The Top IoT Vulnerabilities in Your Devices - Keyfactor - Security Boulevard
The Top IoT Vulnerabilities in Your Devices - Keyfactor - Security Boulevard |
- The Top IoT Vulnerabilities in Your Devices - Keyfactor - Security Boulevard
- COVID-19: Multiplying Modes of Communication During Quarantine: Questions You Did Not Know You Should Be Asking - Lexology
- Ransomware Activity Alert For the Healthcare Sector - by Adam Silverman - The Ark Valley Voice
- Deciphering the data protection mandates in the Indian securities market - ETCIO.com
| The Top IoT Vulnerabilities in Your Devices - Keyfactor - Security Boulevard Posted: 28 Oct 2020 06:40 PM PDT
IoT vulnerabilities provide cybercriminals with a baseline to bypass firewalls, gain access to private networks, and steal sensitive information as it travels across connected device environments. The risk involved with these compromised devices also allows cyber-attacks to spread to other networked systems. Manufacturing Insecure IoT Devices? Try Keyfactor Control. OWASP Top 10 IoT outlines ten vulnerabilities that have caused the most impact and damage in the design, implementation, and handling of IoT systems over the last few years. This blog further examines each vulnerability's details, how to protect your company, your employees, and your customers from the potential threats and risks involved. Table of contents Lack of a Secure Update Mechanism"Lack of ability to securely update the device. This includes lack of firmware validation on device, lack of secure delivery (un-encrypted in transit), lack of anti-rollback mechanisms, and lack of notifications of security changes due to updates." It is necessary to consider how these updates will take place and how to make them more secure. For example, when designing a device like a smartwatch or a sensor, you'll need to consider building in an update mechanism for timely updates. Companies often struggle to keep their IoT systems up-to-date because many device manufacturers rarely provide updated security patches. Some devices may have reached the end of life date, while others never offered the ability to update in the first place. The ability of the device to receive Over-the-Air (OTA) updates is critical to addressing this vulnerability. OTA updates allow you to update your latest hardware, software, and firmware security patches over a wireless network, including 2G, 3G, 4G, 5G, Wi-FI, and CDMA connections. Regular updates minimize the number of attack vectors in operating systems, firmware, and applications. If updates are available, some devices may not notify the user that an update is available. Conversely, while other devices might install updates automatically, it may require a hardware reboot before the update takes effect. This reboot leaves systems vulnerable and unavailable while applying the update. It is essential to check each update's origin and integrity and only use legitimate vendors' legitimate applications. Some available update mechanisms lack integrity guarantees, making them vulnerable to MITM attacks and modification attacks. The IoT device can also use machine-to-machine authentication methods to authenticate an upgrade server before downloading a new firmware image, adding a layer of protection. This ensures device updates come from only the device OEM or another trusted source. Implementing X.509 digital certificates with OTA updates ensures an unchanged update from the verified source. By using the secure boot, the cryptographically secure hash validation ensures integrity by checking the patch before storing it on the device. Lack of Device Management"Lack of security support on devices deployed in production, including asset management, update management, secure decommissioning, systems monitoring, and response capabilities." One of IoT's most significant safety risks and challenges is managing all of our devices and closing the perimeter. However, rogue devices or counterfeit malicious IoT devices are installed in secure networks without authorization. A rogue device replaces or integrates the original device as a group member to collect or alter sensitive information. These devices are breaking the perimeter of the network. Device management is like other IT asset management systems: the primary concerns are the provisioning, operation, and updating of devices. These concerns apply to all devices, including gateways. The discovery and identification of IoT devices is a necessary first step in the monitoring and protection of these devices. Large IoT networks, comprising many almost identical devices, are attractive targets for cyber attackers. However, it is costly and slow to recover from compromises by conventional means, primarily if they distribute the devices over a large geographical area where network administrators or operators would have to travel to the devices to recover them manually. An outdated, static inventory of IoT assets controls the box but is far from efficient security management. Identification of devices using traditional features of IT devices, such as IP addresses and underlying operating systems, does not work for IoT. Only by identifying a specific device can an organization accurately plan its network access requirements, deployment tactics, security strategy optimization, and operational plans. Once device identities are determined, security systems can track device behavior in an organization's workflow context rather than view it as dynamic IP addresses of an unknown device type. IoT security solutions enable organizations to discover and identify IoT devices on their networks. Despite the significant growth