7 mobile device security best practices for businesses - TechTarget
7 mobile device security best practices for businesses - TechTarget |
- 7 mobile device security best practices for businesses - TechTarget
- The 5 Best Android Gallery Vault Apps to Hide Your Private Photos - MUO - MakeUseOf
- Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data - HealthITSecurity.com
| 7 mobile device security best practices for businesses - TechTarget Posted: 30 Apr 2021 01:56 PM PDT It's up to IT admins to enable employees to work from their mobile devices, but IT admins have to keep mobile security at the top of their list in addition to end-user experience. Users are most productive when they have mobile access to their corporate resources, so enabling this access is a critical goal for most organizations -- but mobility is complex. It is not as simple as giving an end user a device and having them log into their preferred email client. IT admins needs to think about getting devices to a securely managed and productive state while ensuring the onboarding process is simple, minimally invasive and streamlined for end users. Further, they need to guarantee that users can perform all necessary productivity tasks in a secure environment. Mobile administrators should follow these seven mobile device security best practices to ensure they meet these goals. 1. Manage mobile devices with an MDMAny organization that gives access to corporate data on mobile devices should consider using mobile device management. MDM is an IT admin's first line of defense when it comes to securing mobile devices. MDM's role is to provide the organization with the ability to enforce security compliance controls on devices (see Figure 1). 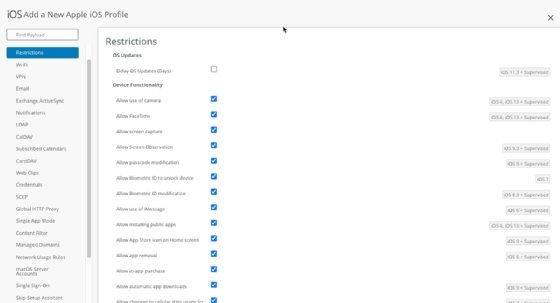 Some of the most common profile and compliance settings include the following:
An MDM platform can manage various devices, including iOS, Android, Windows, macOS and even Chrome OS in some cases. MDM is a very flexible type of tool that gives admins many controls to ensure devices are secured and properly supported. Additionally, for business-only mobile devices, consider looking into Apple Business Manager and Android Enterprise programs. They integrate with the MDM to give organizations more privileges on a device to enforce higher-level security configurations, including advanced restrictions and settings controls, home screen layout, single app mode, multi-user and shared modes, zero-touch enrollments and much more. 2. Manage authentication and accessThere are plenty of different approaches that IT admins can take to enable mobile authentication, including the following: PIN code managementThe PIN often serves as a password for mobile devices, preventing bad actors from gaining unauthorized access to a device. For both the end users' and organization's safety and security, organizations should enforce a PIN code policy. This policy could, for example, require a minimum of eight digits for the PIN. This will ensure that devices are always in compliance. IT can best implement this automation from an MDM. Multifactor authenticationAdmins may do their best to ensure mobile device security, but once a device leaves the office building it is susceptible to numerous attacks. An admin can't always control what network that device will connect to next, or the risk conditions the device will enter. Multifactor authentication (MFA) will provide more comprehensive security by confirming that the end user logging on is who they claim to be. It requires two or more authentication methods, which can include PIN or password, SMS verification and biometric factor authentication. An admin can then set parameters for when to require MFA based on the device's trust and risk conditions. MDM can also be a mechanism to push out the requirement to devices, integrating the preferred MFA into the MDM enrollment workflow and allowing the MDM to serve as the central hub for all device security and enrollment configurations. 3. Enable data loss prevention policiesUsers require numerous applications on their mobile devices to get their job done, so IT admins have to ensure any corporate data is not copied and accessed in an unmanaged or untrusted application. Organizations can use app protection and DLP policies to prevent company data from saving locally to the device. IT admins can also restrict data transfer -- or the "open in" option -- to other apps that are not approved or managed, limiting specific capabilities, such as copy and paste (see Figure 2). 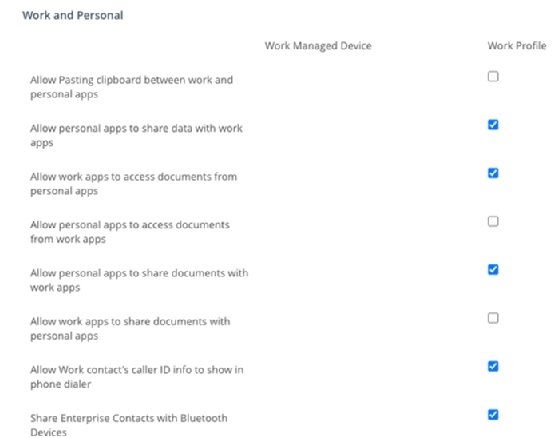 Platforms such as Microsoft Endpoint Manager will even allow app protection policies on Microsoft apps without requiring devices to be enrolled in MDM. For devices that are enrolled in an organization's MDM, the MDM is the mechanism to create and enforce these security restrictions to ensure data loss protection. 