Zoom acquires security startup Keybase to offer end-to-end encryption - Yahoo Lifestyle
Zoom acquires security startup Keybase to offer end-to-end encryption - Yahoo Lifestyle |
- Zoom acquires security startup Keybase to offer end-to-end encryption - Yahoo Lifestyle
- The Definitive Cyber Security Statistics Guide for 2020 - Security Boulevard
- Putin Is Well on His Way to Stealing the Next Election - The Atlantic
| Zoom acquires security startup Keybase to offer end-to-end encryption - Yahoo Lifestyle Posted: 07 May 2020 07:50 AM PDT  In its latest effort to beef up security, Zoom has acquired Keybase, a popular startup that provides encrypted communication services -- like secure messaging and file sharing. The deal is part of Zoom's 90-day plan to address security issues brought to light by the recent surge in demand. In a blog post, Zoom said it plans to offer an end-to-end encrypted meeting mode to all paid accounts in the near future. When Keybase is implemented, CNBC explains, paid Zoom users who schedule meetings will be able to choose end-to-end encryption. The setting will prevent anyone from calling in by phone, and it will disable cloud-based meeting recordings. With so many people working and learning from home due to the coronavirus crisis, Zoom has seen a huge uptick in use. But that exposed critical underlying security flaws. Zoom has issued fixes, vowed to win back users' trust, formed a security council and made other changes. But we've seen school districts ban Zoom over these issues, and plenty of competitors are looking to take advantage of Zoom's missteps. Keybase, which has a team of just 25, is Zoom's first acquisition in its nine-year history, CNBC reports. Fittingly, the deal was worked out over Zoom, and Keybase co-founder Max Krohn said not having to travel allowed the deal to close about 25 percent faster. Time will tell if other businesses trust Zoom enough to hash out their deals over the platform. |
| The Definitive Cyber Security Statistics Guide for 2020 - Security Boulevard Posted: 15 May 2020 08:29 AM PDT Cyber attacks continue to grow in both numbers and ferocity — 2019 was just a sign of the things to come. Here's your list of 122 of the most current cybersecurity industry, cyber attack, and data breach statistics for 2020 and beyondLast year, we published our first comprehensive list of cyber security statistics for our readers on Hashed Out. The article was such a hit that we wanted to make this an annual project that we publish with updated cybersecurity stats each year. This way, you know right away where you can turn for all of your cyber security data needs. This year, we wanted to up the ante and increased the number of cybersecurity statistics we report from 80 to 122. Since we're using the most current information available — most of the data comes from 2019 and 2020 reports, studies, and news reports — it's been a pretty massive undertaking. But we're excited to share with you as much current and useful information as possible from many of the world's leading sources and industry leaders. So, what numbers and sources made our list of the 122 top cyber security statistics for 2020 (and the years to come)? Let's hash it out. Cyber Security Statistics: Our Choice of the Top 122 Statistics for the Year 2020 (So Far)Before we get started, there's one quick thing I'd like to mention. Something that's always important to consider when you're looking at any list of cybersecurity statistics is that:
Various organizations use different qualifiers and methodologies in their reporting in terms of what may qualify as a cyber incident or data breach. Furthermore, the research is typically based on their own internal systems data, customers monitoring data, or information reported by victims of cybercrimes or survey responses from people within specific industries. And considering it can take weeks, months, or even years for some breaches or cyber attacks to be discovered — if they're discovered at all — it means that the actual numbers may actually be higher (or lower) than what's reported. These are just some of the reasons why you'll often see different information from one company to the next. With these things in mind, here are your top cyber security statistics for 2020: Cyber Security Statistics: An Overall Industry Perspective and the Economic Outlook1. Business Email Compromise / Email Account Compromise Scam Costs Top $26 Billion  Holy crap. That's a horrifying number! But before we rush on to the next statistic, let's look at this disturbing cyber security stat a little more closely to get some context. While it's true that the Federal Bureau of Investigation (FBI) Internet Crime Complaint Center's (IC3) did report that $26.2 billion dollars was the reported domestic and international losses reported between June 2016 and July 2019, we need to stop a moment and take a breath. Don't get me wrong — that number is still more disturbing than the scenarios told in children's nursery rhymes. But it's important to note that this isn't an annual cost of $26 billion, but rather an accumulated cost that's calculated over a three-year period based on data from the IC3 and international law enforcement. We just want to make sure that you have that bit of context. So, what was the one-year calculation of adjusted losses due to BEC/EAC complaints? More than $1.7 billion due to 23,775 complaints, the IC3 states in its 2019 Internet Crime Report. 2. More Than $3.5 Billion Was Lost to Cyber Crime Globally in 2019 Alright, let's take a one-year look at global cybercrime costs. Research from the same FBI IC3 2019 Internet Crime Report indicates that more than $3.5 billion was reported lost as the result of cyber crimes in 2019 alone. In that period, the IC3 report states that a total of 467,351 incidents were reported by businesses and individuals — of which, the most common types of crime with the highest reported losses include:
It's important to note that these cyber security statistics only include the number of reported attacks and losses. This means that these cyber security stats don't include the attacks and losses that resulted in unreported attacks. And considering that confidence/romance fraud scams often go unreported by victims, this means that the numbers are thought to be grossly underreported. 3. Apple, Netflix, and Yahoo Account for 25% of Brand Impersonations in Phishing Attacks in Q1 2020 Apple is one of the reigning consumer brands because of the popularity of its iPhones, Apple Watches, flashy marketing, and other useful consumer technologies. But Apple is also the brand that was most frequently impersonated overall by cybercriminals during the first quarter of this year, according to research from Check Point. It jumped from its previous seventh place rank in Q4 2019 to first place with 10% of all brand phishing attempts. Netflix is a close second, claiming 9% of all phishing attempts, and Yahoo comes in third with another 6%. 4. 57% of Survey Respondents Used Third-Party Cyber Security Assessments in 2019 Cyber security assessments are a critical component of making your cyber defenses stronger and more effective. More than half of the 1,100 respondents to Experian's Seventh Annual Data Breach Preparedness Study indicate that they regularly conducted "third-party cyber security assessments" in 2019. While this may seem low, just keep in mind that this number has increased by about 9% over the past two years, according to their data. 5. 73% of Survey Respondents Check Access and Physical Security  This brings us to number five on our list of cyber security statistics. While it's true that it's vital for organizations to focus on their digital security measures, that's not to say that they can ignore or forget about physical security. In that same Experian breach preparedness study, another nearly three-quarters of the respondents indicated that they regularly review "physical security and access to confidential information." While it's a relief that the majority of respondents indicate that they are looking into and monitoring these things, ideally, this number should be 100%. That's because everyone should be making an effort to regularly review physical security and access within their organization to ensure that their data and systems don't become compromised. 6. IoT Platform Revenue Forecast to Reach $66 Billion in 2020 Let's switch gears a little bit. Revenue growth for IoT platforms will grow 20% this year, Juniper Research forecasts in its report IoT ~ The Internet of Transformation 2020. Interestingly, the research company anticipates that the COVID-19 pandemic will play a role in increasing the IoT adoption in healthcare. 7. Online Payment Fraud to Cost Ecommerce At Least $25 Billion Annually by 2024 Ouch… This is a particularly painful cybersecurity statistic if it holds true. The outlook for ecommerce merchant losses to online payment fraud isn't a positive one, according to another Juniper Research report, Online Payment Fraud: Emerging Threats, Segment Analysis & Market Forecasts 2020-2024. They expect those losses to exceed $25 billion with a growth rate of 52% over the next four years. 8. 73% of "Leading" Organizations View Strong Cybersecurity as a Contributor to Business Success 73% of "leading" organizations that were surveyed by AT&T strongly agree with the idea that their organization's security posture is something that makes their overall business success much more likely. But what is a "leading" organization? AT&T defines that term in their 2020 benchmark report The Relationship Between Security Maturity and Business Enablement as those organization who "weave strong cybersecurity into the business, IT, and organizational culture" and tend to be further along in the NIST Cyber Security Framework than "following" or "emerging" organizations. They're also those organizations whose survey scores placed them in the top 20% of survey respondents. 9. "Leading" Organizations Are 4.3X More Effective at Prioritizing Cybersecurity Incidents Having the ability to prioritize cybersecurity threats and vulnerabilities based on their business impact is a necessary skill for every organization… That is, if they want to stay in business and all. AT&T's security maturity and business enablement survey shows that "leading" organizations are more than four times more likely to identify themselves as being "very effective" at doing so. Cyber Security Statistics: What Organizations Are Investing in Cyber SecurityCybersecurity is a critical area for organizations and businesses to invest in. In addition to your "human firewall," your cybersecurity systems and infrastructure are what's going to hold the line (or the door, for my fellow Game of Thrones fans) between your organization's sensitive data and the cybercriminals who want it. So, how much does this line of defense mean to many organizations? Let's see what kind of numbers governments, organizations, and businesses are willing to dedicate to strengthening their cyber defenses — and what kind of cost savings these efforts can provide — in our next section of cybersecurity statistics: 10. Global IT Spending Forecast to Total $3.9 Trillion in 2020 Gartner's most recent research estimates that worldwide IT spending will increase 3.4% in 2019 to nearly $4 trillion by the end of this year. So, which industry are they expecting to see the largest growth? The report indicates that software will experience a staggering estimated growth rate of 10.5%. Of course, how the impact of the Coronavirus (COVID-19) plays a role in how any spending-related estimates actually play out as the year progresses is anyone's guess. Only time will tell. 11. U.S. President's Budget Includes $18.8 Billion in Cyber Security Funding for FY 2021  According to the proposed Budget of the U.S. Government Fiscal Year 2021, the Trump administration plans to dedicate nearly $18.8 billion to spending on federal cybersecurity programs and initiatives. The budget document outlines more than $1.1 billion for the U.S. Department of Homeland Security's (DHS) cybersecurity efforts. Much like last year, of course, the Analytical Perspectives document for the FY 2021 budget stipulates that it doesn't include all cyber-related information. Why? "Due to the sensitive nature of some activities, this amount does not represent the entire cyber budget." Basically, it boils down to the standard statement about protecting national security. 12. Information Security Spending Forecast for 2023 Surpasses $151 Billion Data from the International Data Corporation's (IDC) Worldwide Semiannual Security Spending Guide indicates that global spending on security products and services is expected to increase to $151.2 billion by 2023. This is based on an estimated compound annual growth rate (CAGR) of 9.4% over that period. This is up from their estimated spending of $106.6 billion in 2019. The report indicates that the banking industry, discrete manufacturing industry, and federal/central government are forecast to be the biggest spenders globally in terms of security tools and solutions over this forecast period. 13. The Deception Technology Market is Forecast to Reach $2.48 Billion by 2025 Research from Mordor Intelligence forecasts a 13.3% CAGR for the deception technology industry within the next five years. Deception technology, which is used to detect and prevent advanced persistent threats (APTs), often integrates artificial intelligence (AI) and machine learning (ML) to make them more dynamic. It's something that, historically, the National Institutes of Standards and Technology (NIST) has stayed away from. But last year, they began recommending the use of deception techniques and technologies in NIST Special Publication 800-160 v2 and their draft of NIST SP 800-171B. (Author note: I know it's a little off topic, but can we Lord of the Rings fans just take a moment to appreciate this research company's name?) 14. COVID-19 Forecast to Slow Average Growth Rate of Cybersecurity Market to 6.2% Per Year  Although the cybersecurity market is still expected to grow, it's now forecast to do so at a slower rate. The Global Cyber Security Market Analysis by ResearchAndMarkets.com is saying the market will likely grow 6.2% per year to 2023 due to the economic impact of the Coronavirus pandemic. Yeah, this virus really is messing with everyone's plans. 15. Cybersecurity Prevention Efforts Can Save Businesses Up to $1.4 Million Per Attack Here's some really great news from the Ponemon Institute and Deep Instinct: Cyber attack prevention initiatives can have a significant payoff for organizations. Their study indicates that you could save up to 82% of the costs associated with the cybersecurity lifecycle (prevention, detection, containment, recovery, and remediation). So, if you're able to prevent a cyber attack that would have cost your business a cool $1 million, that would be a savings of $820,000 ($1,000,000-180,000 in prevention costs = $820,000 in savings). So, what's the downside? Keep reading. 16. 76% of Security Pros Focus on Detection and Containment Instead of Prevention So, even though research from Ponemon Institute and Deep Instinct shows that prevention can save you lots of moolah, only 24% of cybersecurity pros they surveyed actually focus on prevention. Why? Because they perceive containment to be more "accountable" than prevention. So, as a result, the majority of cybersecurity budgets go towards activities within the other four steps of the cybersecurity lifecycle. 17. 93% of Organizations Have or Plan to Get API Gateway Protection Application programming interface (API) cybersecurity is a growing area of interest for nine in 10 surveyed users, according to CyberEdge Group's 2020 Cyberthreat Defense (CDR) Report. 63.1% of respondents indicate that they already use API gateway/protection, and another nearly 30% indicate that they plan to get it within the next 12 months. 