in the number of IoT assets, most organizations are unaware of device vulnerabilities and do not manage their safety postures or risk profiles. Intelligent device scanning and profiling allow IT security teams to have visibility of their networked IoT devices, their risk profiles, and their network behavior when interacting with other devices on the network. Today's most advanced IoT security solutions use machine learning to identify IoT devices that have never been seen before and to recognize malicious network communication patterns before they cause damage. Insecure Data Transfer and Storage"Lack of encryption or access control of sensitive data anywhere within the ecosystem, including at rest, in transit, or during processing." The network and communication layers play a central role in all IoT applications and implementations, facilitating sharing information between different layers and generating value through real-time interaction between IoT devices. One of IoT applications' key features is transferring information between IoT devices, networks, networks and networks, and high-level information processing infrastructures (e.g., clouds, data centers, etc.). However, the potential for compromising data collected by a smart device moving across the network, or storing in a new location, is increasing. For example, MITM attacks exploit poor key exchange practices and allow a malicious device to intercept all information passed through the ecosystem. Most IT teams design their network dynamically on-board IT devices using network access control protocol but do not extend this capability to IoT assets. As cloud-based communications and data storage continues to grow, more data is flowing to cloud and IoT computers. Customers expect their data to be secure during transit. Today, IoT data transfer and storage best practices call for secure public-key cryptography via the DTLS protocol for encrypted IoT device communication across public networks. Public Key Cryptography is a robust encryption method that relies on private and public encryption keys rather than hard-coded secrets. Several IoT security solutions offer integration with DTLS, PKI, and next-generation hardware security to manage device identities, permissions, and risk profiles. Data-in-motion communication security is achieved by a chain of trust model used in the typical PKI. PKI certificates have the most common encryption and authentication and are most commonly used in the HTTPS Internet Protocol. The certificate authority that certifies the complete validation of the certified party's identity shall issue each digital certificate. Data tokenization can protect sensitive encrypted data that only authorized devices can decode. Weak, Guessable, or Default Passwords"Use of easily brute-forced, publicly available, or unchangeable credentials, including backdoors in firmware or client software that grants unauthorized access to deployed systems." A common and pervasive vulnerability in IoT systems today stems from weak or unchanged default passwords. Poor management of device credentials places IoT devices at greater risk of becoming targets of a brute force attack. Inconsistent management practices allow for password-oriented attacks. For example, your employees' passwords might not align with your IT's more advanced password management policies. In 2018, California's SB-327 IoT law passed to prohibit the use of default certificates. This law finally aims to solve the use of weak password vulnerabilities. Until IoT manufacturers fully realize the need for these changes, IoT's security equipment rests with users, IoT service providers, and IT services. The immediate step to securing these systems is for IT administrators to set up new login policies that require users and administrators to change default device passwords. This policy means adding layers of special and complex character combinations before redeploying them to live environments. Insecure Network Services"Unnecessary or unsafe network services that run on the devices, particularly those that are exposed to the internet, jeopardize the availability of confidentiality, integrity / authenticity of information, and open the risk of unauthorized remote control of IoT devices." IoT devices are integrated into the network infrastructure and can transmit, retrieve, and interpret data from linked smart devices, such as smoke alarms, proximity sensors, or optical devices. The system's communication mechanisms will vary but may include network protocols ranging from BLE and ZigBee to WiFi, cellular data, and Ethernet. The ability for smart technologies to make choices without human interference makes them unique. This level of device autonomy creates challenges to ensure consumer-grade mobility and interoperability without compromising the safety of IoT devices. To function correctly, any Internet-connected service requires opening specific ports. Leaving open ports and services that provide access to devices or other machines is a typical security error. A joint study between BitSight and Advisen showed that 60 percent of the breached organizations had ten or more vulnerable, open ports. Exploited service vulnerabilities in IoT devices may allow for stealthy malware services such as viruses, spyware, ransomware, and Trojans. Cybercriminals may use these open-port services to access sensitive data, listen to private communications, or execute Denial-of-Service (DoS) and Man-in-the-Middle (MITM) attacks. However, there is a lack of automated security options available to address this network layer vulnerability despite serious security threats. With