cookie stealing abilities. 3. Ryuk Ransomware – Costliest malware ever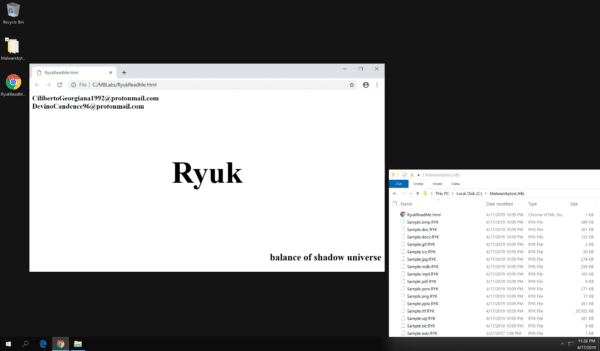 Ryuk malware appeared throughout the year and affected millions of people all over the world. The malware targeted several state, local and territorial government entities, and demanded ransom in Bitcoin to decrypt files. Recently, Ryuk malware affected the servers and computers of the City of New Orleans. It usually demands 15-50 Bitcoins translating to $100,000-$500,000. Malwarebytes labeled Ryuk ransomware one of the costliest amongst other malware. 4. Sodinokibi – Successor of GandCrab Sodinokibi emerged soon after the retirement of the notorious GandCrab, and security researchers found several similarities between the two. In May 2019, Sodinokibi exploited Oracle Zero-Day flaw, encrypted the files on the target system and demand $2,500 in ransom. If the victim misses the deadline, the ransom doubles to $5,000. Sodinokibi emerged soon after the retirement of the notorious GandCrab, and security researchers found several similarities between the two. In May 2019, Sodinokibi exploited Oracle Zero-Day flaw, encrypted the files on the target system and demand $2,500 in ransom. If the victim misses the deadline, the ransom doubles to $5,000. 5. Dharma – Ransomware that affected a hospital in Texas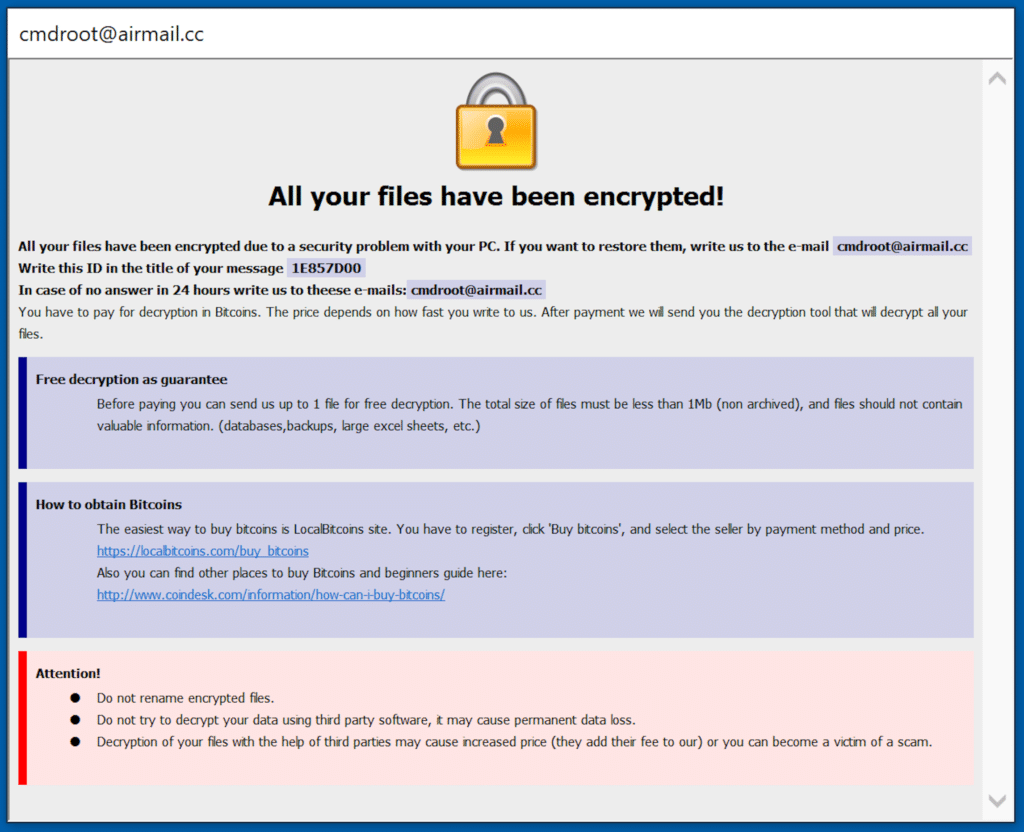 Dharma ransomware was one of the most popular ransomware of 2019. In the last quarter of 2019, Dharma ransomware targeted several businesses and organizations. Most notably, Dharma ransomware encrypted hospital records of a Texas-based hospital having critical patient records. 6. Invisible Malware – A nightmare for your anti-virus As evident from its name, Invisible Malware turns itself invisible, making it impossible for anti-virus software to catch it. It resides only in memory, therefore, cannot be traced by endpoint protection software. Invisible Malware, a type of "fileless malware" can only be removed by forcibly shutting down your computer. 7. HiddenWasp – Malware that could control Linux machines remotely 2019 saw a rise in the number of malware affecting Linux machines and HiddenWasp turned out to be one of the biggest of the lot. The malware, when discovered, had a zero detection rate in all commonly known malware protection systems. HiddenWasp malware could run commands on the terminal, execute files, download more scripts, etc. on the affected Linux computer remotely. 