18. 60% of IT Professionals Believe Cybersecurity Budgets Are Lacking Perceptions about cybersecurity budgets sure do vary across organizations. Current data from ISACA's State of Cybersecurity 2020 global report indicates that 41% of respondents think their organization's budget is "somewhat underfunded" and another 19% indicate that it's "significantly underfunded." Another 34% said they think it's "appropriately funded" and 3% believe the budget to be "somewhat overfunded." This is one of those cyber security statistics that we hope our readers really take to heart… Don't be stingy — dedicate your budget where it needs to go. We know that there are other budgetary concerns, but if your business takes a major hit from a data breach or cyber attack, your reputation (and your organization as a whole) may not be able to withstand the consequences. So, don't wait until after crap goes wrong to make the right budgetary decision. 19. 69% of Experts Say Cybersecurity Cost Increases are Unsustainable 60% of the respondents to Accenture's Third Annual State of Cyber Resilience survey report indicate that they've increased their investments in cybersecurity technologies such as network security, threat detection, and security monitoring over the past two years. However, nearly seven in 10 respondents indicate that the cost of these investments to stay ahead of cyber threats is unsustainable in the long term. Cyber Security Statistics: Where the Industry Stands in Terms of EmploymentHiring and employment are important areas of consideration for virtually every industry, and cybersecurity and IT are no different. With this in mind, here are a few of the top employment and hiring-related cyber security statistics you should see: 20. 82% of CISOS Report Feeling "Burned Out" as Professionals Symantec (now Broadcom), in collaboration with cybersec researcher Dr. Chris Brauer and Goldsmiths, University of London, says that data from their survey of more than 3,000 security decisionmakers in the United Kingdom, Germany, and France indicates that four in five CISOs are feeling significantly overwhelmed. Furthermore, 65% of respondents indicate that they feel like they're being set up for failure, and 64% indicate that they're contemplating leaving their jobs. 21. 62% of Organizations' Cybersecurity Teams are Understaffed, 57% Have Unfilled Positions  Global research from ISACA shows that when it comes to cybersecurity staffing and retention, many organizations are leaving too many seats at the table vacant. The ISACA's State of Cybersecurity 2020 report shows that 62% of respondents indicate that their organization's cybersecurity team is either somewhat or significantly understaffed, and 57% say that some cybersecurity positions within their teams remain unfilled. 22. 72% of IT Professionals Believe Their HR Departments Don't Understand Cybersecurity Hiring Needs While human resources departments may think they're doing a bang-up job of pre-screening cybersecurity candidates, nearly three-quarters of ISACA-surveyed IT professionals seem to think otherwise. Data from the ISACA State of Cybersecurity 2020 report indicate that IT pros think that HR occasionally (37%), rarely (30%) or never (5%) understands their needs. 23. 85% of IT professionals report having at least one certification How many IT-related certifications do you have? How about your employees? Eight in 10 IT professionals say they have at least one industry-related certification, according to Global Knowledge. This means that if you're looking to hire, four out of every five job applicants have at least one certificate, although many professionals have multiple certifications. Wondering what certifications hiring managers are looking for? Check out these insights from industry experts. 24. In the U.S., the Cyber Security Workforce Needs to Grow 62% to Meet Demands You've probably seen news headlines and other cyber security statistics articles talking about how unemployment rates within the cybersecurity industry hover near 0%. Research from ISC2's 2019 Cybersecurity Workforce Study also shows that in order for the industry to meet the needs of U.S. businesses, there needs to be significant employment growth to cover the nearly 500,000-person gap that exists. But the U.S. is still in a better position than the global cybersecurity workforce. ISC2's estimates indicate that the cybersecurity workforce needs to grow 145% to meet the demand of global businesses. 25. IT Security Architect/Engineer Role Is Biggest Area IT Personnel Are Lacking While there are many areas in which cybersecurity skills are having shortfalls, research from CyberEdge Group's 2020 Cyberthreat Defense Report shows that there are three areas where organizations are experiencing the biggest skills shortages:
26. Cybercriminals Prey on Job Seekers at an Average Cost of $3,000 Per Victim Although this particular cybersecurity statistic applies to all job seekers, we thought it would be a pertinent stat to include in this article as well. The FBI's IC3 reports that victims have reported financial losses and damage to their credit scores as the result of fake job scams. According to their January press release:
Cyber Security Statistics: Top Cyber Attack and Data Breach Statistics and TrendsIn this section cyber security stats list, we'll go over some of the top cyber attack statistics and data breach statistics that we found that we think would be of interest to you. The focus of this section isn't to talk about the financial costs of individual cyber attack events and breaches — those types of numbers will be discussed a little later in the two sections that list the top cyber attack statistics by year (2020 and 2019). 27. Americans Experience a 29% Decline in U.S. Robocalls in April 2020 Due to COVID-19 Pandemic 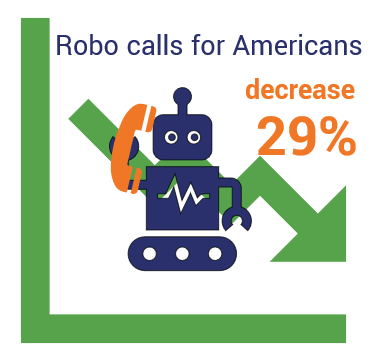 Ah, here's the silver lining! YouMail reports that Americans received nearly 30% fewer robocalls in April 2020 — only 2.86 billion (although I argue that even just one is too many). This is likely because international call centers in some countries are closed due to the virus. This decrease in calls follows a 30% drop in March and nearly a 45% drop in February — a stark contrast from the October 2019 record 5.7 billion calls that were reportedly made. 28. 7 Million: The Number of Data Records Compromised Daily Varonis reports that there are approximately 7 million data records compromised each day, and 56 records compromised each second. This means that in the average year (365 days), based on the number of daily breaches, there's about 2,555,000,000 (2.55 billion) records exposed annually. 29. SonicWall Reports Phishing Volume Was Down 42% in 2019 A surprising statistic that comes from SonicWall's 2020 Sonicwall Cyber Threat Report indicates that the overall number of phishing attacks decreased significantly last year. Part of this is because "Phishers are being measured, pragmatic and patient" in how they choose and target their victims. Basically, they're relying less on a spray-and-pray method and are making their attacks more focused and, therefore, more effective. 30. 8.4 Million DDoS Attacks Were Observed in 2019 There were more than 23,000 DDoS attacks each day last year, according to the NETSCOUT Threat Intelligence Report: Findings from 2H 2019. Netscout researchers equate that to about 16 attacks occurring every minute in 2019. That's literally one attack every 3.75 seconds! According to the report, cybercriminals took advantage of seven "new or increasingly used attack vectors" to help them carry out their distributed denial of service attacks. 31. Deepfake Scams: A $250 Million Problem in 2020 This is probably one of the most disturbing items on our list of cybersecurity statistics. As part of their 2020 cybersecurity predictions, Forrester Research predicts that the costs associated with deepfake scams are going to cost the world more than $250 million this year. In case you're not familiar with deepfake technology, deepfake scams use artificial intelligence (AI) and natural language generation technologies to fabricate seemingly real video and audio clips of a person. While this technology could be used for positive things like booking reservations at restaurants (although, really, how lazy are we that we would require a computer to do this for us?), the issue comes in when cybercriminals get their hands on it. To carry out a deepfake scam, threat actors use these generated pieces to impersonate people and pull off phishing attacks and other scams. So, now imagine when they use spoofing tactics on top of it. So, you could get a phone call from someone who sounds like your boss, using their phone number, and you might not be any the wiser. While we'd like to hope that these scams aren't going to be a big threat because of the amount of resources involved in preparing for one of these attacks, unfortunately, we're already starting to see the impact of this technology. Deepfake scams have already proven successful with the CEO of an unnamed U.K.-based energy firm losing $243,000 to such a scam last year. 32. Cloud-Based BEC Email Scams Top $2.1 Billion In Costs to U.S. Businesses In April, the FBI's IC3 team reported that between January 2014 and October 2019, they received numerous complaints about BEC scams targeting U.S. businesses that involved two cloud-based email services. Unfortunately for those affected organizations, these attacks resulted in actual losses of more than $2.1 billion during that period. But what exactly falls under the category of cloud-based email services? The IC3 says that these services are:
33. 279: The Mean Number of Days It Takes to Identify and Contain a Data Breach It's no secret that the faster you can contain a data breach, the less of an impact it'll have on your business financially. But this isn't very comforting considering that research from the Ponemon Institute and IBM in their 2019 Cost of a Data Breach report indicates that the mean amount of time it took to identify a threat in 2019 was 206 days, and the mean time to contain it was 73 days. This means that the costs could really pile up in the nearly 280 days it takes to discover and contain a breach. 34. SEGS Fail to Stop 99.5% of "Non-Trivial Email Spoofing Attacks" Next on our list of cybersecurity statistics is a topic relating to spoofing. Ironscales reports that nearly all of the 100,000+ verified spoofing attacks they studied over a two-year period made it through secure email gateways (SEGs). The same Ironscales survey also shows that the two most common type of spoofing attack used to bypass SEGs are "exact sender name impersonations" (73.5%) and "similar sender name impersonations" (24%). This is just one of many points on this growing list of cybersecurity statistics that underscores the importance of cyber awareness training for your employees. Technology isn't always going to be able to keep out every threat — this is why your employees need to understand how to identify these threats themselves by carefully analyzing emails before engaging with any links or attachments in them. 35. Cyber Fraud and Abuse Up 20% in Q1 2020 with 445 Million Attacks Reported With the three-ring circus security mess surrounding the COVID-19 global pandemic, cybercriminals are having a field day at the expense of individuals and organizations alike. In their Q2 2020 Fraud and Abuse report, Arkose Labs reports a 20% spike in cyber fraud incidents as a result of the virus. In fact, their research states that 445 million cyber attacks have been detected since the beginning of 2020. Considering that there's still no end in sight regarding the virus situation, we'll likely see these numbers continue to increase. 36. COVID-19 Email Scams Increased More Than 650% in March 2020 I know, you're tired about hearing about COVID-19, aka the Coronavirus. But it's important to note the role that this pandemic has played in the cybersecurity sector. This brings us to number 36 on our list of cybersecurity statistics. Barracuda Networks reported in March that COVID-19-themed spear phishing emails skyrocketed 667% between March 1 and March 23. 37. 50.55: The Average Number of Days It Takes to Remediate Web App Critical Vulnerabilities  According to their 2020 Vulnerability Statistics Report, Edgescan research indicates that organizations reported in 2019 that it took nearly eight weeks to "remediate critical risk vulnerabilities for public internet-facing web applications and 49.26 days for internet-facing network layer critical risk vulnerabilities." While 50 days is still a long time, it's actually a decrease of 18 days since 2018. 38. Gaming and IT Platforms Experience 39% Increase in Attacks in Early 2020 Times are changing, and cybercriminals are changing their behaviors and avenues of attacks to match. According to Akrose Labs' Q2 2020 Fraud and Abuse report, more people are spending a greater amount of time communicating personally and professionally online as the result of the Coronavirus. As such, they've witnessed an increase in cyber attacks targeting specific industries — retail and travel (26%), gaming (23%) and tech platforms (16%). 39. Gift Cards Account for 62% of BEC Attack Cash-Out Methods in Q4 2019 Cybercriminals are always looking for the easiest or most effective ways to scam people, and the same can be said about their approach to getting a payout. In this item on our list of cyber security statistics, data from Agari's Q1 2020 Email Fraud & Identity Deception Trends Report indicates that nearly two-thirds of business email compromise (BEC) attacks in Q4 2019 involved requested payments from victims via gift cards. The next most common payment method was direct transfer (wire transfer), which comes in at 22%. Cybercriminals love gift cards for many reasons — one of which is that this form of digital currency isn't held to the same anti-fraud standards as their credit and debit card counterparts. Another reason is that they can turn around and sell the gift cards they fraudulently gain in online exchanges at a profit. These cards are also easier to trade and use at legitimate businesses — after all most store employees won't think twice about someone using a gift card, but they may ask for ID when you use a credit card to make a large purchase. 40. The Average Cost of a BEC Fraud Wire Transfer Payment Is More Than $55,000 While it may not be the most commonly requested payment method, wire transfer requests are, by far, the most potentially profitable for BEC cybercriminals. Agari's Q1 2020 Email Fraud & Identity Deception Trends Report states that while the average gift card request was $1,627, the average amount they requested that their targets pay via wire transfers was nearly $55,395. That means that BEC fraudsters are requesting 3,305% more via individual wire transfers than they do in individual gift card payments! Part of the reason why these are so profitable is that BEC scammers target large organizations and enterprises that regularly make large wire transfer as part of everyday business transactions. Someone may think twice if they're asked to buy a $50,000 gift card, but they may not bat an eyelash if they're asked to make a wire transfer payment of that size to a vendor because they're used to doing that as a regular business expense. 41. 44% of "Non-Leader" Organizations Report At Least 500,000 of Their Customer Records Exposed Accenture's Third Annual State of Cyber Resilience report breaks the organizations they survey down into two groups: leaders and non-leaders. The first includes organizations whose cybersecurity programs cover 85% of their organization; the latter encompasses organizations whose cybersecurity programs cover a little more than half. With this in mind, 44% of those "non-leader" organizations say that more than 500,000 customer records were exposed last year. This is a stark contrast from those who are considered "leaders," only 15% of whom indicate that same level of customer data exposure. Cyber Security Statistics: A By-the-Numbers Look at Victims and Compromised Records Data42. Le Figaro Database Misconfiguration Exposes 7.4 Billion Records  Security Detectives researcher Anurag Sen and his team discovered an enormous data leak from Le Figaro, France's major news site. Bleeping Computer reports that the 8 TB of data, which was hosted on a Poney Telecom Elasticsearch server, contained a variety of PII of site users, including:
Some of the exposed data, such as full names and email addresses, belonged to Le Figaro's employees and reporters. The researchers say that both new accounts and pre-existing accounts that were accessed between February and April 2020 were part of those records. Sacre bleu! 43. 91 Million Tokopedia Accounts and Passwords Listed for Sale on the Dark Web Under the Breach, a cybersecurity firm, shared with BleepingComputer that a hacker was selling a cache of accounts and passwords for 91 million Tokopedia users. The cost? Just a measly $5,000. The article reports that although only a small subset of the PostgreSQL database fields actually contain sensitive data:
44. Aptoide Data Breach Exposes More Than 20 Million Customer Records Aptoide, a third-party Android app store, reported a breach of its database in April 2020 that led to the exposure of more than 20 million customer records. The company reports that "Besides your email address used for login and encrypted password, no Aptoide user's personal data is in the database." Oh, that's reassuring… Only your login and passwords have been exposed. Considering that a large percentage of users say that they re-use passwords and login credentials across multiple accounts, this is something many affected users should be concerned about. 45. More Than 15 Billion Records Exposed in Data Breaches in 2019 Last year was another "worst year on record" with regard to data breach activity, Risk Based Security reports in their 2019 Year End Report Data Breach QuickView. That statement is to be expected considering that the company reports that 7,098 breaches resulted in the exposure of more than 15.1 billion records. While the number of breaches themselves increased only slightly over 2018, the number of exposed records jumped 284% over the exposed records reported in 2018, and increased 91% compared to the same data reported for 2017. 46. 9.2 Million Suspicious Emails Reported in 2019 While that may not seem quite as bad as some of the numbers you've seen so far on this list of cybersecurity statistics, what's important to note is that this number represents only the suspicious emails that were reported by the end users of Proofpoint's customers in 2019. This is a 67% increase over what they reported the year prior. And, again, this is just the end users related to one company's customers. But, at least, it gives a little perspective of what's going on in the industry as a whole. 47. 425 GB of Sensitive Records Leaked Due to Financial Companies' Unsecure Database More than half a million sensitive and confidential financial and legal records were exposed as part of a 425 GB treasure trove, ZDNet reports. The data, which was discovered by a vpnMentor's research team, came from an open database that was connected to MCA Wizard, an app that was developed by Argus Capital Funding and Advantage Capital Funding. According to ZDNet's report, the AWS S3 bucket lacked basic security measures — such as encryption, authentication measures or access credentials. 48. The PII of 10.6 Million MGM Resorts Guests Compromised in 2019 Attack In February 2020, ZDNet reported that MGM Resorts stated that the personally identifiable information (PII) of 10,683,188 former guests was discovered to have been accessed from a cloud server in 2019. The majority of the exposed information includes the guests' names and phone numbers. According to the ZDNet report:
49. Brazilian Biometric Company Exposes 81.5 Million Records, Including Fingerprints, on Unsecure Server The use of biometric data is often considered one of the most secure forms of security authentication. Biometrics includes a variety of identifying factors and technologies such as retinal scans, facial recognition software, and fingerprint scanning. But Security Detectives researcher Anurag Sen and his team discovered 16 GB worth of data on an unsecured Elasticsearch server belonging to Antheus Tecnologia, a Brazilian biometric solutions provider. The database included 76,000 fingerprints, as well as employee company emails and telephone numbers According to a CNet report, Antheus Tecnologia said that there wasn't any sensitive data on the server, and that the fingerprints didn't come from customers and was actually publicly available data from its development team and NIST. 50. U.S. Federal SBA Loan Program Data Breach Exposes Nearly 8,000 Business Applicants As if many small businesses weren't struggling enough already due to the Coronavirus situation, it turns out the website for the federal government's Economic Injury Disaster Loans (EIDL) program was the source of a data breach. In March, the Small Business Association (SBA), which manages the applications for program, sent out letters to the impacted applicants informing them that their PII, financial and insurance information may have been exposed. How is this possible? It boils down to a web application flaw. Simply by hitting the "back" button during the first round of the online loan application process resulted in the app displaying the information entered by previous applicants. There's no telling yet as to who saw whose information, or whether any leaked information has been used maliciously. Only time will tell. 51. The PII of 6.5 Million Israeli Voters Leaked via App-Promoting Website The personal data of 6,453,254 Israeli voters was leaked via flawed software for a voting app called Elector, the news organization Haaretz reports. The leaked information included vital information, including:
The software vulnerability made it possible to not only view but also download the entire voter registry, according to The New York Times. Considering the entire population of the country is estimated to be around 8.6 million, according to the most recent data from the United Nations, we're talking about the majority of the country's population. 52. 530,000+ Compromised Zoom Accounts Sold (or Given Away) Online Zoom's not-so-secure encryption has been a hot topic of debate. But something more people have been interested in is that more than a half-million Zoom accounts were being peddled via the dark web and hacker forums for as little as $0.0020 per account, according to Bleeping Computer. The accounts were obtained using "credential stuffing attacks where threat actors attempt to login to Zoom using accounts leaked in older data breaches." Bleeping Computer reports that they were informed about the breach by researchers at the cybersecurity firm Cyble. 53. 160,000 Nintendo User Accounts Compromised via Legacy Network Accounts We mentioned earlier that cyber attacks on the gaming industry are increasing. Here's one of those examples. The Japanese game company Nintendo reported unauthorized access to about 160,000 accounts via Nintendo Network IDs (NNIDs). Compromised information includes nicknames, dates of birth, country/region, and email addresses. However, no credit card information was reportedly access during the breach. Cyber Security Statistics: The Costs of the Top Cyber Attacks and Data Breaches in 2020 (So Far)54. Hackers Demand $42 Million Ransom for A-Lister Law Firm's Data Page Six reports that a New York entertainment law firm used by major celebrities around the world was the target of a ransomware attack. The attackers, a hacker group by the name of REvil, initially demanded payment of $21 million of Grubman, Shire, Meiselas & Sacks to prevent them from releasing documents from the 756 GB cache of the firms' celebrity clients' confidential documents, emails, and contracts that they stole. The article stands that the hackers' ransom demands have since doubled to $42 million. According to a statement issued by the law firm to Page Six:
Whether or not they decide to pay — which it doesn't sound like the law firm is willing to do — remains to be seen. We'll just have to stay tuned to see how the situation turns out. 55. Three BEC Attacks Cost the Puerto Rican Government $4 Million According to a report by the Associated Press, the Puerto Rican government lost a total of more than $4 million in three separate business email compromise attacks in January 2020. Of the losses, $2.6 million alone came from an attack that targeted Puerto Rico's Industrial Development Company, and another $1.5 million targeted Puerto Rico's Tourism Company — both of which are government-owned organizations. 56. Shark Tank Investor Barbara Corcoran Loses Nearly $400,000 to a BEC Scam In February 2020, a cybercriminal decided to take a bite out of real estate tycoon and business investor Barbara Corcoran. She was the victim of a successful business email compromise (BEC) scam that cost her $388,700.11, according to People Magazine. The attack, which was later traced to a Chinese IP address, occurred when the criminal, posing as Corcoran's assistant, sent an email to Corcoran's bookkeeper requesting a wire transfer to pay for a real estate renovation. Thankfully, for Corcoran, USA Today reports that the money has since been returned. So, how did the attack originally happen? In the USA article, Corcoran says:
57. Americans Lose $24.44 Million to Coronavirus-Themed Scams (So Far) As if that number isn't bad enough on its own — just remember, this is likely only the beginning. The Federal Trade Commission (FTC) reports that they recorded 36,238 complaints between Jan. 1 and May 5, 2020 with total losses approaching $25 million. The states with the highest numbers of complaints include California (4,010), Florida (2,515), New York (2,220), Texas (2,196) and Massachusetts (1,515). Cyber Security Statistics: The Costs of BEC Scams, Cyber Attacks, and Data Breaches in 201958. $3.92 Million Is the Average Total Cost of a Data Breach 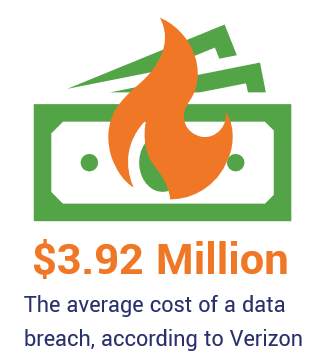 Although this research is from 2019, the Ponemon institute and IBM's 2019 Cost of a Data Breach Report is still a great resource for getting current estimates of costs associated with data breaches. Their data reports a total average cost of $3.92 million per data breach at a cost of $150 per lost record. Their report also indicates that a breach that has a lifecycle of less than 200 days costs $1.2 million less than one with a lifecycle that extends past 200 days. 59. $37 Million — The Amount a Toyota Subsidiary Lost to a BEC Scam in August 2019 2019 wasn't a great year for Toyota and its subsidiaries when it comes to cybersecurity. Proofpoint reports that Toyota Boshoku, a subsidiary of the Toyota car manufacturing company, lost tens of millions of dollars to a BEC scam. According to a news release from the Toyota Boshoku Corporation:
60. Nikkei America Lost $29 Million to EAC Attack in September 2019 Nikkei America, the U.S. subsidiary of Japan's media conglomerate, was the target of an email-based attack. Nikkei, Inc. (Japan) reports that an employee at its American subsidiary made a wire transfer based on instructions that were received via email from someone pretending to be a company executive. While the official statement says that they're "taking immediate measures to preserve and recover the funds that have been transferred," there's been no follow up stating whether their efforts have been successful. 61. Texas School District Loses $2.3 Million to Phishing Scam Looks like a cybercriminal decided to try their hand at "schooling" the education system with this next point on our list of cybersecurity statistics. Manor Independent School District reported on Twitter that it lost around $2.3 million due to a phishing scam, according to a report by CNN. The attack, which involved three fraudulent transactions, took place in November 2019 but weren't publicly reported until January 2020. 62. Erie, Colorado Loses $1.01 Million to a BEC Scammer Posing as Construction Company Cybercriminals are, unfortunately, very creative and always come up with new ways to shake down businesses. In this particular situation, a scammer pretended to be a local construction company that completed work on the Erie Parkway Bridge, the Denver Post reports. The criminal submitted an online request via the town's website that asked for any future payments made for work completed to be paid electronically. Two payments, totaling more than a million dollars, were then subsequently wired electronically to the cybercriminal's account where they were then transferred elsewhere. Security Intelligence also reports that even though the town had guidelines in place, the staff member who accepted the changed payment information form didn't follow them. 63. Chinese Venture Capital Firm Loses $1 Million in Seed Money in Elaborate Scam A Chinese venture firm that had a deal with an Israeli startup lost $1 million to an elaborate targeted phishing campaign that used a combination of BEC tactics, look-alike domains and a MitM attack, Check Point reports. Not only did the threat actor use spoofed emails to communicate with both groups, while impersonating real contacts on both sides, but the cybercriminal also registered two fake domains that looked nearly identical to the organizations' websites. The entire attack involved a total of 32 emails — nearly three dozen messages — between the attacker and the two firms! Cyber Security Statistics: A Look at the Types of Threats That Can Impact Your BusinessCybercriminals are always seeking out new and inventive ways to victimize their targets. Sometimes, it's just putting a new shade of lipstick on the pig by applying new tactics to old scams. But regardless of the tactics they use, it's up to us as businesses, government agencies, and consumers to educate ourselves and our employees about these threats. Next on our list of cyber security statistics, we've put together some categories or areas to look out for when working to strengthen your cyber defenses: Employee Complacency or Collaboration Issues64. 63% of Emerging Organizations Ignore More Than 25% of Security Events and Alerts AT&T's previously-referenced benchmark report for The Relationship Between Security Maturity and Business Enablement study shows that more than nearly two-thirds of leading organizations ignore more than 25% of their security alerts and events because investing every individual alert is too "impractical." More than half (52%) of following organizations and 27% of leading organizations say the same. 65. 77.4% of Respondents Indicate Poor Relationships Exist Between Their IT and Security Teams Collaboration is critical when it comes to making an organization's cybersecurity programs and initiatives most effective. However, it's not all sunshine and rainbows when it comes to collaboration between IT and security teams, according to VMWare Carbon Black's March 2020 Cybersecurity Outlook Report. The study, which was conducted by Forrester Consulting, indicates that more than three-quarters of survey respondents view the relationship between the two groups as being sour. 66. 55% of organization Say Collaboration Needs to Be a Top Priority The good news, at least, is that the majority of organizations realize that collaboration is key to improving their overall cybersecurity. Data from VMWare Carbon Black's Cybersecurity Outlook Report indicates that more than half of their survey respondents indicate that they want to make collaboration between their IT and security teams a top priority over the next year. Poor Asset Visibility and Management67. 