over 65,000 TCP ports and a corresponding number of UDP ports, there is no simple way to open and close ports. Port maintenance requires an administrator who knows which ports should remain open to connect essential services to the network. If the port is open and not connected to any crucial network services, the port should be closed immediately. A small network with relatively few IP addresses should not take a long time to close vulnerable ports. However, monitoring and managing open ports can be time-consuming on enterprise networks with a constant adding new devices. System administrators must scan and close unneeded open ports and services which exchange information on their networks. Insecure Ecosystem Interfaces"Insecure web, backend API, cloud, or mobile interfaces in the ecosystem outside of the device that allows compromise of the device or its related components. Common issues include a lack of authentication/authorization, lacking or weak encryption, and a lack of input and output filtering." Many companies often overlook IoT system security policies and procedures when connecting to backend APIs. It is crucial to understand all the devices and sensors in the ecosystem and all the devices that interface. IoT systems transmit and receive large amounts of information and secure the data transfer between devices/sensors, gateway devices, and back-end databases through REST-based APIs. Although APIs provide powerful extensibility, these same APIs provide a new entrance for an attacker to connect and access data to your IoT devices. Hackers can breach a router or device's web interface if not correctly secured. Authentication, encryption, and Public Key Infrastructure (PKI) help ensure APIs communicate only with other pre-validated devices and applications. Another common problem is routers connected to remote web interfaces, a feature known as remote management or remote management. Administrators can test a router's availability for remote management by checking the open ports 80 (HTTP) and 443 (HTTPS). This allows them to deactivate this feature safely. The network that connects IoT devices to back-end systems must also be secure. Network security is more challenging with IoT applications because of the wide variety of standards, devices, and communication protocols. IoT network security requires close attention during design and deployment. Developers need to design more secure IoT applications without assuming the devices themselves are protected. Firewalls, anti-virus, and intrusion detection and prevention systems should provide a secure IoT network. IoT devices must authenticate each other to verify the device's identity to which they intend to connect. If the machine carries out identity validation on multiple devices, a central certificate authority may be beneficial. It is also essential for well-trained administrators to regularly update packages and detect and delete outdated services and packages. Use of Insecure or Outdated Components"Use of deprecated or insecure software components/libraries that could allow the device to be compromised. This includes insecure customization of operating system platforms, and the use of third-party software or hardware components from a compromised supply chain." Potential issues may arise from vulnerabilities in software dependencies or legacy systems. A significant vulnerability that affects millions of IoT smart devices is the use of outdated or unsecured software, including third-party components, libraries, and frameworks used by manufacturers to build IoT devices. This software is difficult to track and is vulnerable to cyber-attacks if it is not correctly known or managed. Legacy systems using traditional software update protocols for IoT devices place users' burden to locate and patch security holes. These protocols run on firewall devices without interacting with other systems or devices. As a result, cybersecurity systems see IoT devices as unknown endpoints; therefore, they do not know its specific device type, risk profile, and expected behavior. This differs from traditional network-based cybersecurity systems that have visibility across all network-connected endpoints but can not scale well enough to identify, track, and secure IoT enterprise environments. More robust risk management practices are needed for IoT assets to prevent the execution of these distinct threats. PKI and digital certificates are more critical than ever to secure connections both behind and outside the corporate firewall. Each person, machine, and application must have an identity that can be verified and trusted. As modern cloud-based security infrastructures replace traditional network perimeters, it is crucial to remain aware of any outdated firmware or software on your legacy security systems. Insufficient Privacy Protection"User's personal information stored on the device or in the ecosystem that is used insecurely, improperly, or without permission." When individuals request personal data deletion, the provider must ensure that all third parties delete the data. Unlike websites, many IoT devices do not provide easy access to view privacy policies. They are often included separately from the device manual. Sometimes they are only available after opening and installing the system, or there may be a notice somewhere in the documentation directing the user to visit the manufacturer's website. Because of legitimate concerns about causing damage, such as distracting drivers, IoT devices do not have an excellent way to warn people they are collecting data. Worse, some IoT service providers' privacy policy statements are