2019 saw a rise in the number of malware affecting Linux machines and HiddenWasp turned out to be one of the biggest of the lot. The malware, when discovered, had a zero detection rate in all commonly known malware protection systems. HiddenWasp malware could run commands on the terminal, execute files, download more scripts, etc. on the affected Linux computer remotely. 8. Retadup Crypto Malware – Malware affected 850K Windows PCs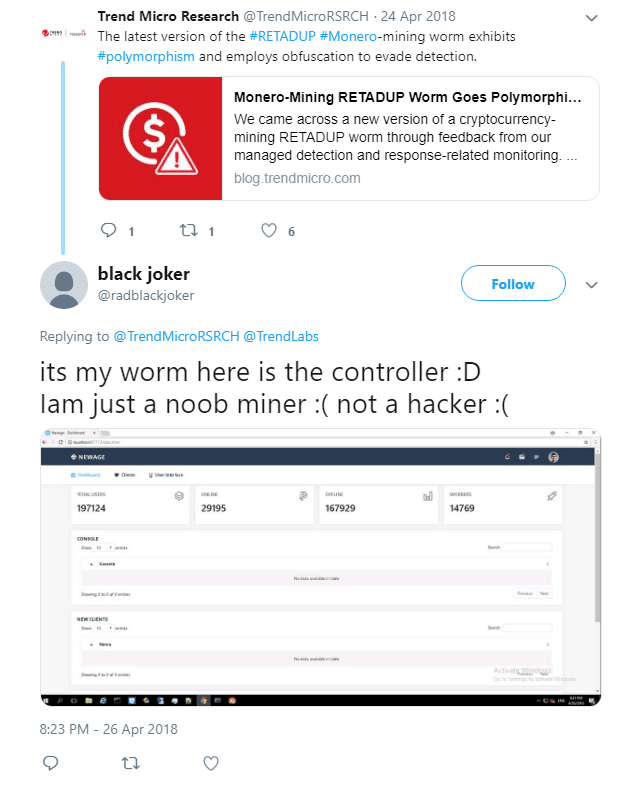 Retadup is a cryptocurrency mining malware that wreaked havoc in 2019. It infected 850,000 Windows PCs before French police neutralized the botnet by exploiting a design flaw in the malware's command and control server. According to French police, Retadup crypto-malware is "one of the largest networks" of hijacked computers ever witnessed. 9. xHelper – Android malware that can't be removed even after factory reset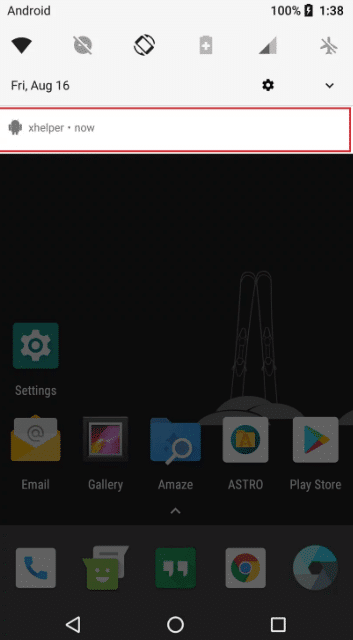 In October, xHelper malware affected 45,000 Android devices and also appeared in the Malwarebytes' top 10 list of malware in August. The malware showed an exemplary technique to evade detection from antivirus software. The malware uses encryption in its full-strength mode and researchers found that it cannot be removed even after the infected device has been factory reset. 10. Pegasus – WhatsApp spyware that targeted Indian journalists, activists Pegasus, an Israeli spyware, was the focus of Indian cybersecurity experts in October-end this year. The malware allowed the Indian government to spy on 1,400 journalists and activists. Pegasus infected devices by disguising itself as an exploit link and accessed personal information like target's passwords, text messages, contact lists, and calendar events. Pegasus, an Israeli spyware, was the focus of Indian cybersecurity experts in October-end this year. The malware allowed the Indian government to spy on 1,400 journalists and activists. Pegasus infected devices by disguising itself as an exploit link and accessed personal information like target's passwords, text messages, contact lists, and calendar events.
| ||||||||||||||||||||||||||||||||||||||||||