74% of Organizations Don't Know How Many Digital Keys and Certificates They Have Nearly three-quarters of the respondents from KeyFactor and the Ponemon Institute's 2020 public key infrastructure research study report that their organizations are unaware of the total number of keys and digital certificates they actually have or use. Why? Because they lack visibility into their PKI certificate management. This includes the use of X.509 digital certificates such as SSL/TLS certificates. So, if you don't know how many certificates you have — let alone where to find them or when they expire — how can you possibly manage or renew them before they expire? Simply put: you can't.  Manage Digital Certificates like a Boss 14 Certificate Management Best Practices to keep your organization running, secure and fully-compliant. 68. 64% of Professionals Don't Know All of Their Organization's Endpoints and Web Apps What a disturbing thought. What if more than two-thirds of your own employees had no clue how many web applications or endpoints your organization had? This is the case for most of the pros surveyed in Edgescan's 2020 Vulnerability Statistics Report. Of course, what makes this worse is that 68% seem to believe their level of visibility is "average" within the industry. Defense Evasion Behaviors69. 90% of Analyzed Malware Demonstrate Defense Evasion Behaviors Just when you thought the issue with malware and ransomware couldn't get worse, VMWare Carbon Black shows up with attacker behavior data that digs that knife a little deeper. Their report, which maps out their attack data according to the MITRE ATT&CK™ Framework, states that defense evasion behaviors were observed in nine out of 10 samples of malware that they analyzed. This indicates that cybercriminals are being more stealthy in their approach and are actively trying to attack around legacy security solutions. This behavior was observed in 95% of ransomware samples. 70. 48% of Malware Demonstrate Software Packing and Hidden Windows for Defense Evasion Tactics Software packing, a "method of compressing or encrypting an executable" (according to MITRE), was the most common malware evasion behavior that VMWare Carbon Black observed in their analysis of the top malware behaviors of 2019. This category encompasses 26% of the samples, and hidden windows constituted 22%. Domain Impersonation/Spoofing71. Domain Impersonation Attacks Increase 400% in 4 Months In January 2020, Barracuda researchers reported that they'd observed an enormous jump in domain-impersonation attacks in relation to conversation hijacking. The company reported that they detected around 500 such attacks weekly in July 2019, but that the number quadrupled to more than 2,000 of these attacks per week in November 2019. Their research shows that this jump means that there were more than 2,000 attacks in the month of July 2019 alone and 8,500 attacks in November 2019. (The numbers in the source article are a bit unclear in terms of how the data was displayed in their article, so I reached out to Barracuda directly for clarification.) Lack of Visibility and Enforced Processes72. 46% of Professionals View Third-Party Access, Visibility as Barriers to IT Security Responses Nearly half of the professionals who responded to Experian's Seventh Annual Data Breach Preparedness Study indicate that a "lack of security processes for third parties that have access to our data" is a major barrier to their data breach response capabilities. Furthermore, 60% also indicated that a "lack of visibility into end-user access of sensitive and confidential information" is among the biggest impediments. HTTPS and Website Phishing73. Every 20 Seconds a New Phishing Site Goes Live As if website phishing wasn't already a bit enough issue, Wandera reports in their 2020 Mobile Threat Landscape Report that a new phishing site launches every 20 seconds. That's three new sites per minute that are specifically designed to victimize users and steal their information! 74. 74% of Phishing Websites Are Served Via HTTPS Protocol Just because you're connected to a website using an encrypted connection doesn't mean your data's safe. It's just as — if not moreso — important that you know what site or organization you're connecting to! Using data from PhishLabs, the Anti-Phishing Working Group's (APWG) Q4 2019 Phishing Activity Trends Report reports that nearly three-quarters of all phishing sites now use encrypted connections via SSL/TLS protocols. 75. 60% of Websites Use HTTPS as the Default Protocol We're happy to say that use of the HTTPS protocol is growing. W3Techs usage statistics show that as of May 8, 2020, nearly two-thirds of all sites use the HTTPS protocol as their default. This number is up from a little more than 50% in May 2019. The tricky part, though, is that some of these sites are going to malicious websites. This is why it's important to assert organizational identity on your site via an SSL/TLS certificate to help site visitors determine whether your site is legit or a fake. Insider Threats (Intentional or Negligence) 76. Cyber Incidents Involving Insider Threats Jump 47% Since 2018 It's no secret that humans are frequently the weakest link in your security defense — but new research from the Ponemon Institute further substantiates this claim. In their 2020 Cost of Insider Threats Global Report, published on behalf of ObserveIT and IBM, their findings indicates that the threat of insider threats is growing rapidly — nearly 50% in the last two years. Furthermore, their research shows that the average annual costs associated with these security threats rose 31% to $11.45 million over the same period. 77. Costs Associated with Insider Threat Prevention and Investigations Increases 60% since 2017 The Ponemon Institute's 2020 Cost of Insider Threats Global Report (sponsored by ObserveIT and IBM) also indicates that organizations are spending significantly more to detect and investigate insider threat-related activities. Specifically, the costs of insider threats to the financial services industry has increased more than 20% to $14.5 million since 2018. 78. Insider Threats and Insider Attacks Top the List of Biggest IT Security Challenges When it comes to judging their organizations' levels of functional security, respondents to CyberEdge Group's 2020 Cyberthreat Defense Report indicate that their greatest challenges relate to worrisome employee behaviors. They view the difficulty of detecting rogue insiders and insider threats as their biggest concern. This is closely followed by a lack of user security awareness. This might boil down to a lack of internal resources that they can use to train as well as monitor their employees. 79. Data Breaches Resulting from Human Error Cost Organizations an Average of $3.5 Million It's no secret that people are considered the biggest cybersecurity vulnerability for organizations. Data from the 2019 Cost of a Data Breach Report by the Ponemon Institute and IBM does nothing to squelch that concern. In fact, many of the cyber security statistics they share in their research further serve to underscore this concern. That's because their research indicates that human error results in data breaches that cost an average of $3.5 million. While this amount is more than what they estimate system errors or glitches cost (an average of $3.24 million), it's still at least less than the average cost of malicious and criminal attacks, which have a price tag of $4.45 million. 80. 90% of Working Adults Use Employer-Issued Devices for Non-Work Activities Nine in 10 working adults report using their employer-issued devices for personal activities, according to Proofpoint's 2020 User Risk Report. Around half of those surveyed also indicated that they also give their friends and family members access to those devices as well. IoT Security81. 83 Billion IoT Connections Expected to Be Made by 2024 New data from Juniper Research indicates that the total number of IoT connections will reach 83 billion by 2024. This is up from estimates of 35 billion connections in 2020, which represents a growth of 130% over the next four years. The industrial sector — which includes agriculture, manufacturing, and retail — is expected to account for more than 70% of those connections in that period. 82. Only a 5% Increase in IoT Malware Observed by SonicWall in 2019 While they report only a moderate (5%) increase in IoT malware (equating to about 34 million attacks) in their 2020 Sonicwall Cyber Threat Report, SonicWall Capture Labs threat researchers say that doesn't mean you can let down your guard. In fact, you should be preparing for the likelihood of increases in such attacks. For additional IoT-specific cyber security statistics, be sure to check out our article 20 Surprising IoT Statistics You Don't Already Know. Malicious ReCaptcha83. A Single Phishing Campaign Had More Than 128,000 Emails Using Fake ReCaptcha As we mentioned earlier, cybercriminals are always trying to put new shades of lipstick on their pigs. In this case, Barracuda researchers report that phishing email scams using malicious reCaptcha to block detection are on the rise. One email phishing campaign that the company analyzed contained "more than 128,000 emails using this technique to obfuscate fake Microsoft login pages." According to the article, "reCaptcha walls to prevent automated URL analysis systems from accessing the actual content of phishing pages." So, essentially, cybercriminals are preventing email security systems from identifying malicious websites. Password Security84. 65% of Users Use the Same Password Across Multiple Accounts With so many PSAs warning against the dangers of re-using passwords and the availability of key managers, we're exasperated to see that the number is still so high. According to the February 2019 Online Security Survey by Google and Harris Poll, 52% of users report using the same passwords across multiple accounts, and another 13% report reusing the same password across all accounts. 85. 24% of Survey Respondents Use a Password Manager The same Google/Harris Poll February 2019 Online Security Survey also reports that fewer than one-quarter of survey respondents indicate that they use a password manager. Surprisingly, the individuals who are more likely to rely on password managers are those who are age 50 and up. Phishing86. 94% of Malware Is Delivered via Email Nearly 9 in 10 instances of malware are delivered using emails as their delivery method, according to Verizon's 2019 Data Breach Investigations Report (DBIR). Of those types of malware, 45% are Office docs. 87. 86% of Email Attacks Lack Malware The bad news is that almost 9 in 10 email-based cyber attacks don't use malware, meaning that they're more likely to make it through your email security defenses. The really bad news is that this just means that cybercriminals are using other tactics to pull off their attacks. Data from FireEye indicates that cybercriminals are more commonly using spear phishing and various impersonation-based attacks to pull off their goals. 88. 37.9% of Users Fail Phishing Tests  Data from KnowBe4's Phishing by Industry Benchmarking Report indicates that nearly 38% of untrained end users are susceptible to phishing attacks and will fail phishing tests. This increase is a significant jump over their 2019 report of 8.3%. So, is there any good news? Yes, there is. KnowBe4's "phish-prone percentage" (PPP) data indicates that computer-based training and simulated phishing tests can help to improve those numbers:
89. More Than 3,900 Unique Users Fell for Mobile Banking Phishing Attack Over a 7-Month Period Recent data from Lookout indicates that nearly 4,000 victims fell for a mobile-only phishing attack campaign that targeted mobile banking users via SMS messages. The threat actors sent phishing links to fake websites impersonating well-known banks in North America to capture their sensitive info and login credentials. Their research shows the breadth of attacks globally with the U.S. being the hardest hit. Image source: Lookout 90. 87% of Successful Phishing Attacks Occur via Methods Other Than Email As you can see from our list of cyber security statistics, phishing doesn't only occur via email. Wandera reports in their 2020 Mobile Threat Landscape Report that nearly nine in 10 successful phishing attacks don't rely on email and frequently operate via other avenues of attack. So, while it's important to educate your users on the dangers of phishing emails, it's vital that you don't limit their education to only email concerns. Also be sure to educate them about the dangers of vishing (voice phishing), smishing (SMS phishing), and other phishing attack methods. To see more information relating to phishing statistics, be sure to check out our article Phishing Statistics: The 29 Latest Phishing Stats to Know in 2020. Ransomware91. The Cost of Ransomware Attacks Topped $7.5 Billion in 2019 Last year, $7.9 billion cost of ransomware attacks were felt by healthcare providers, various government organizations, and educational institutions around the U.S., according to Emsisoft's The State of Ransomware in the US: Report and Statistics 2019. 92. 85% of MSPs Rate Ransomware as a Common Threat to SMBs Data from Datto's Global State of the Channel Ransomware Report indicates that four-in-five managed service providers (MSPs) identified ransomware attacks as the leading malware threat to small and midsize businesses (SMBs). 93. 20% of SMBs Report Being Victims of One or More Ransomware Attacks Datto's Global State of the Channel Ransomware Report also states that one-in-five SMBs report their organizations have sustained ransomware attacks. 94. 10% Increase in Ransomware Detected in 2019 Despite Decrease in New Ransomware Families The detection of new ransomware families decreased by 57% in 2019, Trend Micro reports. But despite the decrease in new families, the IT security company said they detected a 10% increase in detections in the same period. This means that cybercriminals are attempting to carry out more attacks using fewer varieties of ransomware. 95. Ransomware Increased Average Downtime to 16.2 Days in Q4 2019 Downtime is a costly and frustrating experience for any organization regardless of size. But its impact can be felt far beyond just money and time — it also takes a severe toll on your reputation and the trust users and consumers place in you. According to Coveware's Q4 Ransomware Marketplace report, the downtime that resulted from ransomware attacks in the last quarter of 2019 jumped to an average of 16.2 days — a marked increase over their 12.1 day average reported the previous quarter. For additional ransomware statistics, be sure to check out our article Ransomware Statistics You're Powerless to Resist Reading. Web Applications96. Web Applications Attacks Increased 52% in 2019 In their 2020 SonicWall Cyber Threat Report, SonicWall Capture Labs reported that web application attacks more than doubled year over year. The main surge in attacks occurred after May, pushing the total number of web app attacks past 40 million. The main avenues of attack include SQL injections, broken authentication and session management, cross-site scripting (XSS), etc. 97. SQL Injection Accounts for 42% of Common Critical Internet-Facing Vulnerabilities SQL injection, just like other injection attacks, involves injecting data into input fields to affect the execution of pre-defined commands. In this case, though, they involve the use of SQL commands specifically. Edgescan reports in their 2020 Vulnerability Statistics Report that SQL injections accounted for 42% (one in five) of the most common critical vulnerabilities in internet-facing web applications last year. Cyber Security Statistics: A Breakdown of Cyber Attack Statistics by IndustryWe know — while it's interesting to read about cybersecurity statistics in general, it's much more useful to read statistics that apply specifically to your industry. That's why we've put together some industry-specific cyber security statistics that can shed some light on the types of threats or situation your organization — and others like it — are facing. 98. Three Industries Forecast to Account for 30% of Security Spending by 2023 The first in this section of our cybersecurity stats list encompasses several industries. Research from IDC's Worldwide Semiannual Security Spending Guide indicates that nearly 30% of global security spending between 2019 and 2023 is forecast to come from the banking and discrete manufacturing industries, as well as federal/central government. 99. Healthcare Data Breach Costs Come in at an Average of $6.45 Million  The 2019 Cost of a Data Breach Report by the Ponemon Institute and IBM indicates that healthcare is the most expensive industry in terms of the total average cost per breach. They also had the longest data breach lifecycle — the time it takes to identify and contain a breach — of 329 days. 100. 700 Healthcare Providers, 110 Governments and Agencies Victim to Ransomware in 2019 Data from Trend Micro indicates that ransomware threat actors have healthcare and governments in their sights. More than 700 healthcare providers were affected by ransomware attacks last year, and these types of attacks — along with other cyber attacks — are causing life-threatening situations at hospitals. At the same time, the company reports that "at least 110 US state and municipal governments and agencies fell victim to ransomware." But what makes these organizations so at risk? Frequently, it boils down to:
You'd think that after the WannaCry attacks of 2017 that crippled healthcare organizations and government agencies around the world that these types of organizations would be more proactive in updating their operating systems and patching vulnerabilities. But I guess some lessons are harder to learn than others… 101. Early 2020 Observes a 32% Increase in Ransomware Attacks Against Energy/Utilities Organizations Data from VMWare Carbon Black's 2020 Cybersecurity Outlook Report shows that while 2019 was a year of notable attacks against healthcare providers (764) and state and municipal governments and agencies (113), the first three months of 2020 are showing a clear increase in attacks targeting another vertical: Energy/Utilities. According to the report:
102. SaaS/Website Accounts for Nearly 31% of the Most Targeted Phishing Sectors in Q4 2019 It's no secret that cybercriminals love gaining access to email accounts. So it makes sense in some ways that the undesirable "honor" of being the #1 targeted sector for phishing, according to the APWG's Q4 2019 Phishing Activity Trends Report, goes to SaaS/webmail. This was followed by the payment industry (19.8%) and financial institutions (19.4%). 103. Collateral Damage: Satellite Telecommunications Experience 295% Increase in DDoS Attacks Sharing IP space with other organizations sucks, and I'd have to say that no one realized that more than the satellite telecommunications industry by the end of 2019. NetScout's NETSCOUT Threat Intelligence Report 2H 2019 reports that the frequency of DDoS attacks on satellite telecommunications skyrocketed nearly 300% in the second half of the year. Why? They attribute the increase to the result of the flood of DDoS attacks that impacted financial organizations in Europe and Asia minor during that period. According to the report:
Cyber security Statistics: IT and Data Privacy Compliance and Risk Management StatisticsManaging and mitigating risk is essential for every organization if they want to stick around. Part of that boils down to compliance with data security and privacy regulations — compliance isn't optional. While not all data privacy and encryption laws and regulations will apply to every organization or business, it's imperative that you and your employees know which ones do. For example, if you handle protected medical or health-related information, then you need to familiarize yourself with HIPAA. If your business handles payments made via payment cards, then you need to know about PCI DSS compliance requirements. Not to mention GDPR, CCPA, NYDFS… the list goes on and on, and it's continuing to grow as more countries and states create new laws and regulations. On that note, here are some applicable cybersecurity statistics that we thought would be of interest on this topic: 104. 52% of Legal and Compliance Leaders Worry about COVID-19 Related Cybersecurity Risks We know you're likely tired of hearing about the Coronavirus, but we're living in strange times. Many businesses — even if just temporarily — are adopting remote workforces due to the ongoing Coronavirus situation. The responses to a Gartner survey of 145 compliance and legal leaders indicate that organizational leaders are concerned about growing third-party cybersecurity risks as more their organizations are forced to allow their employees to work remotely. Their concerns range from the use of insecure networks to threats of bribery and corruption to fraud and privacy risks. 105. More than 40% of Privacy Compliance Technologies Anticipate Using AI by 2023 Another Gartner survey estimate that artificial intelligence (AI) will play a more significant role in privacy compliance technology within the next three years. With the advances we've been seeing in artificial intelligence (AI) — as well as the increasingly stringent data privacy and security related laws and regulations that have come out — in recent years, as well as the increasing reliance on AI within the cybersecurity industry, it seems like a logical next step in compliance and risk management. 106. 67% of Enterprise Survey Respondents Identify Data Visibility as Biggest Challenge The handling of sensitive data is frequently an issue for businesses regardless of size. According to the Ponemon Institute's 2020 Global Encryption Trends Study, more than two-thirds of the survey's respondents say that their organization's biggest challenge is locating sensitive information. Another 31% share that identifying and classifying which data to encrypt is another significant challenge. 107. Only 36.7% of Global Organizations Report Maintaining Full Compliance with PCI DSS  It's a disturbing trend, but it's one you need to know, which is why we've included it on our list of cybersecurity statistics. Slightly more than one-third of surveyed organizations say they were actively maintaining their Payment Card Industry Data Security Standards (PCI DSS) programs in 2018, according to Verizon's 2019 Payment Security Report (PSR). This is a significant drop from the 55.4% who reported 100% compliance during interim validation in 2016! 108. Data Protection Compliance Programs: 20% Advanced, 0% Optimized Verizon's 2019 Payment Security Report reports that of the 55 organizations they surveyed for their 2018 PSR, only one-in-five rated their PCI data protection compliance programs (DPCP) as "advanced." What's worse is that none of them rated the maturity of their programs as "optimized." While it's bad enough that so few organizations have DPCP programs that are considered advanced, what's even worse is that many organizations don't even bother to measure the maturity of their payment card industry (PCI) security programs at all! 109. 48% of Enterprises Report Having and Applying a Consistent Encryption Strategy The 2020 Global Encryption Trends Study by the Ponemon Institute, sponsored by nCipher and Entrust Datacard, indicates that nearly half of the respondents indicate that their organizations have and consistently apply an encryption plan across their enterprises. Only 39% of respondents indicate that they have a limited plan that's applied to specific types of data and applications. The first cyber stat represents an increase of 11% since FY 2015 and the second, a decrease of 6% in the same period. Another 13% indicate that they have no encryption plan or strategy overall. This has been a pretty consistent number since it was reported in FY 2016. 110. 58% of Organizations Use the Cloud for Sensitive or Confidential Data The same Ponemon Institute 2020 Global Encryption Trends Study reports that more than half of respondents indicate that their businesses use cloud technology to transfer or store data — regardless of whether it's encrypted or protected via any security mechanisms. This number decreased 2% from last year's survey result of 60%. Cyber Security Statistics: Cybersecurity Statistics By LocationSo, what are some of the key cyber security stats if you're more interested in looking at data that's broken down by country or region? Yeah, we've got you covered for that as well with this location-specific cybersecurity data: North America111. $8.19 Million: The Average Cost of a Data Breach in the U.S.  The U.S. leads the way with the highest average cost of a data breach, according to the Ponemon Institute and IBM's 2019 Cost of a Data Breach report. Not exactly the ranking we're hoping for, but also not necessarily unexpected, either. 112. 44% of U.S. Users Indicate They Use Password Managers Many cybersecurity experts promote the idea of using password managers. Here in the U.S., we have a far higher password manager usage rate than other countries, according to Proofpoint's 2020 User Risk Report. Globally, only 23% of respondents indicate that they use a password manager. South America113. Phishing Attacks in Brazil Increased 275.5% Between Q1 and Q4 2019 Brazil, the largest economy in South America, experienced 24,251 phishing attacks in 2019, according to data from Axur, the APWG reports in its Q4 2019 Phishing Activity Trends Report. Q1 2019 had the fewest phishing attacks, with just 3,220 observed. However, in Q4 2019, they reported observing 8,872 such attacks. That's an increase of nearly 276% from Q1 to Q4! 114. 35.7% of Email URLs in Brazil Are Malicious In other phishing news, Brazil also claims first place when it comes to having the highest percentage of malicious links in emails. According to Broadcom's 2019 Internet Security Threat Report (formerly the Symantec ISTR), more than one-third of all emails contain malicious links. They're followed by Mexico (29.7%), Norway (12.8%), and Sweden (12.4%). 115. 42% of Cyber Attacks in Colombia Resulted From Malicious Websites Malicious websites are a threat to organizations, governments, and users the world over. But one in five survey respondents in Colombia said that their organizations were hit by cyber attacks in the last year that used this attack vector specifically, according to Sophos' report The Impossible Puzzle of Cybersecurity. Mexico and Central America116. Nearly 94% of Organizations in Mexico Were Compromised in Last 12 Months  Topping the list of organizations that have experienced at least one successful cyber attack within the last year is Mexico with this shocking cyber security statistic. CyberEdge Group's 2020 CDR report shows that the country ranked No. 1 with 93.9% of surveyed organizations indicating that their organizations sustained at least one successful attack. 117. Nearly 25% of Cyber Attacks in Mexico Result from External Media Devices Different countries tend to show greater vulnerabilities to some attack vectors more than others. For Mexico, one in four attacks within the last year resulted from the use of external media devices such as USB sticks, Sophos reports in The Impossible Puzzle of Cybersecurity. This is why it's important to train employees to only use company-provided devices and to enforce company computer use policies. Middle East118. One in Every 118 Emails in Saudi Arabia Is Malicious Looks like Saudi Arabia leads the world in terms of the highest number of malicious emails, according to Broadcom's 2019 ISTR. They are followed by Israel (1 in 122), Austria (1 in 128), and South Africa (1 in 131). 119. 52.68% of Iranian Users Have Mobile Malware Infections Mobile malware is a growing issue in many countries, various lists of cyber security statistics show. But Comparitech reports that they observed that more than half of the users who sustained cyber attacks in Q3 2019 had mobile malware infections. Europe120. 110,000 Daily Bot Infections in German IT Systems Reported There were up to 100,000 daily bot infections affecting German IT systems reported to the BSI between June 1, 2018 and May 31, 2019, according to The State of IT Security in Germany in 2019 report and data from AV-Test Institute. The data is from Germany's Federal Office for Information Security (Bundesamt fur Sicherheit in der Informationstechnik, or BSI for short). But the report indicates something even more disturbing:
121. German Institute Registers 350,000+ New PAUs and Malware Daily Here's another dose of malware-related cyber security stats to make your day. As of May 4, the AV-TEST Institute reports that they register more than 350,000 new potentially unwanted applications (PAUs) and malicious software each day. Yes, they register that many new PAUs and malware every day. 122. Denmark Reports the Lowest Number of Users with Malware Infections (3.15%) And, last but not least, our final item on this list of cyber security statistics. Based on seven specific criteria items, Denmark is ranked the world's most cyber-secure country by Comparitech. Their numbers, based on Q3 2019 reported cyber attacks, moved them up from fourth place in Comparitech's 2019 report. Compare this to the United Kingdom (7.69%), U.S. (9.075), and France (15.09%). While there are many other compelling cyber security statistics out there, we simply can't compile and write about all of them. There isn't enough time and, frankly, "current" cybersecurity stats are always changing as new data comes to light. However, be sure to subscribe and follow our blog because many aspects of the statistics we've covered — and other stats that we haven't yet touched upon — will be covered in future Hashed Out blog posts. Stay tuned. Wrapping Up the 2020 List of Cyber Security StatisticsYeah, that was a lot to take in. But we hope that this list of cyber stats provides you with a plethora of useful information about every aspect of cybersecurity. Looking at the data here, it's easy to see that cybercriminals represent an imminent threat to businesses, governments, and consumers alike. However, it also demonstrates that the biggest threats exist within our own organizations — and I'm not just talking about insider threats. No, I'm talking about:
Thankfully, there are things you can do to help protect your organization from many of these growing threats. Follow industry best practices, implement the use of defense technologies and resources from reputable vendors, and offer in-house or third-party cyber awareness training to decrease employee ignorance and apathy. Do you have other current cyber security statistics that you'd like to share with me and your fellow readers? I'd love to see them! Be sure to share them in the comments section below. *** This is a Security Bloggers Network syndicated blog from Hashed Out by The SSL Store™ authored by Casey Crane. Read the original post at: https://www.thesslstore.com/blog/cyber-security-statistics/ |