challenging to identify system capabilities and unclear about data collection. IoT applications are also vulnerable to data leak vulnerabilities. When researchers analyzed 230 SmartThings applications, they found 138 of the applications exposed at least one piece of sensitive data via the Internet or messaging services. The authors also showed that half of the analyzed applications leak at least three different sensitive data sources, such as device information, device status, user input, Internet, or messaging services. Insecure Settings by Default"Devices or systems shipped with insecure default settings or lack the ability to make the system more secure by restricting operators from modifying configurations." Device onboard occurs when a new device is added to the restricted IoT ecosystem. Eavesdropping may take place during the onboard step of a new device where the hacker can intercept secret keys that are used to establish communications within a constrained network. Hackers can start from the deepest layer of the IoT device, the physical motherboard. The hardware debug port or communication port, e.g., JTAG UART, I2C, and SPI, can be found there. From there, they can search for hard-coded passwords, hidden backdoors, and vulnerabilities in their dumped firmware. To set up applications on devices, review the permissions they require and restrict access to these apps. Settings, credential, firmware versions, and recent patches should be noted. This step can help assess which security measures should be taken by users and identify which devices should be replaced or updated. Enabling a firewall router, disabling WPS, enabling the WPA2 security protocol, and using a strong Wi-Fi password are just some of these practices. It is also now possible to encrypt all traffic through your ISP by installing Virtual Private Networking (VPN) on your router. Lack of Physical Hardening"Lack of physical hardening measures, allowing potential attackers to gain sensitive information that can help in a future remote attack or take local control of the device." Because of the ubiquity of IoT computing, devices are usually not kept in a secure location but must be exposed in the field to perform their tasks. In the absence of surveillance, this could easily allow malicious actors to tamper with or access devices. In particular, IoT devices are vulnerable because they lack the necessary built-in security to counter threats. Unlike our phones, laptops, and personal computers, many IoT devices operate unattended, making it easier for criminals to tamper with the devices and go undetected. Security protocols protect data while transmitted across networks but do not protect data while stored on the device. Massive data breaches resulted from data recovered from stolen or discarded equipment. Lack of encryption allows hackers to change each device's file system. Engineers should have any sensitive data stored on the device. A significant hardware vulnerability exists in both consumer and industrial control systems with unrestricted access to the universal asynchronous receiver transmitter (UART), allowing them to change the device boot sequences. By modifying the boot sequences, hackers can gain low-level access to the device and extract log-in information. A single attacker can stop the system's IT and OT elements from interacting with each other. The jamming and tampering of the physical layer could prevent sensors from detecting risks such as fire, flood, and unexpected motion. Ensure that the hardware is safe from tampering, physical access, manipulation, and sabotage. One way to achieve strong IoT hardware security is to store keys in Trusted Platform Modules (TPMs) and Trusted Execution Environments (TEE). TPM is essentially a chip installed on an IoT device near the CPU. It's mainly used for cryptographic operations that create a security key, save it, store data, and other related operations. They can ensure the integrity of the disk encryption and password protection platform. ConclusionMake sure you have a strong understanding of your vulnerability.
You may have the proper security tools to monitor your environment, or you need to look into a better way to secure your IoT devices. Early intrusion detection has always been one of the best ways to avoid the worst security incidents, which remains true in the IoT era. *** This is a Security Bloggers Network syndicated blog from PKI Blog authored by Ellen Boehm. Read the original post at: https://blog.keyfactor.com/top-iot-vulnerabilities |
| Posted: 29 Oct 2020 01:06 AM PDT  For many companies, COVID-19 has upended long-established working environments and forced many to rethink how employees can best communicate and collaborate while working remotely. Communication platforms that may have seemed unfamiliar and futuristic have become essential tools virtually overnight. If employers were not equipped to support their employees' transition to working from home—or when the tools the company supported did not adequately meet staffs' needs—many employees embraced communication platforms more rapidly than their employers, leaving behind their employers' retention and privacy policies. Tension between new technologies and old corporate policies is not new, of course. Last month, for example, the Securities and Exchange Commission (SEC) announced it had settled charges against JonesTrading Institutional Services LLC (JonesTrading), a registered broker-dealer, for violating the record-keeping provisions of Section 17(a) of the Securities Exchange Act of 1934 (Exchange Act) and SEC Rule 17a-4(b)(4).1 JonesTrading maintained standard records and