| Surfshark's holiday VPN deal gifts you one free month with 2-year plan - iMore Posted: 18 Dec 2019 08:27 AM PST The holiday season brings loads of great deals on the hottest tech devices of 2019, but you shouldn't forget about discounts on valuable tools that will serve you for years to come. I'm talking about Surfshark VPN, which will provide privacy and anonymity while you traverse the online world. Instead of paying the full price for a 2-year subscription, you can instead get it for just $47.76 and have an additional month thrown in for free. All told, that's an 83% discount, and it brings the monthly price down to $1.91. You'd pay almost $300 on the month-to-month plan for that length of time. 🏄♂️🦈 Surfshark VPNBrowse anonymously, securely, and with no geographic barriers. It works great on mobile, macOS, and Windows, and you can use it on an unlimited number of devices at once. Get this limited-time deal and protect yourself for over 2 years. $47.76 | ||||||||||||||||||||||||||||||||||||||||||
| NordLocker Review – A Reliable, Comprehensive & Easy-To-Use File Encryption Solution! - TechNadu Posted: 25 Nov 2019 12:00 AM PST  During the last year, we've been hearing plenty about exposed private data and hackers stealing sensitive files. It's also a known fact that major IT companies track their users, which means that the privacy of your files (at least those stored on your computer or cloud storage) should be a major concern. What you can already do is be proactive about this – and this is where encryption solutions come into play. As you're about to see, we will be checking such a solution in this article, which has been initially announced close to six months ago. So, welcome to our NordLocker review. In case the name of this encryption software sounds familiar, you're not wrong. NordLocker comes from the same guys who created NordVPN, one of the most popular VPN services right now. They've been expanding their portfolio recently, by introducing NordPass as well – which is a password manager. As you can see, we now have three separate services from this company, all of which are aimed at improving your online security and privacy. First, we will provide some basic information about NordLocker, found in the table below. So, let's introduce you to this file encryption service by listing some of its main features, supported platforms, and its current pricing structure.