| Putin Is Well on His Way to Stealing the Next Election - The Atlantic Posted: 15 May 2020 03:28 PM PDT Jack Cable sat down at the desk in his cramped dorm room to become an adult in the eyes of democracy. The rangy teenager, with neatly manicured brown hair and chunky glasses, had recently arrived at Stanford—his first semester of life away from home—and the 2018 midterm elections were less than two months away. Although he wasn't one for covering his laptop with strident stickers or for taking loud stands, he felt a genuine thrill at the prospect of voting. But before he could cast an absentee ballot, he needed to register with the Board of Elections back home in Chicago. To hear more feature stories, get the Audm iPhone app. When Cable tried to complete the digital forms, an error message stared at him from his browser. Clicking back to his initial entry, he realized that he had accidentally typed an extraneous quotation mark into his home address. The fact that a single keystroke had short-circuited his registration filled Cable with a sense of dread. Despite his youth, Cable already enjoyed a global reputation as a gifted hacker—or, as he is prone to clarify, an "ethical hacker." As a sophomore in high school, he had started participating in "bug bounties," contests in which companies such as Google and Uber publicly invite attacks on their digital infrastructure so that they can identify and patch vulnerabilities before malicious actors can exploit them. Cable, who is preternaturally persistent, had a knack for finding these soft spots. He collected enough cash prizes from the bug bounties to cover the costs of four years at Stanford. Though it wouldn't have given the average citizen a moment of pause, Cable recognized the error message on the Chicago Board of Elections website as a telltale sign of a gaping hole in its security. It suggested that the site was vulnerable to those with less beneficent intentions than his own, that they could read and perhaps even alter databases listing the names and addresses of voters in the country's third-largest city. Despite his technical savvy, Cable was at a loss for how to alert the authorities. He began sending urgent warnings about the problem to every official email address he could find. Over the course of the next seven months, he tried to reach the city's chief information officer, the Illinois governor's office, and the Department of Homeland Security. As he waited for someone to take notice of his missives, Cable started to wonder whether the rest of America's electoral infrastructure was as weak as Chicago's. He read about how, in 2016, when he was a junior in high school, Russian military intelligence—known by its initials, GRU—had hacked the Illinois State Board of Elections website, transferring the personal data of tens of thousands of voters to Moscow. The GRU had even tunneled into the computers of a small Florida company that sold software to election officials in eight states. Out of curiosity, Cable checked to see what his home state had done to protect itself in the years since. Within 15 minutes of poking around the Board of Elections website, he discovered that its old weaknesses had not been fully repaired. These were the most basic lapses in cybersecurity—preventable with code learned in an introductory computer-science class—and they remained even though similar gaps had been identified by the FBI and the Department of Homeland Security, not to mention widely reported in the media. The Russians could have strolled through the same door as they had in 2016. From the January/February 2018 issue cover story: What Putin really wants Between classes, Cable began running tests on the rest of the national electoral infrastructure. He found that some states now had formidable defenses, but many others were like Illinois. If a teenager in a dorm room—even an exceptionally talented one—could find these vulnerabilities, they were not going to be missed by a disciplined unit of hackers that has spent years studying these networks, a unit with the resources of a powerful nation bent on discrediting an American election. #DemocracyRIP was both the hashtag and the plan. The Russians were expecting the election of Hillary Clinton—and preparing to immediately declare it a fraud. The embassy in Washington had attempted to persuade American officials to allow its functionaries to act as observers in polling places. A Twitter campaign alleging voting irregularities was queued. Russian diplomats were ready to publicly denounce the results as illegitimate. Events in 2016, of course, veered in the other direction. Yet the hashtag is worth pausing over for a moment, because, though it was never put to its intended use, it remains an apt title for a mission that is still unfolding. Russia's interference in the last presidential election is among the most closely studied phenomena in recent American history, having been examined by Special Counsel Robert Mueller and his prosecutors, by investigators working for congressional committees, by teams within Facebook and Twitter, by seemingly every think tank with access to a printing press. It's possible, however, to mistake a plot point—the manipulation of the 2016 election—for the full sweep of the narrative. Events in the United States have unfolded more favorably than any operative in Moscow could have ever dreamed: Not only did Russia's preferred candidate win, but he has spent his first term fulfilling the potential it saw in him, discrediting American institutions, rending the seams of American culture, and isolating a nation that had styled itself as indispensable to the free world. But instead of complacently enjoying its triumph, Russia almost immediately set about replicating it. Boosting the Trump campaign was a tactic; #DemocracyRIP remains the larger objective. From the April 2020 issue: George Packer on how Trump is winning his war on American institutions In the week that followed Donald Trump's election, Russia used its fake accounts on social media to organize a rally in New York City supporting the president-elect—and another rally in New York decrying him. Hackers continued attempting to break into state voting systems; trolls continued to launch social-media campaigns intended to spark racial conflict. Through subsidiaries, the Russian government continued to funnel cash to viral-video channels with names like In the Now and ICYMI, which build audiences with ephemera ("Man Licks Store Shelves in Online Post"), then hit unsuspecting readers with arguments about Syria and the CIA. This winter, the Russians even secured airtime for their overt propaganda outlet Sputnik on three radio stations in Kansas, bringing the network's drive-time depictions of American hypocrisy to the heartland. While the Russians continued their efforts to undermine American democracy, the United States belatedly began to devise a response. Across government—if not at the top of it—there was a panicked sense that American democracy required new layers of defense. Senators drafted legislation with grandiose titles; bureaucrats unfurled the blueprints for new units and divisions; law enforcement assigned bodies to dedicated task forces. Yet many of the warnings have gone unheeded, and what fortifications have been built appear inadequate. Jack Cable is a small emblem of how the U.S. government has struggled to outpace the Russians. After he spent the better part of a semester shouting into the wind, officials in Chicago and in the governor's office finally took notice of his warnings and repaired their websites. Cable may have a further role to play in defending America's election infrastructure. He is part of a team of competitive hackers at Stanford—national champions three years running—that caught the attention of Alex Stamos, a former head of security at Facebook, who now teaches at the university. Earlier this year, Stamos asked the Department of Homeland Security if he could pull together a group of undergraduates, Cable included, to lend Washington a hand in the search for bugs. "It's talent, but unrefined talent," Stamos told me. DHS, which has an acute understanding of the problem at hand but limited resources to solve it, accepted Stamos's offer. Less than six months before Election Day, the government will attempt to identify democracy's most glaring weakness by deploying college kids on their summer break. Despite such well-intentioned efforts, the nation's vulnerabilities have widened, not narrowed, during the past four years. Our politics are even more raw and fractured than in 2016; our faith in government—and, perhaps, democracy itself—is further strained. The coronavirus may meaningfully exacerbate these problems; at a minimum, the pandemic is leeching attention and resources from election defense. The president, meanwhile, has dismissed Russian interference as a hoax and fired or threatened intelligence officials who have contradicted that narrative, all while professing his affinity for the very man who ordered this assault on American democracy. Fiona Hill, the scholar who served as the top Russia expert on Trump's National Security Council, told me, "The fact that they faced so little consequence for their action gives them little reason to stop." David Frum: Trump has lost the plot The Russians have learned much about American weaknesses, and how to exploit them. Having probed state voting systems far more extensively than is generally understood by the public, they are now surely more capable of mayhem on Election Day—and possibly without leaving a detectable trace of their handiwork. Having hacked into the inboxes of political operatives in the U.S. and abroad, they've pioneered new techniques for infiltrating campaigns and disseminating their stolen goods. Even as to disinformation, the best-known and perhaps most overrated of their tactics, they have innovated, finding new ways to manipulate Americans and to poison the nation's politics. Russia's interference in 2016 might be remembered as the experimental prelude that foreshadowed the attack of 2020.  1. Hack the VoteWhen officials arrived at work on the morning of May 22, 2014, three days before a presidential election, they discovered that their hard drives were fried. Hours earlier, pro-Kremlin hackers had taken a digital sledgehammer to a vital piece of Ukraine's democratic infrastructure, the network that collects vote tallies from across the nation. After finishing the task, they taunted their victim, posting photos of an election commissioner's renovated bathroom and his wife's passport. Relying on a backup system, the Ukrainians were able to resuscitate their network. But on election night the attacks persisted. Hackers sent Russian journalists a link to a chart they had implanted on the official website of Ukraine's Central Election Commission. The graphic purported to show that a right-wing nationalist had sprinted to the lead in the presidential race. Although the public couldn't access the chart, Russian state television flashed the forged results on its highly watched newscast. If the attack on Ukraine represented something like all-out digital war, Russia's hacking of the United States' electoral system two years later was more like a burglar going house to house jangling doorknobs. The Russians had the capacity to cause far greater damage than they did—at the very least to render Election Day a chaotic mess—but didn't act on it, because they deemed such an operation either unnecessary or not worth the cost. The U.S. intelligence community has admitted that it's not entirely sure why Russia sat on its hands. One theory holds that Barack Obama forced Russian restraint when he pulled Vladimir Putin aside at the end of the G20 Summit in Hangzhou, China, on September 5, 2016. With only interpreters present, Obama delivered a carefully worded admonition not to mess with the integrity of the election. By design, he didn't elaborate any specific consequence for ignoring his warning. Perhaps the warning was heeded. The GRU kept on probing voting systems through the month of October, however, and there are other, more ominous explanations for Russia's apparent restraint. Michael Daniel, who served as the cybersecurity coordinator on Obama's National Security Council, told the Senate Intelligence Committee that the Russians were, in essence, casing the joint. They were gathering intelligence about the digital networks that undergird American elections and putting together a map so that they "could come back later and actually execute an operation." What sort of operation could Russia execute in 2020? Unlike Ukraine, the United States doesn't have a central node that, if struck, could disable democracy at its core. Instead, the United States has an array of smaller but still alluring targets: the vendors, niche companies, that sell voting equipment to states and localities; the employees of those governments, each with passwords that can be stolen; voting machines that connect to the internet to transmit election results. Matt Masterson is a senior adviser at the Department of Homeland Security's freshly minted Cybersecurity and Infrastructure Security Agency, a bureau assigned to help states protect elections from outside attack; it's where Jack Cable will work this summer. I asked Masterson to describe the scenarios that keep him up at night. His greatest fear is that an election official might inadvertently enable a piece of ransomware. These are malicious bits of code that encrypt data and files, essentially placing a lock on a system; money is then demanded in exchange for the key. In 2017, Ukraine was targeted again, this time with a similar piece of malware called NotPetya. But instead of extorting Ukraine, Russia sought to cripple it. NotPetya wiped 10 percent of the nation's computers; it disabled ATMs, telephone networks, and banks. (The United States is well aware of NotPetya's potency, because it relied on a tool created by—and stolen from—the National Security Agency.) If the Russians attached such a bug to a voter-registration database, they could render an entire election logistically unfeasible; tracking who had voted and where they'd voted would be impossible. But Russia need not risk such a devastating attack. It can simply meddle with voter-registration databases, which are filled with vulnerabilities similar to the ones that Cable exposed. Such meddling could stop short of purging voters from the rolls and still cause significant disruptions: Hackers could flip the digits in addresses, so that voters' photo IDs no longer match the official records. When people arrived at the polls, they would likely still be able to vote, but might be forced to cast provisional ballots. The confusion and additional paperwork would generate long lines and stoke suspicion about the underlying integrity of the election. Given the fragility of American democracy, even the tiniest interference, or hint of interference, could undermine faith in the tally of the vote. On Election Night, the Russians could place a page on the Wisconsin Elections Commission website that falsely showed Trump with a sizable lead. Government officials would be forced to declare it a hoax. Imagine how Twitter demagogues, the president among them, would exploit the ensuing confusion. Such scenarios ought to have sparked a clamor for systemic reform. But in the past, when the federal government has pointed out these vulnerabilities—and attempted to protect against them—the states have chafed and moaned. In August 2016, President Obama's homeland-security secretary, Jeh Johnson, held a conference call with state election officials and informed them of the need to safeguard their infrastructure. Instead of accepting his offer of help, they told him, "This is our responsibility and there should not be a federal takeover of the election system." After the 2016 election, the federal government could have taken a stronger hand with localities. Unprecedented acts of foreign interference presumably would have provided quite a bit of leverage. That did not happen. The president perceives any suggestion of Russian interference as the diminution of his own legitimacy. This has contributed to a conspiracy of silence about the events of 2016. A year after the election, the Department of Homeland Security told 21 states that Russia had attempted to hack their electoral systems. Two years later, a Senate report publicly disclosed that Russia had, in fact, targeted all 50 states. When then–DHS Secretary Kirstjen Nielsen tried to raise the subject of electoral security with the president, acting White House Chief of Staff Mick Mulvaney reportedly told her to steer clear of it. According to The New York Times, Mulvaney said it "wasn't a great subject and should be kept below his level." From the April 2019 issue: William J. Burns on how the U.S.