communications retention policies and prohibited employees from conducting business-related communications over text message or on non-firm systems. However, after the SEC requested certain records from JonesTrading, the firm discovered that some responsive communications had not been retained. Why? Because certain JonesTrading employees had used text messages for business purposes and failed to preserve the messages. To compound the problem, certain JonesTrading senior management and compliance personnel knew that employees were sending and receiving business-related text messages—and were even doing so themselves. After being alerted to this issue, JonesTrading took remedial steps, but it was too late. The SEC censured and fined the company. Months into the challenges posed by ongoing quarantines, companies must grapple with the technologies their employees are using to avoid JonesTrading's fate or worse. But no two communication tools are exactly alike, and various platforms have different retention and privacy features that may present varying types and levels of risk for employers, their employees and other stakeholders such as board members. Companies and their counsel should know what risks lurk in the default settings and user controls of common tools, and remain attuned to these differences to avoid loss of data, regulatory risk and legal liability. This alert highlights for companies and their counsel a set of key issues to consider as we all continue to navigate these uncharted waters. (1) How significant are the risks created by employees' use of communication tools not authorized by the company? Employees may seek out communication tools not authorized by their employer in a good faith attempt to address real business needs. Some technologies are free, easy to use, and may be effective ways to communicate with non-US clients. Earlier this year, the Financial Industry Regulatory Authority (FINRA) sanctioned a broker-dealer employee who used WhatsApp Messenger to communicate with overseas customers on his personal phone and company computer.2 Or employees may seek to use a tool that allows for efficient collaboration while working remotely. Many businesses use Google Docs, which permits simultaneous, live editing of and commenting on documents, rather than static Word documents that require employees to wait for one another to exit the file. Although these new tools may confer many benefits in a remote working environment, companies should not underestimate the risks created by their unauthorized and unsupervised use. Unauthorized tools can limit a company's ability to control data retention or adjust privacy settings. While some tools may make retention features available, they also often permit users to control their own privacy settings, so when individual employees independently employ unauthorized tools, they may disable built-in retention functions and fail to preserve those communications and documents. This presents problems for regulated entities, such as JonesTrading, that are legally required to retain certain documents and communications. Even for companies not subject to those same regulations, loss of data and documents can be problematic. Companies may be required to preserve data as a result of a new investigation or a litigation hold. (This is further discussed immediately below and at Section 4, infra.) Loss of documents also reduces institutional memory, since records might not be preserved when an employee leaves the company. And use of unauthorized tools allows employees to create records that may not otherwise have been permitted to be created—for example, recording, even unwittingly, a sensitive internal meeting or presentation that was not intended to be recorded. Unauthorized tools can also create unique problems if the company or an employee becomes involved in litigation or an investigation. If an employee used personal accounts for business activities, that employee's personal data could be subject to collection and review because the business use and personal use have become intertwined. Employees might be hesitant to turn over personal email, cloud, and cellphone accounts, which would be an issue both they and their employer would need to address. In addition, companies often have no knowledge of what documents are stored in unauthorized locations and by unauthorized platforms. The cost of document collection increases when a company must diligently seek documents from a variety of unauthorized platforms and custodians. And companies facing litigation in years to come may fail to collect and produce documents in response to discovery requests or government subpoenas because the documents are not located within the companies' systems. Finally, unauthorized tools can frustrate efforts to prevent or halt employee wrongdoing. With limited ability to monitor communications, companies may be caught off guard as to their employees' illegal or negligent acts, yet still be liable under theories of vicarious liability. For entities with affirmative obligations to review employees' electronic communications, such as broker-dealers, companies may not be able to comply with their regulatory obligations. (2) Will documents be retained and maintained securely? What controls must an employer know about and manage in order to appropriately retain and protect data? Many communications tools, including videoconference, collaboration, and work management platforms, offer customers a range of subscription options that often determine the extent to which a customer can access or control the retention and privacy features built into the platform. Broadly