As you can expect, we've spent some hands-on time with this software, and we did our best to be thorough. So, in case you don't have the time to read this entire NordLocker review, we've prepared the most prominent highlights, found below.
So, we're now ready to dive deep into everything NordLocker offers. In case you'd like to learn all its ins and outs, make sure to keep on reading. NordLocker – TechNadu's Hands-On ReviewNordLocker is a brand-new file encryption service, and we're happy to have been reviewing it so soon after its launch. With this said, please note that we've been reviewing version 1.0.47.0 of NordLocker on a Windows 10 PC. However, everything said about this article applies to its macOS counterpart as well. Platform Compatibility You can use NordLocker on Windows and macOS computers, and the application comes cross-compatible. There are no Android or iOS apps at the moment, but we believe this could change soon enough. Our Score: 7.5/10. At the moment, you will find NordLocker applications for Windows and macOS. And also, both of these are easily accessible from this application's website. This means that at the moment, users of desktop platforms are the only ones who can take advantage of NordLocker. This isn't a major downside, as there's plenty of use for this application on desktop platforms. The good news here is that NordLocker is cross-platform compatible. This means that encrypted files can be sent between Windows and macOS users. However, the bad news is that Android and iOS users are left out at the moment. We are sure that NordLocker is looking for a way to reach these platforms as well, and we can only hope this to happen soon enough. In case you're worried about whether your computer will run this application, let's clear up your doubts. NordLocker might sound like a technically complex application, but it's actually a simple one. You don't need a powerful computer, and even some pretty old models should work just fine. Installation Process NordLocker has done a marvelous job of offering a simple installation process. Download and install the app on your computer, and then log-in and create your master password. That's about it. Our Score: 10/10. You will be happy to know that NordLocker comes with a really easy installation. No matter if you decide to try it for free, or if you'd like to get a NordLocker subscription straight away, you start by downloading the application from its website. We've tested this application on a Windows 10 PC, where we ended up with a 10MB installation file. So, it's pretty lightweight and should download fast even on slow Web connections. Also, as the installation wizard will tell you, there's an important requirement here. You need to have the '.Net Framework 4.8' on your computer, which can be easily downloaded during the installation process. Choose where to save the files and complete the installation – it will all take less than one minute of your time.  