-Russian relationship went bad This atmosphere stifled what could have been a genuinely bipartisan accomplishment. The subject of voting divides Republicans and Democrats. Especially since the Bush v. Gore decision in 2000, the parties have stitched voting into their master narratives. Democrats accuse Republicans of suppressing the vote; Republicans accuse Democrats of flooding the polls with corpses and other cheating schemes. Despite this rancor, both sides seemed to agree that Russian hacking of voting systems was not a good thing. After the 2016 election, Democratic Senator Amy Klobuchar, from Minnesota, partnered with Republican Senator James Lankford, from Oklahoma, on the Secure Elections Act. The bill would have given the states money to replace electronic voting machines with ones that leave a paper trail and would have required states to audit election results to confirm their accuracy. The reforms would also have had the seemingly salutary effect of making it easier for voters to cast ballots. The Secure Elections Act wouldn't have provided perfect insulation from Russian attacks, but it would have been a meaningful improvement on the status quo, and it briefly looked as if it could pass. Then, on the eve of a session to mark up the legislation—a moment for lawmakers to add their final touches—Senate Republicans suddenly withdrew their support, effectively killing the bill. Afterward, Democrats mocked Senate Majority Leader Mitch McConnell as "Moscow Mitch," an appellation that stung enough that the senator ultimately agreed to legislation that supplied the states with hundreds of millions of dollars to buy new voting systems—but without any security demands placed on the states or any meaningful reforms to a broken system. McConnell made it clear that he despised the whole idea of a legislative fix to the electoral-security problem: "I'm not going to let Democrats and their water carriers in the media use Russia's attack on our democracy as a Trojan horse for partisan wish-list items that would not actually make our elections any safer." For McConnell, suppressing votes was a higher priority than protecting them from a foreign adversary. 2. The Big PhishTo raise the subject of John Podesta's email in his presence is a callous act. But I wanted his help tabulating a more precise toll of Russian hacking—how it leaves a messy trail of hurt feelings, saps precious mental space, and reshapes the course of a campaign. After repeatedly prodding him for an interview, I finally met with Hillary Clinton's old campaign chief in his Washington office, which stares down onto the steeple of the church Abraham Lincoln attended during the Civil War. Dressed in a plaid shirt, with a ballpoint pen clipped into the pocket, Podesta rocked back and forth in a swivel chair as he allowed me to question him about one of the most wince-inducing moments in recent political history. Months before WikiLeaks began publishing his emails, Podesta had an inkling that his Gmail account had been compromised. Internal campaign documents had appeared on an obscure website, and he considered the possibility that they had been lifted from his computer. Still, the call from a member of the campaign's communications team on October 7, 2016, left him gobsmacked. As he finished a session of debate preparation with Clinton, he learned that Julian Assange intended to unfurl the contents of his inbox over the remaining month of the campaign. It's a familiar if much-ignored maxim in politics that no email should ever contain content one wouldn't want to see on the front page of The New York Times. This was now Podesta's reality. On the 10th floor of the Clinton campaign's headquarters, in Brooklyn, a team of 14 staffers quickly assembled. They covered a glass door in opaque paper to prevent voyeurs from observing their work and began to pore over every word of his 60,000 emails—every forwarded PDF, every gripe from an employee, even the meticulous steps of his risotto recipe. The project would consume the entirety of the month. Every day, Podesta set aside time to meet with emissaries from the 10th floor and review their findings. "I willed myself not to feel pain," he told me.  The material that WikiLeaks eventually posted created some awkward moments. Podesta had received snarky emails from colleagues, and had sent a few himself. To repair relationships, Podesta found himself apologizing to co-workers, friends, former Cabinet secretaries. Even when the contents of the leaked messages seemed innocuous, new annoyances would arise. WikiLeaks hadn't redacted the correspondence to protect privacy, leaving the cellphone numbers of campaign staffers for the world to view. In the middle of meetings, staffers would find their devices vibrating incessantly; strangers would fill their voicemails with messages like I hope you're raped in prison. Identity thieves quickly circled Podesta, attempting to claim his Social Security benefits and applying for credit cards in his name. Despite a political career that has permitted him to whisper into the ears of presidents, the legendarily frugal Podesta had commuted to New York on Vamoose, a discount bus line. A fraudster exploited the hack to steal the points he had accumulated in the Vamoose rewards program. As Podesta revisited these painful moments, he claimed that he'd stoically persisted in their face: "I kept going on television. I kept raising money. I kept traveling with Hillary and President Clinton. I kept doing everything that I had been doing." But these were the closing weeks of an election that would turn on fewer than 80,000 votes spread across three states. For a campaign that arguably didn't invest its resources properly in the final stretch, the question must be asked: How badly did the Russians throw the campaign off its game? The least visible damage of the hack might have been the most decisive. Read: How Trump plans to weaponize COVID-19 against Biden In the years since the Podesta hack, Microsoft's Tom Burt has continually battled its perpetrators. As the man charged with safeguarding the security of Windows, Word, and his company's other software, he has developed a feel for the GRU's rhythms and habits. Through Microsoft's work with political parties and campaigns around the world—the company offers them training and sells them security software at a discount—Burt has accumulated lengthy dossiers on past actions. What he's noticed is that attacks tend to begin on the furthest fringes of a campaign. A standard GRU operation starts with think-tank fellows, academics, and political consultants. These people and institutions typically have weak cybersecurity fortifications, the penetration of which serves dual purposes. As the GRU pores through the inboxes of wonks and professors, it gathers useful intelligence about a campaign. But the hacked accounts also provide platforms for a more direct assault. Once inside, the GRU will send messages from the hacked accounts. The emails come from a trusted source, and carry a plausible message. According to Burt, "It will say something like 'Saw this great article on the West Bank that you should review,' and it's got a link to a PDF. You click on it, and now your campaign network is infected." (Although Burt won't discuss specific institutions, he wrote a blog post last year describing attacks on the German Marshall Fund and the European offices of the Aspen Institute.) Podesta fell victim to a generic spear-phishing attack: a spoofed security warning urging him to change his Gmail password. Many of us might like to think we're sophisticated enough to avoid such a trap, but the Russians have grown adept at tailoring bespoke messages that could ensnare even the most vigilant target. Emails arrive from a phony address that looks as if it belongs to a friend or colleague, but has one letter omitted. One investigator told me that he's noticed that Russians use details gleaned from Facebook to script tantalizing messages. If a campaign consultant has told his circle of friends about an upcoming bass-fishing trip, the GRU will package its malware in an email offering discounts on bass-fishing gear. From the March 2017 issue: How to build an autocracy Many of these techniques are borrowed from Russian cybercrime syndicates, which hack their way into banks and traffic in stolen credit cards. Burt has seen these illicit organizations using technologies that he believes will soon be imported to politics. For instance, new synthetic-audio software allows hackers to mimic a voice with convincing verisimilitude. Burt told me, "In the cybercrime world, you're starting to see audio phishes, where somebody gets a voicemail message from their boss, for example, saying, 'Hey, I need you to transfer this money to the following account right away.' It sounds just like your boss and so you do it." What the Russians can't obtain from afar, they will attempt to pilfer with agents on the ground. The same GRU unit that hacked Podesta has allegedly sent operatives to Rio de Janeiro, Kuala Lumpur, and The Hague to practice what is known as "close-access hacking." Once on the ground, they use off-the-shelf electronic equipment to pry open the Wi-Fi network of whomever they're spying on. The Russians, in other words, take risks few other nations would dare. They are willing to go to such lengths because they've reaped such rich rewards from hacking. Of all the Russian tactics deployed in 2016, the hacking and leaking of documents did the most immediate and palpable damage—distracting attention from the Access Hollywood tape, and fueling theories that the Democratic Party had rigged its process to squash Bernie Sanders's campaign. In 2020, the damage could be greater still. Podesta told me that when he realized his email had been breached, he feared that the hackers would manufacture embarrassing or even incriminating emails and then publish them alongside the real ones. It's impossible to know their reasoning, but Russian hackers made what would prove to be a clever decision not to alter Podesta's email. Many media outlets accepted whatever emails WikiLeaks published without pausing to verify every detail, and they weren't punished for their haste. The Podesta leaks thus established a precedent, an expectation that hacked material is authentic—perhaps the most authentic version of reality available, an opportunity to see past a campaign's messaging and spin and read its innermost thoughts. In fact, the Russians have no scruples about altering documents. In 2017, hackers with links to the GRU breached the inboxes of French President Emmanuel Macron's campaign staffers. The contents were rather banal, filled with restaurant reservations and trivial memos. Two days before these were released, other documents surfaced on internet message boards. Unlike the emails, these were pure fabrications, which purported to show that Macron had used a tax haven in the Cayman Islands. The timing of their release, however, gave them credibility. It was natural to assume that they had been harvested from the email hack, too. The Macron leaks suggested a dangerous new technique, a sinister mixing of the hacked and the fabricated intended to exploit the electorate's hunger for raw evidence and faith in purloined documents. 3. Disinformation 2.0In the spring of 2015, trolls in St. Petersburg peered at the feed of a webcam that had been furtively placed in New York City. Sitting in front of a computer screen on the second floor of a squat concrete office building, the trolls waited to see if they could influence the behavior of Americans from the comfort of Russian soil. The men worked for a company bankrolled by Yevgeny Prigozhin, a bald-headed hot-dog vendor turned restaurateur, known to the Russian press as "Putin's chef." In the kleptocratic system that is the Russian economy, men like Prigozhin profit from their connections to Putin and maintain their inner-circle status by performing missions on his behalf. The operation in St. Petersburg was run by the Internet Research Agency, a troll farm serving the interests of the Kremlin. (Prigozhin has denied any involvement with the IRA.) The IRA is an heir to a proud Russian tradition. In the Soviet Union's earliest days, the state came to believe that it could tip the world toward revolution through psychological warfare and deception, exploiting the divisions and weaknesses of bourgeois society. When it was assigned this task, the KGB referred to its program by the bureaucratic yet ominous name Active Measures. It pursued this work with artistic verve. It forged letters from the Ku Klux Klan that threatened to murder African athletes at the 1984 Summer Olympics in Los Angeles. It fomented conspiracies about the CIA—that the agency had orchestrated the spread of the AIDS virus in a laboratory and plotted the assassination of President John F. Kennedy. Some of these KGB schemes were harebrained. But as one defector to the West put it, more Americans believed the Soviet version of JFK's murder than the Warren Report. The IRA has updated the principles of Active Measures for the digital age. On social media, disinformation can flourish like never before. Whereas the KGB once needed to find journalistic vehicles to plant their stories—usually the small-audience fringes of the radical press—Facebook and Twitter hardly distinguished between mainstream outlets and clickbait upstarts. And many of the new platforms were designed to manipulate users, to keep them engaged for as long as possible. Their algorithms elevated content that fueled panic and anger. Read: What Facebook did to American democracy With the New York webcam, the IRA was testing a hunch: that, through the miracle of social media, it could now toy with Americans as if they were marionettes. As the political scientist Thomas Rid recounts in his powerful new history, Active Measures, a post on Facebook promised that free hot dogs would be available to anyone who arrived on a specific corner at a prescribed time. Back in St. Petersburg, IRA employees watched as New Yorkers arrived, looked at their phones in frustration, and skulked away. The ruse was innocuous, but it proved a theory that could be put to far more nefarious ends: Social media had made it possible, at shockingly low cost, for Russians to steer the emotions and even movements of Americans. No study has quantified how many votes have been swayed by the 10 million tweets that the IRA has pumped into the digital world; no metric captures how its posts on Facebook and Instagram altered America's emotional valence as it headed to the polls in 2016. In the end, the IRA's menagerie of false personas and fusillades of splenetic memes were arguably more effective at garnering sensationalistic headlines than shifting public opinion. For their part, the IRA's minions immodestly credited themselves with having tilted the trajectory of history. The U.S. government obtained an email from an IRA employee describing the scene at the St. Petersburg office on Election Night: "When around 8 a.m. the most important result of our work arrived, we uncorked a tiny bottle of champagne … took one gulp each and looked into each other's eyes … We uttered almost in unison: 'We made America great.' " Having run a noisy operation in 2016, the IRA has