Capital One Data Theft Impacts 106M People — Krebs on Security - Krebs on Security
Capital One Data Theft Impacts 106M People — Krebs on Security - Krebs on Security |
- Capital One Data Theft Impacts 106M People — Krebs on Security - Krebs on Security
- 5 Ways to Protect Yourself from Cybercrime - Government Technology
- Encryption for Android (Guide) | 3 ways to Secure your Android phone - https://proprivacy.com/
- Hacker Arrested In Capital One Breach Affecting 100M+ - pymnts.com
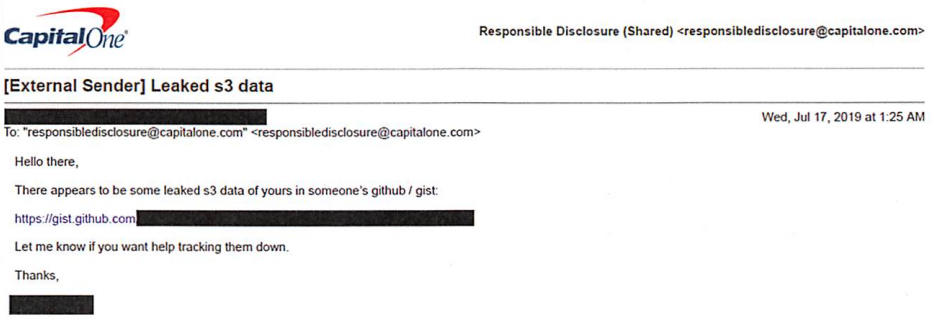
| Capital One Data Theft Impacts 106M People — Krebs on Security - Krebs on Security Posted: 30 Jul 2019 01:04 PM PDT Federal prosecutors this week charged a Seattle woman with stealing data from more than 100 million credit applications made with Capital One Financial Corp. Incredibly, much of this breach played out publicly over several months on social media and other open online platforms. What follows is a closer look at the accused, and what this incident may mean for consumers and businesses.  Paige "erratic" Thompson, in an undated photo posted to her Slack channel. On July 29, FBI agents arrested Paige A. Thompson on suspicion of downloading nearly 30 GB of Capital One credit application data from a rented cloud data server. Capital One said the incident affected approximately 100 million people in the United States and six million in Canada. That data included approximately 140,000 Social Security numbers and approximately 80,000 bank account numbers on U.S. consumers, and roughly 1 million Social Insurance Numbers (SINs) for Canadian credit card customers. "Importantly, no credit card account numbers or log-in credentials were compromised and over 99 percent of Social Security numbers were not compromised," Capital One said in a statement posted to its site. "The largest category of information accessed was information on consumers and small businesses as of the time they applied for one of our credit card products from 2005 through early 2019," the statement continues. "This information included personal information Capital One routinely collects at the time it receives credit card applications, including names, addresses, zip codes/postal codes, phone numbers, email addresses, dates of birth, and self-reported income." The FBI says Capital One learned about the theft from a tip sent via email on July 17, which alerted the company that some of its leaked data was being stored out in the open on the software development platform Github. That Github account was for a user named "Netcrave," which includes the resume and name of one Paige A. Thompson. The complaint doesn't explicitly name the cloud hosting provider from which the Capital One credit data was taken, but it does say the accused's resume states that she worked as a systems engineer at the provider between 2015 and 2016. That resume, available on Gitlab here, reveals Thompson's most recent employer was Amazon Inc. Further investigation revealed that Thompson used the nickname "erratic" on Twitter, where she spoke openly over several months about finding huge stores of data intended to be secured on various Amazon instances. 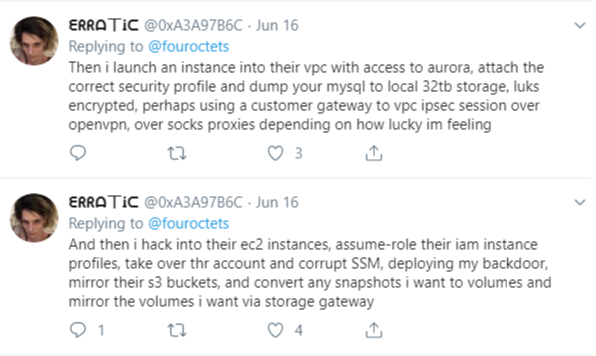 The Twitter user "erratic" posting about tools and processes used to access various Amazon cloud instances. According to the FBI, Thompson also used a public Meetup group under the same alias, where she invited others to join a Slack channel named "Netcrave Communications." KrebsOnSecurity was able to join this open Slack channel Monday evening and review many months of postings apparently made by Erratic about her personal life, interests and online explorations. One of the more interesting posts by Erratic on the Slack channel is a June 27 comment listing various databases she found by hacking into improperly secured Amazon cloud instances. That posting suggests Erratic may also have located tens of gigabytes of data belonging to other major corporations: 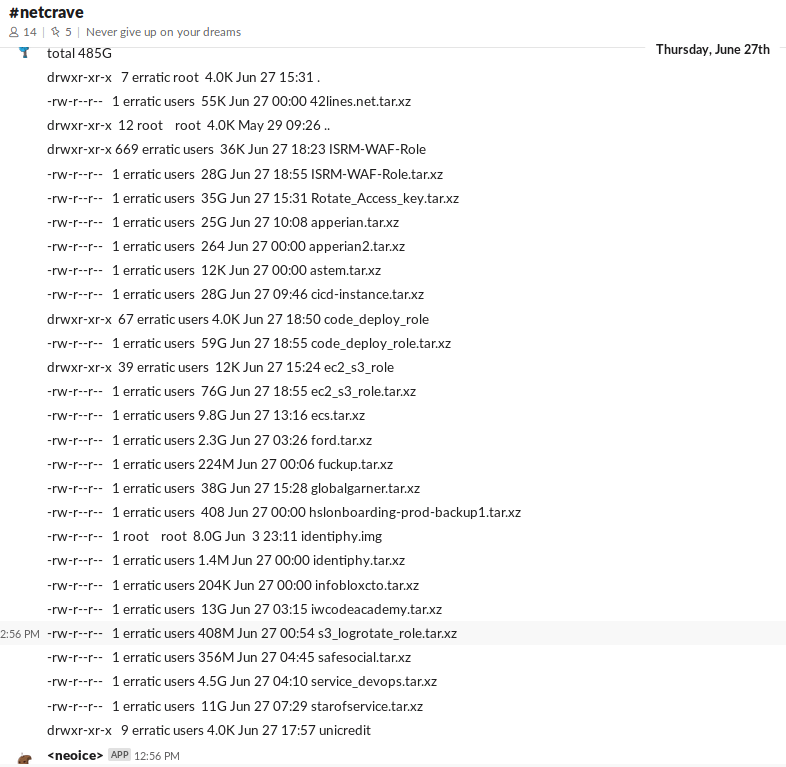 According to Erratic's posts on Slack, the two items in the list above beginning with "ISRM-WAF" belong to Capital One. Erratic also posted frequently to Slack about her struggles with gender identity, lack of employment, and persistent suicidal thoughts. In several conversations, Erratic makes references to running a botnet of sorts, although it is