Before you jump into NordLocker's interface, you'll need to log-in to your account. In addition, you'll need to provide your master password, used to authenticate your access each time you want to open your encrypted files. Important Note: NordLocker will provide a recovery key, which is best kept offline. This key is only available to you, and you can use it to recover your master password. In case you lose both your recovery key and your master password, it will be impossible to decrypt your data. So, make sure to pay attention to where your recovery key is stored. User Interface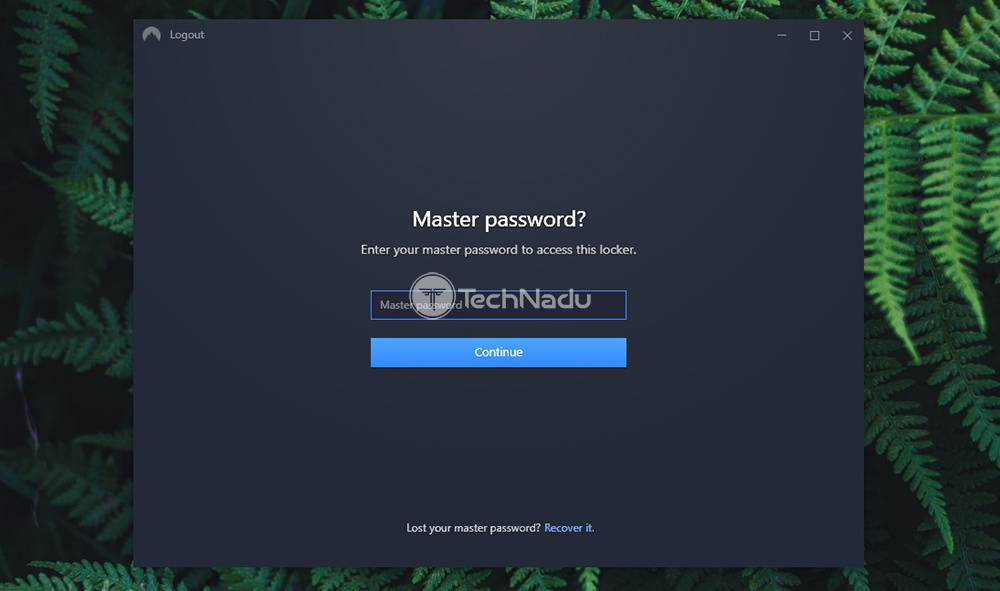 If you need a very simple encryption solution, NordLocker can be the right pick. It comes with a simple UI that's suitable even for complete beginners. Aside from occasional (minor) glitches, everything seems to be working just fine. Our Score: 9/10. As you can see from the screenshots found in this article, NordLocker comes with a simple interface. At the very top, you will see a navigation bar, along with a button used to add individual files and folders. Then, on the far-right side, you can check the application's settings and log out. There isn't much to play around here, as there are only two settings to tweak. You can decide to launch the application on system startup, and you can opt-in/out of anonymous data collection. Then, the central portion of the screen shows your files and folders. Everything you add to your locker is visible here – and you're the only one who can open those files. If you double-click on any of those, the files will open, like they normally would. However, they're being encrypted and decrypted in the background, which happens automatically. As you can see, very little input is needed. All you have to do is to add and remove files and folders from your locker. 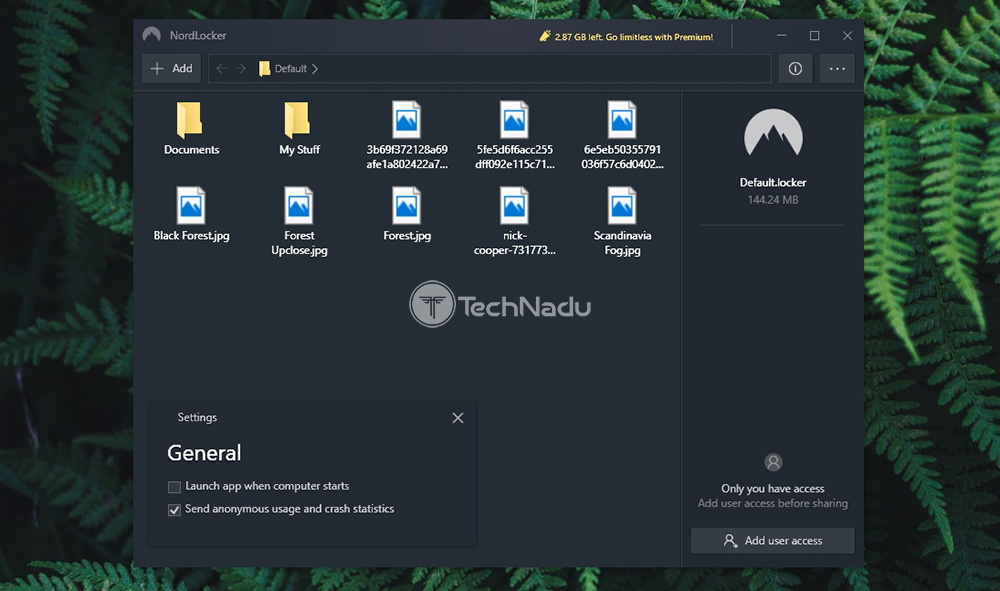 On the right-hand side, you will see four additional options (and these can be triggered by clicking on individual files). You get to prepare the file for sharing, export a decrypted copy, as well as rename or delete the file. We'll talk about sharing in the following segment, so make sure to stick with us. All in all, NordLocker seems like a very simple application – suitable even for complete beginners. However, we wished to see additional options to fine-tune its interface and behavior. And also, there seems to be a strange glitch (or stuttering) when resizing the window of NordLocker. Of course, this is nothing major, but it does point out that the application could be optimized even more. Ease of Use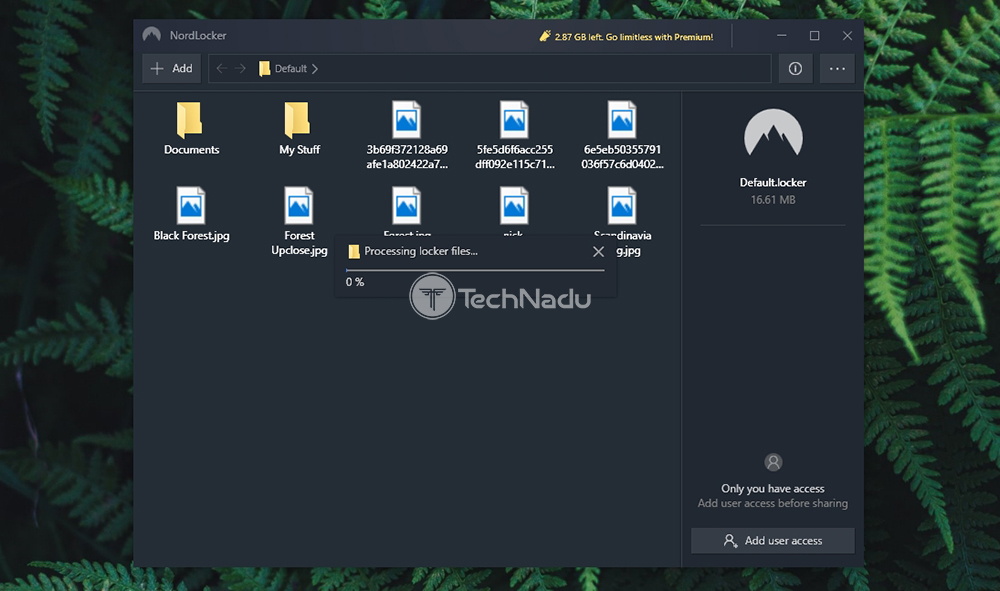 NordLocker isn't made for IT experts – it's made for average PC/Mac