4. Corporate and BYOD remote lock, device wipe policiesWhat happens if an employee loses a device or leaves the company? Every business should develop a corporate-owned and BYOD policy on how to handle device loss and data wipes. Under this type of policy, whenever a mobile device is thought to be lost or stolen, the organization can take actions to secure data, including a data wipe, reset or device lock. This type of policy gets messy with BYOD environments; not every user likes the idea of allowing IT this type of control over their devices. However, both Google and Apple have addressed this issue with recent updates to their platforms. In iOS 13, Apple introduced User Enrollment, which significantly restricts how much an MDM platform can do on a personal BYOD iPhone -- including removing the ability to perform a factory reset of a device. In the latest Android versions, Google's Android Enterprise work profile feature enables users to keep distinct work and personal apps and data. Each profile is entirely separate; the organization manages the work apps and data, while the end user's apps, data and usage remain untouched. This restricts invasive management tasks, such as the factory reset. 5. Keep BYOD and corporate devices updatedKeeping devices updated is not an easy task, but it is extremely important. For example, in March 2021 Apple released a critical iOS update -- 14.4.2 -- that patched a crucial vulnerability in WebKit, and advised all users to install it. Mobile devices are a growing target for malware and other attacks, and one of the best ways to fight against that is to ensure that all managed devices are fully up to date.
There are plenty of different approaches that IT admins can take to keep devices updated in a timely manner. Asking users to implement updates is a simple approach, but not always a successful one. One of the best ways to encourage end users to update is to enforce controls via the MDM. For devices that are enrolled with an MDM platform, an IT admin can schedule a mobile OS update for all users -- ideally in a low-use time, such as the middle of the night. On corporate-only devices, IT can take that a step further, and the MDM can schedule, download and auto-install the updates. With BYOD environments, it can be a bit trickier. Mobile IT admins can schedule a prompt for the user to download and install the update, but it is still up to the end user to trigger the process. However, there are mechanisms IT admins can put in place via MDM; one such mechanism is a compliance policy. A compliance policy would allow an admin to create an "if this, then that" automation for devices. An example of this would be a compliance policy that targets devices with a specific version of iOS. An admin can create an action that would send a notification to a user to update; then, after two days, if that device has not been updated, an admin can take steps such as the quarantine or removal of corporate email and access from the device. These restrictions would remain in place until the user updates the device OS. These compliance policies help keep corporate data safe while also encouraging end users to stay up to date. While this example targeted iOS, the same types of policies can apply to Android devices. 6. Monitor device compliance and automate with mobile threat defenseMDM is a management tool with device-level security controls, but it can lack the ability to detect and prevent attacks from malicious applications, networks and phishing. Over the past year, there has been an increase in phishing attacks against mobile devices. Mobile devices are still endpoints, just like a desktop OS, and in many of the same ways IT also needs to secure them. Mobile threat defense (MTD) platforms detect man-in-the-middle attacks over Wi-Fi, identify suspicious behavior on a device, and proactively search for malware, harmful applications and mobile phishing attacks. It can then remediate issues with various methods, including killing the device's Wi-Fi or cellular connection to prevent further data leakage, or working in tandem with an MDM to quarantine a device. At a high level, an MTD platform can perform these functions:
Together MTD and MDM platforms provide more robust security for mobile devices and users. 7. Keep your end users informedIT admins can put as much technology as they want toward fixing a problem, but the end users hold the keys to success. It is vital to train end users and keep them informed on current threats and vulnerabilities. Helping end users understand the importance of updates -- and how they can affect corporate data -- should help them make the right decisions related to device security. |
| The 5 Best Android Gallery Vault Apps to Hide Your Private Photos - MUO - MakeUseOf Posted: 09 Apr 2021 12:00 AM PDT [unable to retrieve full-text content]The 5 Best Android Gallery Vault Apps to Hide Your Private Photos MUO - MakeUseOf |