speaking, the level of customization and control increases with the cost of the subscription. a. Enterprise and Business subscriptions. In Enterprise and Business subscriptions, the customer, usually an employer, designates an administrator account to manage retention and privacy features for individual employee use. This provides a greater degree of employer control over and consistency to these settings. As individual users of an Enterprise subscription, employees do not possess the same privileges as an administrator, and so cannot override the administrator's decisions or chosen privacy and retention settings. On Skype for Business or Webex, for example, if an employee wishes to delete all or part of her self-generated content, she usually cannot directly request deletion from the platform and must seek permission from the administrator. b. Individual and Free subscriptions. Fee-based Individual subscriptions as well as Free subscriptions may appeal to companies looking to save money because there is no need to invest in an Enterprise subscription. However, such subscriptions typically lack centralized control over privacy and retention settings, and carry attendant risks that companies should keep in mind. On some platforms, Free subscriptions permit individual users to control the retention and privacy settings of their own user-generated content. On Skype or Slack, for example, a user can often unilaterally determine the scope of content sharing (e.g., sharing only the transcript of a recorded videoconference) or the length of a data retention period (e.g., designating files to be preserved by the platform for a month as opposed to a week). For other platforms, Free subscriptions permit retention and privacy settings to be determined by any users in a room or chat. On WeChat, for example, a specific chat is retained and encrypted according to the highest levels of privacy setting established by any chat participant, trumping other participants' retention and encryption settings for that chat. To illustrate: If three people are in a chat and two participants have settings that save the chat to the cloud but one does not, the chat would not be saved to the cloud. Similarly, if one participant has a setting to encrypt the chat and the other two do not, the chat would be encrypted. c. A note on data encryption and retention. Regardless of subscription type, companies should focus on the encryption settings for their communication tools. Depending on the nature of the encryption, text message collection may not be possible, which would limit or prohibit the ability to retain that data. (Other encryption-related issues are discussed at Section 3, infra.) If the platform's encryption settings make text collection impossible, the company may need to consider alternative retention methods, such as capturing screenshots of text exchanges or video recording text chats. (3) Is end-to-end encryption a necessary security feature, an organizational vulnerability or both? End-to-end encryption typically prevents third-party intermediaries that help transmit (and often store) a communication from accessing that communication's content. Platforms offering end-to-end encryption now increasingly also prevent themselves, the provider of the communications service, from accessing a message's content. While this feature provides heightened security for those transmitting communications, it can hinder a platform's ability to preserve or otherwise retain data. For example, some messengers' end-to-end encryption prevents them from accessing, and therefore retaining, the content of communications. As a result, the content is preserved only on the devices of the sender and the recipient of the message. Those platforms might still collect and retain metadata, however, including a device's unique Internet Protocol address and message time stamps. In contrast, other messengers do not collect either the content or the metadata associated with any messages, but the content remains accessible on the devices themselves, so long as the sender or recipient does not delete it. Companies should be aware of the security and encryption settings of any communication platform their employees use, and consider whether additional software is needed to ensure sufficient data retention. (4) How significant are the risks created by employees using personal devices for work? As the JonesTrading matter illustrates, personal cellphones and personal computers have replaced company devices for many employees. While the use of personal devices is fairly common across industries, there are significant risks to consider for conducting business on personal devices. One of the largest risks is that data might be unrecoverable by the company in the event of an investigation—for example, if the employee used a communication tool that permits the deletion of message content, such as Signal or Telegram, and deleted the communication. For employers in industries that require document retention, such as certain regulated financial institutions, failure to retain company communications transmitted over employees' personal devices can also result in violations of federal laws and regulations. As JonesTrading and others have discovered, employers can still be responsible for retaining relevant electronic information, even from employees' personal devices, and be held liable and subject to fines if such material is lost.3 In contrast, employer-provided devices or software provide better control of content, are clearly the property of the employer and assist with improved liability management. Consider whether a personal