users. Therefore, it's intuitive enough and comes without any distractions or complications. Our Score: 10/10. Each time you open NordLocker, you'll be asked for your master password. Once you provide it, you'll get to see the application's UI, along with all your encrypted files. To add files, you simply drag-and-drop them onto this interface. Alternatively, you can use the 'Add' button to add folders of individual files. Upon doing so, NordLocker will copy the files to its locker (which is located on your computer) and encrypt them. If you locate and open this folder (without opening NordLocker first), the main application will initialize asking for your master password. 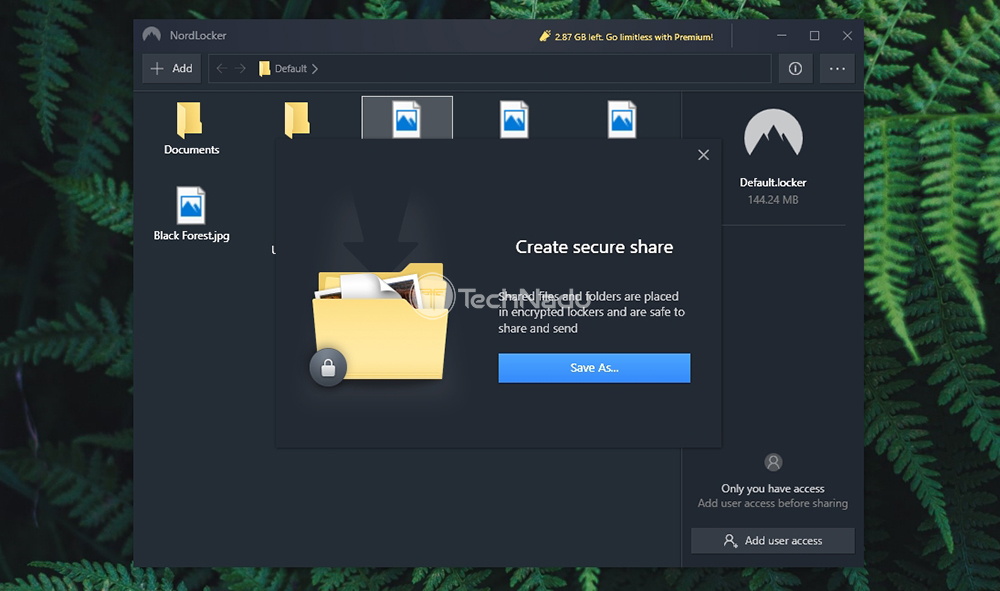 While working in NordLocker, you are free to open and delete files, rename them, and share them. Encrypted files can be shared via email, shared Dropbox folder, or even on a USB stick. However, for someone else to open them, they need a valid NordLocker key (which means that they need to be a user of this service, either free or premium one). You can easily share files by entering the recipient's email address, and NordLocker will finish the procedure on its own. Privacy & Security Tefincom, the company behind NordLocker, has had some problematic situations in the past (related to NordVPN mostly). However, we're more than sure that NordLocker comes without any vulnerabilities, as it seems that its privacy-related aspect has been well-thought-out. Our Score: 9/10. Since we're dealing with an application designed to work with your sensitive data, it's important to know how your data is handled. In other words, we'll check three equally important aspects to NordLocker's privacy, so here's what you need to know. Jurisdiction & Applicable LawsAs already explained in our NordVPN review, the company behind Nord-branded products comes from the Republic of Panama. This is good news as Panama is outside the 14-Eyes Alliance, which means that intelligence agencies will need to jump through several hoops to get to your data. Also, it's worth mentioning that this group of countries has been lobbying for the creation of encryption backdoors. This is why it's good to know that NordLocker is outside of those jurisdictions. It is also worth noting that NordVPN is a recipient of numerous awards and that it was put through independent audits. However, let's also not forget to mention that it was found to contain serious bugs and it was even hacked not too long ago. Of course, everything said in this paragraph doesn't apply to NordLocker – it applies to NordVPN. However, it shows that you shouldn't be too comfortable with cyber-sec solutions and that you should take extra steps to make sure that your data is safe. Privacy PolicyWhen it comes to NordLocker's privacy policy, the company behind this