since learned to modulate itself. Its previous handiwork, much of which was riddled with poor syntax and grammatical errors, hardly required a discerning eye to identify. These days, the IRA takes care to avoid such sloppiness. Now, when they want to, IRA trolls can make themselves inconspicuous. Relying on this quieter approach, the IRA has carried the theory of its hot-dog experiment into American political life. When white supremacists applied for a permit to hold a march in 2018 to commemorate the first anniversary of their protests in Charlottesville, Virginia, a Facebook group organized a counterprotest in Washington, D.C. The group was called the Resisters. Its administrators, who went by the names Mary and Natasha, recruited a coterie of enthusiastic organizers to promote the rally. When Facebook took down the Resisters' page—noting its ties to IRA accounts, and implying that Mary and Natasha were fictitious creations—American leftists were shocked to learn that they had apparently been hatching plans with foreign trolls. According to The New York Times, they were also furious with Facebook: Whether or not the page was a Russian ploy, it had become a venue for real Americans to air their real grievances. In fact, it was hard to pinpoint where the Active Measures ended and the genuine action began—the sort of tradecraft that the KGB would have admired. From the December 2019 issue: The dark psychology of social networks Although the IRA might practice stealth when the operation demands, in other circumstances it will deploy raw bluster. Starting in 2017, it launched a sustained effort to exaggerate the specter of its interference, a tactic that social-media companies call "perception hacking." Its trolls were instructed to post about the Mueller report and fan the flames of public anger over the blatant interference it revealed. On the day of the 2018 midterm elections, a group claiming to be the IRA published a grandiloquent manifesto on its website that declared: "Soon after November 6, you will realize that your vote means nothing. We decide who you vote for and what candidates will win or lose. Whether you vote or not, there is no difference as we control the voting and counting systems. Remember, your vote has zero value. We are choosing for you." The claim was absurd, but the posturing had a purpose. If enough Americans come to believe that Russia can do whatever it wants to our democratic processes without consequence, that, too, increases cynicism about American democracy, and thereby serves Russian ends. As Laura Rosenberger, a former National Security Council staffer under Obama who runs the Alliance for Securing Democracy, put it, "They would like us to see a Russian under every bed." Judging by this year's presidential-primary campaign, they have been successful in this effort. When the Iowa Democratic Party struggled to implement new technology used to tally results for the state's caucus, television panelists, Twitter pundits, and even a member of Congress speculated about the possibility of hacking, despite a lack of evidence to justify such loose talk. American incompetence had been confused for a plot against America. 4. An Uncoordinated ResponseAs the outlines of the IRA's efforts began to emerge in the months following the 2016 election, Facebook at first refused to acknowledge the problem. The company's defensiveness called attention to its laissez-faire attitude toward the content that it elevated in people's News Feeds. Facebook found itself flayed by congressional committees, its inner workings exposed by investigative journalists. Ostensibly it had been Alex Stamos's job to prevent the last attack, and now he faced another wave of disinformation, with midterm elections fast approaching. Stamos worried that, in the absence of an orchestrated defense, his company, as well as the nation, would repeat the mistakes of 2016. In the spring of 2018, he invited executives from the big tech companies and leaders of intelligence agencies to Facebook's headquarters in Menlo Park, California. As he thought about it, Stamos was surprised that such a summit hadn't been organized sooner. What shocked him more was a realization he had as the meeting convened: Few of these people even knew one another. "People who ran different agencies working on foreign interference met for the first time at Menlo Park, even though they were 10 Metro stops away in D.C.," he told me. "The normal collaborative process in government didn't exist on this issue." Stamos's summit succeeded in spurring cooperation. Prior to the meeting, one tech company would identify and disable Russian accounts but fail to warn its competitors, allowing the same trolls to continue operating with impunity. Over the course of 2018, the tech industry gradually began acting in concert. The lead investigators on the threat-intelligence teams at 30 companies—including Facebook, Verizon, and Reddit—joined a common channel on Slack, the messaging platform. When one company spies a nascent operation, it can now ring a bell for the others. This winter, Facebook and Twitter jointly shut down dozens of accounts associated with a single residential address in Accra, Ghana, where the Russians had set up a troll factory and hired local 20-somethings to impersonate African Americans and stoke online anger. From the May 2019 issue: Trump's second term Yet this remains a game of cat and mouse in which the mice enjoy certain advantages. Despite the engineering prowess of the social-media companies, they haven't yet built algorithms capable of reliably identifying coordinated campaigns run by phony Russian accounts. In most instances, their algorithms will suggest the inauthenticity of certain accounts. Those data points become a lead, which is then passed along to human investigators. Facebook has several dozen employees on its threat-intelligence team, many of them alumni of the three-letter agencies in Washington. Still, the tech companies rely heavily on law enforcement for tips. Facebook and Twitter have frequent check-ins with the FBI. Without the bureau, Facebook might have missed an IRA video filled with lies about Russian tampering in the midterm elections. After a heads-up from the government, Facebook blocked the IRA from uploading the video before it ever appeared on its site, using the same technique that it deploys to suppress Islamic State snuff videos and child pornography. Rising from their denialist crouch, the social-media companies have proved themselves capable of aggressive policing; after treating the IRA as a harmless interloper, they came to treat it with the sort of disdain they otherwise reserve for terrorists and deviants. Devising strategies for thwarting the last attack is far easier than preventing the next one. Even if Russian disinformation can be tamped down on social media—and the efforts here, on balance, are encouraging—there are other ways, arguably more consequential, to manipulate American politics, and scant defense against them. On an early-March afternoon, I typed the Federal Election Commission as a destination into Uber and was disgorged at a building the agency hasn't occupied for two years. The antiquated address placed me on course to arrive half an hour late for an appointment with Ellen Weintraub, the longest-serving and most vociferous member of the commission nominally assigned to block the flow of foreign money into political campaigns. When I called her office to inform her of my tardiness, her assistant told me not to worry: Weintraub's schedule was wide open that afternoon. In fact, for the past six months the FEC hadn't conducted much official business. Only three Senate-approved commissioners were installed in their jobs, even though the agency should have six and needs four for a quorum. Weintraub, a Democrat, has an impish streak. Near the beginning of the FEC's hibernation, she called out a fellow commissioner who had blocked the publication of a memo that seemed to criticize the Trump campaign for its 2016 meeting with a Russian lawyer—then posted the memo in a 57-part thread on Twitter. Weintraub has grown accustomed to her colleagues ignoring her questions about the presence of Russian and other illicit money in American campaigns. When the commission received a complaint suggesting that the FBI was investigating the National Rifle Association as a conduit for Russian money, she asked her fellow commissioners for permission to call the FBI, to, as she put it, "see if they have interesting information they want to share. But they said, 'We're not going to call the FBI.' They didn't want to do anything." Outside Weintraub's office, the subject of Russia's illicit financing of campaigns hardly provokes any attention. The Alliance for Securing Democracy was the only organization I could find that comprehensively tracks the issue. It has collected examples of Russian money flowing into campaigns around the world: a 9.4-million-euro loan made to the French nationalist Marine Le Pen's party; operatives arriving in Madagascar before an election with backpacks full of cash to buy TV ads on behalf of Russia's preferred candidate and to pay journalists to cover his rallies. Or take a case closer to home: Lev Parnas and Igor Fruman—the Soviet-born Americans who worked with Rudy Giuliani in his search for politically damaging material to deploy against former Vice President Joe Biden—were charged with conspiring to funnel money from an unnamed Russian into American campaigns. Some of the cases cited by the Alliance for Securing Democracy are circumstantial, but they form a pattern. Since 2016, the group has identified at least 60 instances of Russia financing political campaigns beyond its borders. (The Kremlin denies meddling in foreign elections.) From the May 2018 issue: The era of fake video begins When I asked Weintraub if she had a sense of how many such examples exist in American politics, she replied, "We know there's stuff going on out there, and we're just not doing anything." Since the Supreme Court's 2010 Citizens United decision, which lifted restrictions on campaign finance, hardly any systemic checks preclude foreigners from subsidizing politicians using the cover of anonymous shell companies. With that decision, the high court opened the door for Russia to pursue one of its favored methods of destabilizing global democracy. By covertly financing campaigns, the Russians have helped elevate extremist politicians and nurture corrosive social movements. "Everyone knows there are loopholes in our campaign-finance system," Weintraub said. "Why would we think that our adversaries, who have demonstrated a desire to muck around in our democracy, wouldn't be using those loopholes, too?" Problems of inattention, problems of coordination, and deep concerns about November—these themes came up over and over in my interviews for this story. Indeed, at times everyone seemed to be sounding the same alarm. H. R. McMaster, who briefly served as Donald Trump's national security adviser, sounded it when he proposed a new task force to focus the government's often shambolic efforts to safeguard the election. Adam Schiff, the chairman of the House Intelligence Committee, sounded it when he realized how poorly the bureaucracy was sharing the information it was gathering about the Russian threat. There was a moment that crystallized Schiff's sense of this disjointedness. In the summer of 2018, he attended a security conference in Aspen, Colorado, where Tom Burt revealed that Microsoft had detected Russian phishing attacks targeting Democratic senatorial candidates. "When I went back to Washington," Schiff told me, "I asked agency heads within the [intelligence community] whether they were aware of this. The answer was no." That the chairman of the House Intelligence Committee had to learn this elemental fact about his own branch of government at a public gathering is troubling; that the people charged with protecting the country didn't know it is flabbergasting. The sprawling federal bureaucracy has never been particularly adept at the kind of coordination necessary to anticipate a wily adversary's next move. But there is another reason for the government's alarmingly inadequate response: a president who sees attempts to counter the Russia threat as a personal affront. After McMaster was fired, having made little if any progress on Russia, the director of national intelligence, Dan Coats, took up the cause, installing in his office an election-security adviser named Shelby Pierson. This past February, Pierson briefed Schiff's committee that the Russians were planning to interfere in the upcoming election, and that Trump remained Moscow's preferred candidate. Anyone who follows the president on Twitter knows this is a subject that provokes his fury. Indeed, the day after Pierson's testimony, the president upbraided Coats's successor, Joseph Maguire, for Pierson's assessment. A week later, he fired Maguire and installed in his place the ambassador to Germany, Richard Grenell, a loyalist with no intelligence experience. Grenell immediately set about confirming the wisdom behind Trump's choice. Three weeks into his tenure, a senior intelligence official in the Office of the DNI informed the Senate that Pierson's assessment was mistaken. Trump had graphically illustrated his recurring message to the intelligence community: He doesn't want to hear warnings about Russian interference. Mark Warner, the highest-ranking Democrat on the Senate Intelligence Committee, told me, "A day doesn't go by that I don't hear from someone in the intelligence community saying, 'Oh my gosh, we're worried about integrity, we're worried about morale, we're worried about willingness to speak truth to power.' " I asked Warner whether he could still trust the intelligence about Russia he received—whether he has faith that the government will render an accurate portrait of the Russian threat to the upcoming presidential election. As he considered his answer, he leaned toward me. "I don't know the answer to that," he replied, "and that bothers me." From the October 2017 issue: Will Donald Trump destroy the presidency? Vladimir Putin dreams of discrediting the American democratic system, and he will never have a more reliable ally than Donald Trump. A democracy can't defend itself if it can't honestly describe the attacks against it. But the president hasn't just undermined his own country's defenses—he has actively abetted the adversary's efforts. If Russia wants to tarnish the political process as hopelessly rigged, it has a bombastic amplifier standing behind the seal of the presidency, a man who reflexively depicts his opponents as frauds and any system that produces an outcome he doesn't like as fixed. If Russia wants to spread disinformation, the president continually softens an audience for it, by instructing the public to disregard authoritative journalism as the prevarications of a traitorous elite and by spouting falsehoods on Twitter. In 2020, Russia might not need to push the U.S. for it to suffer a terrible election-year tumble. Even without interventions from abroad, it is shockingly easy to imagine how a pandemic might provide a pretext for indefinitely delaying an election or how this president, narrowly dispatched at the polls, might refuse to accept defeat. But restraint wouldn't honor Russia's tradition of Active Measures. And there may never be a moment quite so ripe for taking the old hashtag out of storage and giving it a triumphalist turn. #DemocracyRIP. This article appears in the June 2020 print edition with the headline "The 2016 Election Was Just a Dry Run." Related Video |
| You are subscribed to email updates from "encrypted sms app,honor 8 encryption,file encryption app" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |

Comments
Post a Comment