| Google Sued, Lawsuit Claims COVID-19 Contact Tracing Tool Exposes Data - HealthITSecurity.com Posted: 30 Apr 2021 07:24 AM PDT - Two individuals who used California's state public health COVID-19 contact tracing app have filed a lawsuit against its developer, Google, claiming the tool exposes user data and violated their privacy, among other allegations. The Google-Apple Exposure Notification (GAEN) System was developed by the tech giants to support governments and public health agencies control the spread of the coronavirus. The tech leans on proximity data gathered from Bluetooth functions of mobile devices and alerts individuals of potential exposure. At the time of the announcement in April 2020, Google provided a detailed plan of its privacy policies that included a requirement of explicit user consent, along with a list of frequently asked questions to reiterate the companies' privacy policies. Those policies included ensuring the generation of tracking keys linked to the user's device were randomized, instead of mathematically pulling the data from the user's private key. The tech companies also pledged to disable the service once the pandemic had been contained. The announcement was met with a host of concerns from a range of privacy stakeholders, particularly around user consent and the heavy reliance on APIs. The National Association of Attorneys General (NAAG) stressed that the apps may not sufficiently protect the personal information of consumers. READ MORE: AGS Urge Apple, Google to Ensure Privacy of COVID-19 Contact Tracing The lawsuit, filed in the US District Court of Northern California in San Jose, alleges the app confirmed those concerns. "Because Google's implementation of GAEN allows this sensitive contact tracing data to be placed on a device's system logs and provides dozens or even hundreds of third parties access to these system logs, Google has exposed GAEN participants' private personal and medical information associated with contact tracing, including notifications to Android device users of their potential exposure to COVID-19," according to the lawsuit. Specifically, the lawsuit alleges that the app's use of "rolling proximity identifiers" on devices' Bluetooth radio is recorded by Google's GMS records, which "unwittingly expose[d] not only their information to numerous third parties, but also information from unsuspecting GAEN users on other devices (including non-Android devices, such as iPhones) who come within range of them." Further, the identifiers are maintained along other device identifiers and stored to mobile device system logs, it's then available to third parties that have access to those logs. And as the exposed information is personally identifiable, the information can be used to trace the identifier back to user identities, locations, and other identifiers. "For those who have reported testing positive, it enables third parties to link that diagnosis back to the particular patient, defeating the purported anonymity Google claims for its service," the lawsuit claims. READ MORE: New COVID-19 Spear-Phishing, Spoofing Attacks Mimic Google, WHO "Even if GAEN does not log COVID-19 diagnoses to the system logs directly, a positive COVID-19 test result can be inferred from the RPIs that are written to the system logs, because, as discussed supra, the Key associated with a positive diagnosis is made publicly available," it continues. "Anyone can access the publicly-disclosed Key and identify which RPIs were generated by a device belonging to a COVID-19 infected individual." The lawsuit further claims that Google was informed of the GAEN flaw in February 2021, which caused the alleged data breach. However, the public has not been informed that "their private personal and medical information exposed to third parties." The individuals also claimed that Google indirectly confirmed the existence of the flaw outlined in the lawsuit, when it began addressing a security flaw through a software update. The lawsuit claims the tech giant violated the California Confidentiality of Medical Information Act, as well as common law and privacy rights, and seeks to obtain a mandatory public injunction that would require Google to remediate the alleged issue. The individuals are also seeking alleged damages and restitution, along with a nationwide class-action for Android users who downloaded or activated a contact tracing app built on Google's GAEN—roughly 28 million individuals. READ MORE: Sens. Flag Privacy, Security Concerns Over Google COVID-19 Screening Site As previously explained to HealthITSecurity.com by Kelvin Coleman, executive director, National Cybersecurity Alliance (NCSA), the lack of a federal privacy in the US has fueled privacy concerns. But the tech giants implemented key security requirements, likely built on compliance with privacy regulations. "Google and Apple have already taken a good first set of steps to better ensure privacy by barring the use of location data tracking in their contact tracing API," Coleman said, at the time. "Other government agencies or private sector developers should ideally follow the same example." "They should also be transparent in communicating to users the vulnerabilities surrounding Bluetooth functionality, why enabling it on devices should be done on as needed basis, the importance of using encryption measures and enabling MFA for any apps that use or collect personally identifiable information." |
| You are subscribed to email updates from "mobile phone security,encryption policy android,how good is android encryption" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |
Comments
Post a Comment