product has done a good job of making sure that you're left alone. The application uses client-side encryption, which means that NordLocker's developers have no access to your data. Still, some data is collected, nonetheless. NordLocker's privacy policy says that three types of data can be collected. We're talking about application diagnostics, anonymized app usage statistics, and device information. Luckily, this is fairly standard practice for any type of software, and this doesn't raise any red flags. In addition, you can opt-out of this data logging, at least via its Windows client. Encryption & Technical SecurityFirst of all, you should know that NordLocker uses client-side encryption. If you share your files with someone, then we're talking about end-to-end encryption. This means that files are being encrypted on your computer, and this process doesn't have anything to do with any servers. If you send an encrypted file to someone, the recipient needs to have NordLocker installed to decrypt them. This is a good thing because it eliminates any role of this application's developers. In terms of its technical security, NordLocker uses AES-256-GCM to encrypt your data, using the encrypted keys hashed via Argon2. Also, locker keys never leave your device and they are never stored on any servers. This means that you're free to store your encrypted files elsewhere, even on cloud storage solutions like Dropbox, Google Drive, or OneDrive. That's because all your files are being encrypted using your secret key, derived from your master password. Customer Support Unfortunately, NordLocker comes without a live-chat option on its website (which could soon change). However, there are plenty of other helpful resources. Our Score: 8/10. Other Nord-branded products are known for their customer support. However, when it comes to NordLocker, the situation is somewhat different. That's because live-chat isn't available for this product, even though we're sure that this option will arrive soon enough. This means that you can rely on two types of customer support resources. You can open a customer support ticket and explain your problem. It shouldn't take too long to receive a response, as this team is known for being prompt. Then, you can check various types of guides and frequently asked questions. There are related to the general use of NordLocker, billing, and troubleshooting. These resources should be sufficient to answer your questions. PricingNordLocker isn't the most affordable option around. However, you'll find some very attractive savings if you pick one of its long-term plans. Our Score: 8/10. NordLocker comes with a subscription model, ranging from 1 month up to 3 years. So, let's take a look at how much you'll need to pay for this encryption tool, as well as how much you can potentially save.