unclear how serious those claims were. Specifically, Erratic mentions one botnet involved in cryptojacking, which uses snippets of code installed on Web sites — often surreptitiously — designed to mine cryptocurrencies. None of Erratic's postings suggest Thompson sought to profit from selling the data taken from various Amazon cloud instances she was able to access. But it seems likely that at least some of that data could have been obtained by others who may have followed her activities on different social media platforms. Ray Watson, a cybersecurity researcher at cloud security firm Masergy, said the Capital One incident contains the hallmarks of many other modern data breaches. "The attacker was a former employee of the web hosting company involved, which is what is often referred to as insider threats," Watson said. "She allegedly used web application firewall credentials to obtain privilege escalation. Also the use of Tor and an offshore VPN for obfuscation are commonly seen in similar data breaches." "The good news, however, is that Capital One Incidence Response was able to move quickly once they were informed of a possible breach via their Responsible Disclosure program, which is something a lot of other companies struggle with," he continued. In Capital One's statement about the breach, company chairman and CEO Richard D. Fairbank said the financial institution fixed the configuration vulnerability that led to the data theft and promptly began working with federal law enforcement. "Based on our analysis to date, we believe it is unlikely that the information was used for fraud or disseminated by this individual," Fairbank said. "While I am grateful that the perpetrator has been caught, I am deeply sorry for what has happened. I sincerely apologize for the understandable worry this incident must be causing those affected and I am committed to making it right." Capital One says it will notify affected individuals via a variety of channels, and make free credit monitoring and identity protection available to everyone affected. Bloomberg reports that in court on Monday, Thompson broke down and laid her head on the defense table during the hearing. She is charged with a single count of computer fraud and faces a maximum penalty of five years in prison and a $250,000 fine. Thompson will be held in custody until her bail hearing, which is set for August 1. A copy of the complaint against Thompson is available here. Update, 3:38 p.m. ET: I've reached out to several companies that appear to be listed in the last screenshot above. Infoblox [an advertiser on this site] responded with the following statement: "Infoblox is aware of the pending investigation of the Capital One hacking attack, and that Infoblox is among the companies referenced in the suspected hacker's alleged online communications. Infoblox is continuing to investigate the matter, but at this time there is no indication that Infoblox was in any way involved with the reported Capital One breach. Additionally, there is no indication of an intrusion or data breach involving Infoblox causing any customer data to be exposed." Tags: Capital One breach, GitHub, Masergy, Paige A. Thompson, Ray Watson, Slack, twitter |
| 5 Ways to Protect Yourself from Cybercrime - Government Technology Posted: 30 Jul 2019 11:42 AM PDT High-profile data breaches at companies like British Airways and Marriott get a lot of media coverage, but cybercriminals are increasingly going after community groups, schools, small businesses and municipal governments. Just in the Midwest, hospitals, libraries, voter registration systems and police departments have fallen victim to one type of digital hijacking or another. Cybercrime is not just a concern for corporate technology departments. Schools, scout troops, Rotary clubs and religious organizations need to know what to look for and how to handle it. As the academic director of a new cybersecurity clinic at Indiana University, I'll be helping to lead students and faculty members in teaching local, county and state government agencies, not-for-profit organizations and small businesses how to improve their cyberhygiene. They'll learn how to better manage digital systems, protect their intellectual property and improve consumer privacy. Everyone should know the basics for how to protect themselves and the groups or organizations they're part of. Here is a brief look at some of the cybersecurity best practices we'll be teaching members of our communities to keep in mind as they go online for work, play or volunteering. 