device policy or an employer-provided device policy best suits your business needs. (5) What can I do to reduce our company's risk? a. Review your current retention policies. With more employees working remotely than ever before, your company's retention policies may need to be reviewed and updated. For example, you may consider adjusting your company's data retention and deletion periods. The shift to remote working may have increased the volume of your employees' digital footprints, perhaps because in-person handling of data takes too long to be (or cannot be) completed, or because data previously transferred on physical drives has been shifted to transfer by way of FTP/SFTP sites or shared network locations. As a result, it may take longer to run backups of your company data, or you may hit storage volume limits. Now is also a good time to review the retention policies on software and cloud options your company uses and has available. Cloud services often update their service offerings, including security and retention. Even now, providers are modifying their offerings to meet new needs their clients are asking for in the post-COVID-19 environment. b. Send a compliance reminder about which platforms your employees may use while working remotely. Providing clear guidance for employees and reminders of the new communication policies may help reduce employee use of unauthorized tools. But as the JonesTrading matter shows, simply having policies is not enough if those policies are not followed. Therefore, in addition to providing copies of relevant compliance policies, taking the time to explain the security and legal risks of noncompliance may further incentivize employees to refrain from using unauthorized forms of communication. Consider offering trainings on the policies, and create opportunities for employees to ask follow-up questions without fear of retaliation. For example, an employee may realize she needs to transfer a client relationship that had been maintained on an unauthorized platform—the client's preferred form of communication—to an authorized platform but be unsure how to do so; that same employee may also need help retaining any still-available prior communications from the unauthorized platform, whether on the new platform or otherwise. c. Consider whether any SEC and FINRA retention policies make sense for your business. Many industries are subject to retention requirements. For example, retention of broker-dealer books and records is governed by Exchange Act Section 17(a)(1), SEC Rules 17a-3 and 17a-4, and FINRA Rule 4511; for investment advisors, Rule 204-2 of the Investment Company Act of 1940 controls. While not all industries have such legally mandated retention policies, a review of regulatory guidance and industry best practices to ensure compliance with applicable and current data retention policies is recommended. d. Communicate with your employees, and address gaps in the technology. Keep open channels of communication with your employees to ensure they have the communication and internal collaboration tools required to meet client needs. The aphorism "the best offense is a good defense" applies. Identify gaps in technology before your employees need to figure out solutions for themselves. This will not only prevent individualized, and potentially conflicting, approaches, but also affirm your company's commitment to support your employees during this challenging period. e. Be vigilant and respond to red flags. Often, employees using unauthorized methods of communication are well-intentioned. They may refer to their use of unauthorized platforms ("Following up on my text…") or copy or forward unauthorized communications to other staff members or managers. Encourage your entire organization (and especially supervisors) to work together to identify when an employee is using an unauthorized medium and respond appropriately to correct the situation. |
| Ransomware Activity Alert For the Healthcare Sector - by Adam Silverman - The Ark Valley Voice Posted: 29 Oct 2020 06:21 AM PDT Late yesterday the Cybersecurity & Infrastructure Security Agency (CISA), which is part of the U.S. Department of Homeland Security (DHS), issued a ransomware activity targeting alert for the healthcare industry. These attacks are a major problem for hospitals, doctors' offices, and other medical and healthcare providers and facilities at the best of times, as they lock providers out of their systems in an attempt to extort money in order to unlock the system. According to DHS, the threat is coming from Russian hackers. While such ransomware activity is becoming more common, what.is different than normal is that it is aimed at a specific industry category — healthcare, hospitals, and the public health sector. During a pandemic, such attacks move from major problems to existential threats. "We expect panic," one hacker involved in the attacks said in Russian during a private exchange on Monday that was captured by Hold Security, a security company that tracks online criminals. Some hospitals in New York State and on the West Coast reported cyberattacks in recent days, though it was not clear whether they were part of the attacks, and hospital officials emphasized that critical patient care was not affected. The Russian hackers are believed to be based in Moscow and St. Petersburg. Hold Security uncovered evidence that they have been trading a list of more than 400 hospitals they plan to target. Alex Holden, the founder of Hold Security, shared the information with the F.B.I. . He said the hackers claimed to have already infected more than 30 healthcare organizations.