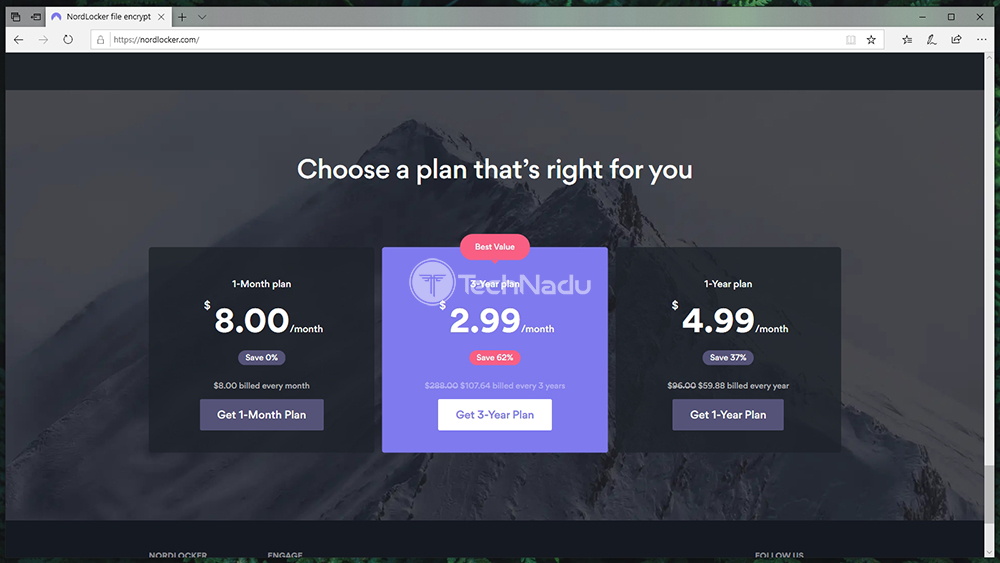
As you can see, the monthly price of NordLocker is $8.00 – which doesn't seem like the most affordable solution. However, the chances are that you don't need to encrypt your files for only a month – and you're probably looking for a long-term solution. With this said, we think you should subscribe to NordLocker by going for its long-term plans. You save up to 62% on the service's 3-year plan, whose price comes down to $2.99 per month. Among other important information, you should know that you'll get a 30-days money-back guarantee. Also, you can pay via debit and credit cards, cryptocurrencies, and Amazon Pay. Do We Recommend NordLocker?In some ways, NordLocker shows its young age. As you start to use it, you'll see that there's plenty of room for additional features that will most definitely come in the future. However, despite its young age, we think that it's usable and capable enough to safeguard your private data.
In case you'd like to learn more about NordLocker, make sure to use the provided link. It will take you to its official website, where you can see if this encryption tool aligns with your needs. We believe that many of you will be perfectly happy using NordLocker, but the final choice is yours to make. In case you've made it this far, why not share this article online? And also, you can follow TechNadu via our Facebook and Twitter pages. Thank you! | ||||||||||||||||||||||||||||||||||||||||||
| You are subscribed to email updates from "encrypted phone number,android crypto,encryption in computer network" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |


Comments
Post a Comment