1. Keep everything up to dateMany breaches, including the 2017 one at the Equifax credit bureau that exposed the financial information of almost every American adult, boil down to someone leaving out-of-date software running. Most major computer companies issue regular updates to protect against newly emerging vulnerabilities. Keep your software and operating systems updated. To make it easy, turn on automatic updates when possible. Also, be sure to install software to scan your system for viruses and malware, to catch anything that might get through. Some of that protection is free, like Avast, which Consumer Reports rates highly. 2. Use strong, unique passwordsRemembering passwords, especially complicated ones, isn't fun, which is why so much work is going into finding better alternatives. For the time being, though, it's important to use unique passwords that are different for each site, and not easy-to-hack things like "123456" or "password." Choose ones that are at least 14 characters long. Consider starting with a favorite sentence, and then just using the first letter of each word. Add numbers, punctuation or symbols for complexity if you want, but length is more important. Make sure to change any default passwords set in a factory, like those that come with your Wi-Fi router or home security devices. A password manager program can help you create and remember complex, secure passwords. 3. Enable multi-factor authenticationIn many situations, websites are requiring users not only to provide a strong password but also to type in a separate code from an app, text message or email message when logging in. It is an extra step, and it's not perfect, but multi-factor authentication makes it much harder for a hacker to break into your accounts. Whenever you have the option, enable multi-factor authentication, particularly for crucial log-ins like bank and credit card accounts. You could also consider getting a physical digital key that can connect with your computer or smartphone as an even more advanced level of protection. 4. Encrypt and back up your most important dataIf you can, encrypt the data that's stored on your smartphone and computer. If a hacker copies your files, all he'll get is gibberish, rather than, for instance, your address book and financial records. This often involves installing software or changing system settings. Some manufacturers do this without users even knowing, which helps improve everyone's security. For data that's crucial, like medical information, or irreplaceable, like family photos, it's important to keep copies. These backups should ideally be duplicated as well, with one stored locally on an external hard drive only periodically connected to your primary computer, and one remote, such as in a cloud storage system. 5. Be careful using public Wi-FiWhen using public Wi-Fi, anyone nearby who is connected to the same network can listen in on what your computer is sending and receiving across the internet. You can use free browsers like Tor, which was originally developed to provide secure communications for the U.S. Navy, to encrypt your traffic and camouflage what you're doing online. You can also use a virtual private network to encrypt all your internet traffic, in addition to what goes through your browser – like Spotify music or video in the Netflix app – to make it more difficult for hackers, or even casual users, to spy on you. There is a wide range of free and paid VPN options. In short: Be cautious, proactive and informedOf course, there is much more a person or organization can do to protect private data. Search engines like DuckDuckGo don't track users or their searches. Firewall software built into both Windows and Mac OS – or downloaded separately – can help stop viruses and worms from making their way into your systems. To protect yourself against data breaches at places where your information is stored, you should consider freezing your credit, which blocks anyone from applying for credit in your name without your personal permission. It's free. If you have already received a notification that your data has been stolen, consider putting a free "fraud alert" on your credit reports. There are plenty of other places to learn more about cybersecurity, too, including some very good podcasts. No person, organization or computer can ever be 100% secure. Someone with the patience, money and skill can break into even the most protected systems. But by taking these steps, you can make it less likely that you'll be a victim, and in the process help raise the overall level of cyberhygiene in your communities, making everyone safer both online and off. This article is republished from The Conversation under a Creative Commons license. Read the original article. |