|
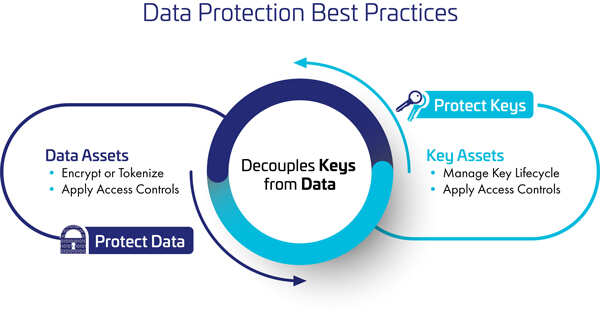
| Deciphering the data protection mandates in the Indian securities market - ETCIO.com Posted: 29 Oct 2020 06:00 AM PDT  Protecting sensitive business data has become increasingly important in today's socially distanced, remote-working world. This is especially true for securities and investments companies that collect and manage an enormous amount of personal data of their customers. Protecting sensitive business data has become increasingly important in today's socially distanced, remote-working world. This is especially true for securities and investments companies that collect and manage an enormous amount of personal data of their customers.Taking into account the rising cybersecurity threats, India's markets regulator Securities and Exchange Board of India (SEBI) has formulated a comprehensive cybersecurity policy framework titled "Cyber Security and Cyber Resilience Framework for Stock Brokers/Depository Participants" and "Mutual Funds/Asset Management Companies (AMCs)." Through these two policy frameworks, SEBI has issued clear data protection mandates that Indian Stock Brokers, Depository Participants, Mutual Fund Companies and AMCs should follow. Below are the five key points outlined in these two mandates: 1. Sensitive data, whether in-motion or at-rest, should be identified and encrypted using strong encryption methods like Advanced Encryption Standard (AES), Rivest–Shamir–Adleman (RSA), etc.2. Data masking should be adopted wherever possible. 3. Specific personnel should be identified to take charge of the encryption methodologies and storage of encryption keys so that they don't fall into the wrong hands. 4. When a company application transmits sensitive data via the Internet, it should be over a secure, encrypted channel to prevent Man-In-The-Middle (MITM) attacks. Strong transport encryption mechanisms like Transport Layer Security (TLS), also known as Secure Socket Layer or SSL should be used. 5. Passwords, security PINs, etc. should never be stored in plain text. Instead, they should be one-way hashed using strong cryptographic hash functions before storage. Additionally, one-way cryptographic hashes should be used to ensure that the stored password hashes are never transformed into their original plaintext values. Just like SEBI's mandates, the practice of data encryption and key management is recommended by almost all data protection regulations like General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry Data Security Standard (PCI DSS). In India, regulators like the Unique Identification Authority of India (UIDAI), Insurance Regulatory and Development Authority of India (IRDAI) and Reserve Bank of India (RBI) have time and again issued circulars mandating the adoption of data encryption and key management. Furthermore, the upcoming Personal Data Protection Act in India also mandates data encryption and key management for protecting sensitive data. In 2018, we comprehensively covered the Personal Data Protection Act in a three-part blog post series (Part 1, Part 2 and Part 3). Failure to comply with the data protection mandates can cause significant damages in penalties as recently experienced by SPARTOO, a European online footwear retailer, who received a fine of €250,000 by French data protection authority CNIL for violating multiple articles of GDPR.Taking a cue from GDPR, the upcoming Personal Data Protection Act in India prescribes a stiff penalty of 4% of a company's global turnover or Rs. 15 crores; whichever is higher, for non-compliance to the mandated data protection guidelines. Complying With Various Data Protection Mandates In India 1. Data Encryption With a proliferation of disparate applications spread across on-premises, cloud and virtual environments, encrypting sensitive data wherever it resides becomes paramount to enterprise-wide data protection. Thales's vast range of data encryption solutions not only helps organisations breach-proof their sensitive data but also helps them cohesively meet compliance mandates across multiple data protection regulations. 2. Key Management Since encryption keys evolve through multiple phases during their lifetime – like generation, registration, distribution, rotation, archival, backup, revocation and destruction, securely and efficiently managing these keys at each phase of their lifecycle becomes fundamental to protection of data. Furthermore, to ensure that the encryption keys don't fall in the wrong hands, and thereby render the entire encryption exercise futile, encryption keys should be decoupled i.e. separated, from encrypted data.
To Sum It Up With cyberattacks increasing in India by as much as 500% since the COVID-19 lockdown was imposed in March this year (as estimated by Mr. Pavan Duggal, a Supreme Court advocate and cyber law expert), protecting sensitive business data has become more important than ever. New insights from the 2020 Thales Asia-Pacific Data Threat Report reveal that nearly half (45%) of Asia-Pacific (APAC) organisations suffered a breach or failed a compliance audit in the last year. Encrypting sensitive data and securely managing the encryption keys centrally not only mitigates data breach risks but also helps organisations adhere to the data protection mandates. |
| You are subscribed to email updates from "encryption software,encrypted device memory,what happens when you encrypt your phone" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |

Comments
Post a Comment