| Encryption for Android (Guide) | 3 ways to Secure your Android phone - https://proprivacy.com/ Posted: 02 May 2019 12:00 AM PDT  Encryption in its most basic form is the process of changing information into illegible code to prevent people from accessing your data. As of Android 7.0 Nougat, which was first released in March 2016, almost all Android phones come pre-encrypted. However, this encryption is not without problems. In this article, we show you several ways of encrypting your Android phone. 3 ways to encrypt your Android phone
Current Android EncryptionBefore Android 7.0, data was protected using dm-crypt full disk encryption (FDE). An open source transparent disk encryption subsystem used in Linux, dm-crypt is commonly used for desktop encryption. This approach works quite well on desktop computers, but not so well in Android as users rarely power their devices down. Android enforced strong lock screen protection (via either password or fingerprint) to mitigate against this problem, but this could never be as secure as the 128-bit AES-CBC with essiv:sha256 encryption used to secure data when the device was off. If an adversary could bypass the lock screen, a not impossible task, then the encryption keys would just be sitting there in the memory for them to grab. Final thoughtsThese days, high and mid-range Android phones all come encrypted straight out-of-the-box, and this should also soon be true of low-end Android phones. This is undoubtedly a step forward for the security of most phone users' personal data, but if you store sensitive files on your phone, then you should further encrypt them using something like EDS. |
| Hacker Arrested In Capital One Breach Affecting 100M+ - pymnts.com Posted: 30 Jul 2019 04:01 AM PDT A former Amazon systems engineer working for Capital One is said to be the woman behind a breach that accessed the data of over 100 million people.Software engineer Paige Thompson, 33, allegedly boasted about the hack and left crumbs for investigators to follow, The New York Times reported. Thompson formerly worked for Amazon Web Services, which hosted the Capital One database that was breached. Seattle-based Thompson was charged with one count of computer fraud and abuse following her arrest on Monday (July 30).
The F.B.I. noticed her activity on a Meetup she organizes called Seattle Warez Kiddies, which is for people into "hacking, cracking." This led a GitHub post and to the incriminating Slack message and Tweet. Online, she used the name "erratic." Court documents filed with Seattle's District Court state that Thompson appeared to brag about the information she had accessed related to Capital One. The documents said Thompson accessed the data through a "misconfiguration" of a firewall on a web application. Capital One revealed the massive data breach in a news release on July 29, 2019. The bank says it does not appear that the hacker had used the stolen information for fraudulent purposes, but investigators will continue to look into it. The company said it discovered July 19 that there was unauthorized access and fixed the configuration vulnerability, then immediately notified federal law enforcement. The breach impacts about 100 million individuals in the United States and around 6 million in Canada. Capital One stressed that credit card account numbers and login credentials were not compromised, while more than 99 percent of Social Security numbers were not impacted.
The hack is expected to cost the company between $100 million and $150 million in the near term.  |
| You are subscribed to email updates from "secure email,smartphone encryption app,storage card encryption" - Google News. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |

Comments
Post a Comment